Configuring the Tunnel in the Harmony SASE Administrator Portal
-
Access the Harmony SASE Administrator Portal and click Networks.
-
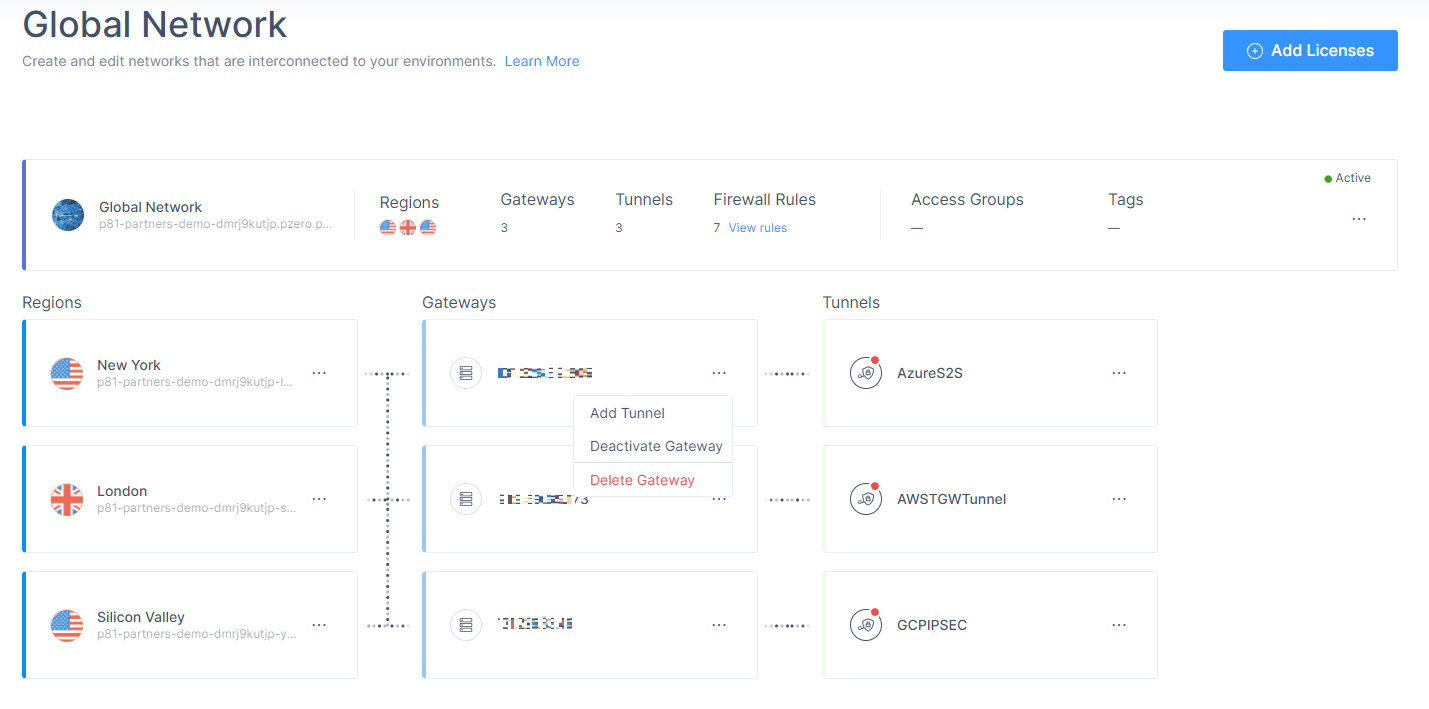
Select the network.
-
Click
and select Add Tunnel for the gateway from which you want to add the IPSec Site-to-Site VPN tunnel.

Note - Only a single dynamic IP IPSec tunnel is supported per each Cloud Gateway.
-
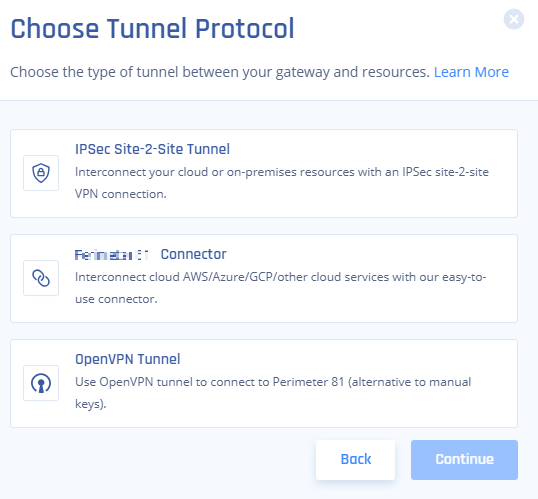
Click IPSec Site-2-Site Tunnel and click Continue.
-
Click Single Tunnel and click Continue.
-
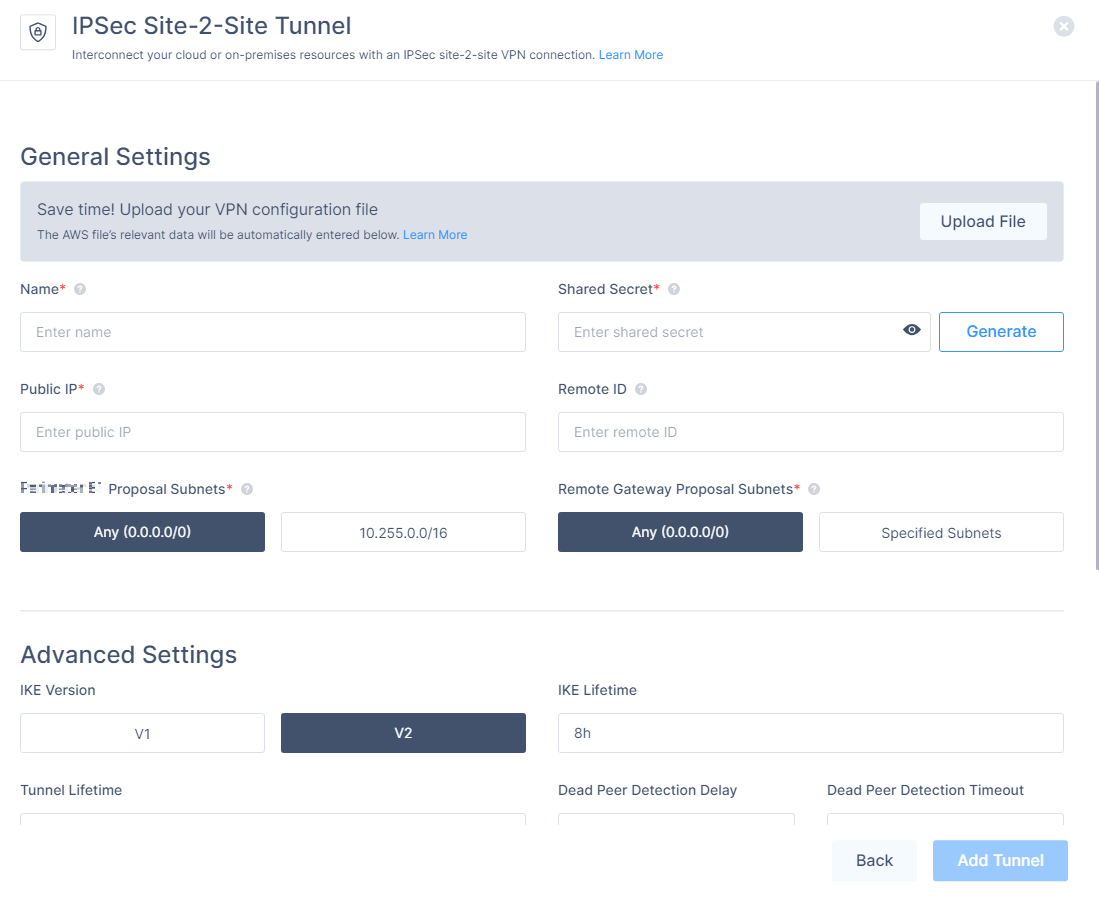
In the General Settings section, enter the relevant details:
Field
Name
Shared Secret
Public IP 1
Remote ID 2
Harmony SASE Gateway Proposal Subnets 3
Remote Gateway Proposal Subnets
Firewall/Router
Name for the tunnel. Enter a secret key or click Generate to generate it.
Barracuda Firewall Public WAN IP address.
Barracuda Firewall Public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
Barracuda internal LAN subnets.
Name for the tunnel. Enter the secret key specified in Check PointSmartConsole or click Generate to generate it.
Public or Egress IP address of Check Point Firewall
Public or Egress IP address of Check Point Any (0.0.0.0)
Any (0.0.0.0)
Name for the tunnel.
Enter a secret key or click Generate to generate it.
Cisco ASA Firewall Public WAN IP address.
Cisco ASA Firewall Public WAN IP address.
Any (0.0.0.0)
Any (0.0.0.0)
Name for the tunnel.
Enter a secret key or click Generate to generate it.
Cisco Meraki Router Public WAN IP address.
Cisco Meraki Router Public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
Cisco Meraki internal LAN subnets.
Name for the tunnel.
Enter a secret key or click Generate to generate it.
D-Link DSR Series Router Public WAN IP address.
D-Link DSR Series Router Public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
D-Link DSR Series Router internal LAN subnets.
Name for the tunnel.
Enter a secret key or click Generate to generate it.
DrayTek Vigor3900 Router Public WAN IP address.
DrayTek Vigor3900 Router Public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
DrayTek Vigor internal LAN subnets.
Name for the tunnel.
Enter a secret key or click Generate to generate it.
DrayTek Vigor2862 Router Public WAN IP address.
Name for the VPN profile on the DrayTek Vigor2862 Router.
Harmony SASE network subnet. The default is 10.255.0.0/16.
DrayTek Vigor internal LAN subnets.
Name for the tunnel.
Enter a secret key or click Generate to generate it.
EdgeMax Router Public WAN IP address.
EdgeMax Router Public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
EdgeMax internal LAN subnets.
Name for the tunnel. Enter a secret key or click Generate to generate it. FortiGate Next Generation Firewall public IP address. FortiGate Next Generation Firewall remote ID. Harmony SASE network subnet. The default is 10.255.0.0/16. FortiGate Next Generation Firewall internal LAN subnets. Name for the tunnel.
Enter a secret key or click Generate to generate it.
Linksys public WAN IP address.
Linksys public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
Linksys internal LAN subnets.
Juniper Networks ScreenOS Firewall Name for the tunnel. Enter a secret key or click Generate to generate it. Juniper Networks ScreenOS Firewall Public WAN IP address. Juniper Networks ScreenOS Firewall Public WAN IP address. Harmony SASE network subnet. The default is 10.255.0.0/16. Juniper Networks ScreenOS internal LAN subnets. Name for the tunnel.
Enter a secret key or click Generate to generate it.
Juniper SRX Firewall Public WAN IP address.
Juniper SRX Firewall Public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
Juniper Networks ScreenOS internal LAN subnets.
Name for the tunnel.
Enter a secret key or click Generate to generate it.
Netgear BR500 Router Public WAN IP address.
Netgear BR500 Router Public WAN IP address.
Harmony SASE network subnet. The default is 10.255.0.0/16.
Netgear BR500 internal LAN subnets.
Palo Alto Firewall Name for the tunnel. Enter the secret key specified in the Palo Alto Management Portal. External internal IP address of Palo Alto Firewall.
You can obtain this from Interfaces > Ethernet in the Palo Alto Management Portal.
External internal IP address of Palo Alto Firewall.
You can obtain this from Interfaces > Ethernet in the Palo Alto Management Portal. If NAT is configured, then enter the internal LAN IP address of the Palo Alto Firewall.
Any (0.0.0.0) Any (0.0.0.0) pfSense Firewall Name for the tunnel. Enter a secret key or click Generate to generate it. pfSense Firewall Public WAN IP address. pfSense Firewall Public WAN IP address. Harmony SASE network subnet. The default is 10.255.0.0/16. pfSense internal LAN subnets. Name for the tunnel. Enter a secret key or click Generate to generate it. SonicWall Firewall Public WAN IP address. SonicWall Firewall Public WAN IP address. Harmony SASE network subnet. The default is 10.255.0.0/16. SonicWall internal LAN subnets. Sophos XG Firewall Name for the tunnel. Enter a secret key or click Generate to generate it. Sophos XG Firewall Public WAN IP address. Sophos XG Firewall Public WAN IP address. Harmony SASE network subnet. The default is 10.255.0.0/16. Sophos XG internal LAN subnets. UniFi USG Firewall Name for the tunnel. Enter a secret key or click Generate to generate it. UniFi USG Firewall Public WAN IP address. UniFi USG Firewall Public WAN IP address. Harmony SASE network subnet. The default is 10.255.0.0/16. UniFi USG internal LAN subnets. WatchGuard Firewall Name for the tunnel. Enter a secret key or click Generate to generate it. WatchGuard Firewall Public WAN IP address. WatchGuard Firewall Public WAN IP address. Harmony SASE network subnet. The default is 10.255.0.0/16. WatchGuard internal LAN subnets. Zyxel USG Firewall Name for the tunnel. Enter a secret key or click Generate to generate it Zyxel USG Firewall Public WAN IP address. Zyxel USG Firewall Public WAN IP address. Harmony SASE network subnet. The default is 10.255.0.0/16. Zyxel USG internal LAN subnets. -
In the Advanced Settings section, enter the relevant details:
Field
IKE Version1 2
IKE Lifetime
Tunnel Lifetime
Dead Peer Detection Delay
Dead Peer Detection Timeout
Encryption (Phase 1)
Encryption (Phase 2)
Integrity (Phase 1)
Integrity (Phase 2)
Diffie Hellman Groups (Phase 1)
Diffie Hellman Groups (Phase 2)
Firewall/Router
Barracuda V2
8h
1h
10s
30s
aes256
aes256
SHA
SHA
modp1024 modp1024 Check Point V2
8h
1h
10s
30s
aes256
aes256
sha256
sha256
modp2048 modp2048 Cisco ASA
V2
8h
1h
10s
30s
aes256
aes256
sha512
sha512
ecp521 ecp521 Cisco Meraki
V1
8h
1h
10s
50s
aes256
aes256
sha1
sha1
modp1536 modp1536 D-Link DSR Series Router
V1
8h
1h
30s
10s
aes256
aes256
sha512
sha512
modp1536 modp1536 DrayTek Vigor2862
V2
8h
1h
30s
60s
aes256
aes256
sha1
sha1
modp1024 modp1024 DrayTek Vigor3900
V1
8h
1h
30s
60s
aes256
aes256
sha1
sha1
modp1536 modp1536 EdgeMax
V1
8h
1h
15s
30s
aes256
aes256
sha1
sha1
modp2048 modp2048 FortiGate Next Generation Firewall V2
8h
1h 10s 30s Default value Default value Default value Default value ecp521 ecp521 Linksys
V2
8h
1h
30s
10s
aes256
aes256
sha1
sha1
modp1536 modp1536 Juniper Networks ScreenOS V1
8h
1h
10s
50s
aes256
aes256
sha1
sha1
modp1536 modp1536 Juniper Networks SRX
V2
8h
1h
10s
30s
aes256
aes256
sha256
sha256
modp2048 modp2048 Netgear BR500
V2
8h
1h
30s
10s
aes256
aes256
sha1
sha1
modp1536 modp1536 Palo Alto V2
8h
1h
10s
30s
aes256
aes256
sha256
sha256
modp2048 modp2048 pfSense V2
8h
1h
10s
30s
aes256
aes256
sha256
sha256
modp2048 modp2048 SonicWall V2
8h
1h
10s
30s
aes256
aes256
sha1
sha1
modp1024 modp1024 Sophos XG V2
8h
1h
10s
30s
aes256
aes256
sha512
sha512
modp2048 modp2048 UniFi USG V2
8h
8h
10s
30s
aes256
aes256
sha1
sha1
ecp521 ecp521 WatchGuard V2
8h
1h
10s
30s
aes256
aes256
sha256
sha256
modp2048 modp2048 Zyxel USG V2
8h
1h
10s
30s
aes256
aes256
sha256
sha256
modp2048 modp2048 1 If V2 is not supported, select V1.
2 For dynamic IP tunnels, select V2.
-
Click Add Tunnel.
1This is the public IP address of the second end of the tunnel.
2 In most cases, the ID of the remote tunnel is the public IP of the tunnel. However, it must be configured to the same value on both ends.
3 The IPSec network selector must be configured to the same value at both ends of the tunnel.