065
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
Post-infection Threat Prevention
On-host software scans workstations for malware. Containment controls are
activated if an infection is discovered
Data Protection
Full disk encryption protects data from physical access threats
Removable media is encrypted to prevent unauthorized access to the data
outside of the organization. Data transfer to unencrypted removable media is
blocked
Document encryption provides fine-grained access control for documents
In Virtually Dedicated Access Network design patterns, VPN trusted channels
are established with departmental server segments
Design Pattern
Internet Access
An Internet Access segment consists of network elements that support outbound interactions
from an enterprise site to external entities via the Internet. Note that all inbound interactions
should be handled via a Controlled Sharing (DMZ) segment (see next section).
Segmentation
An Internet Access segment typically does not have significant internal structure. Consider
the following items:
The security profile for an Internet Access segment is equivalent to that of the
Internet. In other words, strict controls should be placed on all interactions with
this segment
Outbound interactions are initiated by clients within the enterprise. Once
initiated, these interactions will allow bi-directional data flow. Controls should
be selected to prevent users from interacting with known or suspected malicious
entities and to protect internal assets from attacks over this vector
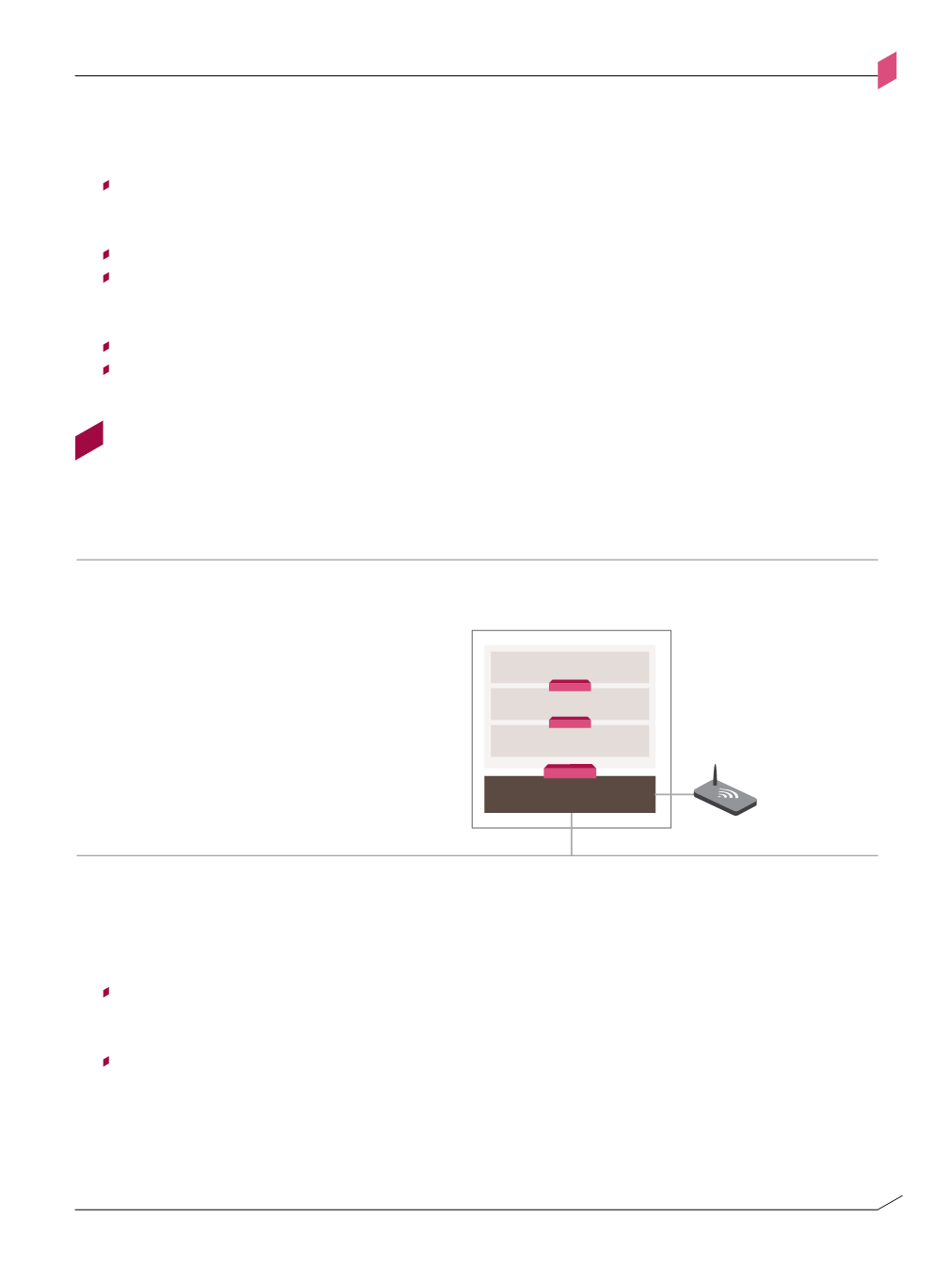
Internet Access design pattern
Figure A-J
Figure A-j: Internet Access design pattern
Main
Office
Servers
Access Network
WAN
Internet Access


