072
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
2.
Authentication and authorization to connect from the control plane
3.
Security audit records forwarded to a monitoring system on the control plane
The Network Infrastructure should be segmented in order to manage the risk of network
element compromise. This is especially true where the network elements provide network
virtualization (see Virtual LANs and Software-defined Networking (SDN)). For example,
security-critical segments should have physically independent switches that are not shared
with other segments showing a significant security profile differential
Network management applications should be grouped into segments that are protected
using boundary controls from other segments
Use Server and Access Network segment boundary controls to enforce Least Privilege on
network traffic flowing through the inter-segment Network Infrastructure. For example,
end-user workstations should be prevented from attempting to tamper with or bypass a
network switch. Unauthorized route injection should be blocked at segment boundaries
It is a recommended practice to create an independent protected segment for the Network
Operations Center (NOC) to enable continued operations even while under attack. This
can be achieved by using out-of-band networking or by using QoS controls to allocate
minimum bandwidth for security monitoring controls
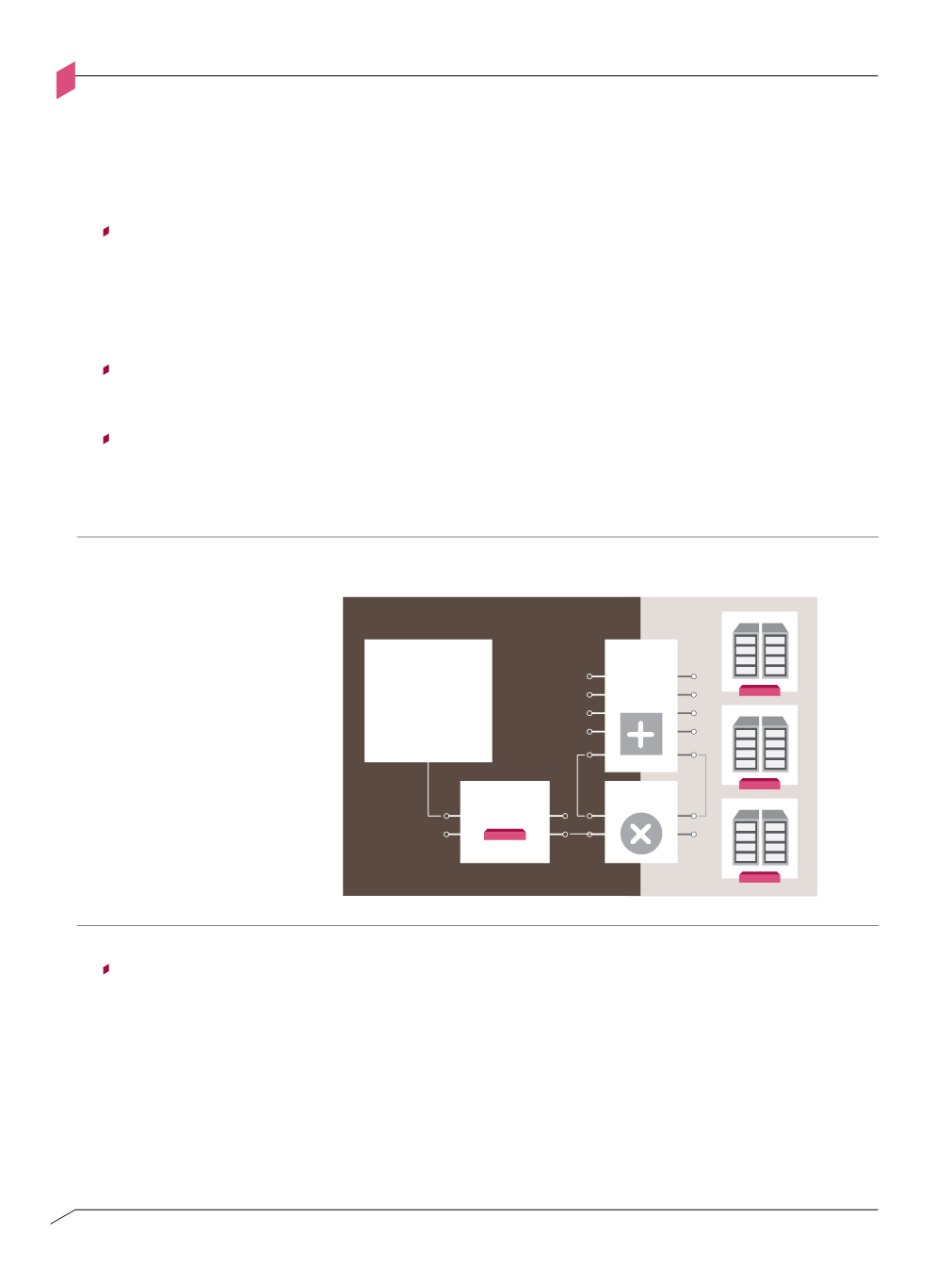
Network Infrastructure
design pattern
Figure A-
P
Figure A-p: Network Infrastructure design pattern
Data Plane
Control Plane
Switch
Router
Network
Management
Applications
Security
Gateway


