063
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
Virtual Hosted Desktops
A Virtual Desktop Infrastructure (VDI) configuration runs end-user software on a virtual
machine in the data center. The end-user workstation provides the human interface only.
Communications between the workstation and the VDI are restricted to a remote desktop
protocol (RDP) such as Microsoft RDP or similar protocols. This approach partitions the
protection issue into two parts:
1.
The end-user workstation is deployed in either a Shared Access Network or Dedicated Access
Network configuration. It is restricted to connecting to the VDI environment via the RDP
2.
The VDI environment is implemented and secured as a private or public cloud environment
(see Cloud design pattern). Security controls are applied to the client/server interaction
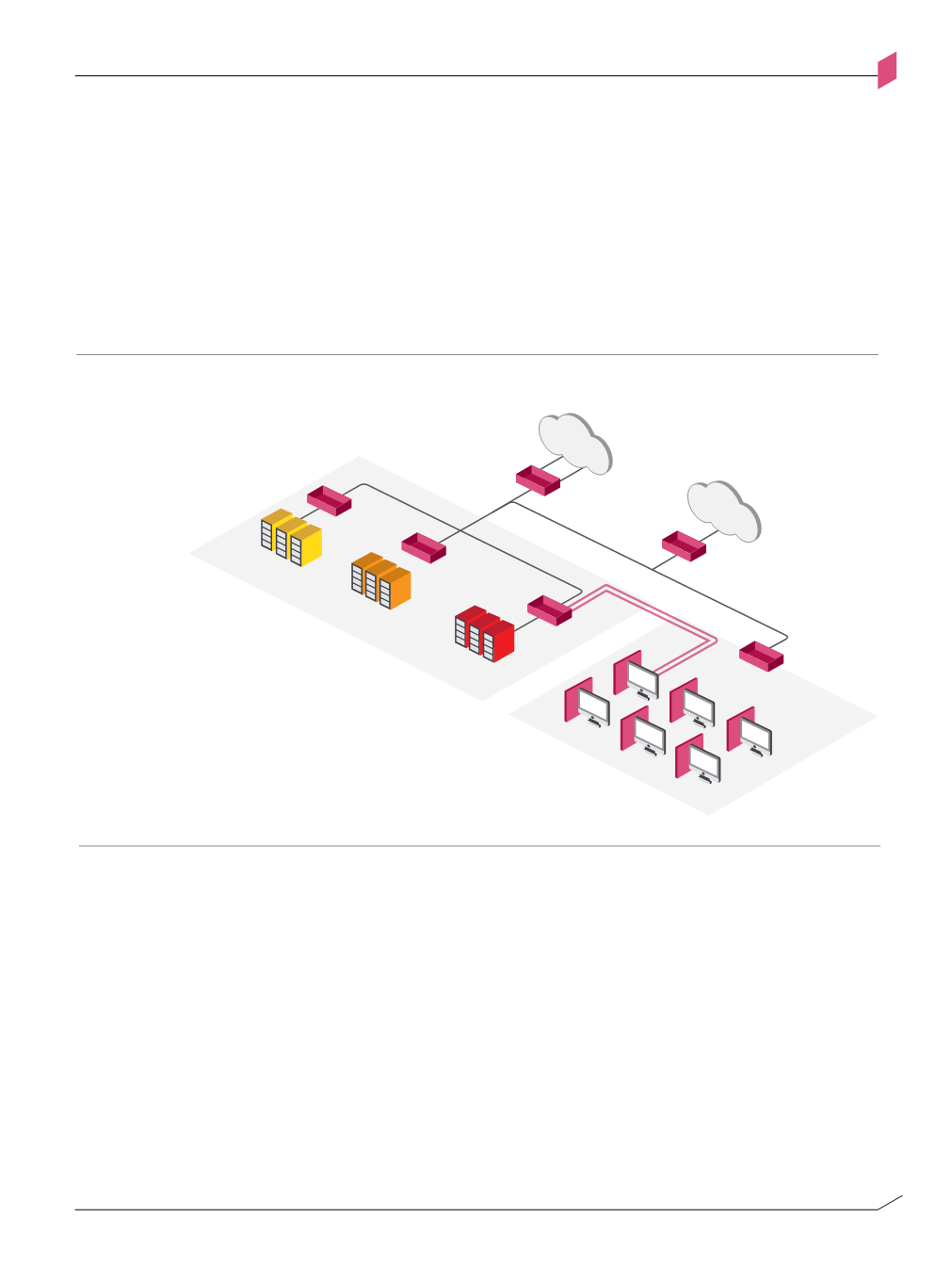
Access Network design pattern –
Virtually Dedicated Access Network
Figure A-H
Figure A-h: Access Network design pattern – Virtually Dedicated Access Network
DATA CENTER
PRODUCTION
SERVERS
SENSITIVE
SERVERS
LAN
MPLS
INTERNET
TRUSTED CHANNEL
INTERNAL
SERVERS
Virtually Dedicated Access Network
The Virtually Dedicated Access scenario is a hybrid of the Shared and Dedicated Access Network
design patterns. It is common when users are physically distributed throughout the organization
(Shared Access) but need to receive restricted access according to their function (Dedicated Access).
Each end-user host runs on-host security software that includes firewall and VPN controls at a
minimum. All interactions to and from the host are routed through VPN gateways that protect
specific server segments. Interactions outside of the authorized VPN communities are blocked.


