067
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
Design Pattern
Controlled Sharing
(DMZ)
A demilitarized zone (DMZ) design pattern is used for controlled sharing between two segments
that have a significant security profile differential. This design pattern is applied when users on the
Internet or an extranet need to receive controlled access to internal resources. The DMZ design
pattern can also be used for sharing highly sensitive assets within the organization.
Segmentation
The underlying assumption for a DMZ segment is that attackers from one connected segment
are motivated to compromise the integrity of its internal elements in order to gain access into
the other connected segment. For this reason, DMZ hosts are often referred to as “bastion”
hosts, requiring extraordinary hardening to withstand such attacks. The DMZ security gateways
perform a dual role of protecting against attacks and detecting anomalous information flow
from within the DMZ. The latter may indicate a compromised bastion host.
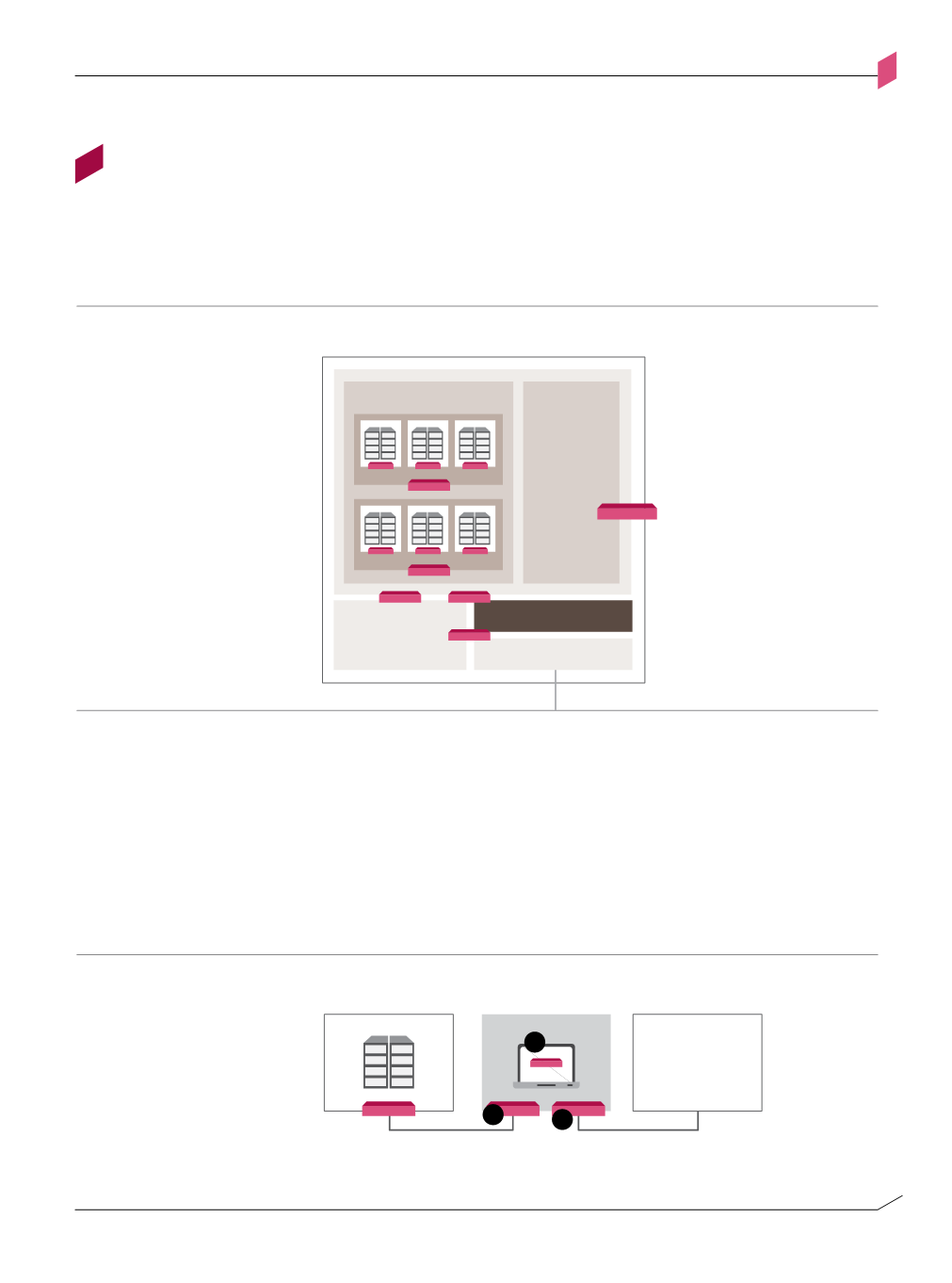
The segmentation model for a DMZ segment is as follows:
DMZ design pattern
Figure A-K
Figure A-k: DMZ design pattern
Data Center
WAN
Servers
NOC/
SOC
DMZ
Internet Access
DMZ segmentation model
Figure A-L
Figure A-l: DMZ segmentation model
De-Militarized Zone
External
(or Segment B)
1
3
2


