015
ENTERPRISE SECURITY BLUEPRINT
ENFORCEMENT LAYER
01
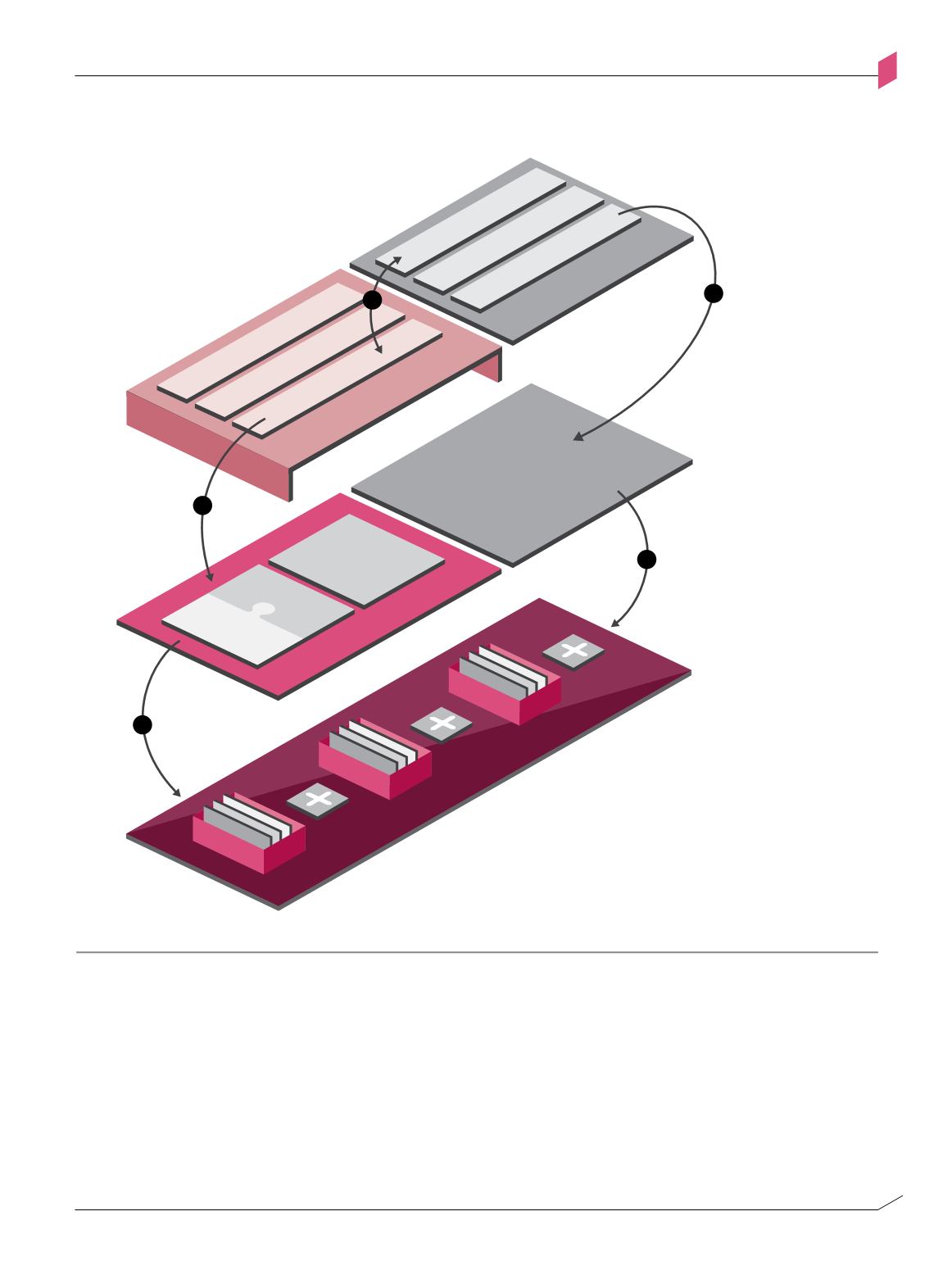
Figure 1-g: SDP/SDN integration
Enforcement Layer
Enforcement
Point
Enforcement
Point
Enforcement
Point
SDP Control Layer
SDN Controller
Access
Control
Data
Protection
Threat
Prevention
SDP Management Layer
Modularity
Visibility
Automation
Business Application
Business Application
Business Application
SDN Application Layer
1
3
3
2
2
SDP/SDN integration
Figure 1-G
For example, the SDN switches could be instructed to forward interactions between the LAN
segment and the Internal Servers through one security gateway enforcement point, whereas
interactions with the DMZ should be forwarded through another enforcement point that
implements an extended set of protections. As another example, Distributed Denial of Service
(DDoS) traffic, once identified, can be routed differently than legitimate traffic, allowing
authorized interactions to flow freely.


