057
ENTERPRISE SECURITY BLUEPRINT
APPENDIX
A
Data center design pattern –
servers segments
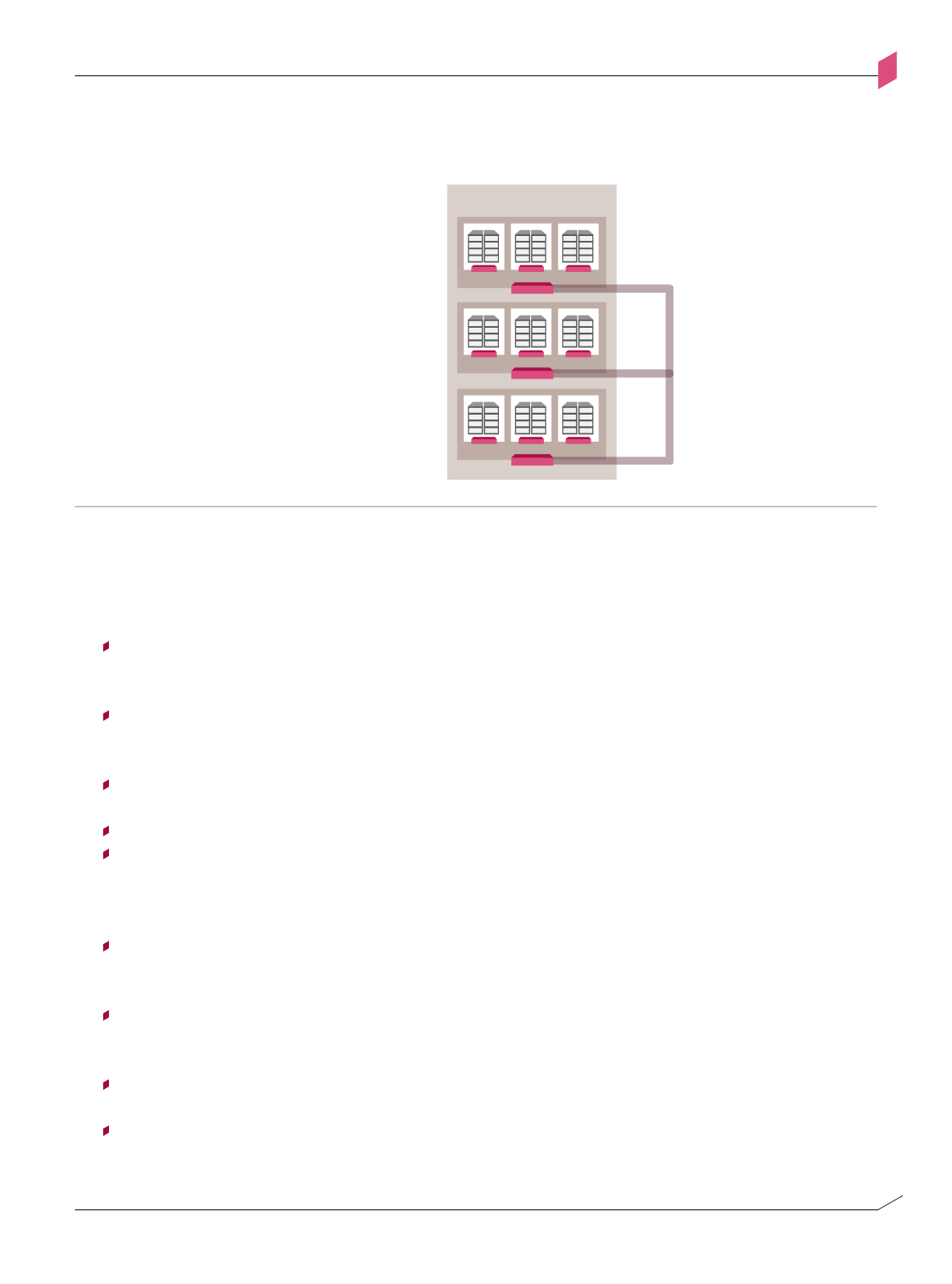
Figure A-C
Data Center
Figure A-c: Data center design pattern – servers segments
Servers
TRUSTED CHANNEL
Protections
The following protections are typical for the Servers design pattern:
Inbound Access Control
Performs client identification and authentication in support of the Access
Control rules at the security gateway or application-level security layers, based on
organizational identity management infrastructure
Enforces firewall security policy authorizations based on whether the external
client (e.g., user, host, program) is authorized to access the server (e.g., host, service,
application) according to client and server identities
Enforces application control policy authorizations based on whether client is
authorized for specific application-level requests (e.g., insert, delete, upload)
Enforces IPS protocol compliance checks for authorized interactions
Enforces Firewall protection of shared infrastructure (e.g., management servers,
network elements) from unauthorized access originating from outside of the servers
segments
Outbound Access Control
Firewall allows only authorized outbound interactions based on client and server
identities and service request
Pre-infection Threat Prevention
IPS blocks exploitation of known application vulnerabilities within the servers
segment boundary
Data Protection
Prevents leakage of sensitive information to unauthorized users, both external and
internal
Supports segmentation by establishing trusted channels with interacting segments
for distributed departmental server segments or the public cloud


