070
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
Segmentation
Mobile devices are considered atomic segments and must be protected using on-device
software. The device connects over a trusted channel to a mobile access server hosted on a
DMZ segment within an enterprise-managed site (see Figure A-N) or a public cloud (see Figure
A-O). The mobile access server mediates access from the mobile device to the enterprise assets.
It also mediates the mobile device’s access to the Internet, providing the device with layered
protection.
At a minimum, data protection controls must be implemented on the device itself. This design
pattern allows offloading of network-related access control and threat prevention protections, as well
as security event storage, to the mobile access server or cloud-based enforcement points (see section
Offloading Security Processing to the Cloud), reducing the reliance on the device’s capabilities.
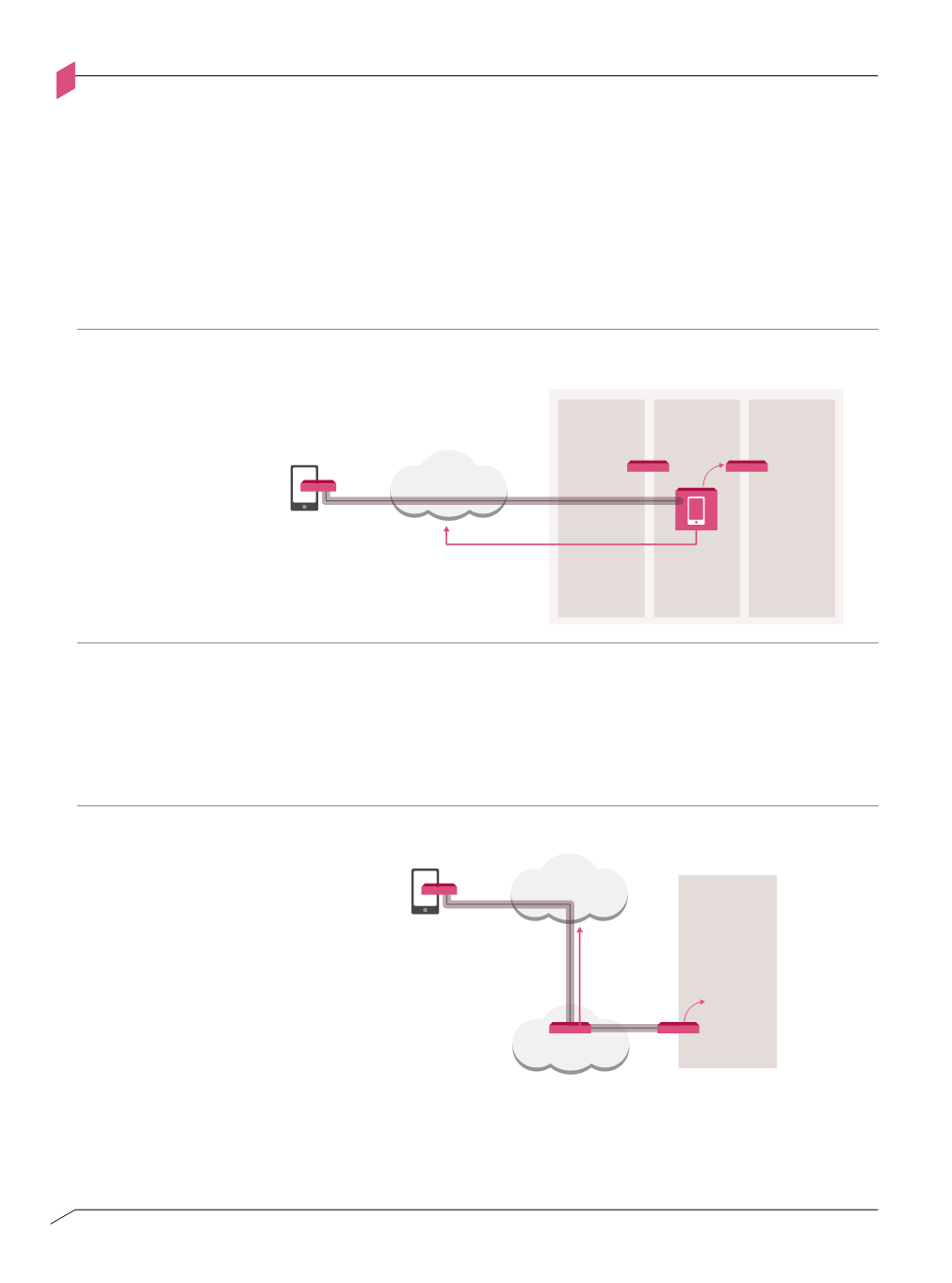
Mobile design pattern
Figure A-N
Mobile
Device
INTERNET
Data Center
Figure A-n: Mobile design pattern
TRUSTED CHANNEL
Internet
Access
DMZ Enterprise
Assets
Mobile
Access
Server
Mobile/Cloud design pattern
Figure A-O
Figure A-o: Mobile/cloud design pattern
Mobile
Device
INTERNET
CLOUD
Enterprise
Assets


