062
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
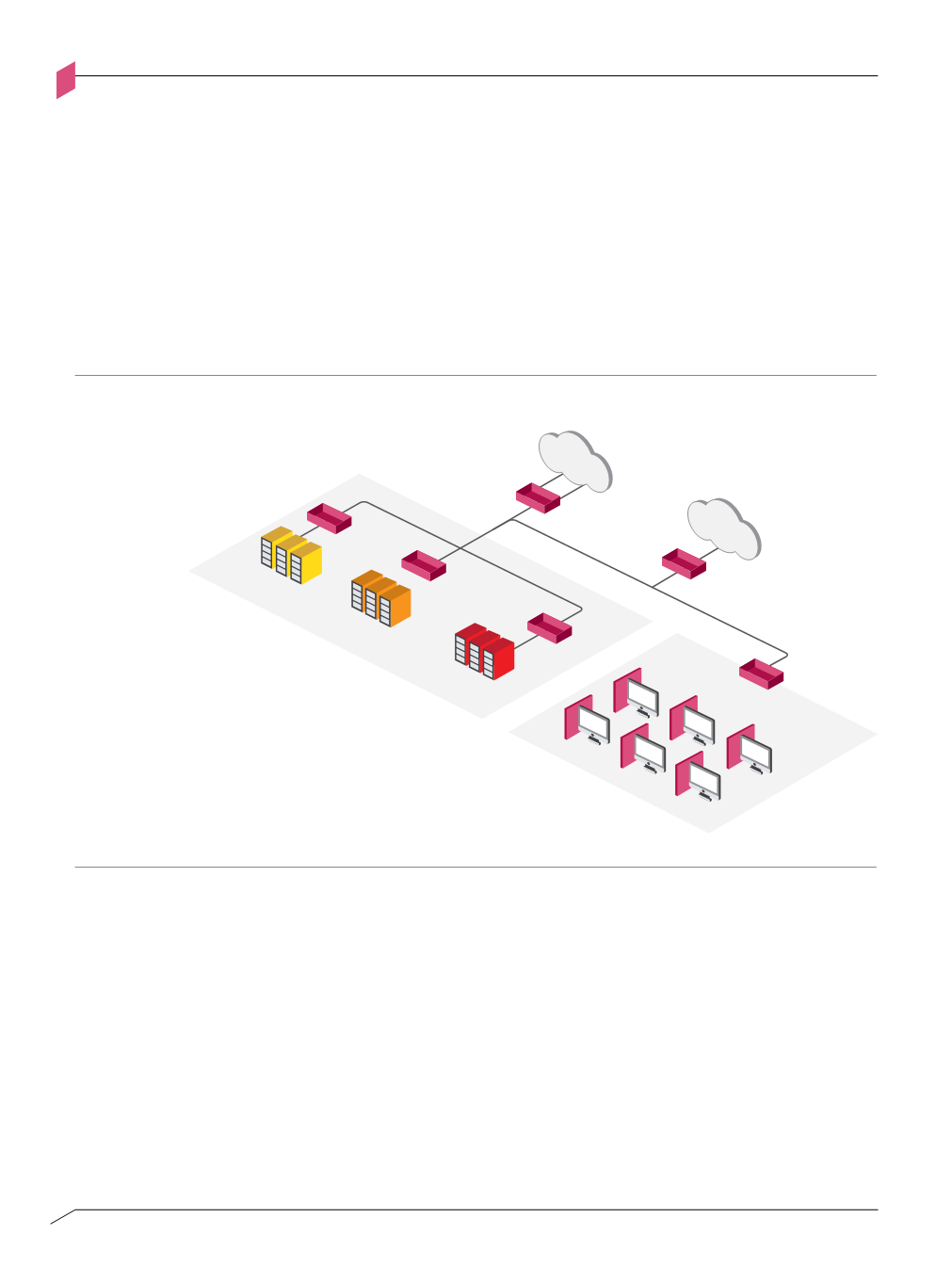
Shared Access Network
In a Shared Access Network configuration, all end-user workstations at a given location are
connected to a shared network infrastructure. Access to internal and external services is
controlled at the data center or at Internet access segment boundaries, and is determined in
relation to the host and/or user identity rather than the network segment.
Under this scenario, any compromised user workstation could potentially infect all other users.
It is therefore recommended that each workstation be defined as an atomic segment, with an
on-host security software enforcement point.
Access Network design
pattern – Shared
Access Network
Figure A-G
Figure A-g: Access Network design pattern – Shared Access Network
DATA CENTER
INTERNAL
SERVERS
PRODUCTION
SERVERS
SENSITIVE
SERVERS
LAN
MPLS
INTERNET


