018
ENFORCEMENT LAYER
01
ENTERPRISE SECURITY BLUEPRINT
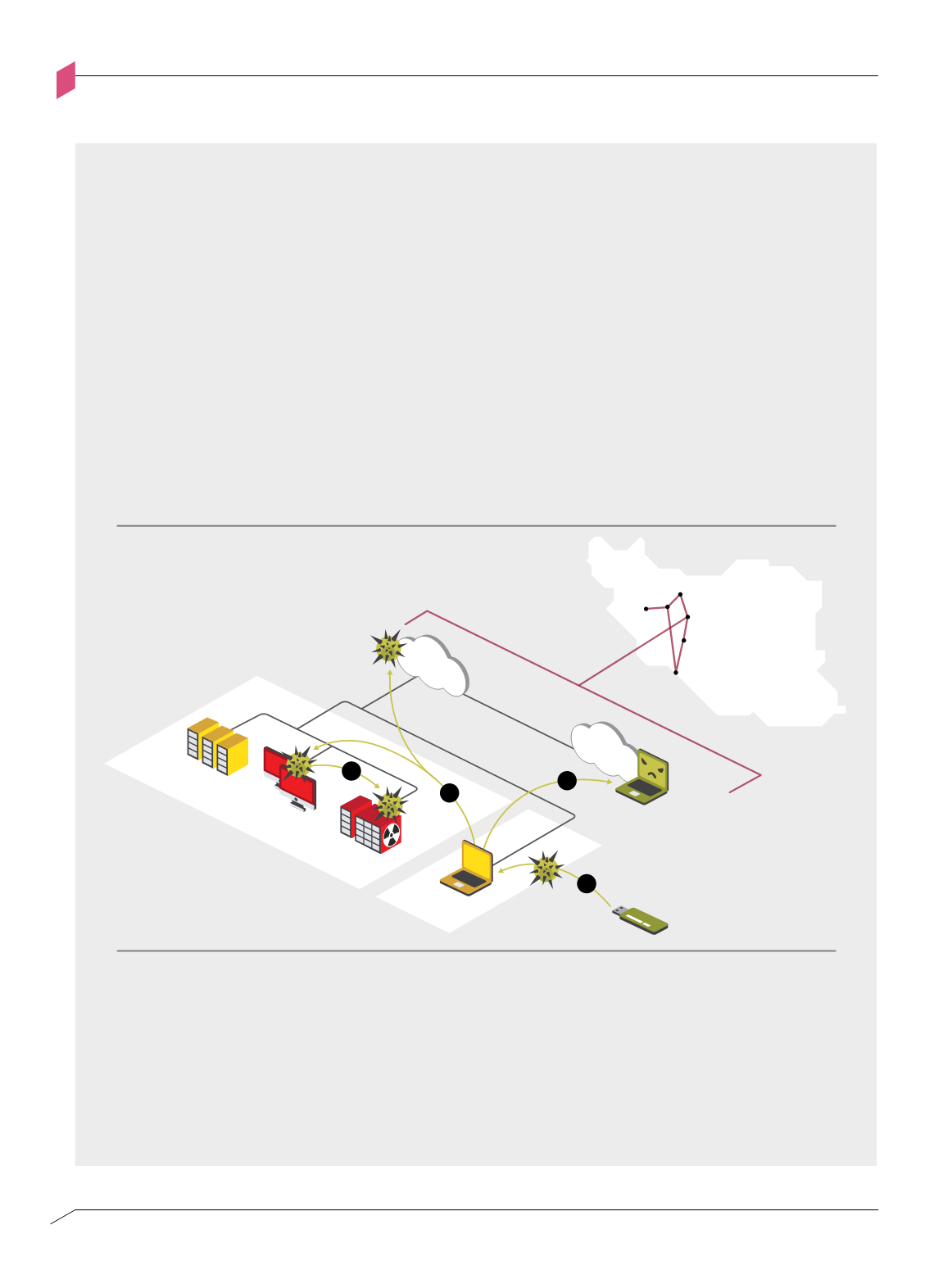
In June 2010, a new network worm was discovered that targeted the Siemens Supervisory Control and
Data Acquisition (SCADA) industrial control systems used in the Iranian nuclear program. According
to public sources, the worm damaged nuclear enrichment machinery, significantly impacting the
program’s objectives. This case study analyzes the worm’s characteristics and demonstrates a direct link
between its success and ineffective segmentation. Commonly named “Stuxnet,” the worm was a blended
threat that: (1) infected Windows-based workstations via USB flash drives, (2) spread across network
and removable media attack vectors, (3) allowed the infected host to connect to a Command and
Control (C&C) server to receive further commands and extract information, and (4) identified hosts
running SCADA control software and reprogrammed their Programmable Logic Controllers (PLCs) to
damage the centrifuges used for uranium enrichment.
Stuxnet used multiple deception techniques to conceal itself and to complicate eradication efforts. The
worm remained hidden for a number of years and spread via both known and previously unknown
vulnerabilities. Initially injected into an internal, trusted workstation, it spread laterally and infected over
60,000 hosts in Iran alone, reportedly damaging almost 1,000 centrifuges at the Natanz nuclear facility.
Recovery required months of intensive effort due to the worm’s aggressive reinfection behavior.
Stuxnet Case Study
How segmentation can prevent computer worms from spreading
Stuxnet
Figure 1-I
DATA CENTER
Figure 1-i: Stuxnet
INTERNAL
SERVERS
OPERATOR
PCS
PLC
SERVERS
LAN
C&C SERVERS
P2P
NETWORKING
INTERNET
WAN
1
2
3
4
Arak
Qom
Teheran
Natanz
Isfahan
Bushar
Iran


