058
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
Design Pattern
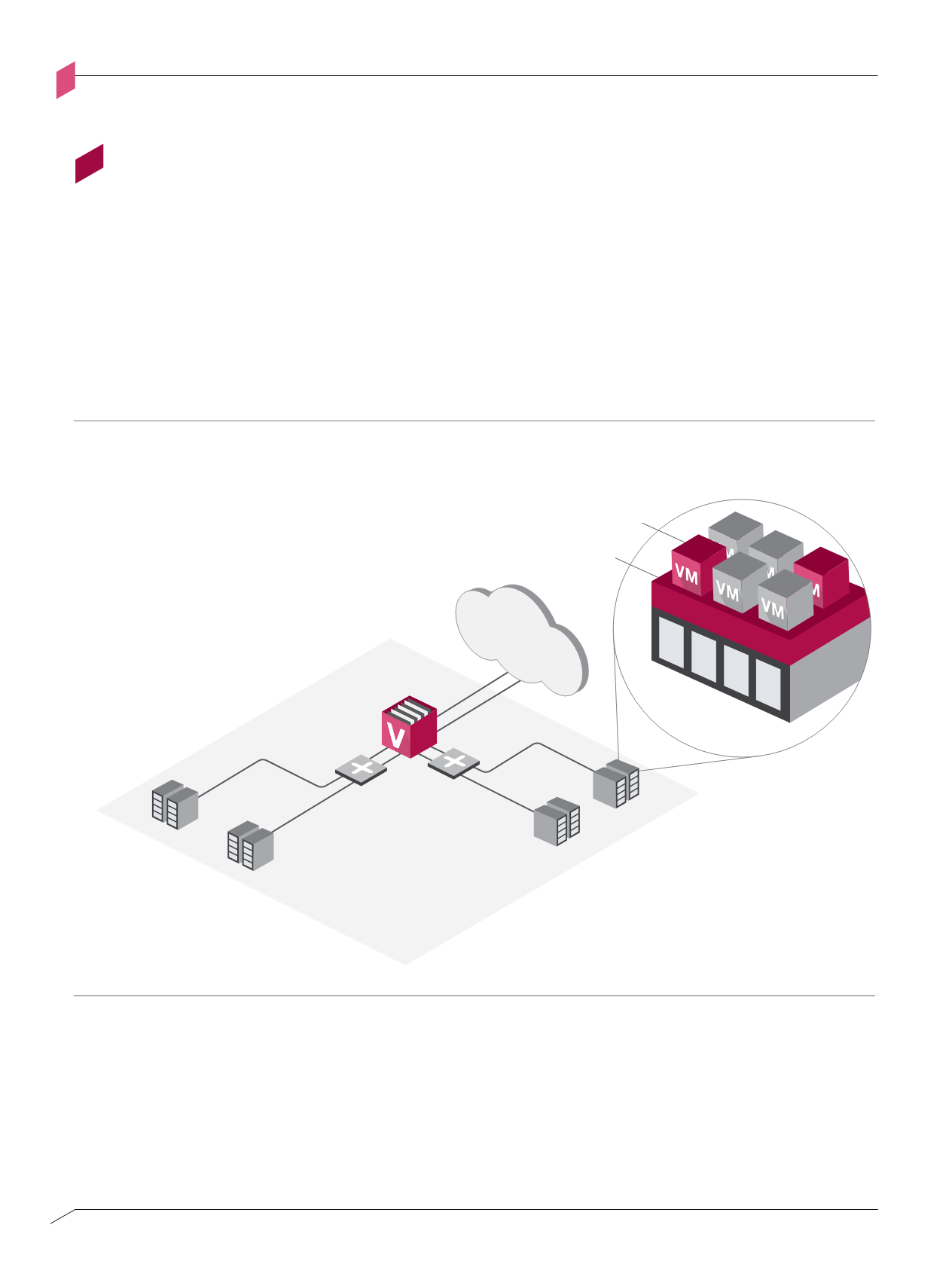
Cloud
Cloud computing is used to achieve economies of scale and to leverage corporate computing,
storage and networking resources. A cloud environment is composed of large numbers of
network-connected hosts that run virtual machine hypervisors. Hypervisors provide an
execution and virtual networking environment for multiple virtual machines.
Cloud computing may be provisioned for exclusive use by a single organization (private cloud),
or it may be operated by a third party servicing the general public or a specific user community
(public cloud). A private cloud may also be implemented as part of a servers segment or on
the Internet.
Cloud design pattern
Figure A-D
Figure A-d: Cloud design pattern
INTERNET
(PUBLIC CLOUD)
or WAN
(PRIVATE CLOUD)
VM-LEVEL
ENFORCEMENT POINT
HYPERVISOR-LEVEL
ENFORCEMENT POINT
HYPERVISOR


