010
ENFORCEMENT LAYER
01
ENTERPRISE SECURITY BLUEPRINT
Step 3: Enforcement Consolidation
From Model to Implementation
Once the segmentation model has been created, the defined enforcement points need to be
implemented as network security gateways or as host-based software. Consolidation and
virtualization technologies including multi-homed gateways, gateway virtualization, Virtual
Local Area Networks (VLANs), SDN and network virtualization can be used to achieve
optimal performance, manageability and cost of ownership.
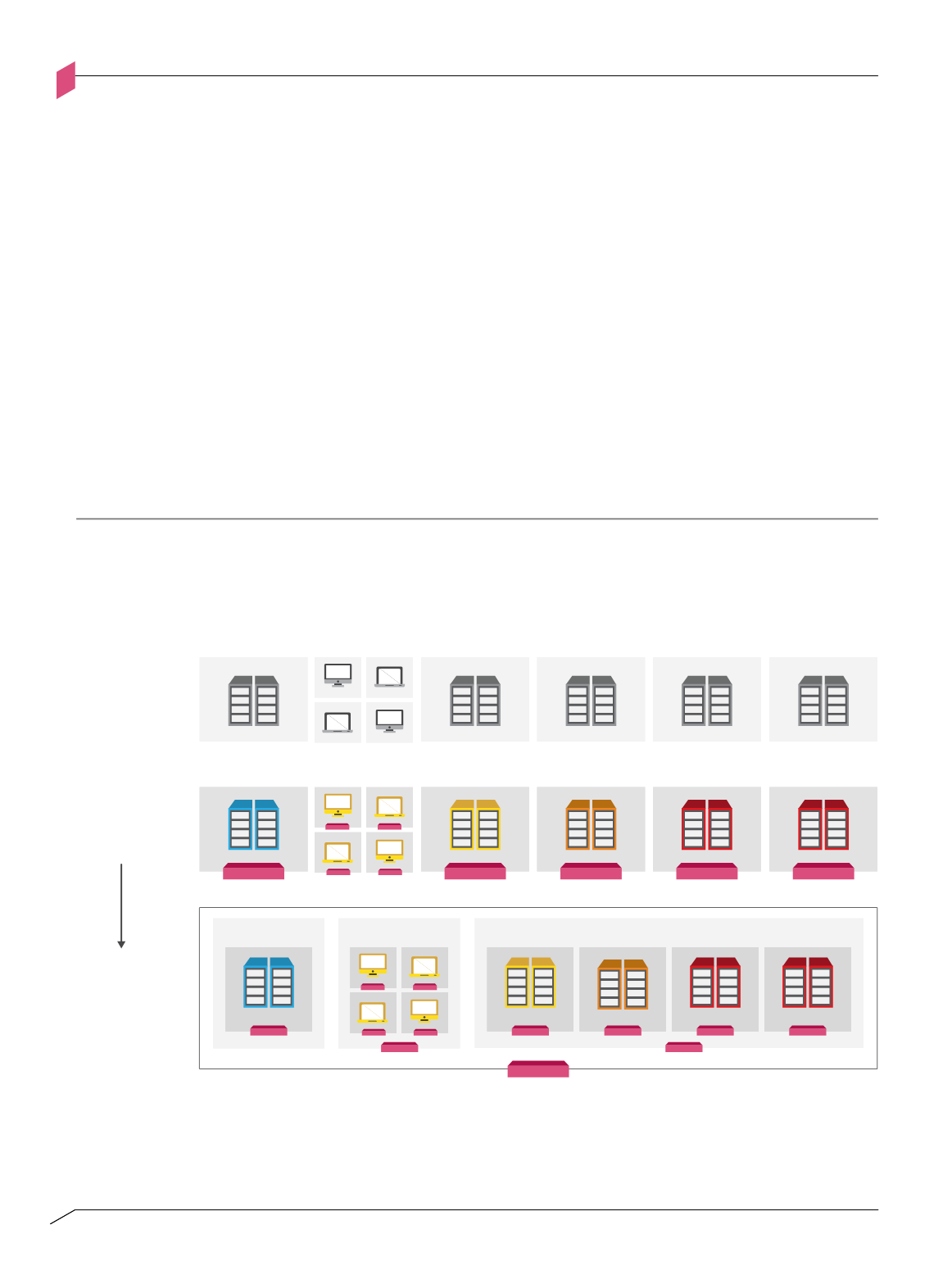
The segmentation modeling process (Figure 1-B) demonstrates segmentation for a sample
network comprising user workstations, servers (CRM, R&D and Finance), a Security
Operations Center (SOC) and external-facing servers on a DMZ segment. Security profiles
are associated with atomic segments (see “segment classification” legend in Figure 1-A).
Enforcement points are placed at the boundary of each segment. Segments are grouped
according to their security profiles.
Enterprise segmentation process
Figure 1-B
Figure 1-b: Enterprise segmentation process
Public
DMZ
Web
Servers
CRM
Servers
SOC
Servers
Finance
Servers
R&D
Servers
USERS
PCs/LAPTOPS
Internal
Internal
Departmental
DATA CENTER
Departmental
Sensitive
LAN USERS
1.
Atomic
Segments
2.
Segment
Grouping


