050
ENTERPRISE SECURITY BLUEPRINT
CHECK-POINT SOFTWARE-DEFINED PROTECTION
CP
SDP
Next Generation Data Protection
Check Point Next Generation Data Protection adds data awareness. It includes our Data Loss
Prevention (DLP) software blade which performs content inspection and matches file contents
with files stored in enterprise repositories. Check Point DLP supports content inspection for
more than 800 file types and includes over 650 pre-defined content types. This makes it one of
the most comprehensive and efficient Data Loss solutions on the market.
In addition, Check Point provides Data Protection for data at rest and in storage with encryption
technologies. These technologies can be implemented on all enforcement points protecting
sensitive documents and confidential data from being accessed or transferred to removable
media or by unauthorized users.
Check Point SDP Management Layer
The Management Layer makes the Software-defined Protection architecture come alive.
By enabling each component of the architecture, this layer acts as the interface between
the security administrators and the other two SDP layers.
Check Point Modular / Layered Policy Management
All Check Point protections and enforcement points are managed from a single unified security
management console. Check Point security management is highly scalable, providing the ability
to manage tens of millions of objects while maintaining super-fast user interface response times.
The SDP Architecture requires the Management to support the enterprise segmentation,
allowing administrators to define security policy for each segment while enforcing segregation of
duties. Each administrator should be provided with a simple view of the security policies under
his responsibility for threat prevention, access control or data protection.
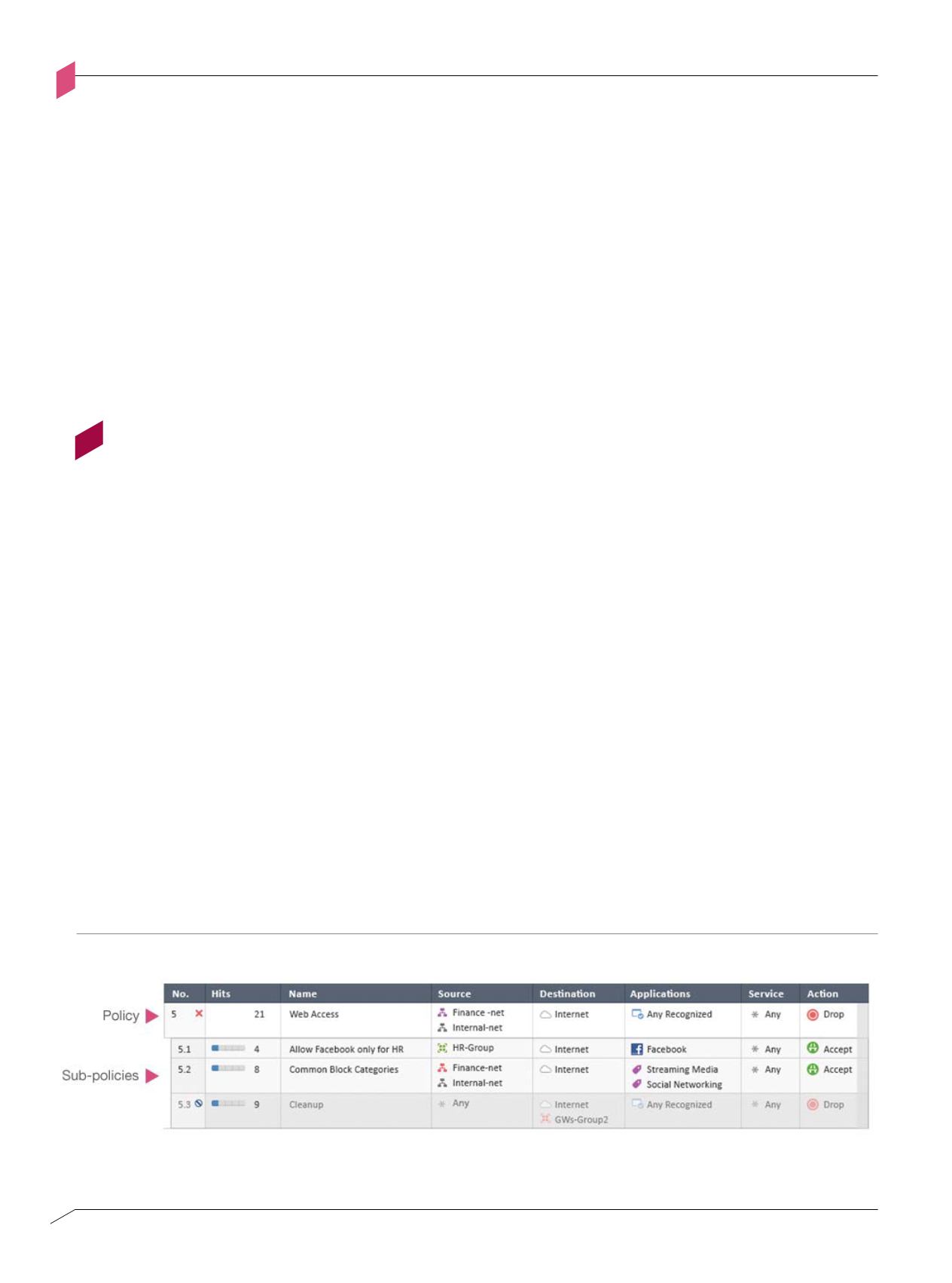
Check Point Security Management fulfills these SDP requirements with a new concept called
Layers and Sub Layers. Policies can be defined for each segment. Access control policies can
be defined using separate layers, which can be assigned to different administrators. Multiple
administrators can then work on the same policy simultaneously.
Sub-policies
Figure CPSDP-F


