064
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
Protections
The following security controls are typical for the Access Network design pattern:
Inbound Access Control
On-host firewall restricts external access to workstations and allows identified
programs to access appropriate server hosts and services
Endpoint I/O ports (e.g., USB ports) are controlled to block unauthorized
devices and removable media
Outbound Access Control
Firewall allows only authorized outbound interactions based on process identity,
server identity, service request and detected host compromise status
In VDI design patterns, the end-user workstation is restricted to using only
remote desktop protocol access into the VDI. The VDI is allowed to access
authorized services while preventing lateral attacks from within the cloud
Pre-infection Threat Prevention
Scanning of inbound interactions to search for exploits and malware
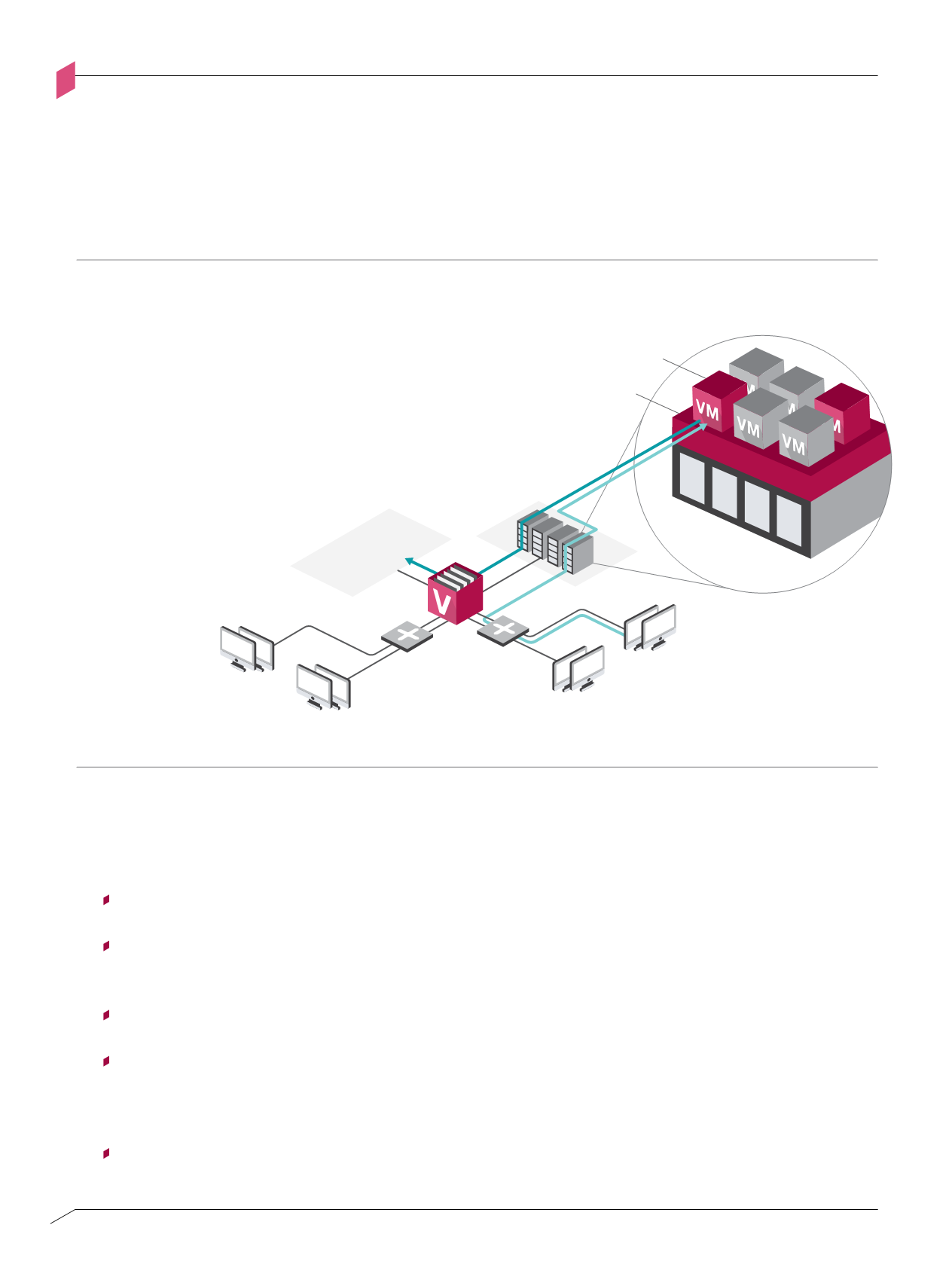
Access Network design pattern –
Virtual Hosted Desktops
Figure A-I
between the end-user workstation and the VDI, as well as to the access from each VDI to the
servers in the data center. Each virtual machine also runs host security software that provides
fine-grained control and supports containment of the individual VDI in case of detected non-
compliance or compromise
Figure A-i: Access Network design pattern –Virtual Desktop Infrastructure
NETWORK
003
DATA
CENTER
CLIENT/SERVER
PROTOCOLS
NETWORK
001
NETWORK
002
NETWORK
004
RDP
VM-LEVEL
ENFORCEMENT POINT
HYPERVISOR-LEVEL
ENFORCEMENT POINT
HYPERVISOR


