Cisco ASA Firewall
You can configure the tunnel in the Cisco Adaptive security Appliance (ASA) firewall either using CLI or ASDM.
To configure the tunnel in Cisco ASA firewall through CLI:
-
Connect to the firewall through SSH with the privilege-15-level account and then enter the enable mode. For example, using PuTTY.
-
Create a tunnel profile and proposal with the values specified in the Harmony SASE Administrator Portal. Run:
crypto ipsec ikev2 ipsec-proposal Tun-Prop
protocol esp encryption aes-256
protocol esp integrity sha-512
crypto ipsec profile Tun-Prof
set ikev2 ipsec-proposal Tun-Prop
set pfs group21
set security-association lifetime seconds 3600 -
Create a crypto policy with the values specified in the Harmony SASE Administrator Portal. Run:
crypto ikev2 policy 10
encryption aes-256
integrity sha512
group 21
prf sha512
lifetime seconds 28800
crypto ikev2 enable outside -
Select IPsec IKEv2 Tunnels and create a new tunnel with the values specified in the Harmony SASE Administrator Portal. Run:
group-policy Tun-Grp-Pol internal
group-policy Tun-Grp-Pol attributes
vpn-tunnel-protocol ikev2
tunnel-group 131.226.X.X type ipsec-l2l
tunnel-group 131.226.X.X general-attributes
default-group-policy Tun-Grp-Pol
tunnel-group 131.226.X.X ipsec-attributes
ikev2 remote-authentication pre-shared-key SuperSecret
ikev2 local-authentication pre-shared-key SuperSecret -
Create your Virtual Tunnel Interface (VTI). Please be sure to use the IP address in the text. Run:
interface Tunnel1
nameif P81_131.226.X.X
ip address 169.254.2.122 255.255.255.252
tunnel source interface outside
tunnel destination 131.226.X.X
tunnel mode ipsec ipv4
tunnel protection ipsec profile Tun-Prof -
Create a route back to the Harmony SASE subnet. Run:
route P81_131.226.X.X 10.255.0.0 255.255.0.0 169.254.2.121 1
To configure the tunnel with Cisco ASA firewall through Adaptive Security Device Manager (ASDM):
-
Log in to the firewall using ASDM.
-
Create a tunnel profile and proposal with the values specified in the Harmony SASE Administrator Portal:
-
Click Configuration > Site-to-site VPN > Advanced > IPsec Proposals (Transform Sets).
-
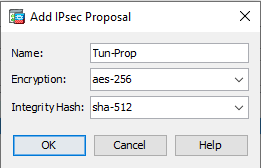
In the IKE v2 IPsec Proposals section, click Add:
Field
Enter
Name Tun-Prop Encryption aes-256
Integrity Hash
sha-512
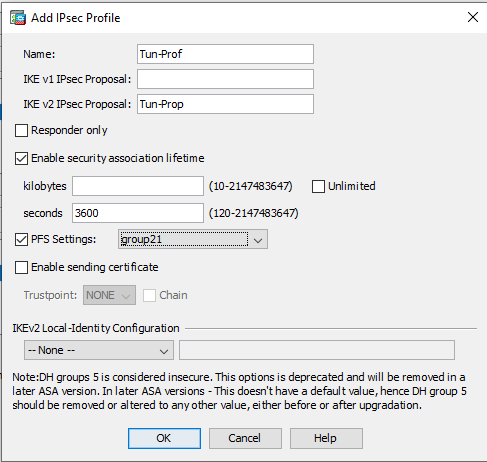
In the IPsec Profile section, click Add:
Field
Enter
Name Tun-Prop IKE v2 IPsec Proposal Tun-Prop
Enable security association lifetime
Select and leave kilobytes blank.
Seconds
3600
-
Click OK.
-
Click Apply and Save.
-
-
Create a crypto policy with the values specified in the Harmony SASE Administrator Portal:
-
Go to Configuration > Site-to-Site VPN > Advanced > IKE Policies.
-
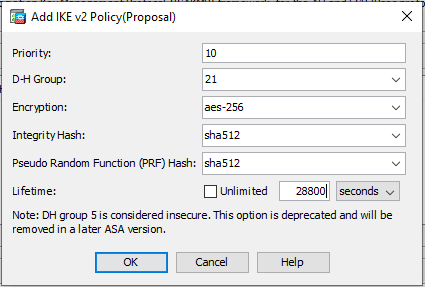
In the IKEv2 Policies section, click Add:
Field
Enter
Priority 10 D-H Group 21
Encryption
AES-256
Integrity Hash
sha256
Pseud0-Random Function (PRF) Hash
sha256
Lifetime
28800 seconds
-
Click OK.
-
-
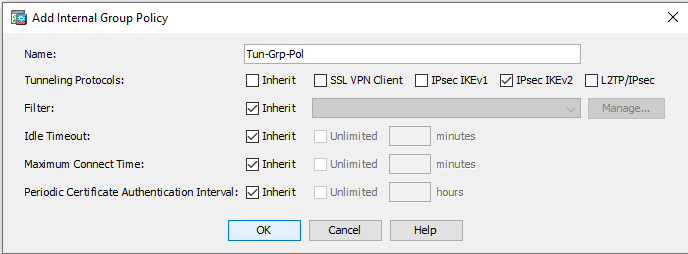
Go to Configuration > Site-to-Site VPN > Group Policies and click Add:
Field
Enter
Name Tun-Prop Tunneling Protocols IPsec IKEv2
-
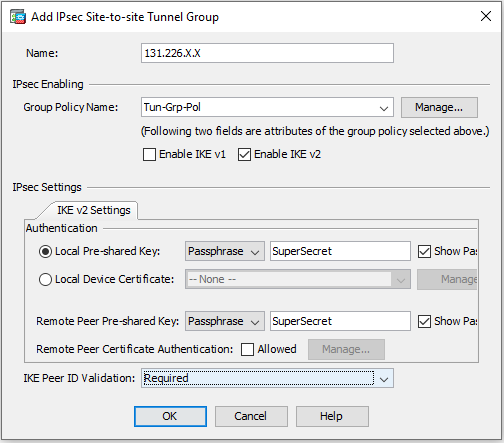
Go to Configuration > Site-to-Site VPN > Advanced > Tunnel Groups and click Add:
Field
Enter
Name 131.226.x.x. Make sure this is same value specified in the Harmony SASE Administrator Portal. Group Policy Name Tun-Grp-Pol
Local Pre-Shared Key
Secret key specified in the Harmony SASE Administrator Portal.
Remote Pre-Shared Key
Secret key specified in the Harmony SASE Administrator Portal.
-
Go to Configuration > Device Setup > Interface Settings > Interfaces and click Add.
-
Select VTI Interface:
-
In the General tab:
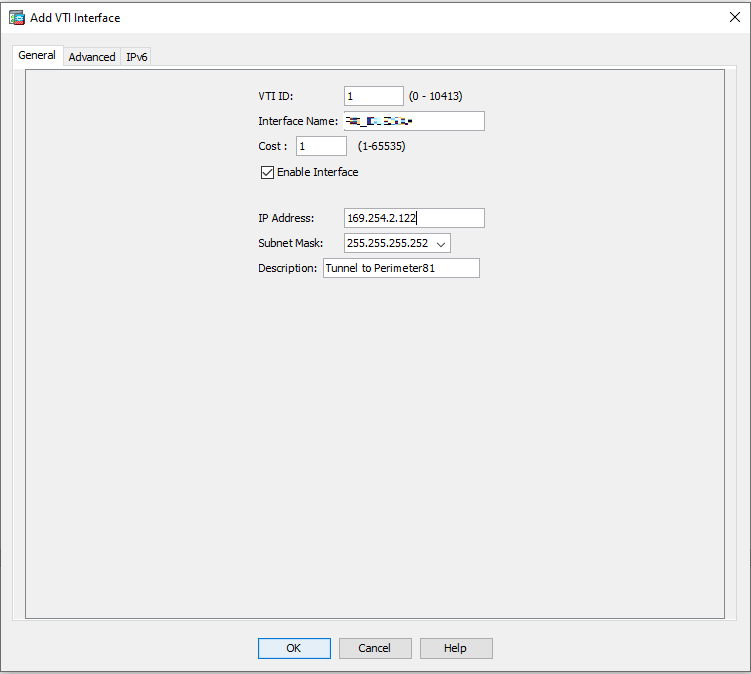
Field
Enter
VTI ID 1 Interface Name Name for the interface.
IP Address
169.254.2.122
Subnet Mask
255.255.255.252
Description
Tunnel to Harmony SASE.
-
In the Advanced tab:
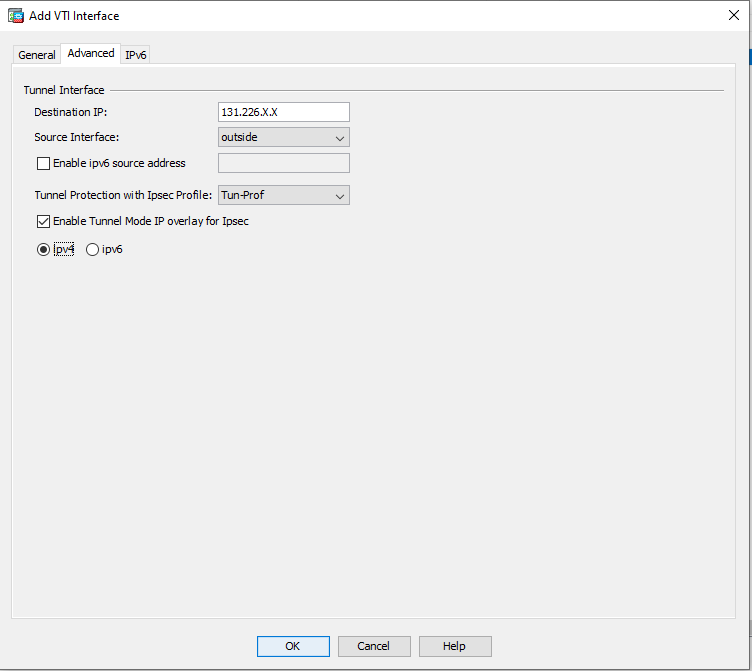
Field
Enter
Destination IP 131.226.x.x. Public IP address of Harmony SASE gateway. Source Interface Name for your outside interface.
Tunnel Protection with Ipsec Profile
Tun-Prof
Enable Tunnel Mode IP overlay for Ipsec
Select and select ipv4.
-
-
Create a route back to the Harmony SASE subnet:
-
Go to Configuration > Firewall > Objects > Network Objects/Groups.
-
Clicking Add > Network Object:
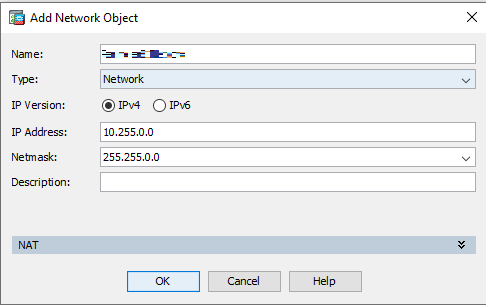
Field
Enter
Name Name for the object. Type Host
IP Version
IPv4
IP Address
169.254.2.121
-
Click OK.
-
-
Go to Configuration > Device Setup > Routing > Static Routes and then click Add:
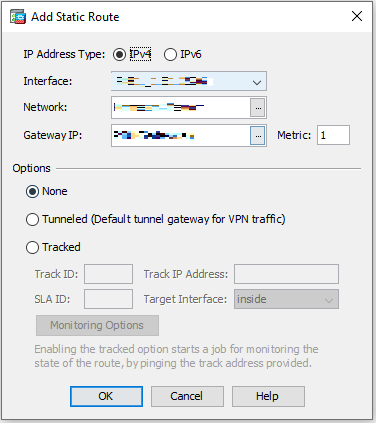
Field
Enter
IP address Type IPv4 Interface Interface that you created for the setup.
Network
Network that you created for the setup.
Gateway IP
Gateway that you created for the setup.
