009
ENTERPRISE SECURITY BLUEPRINT
ENFORCEMENT LAYER
01
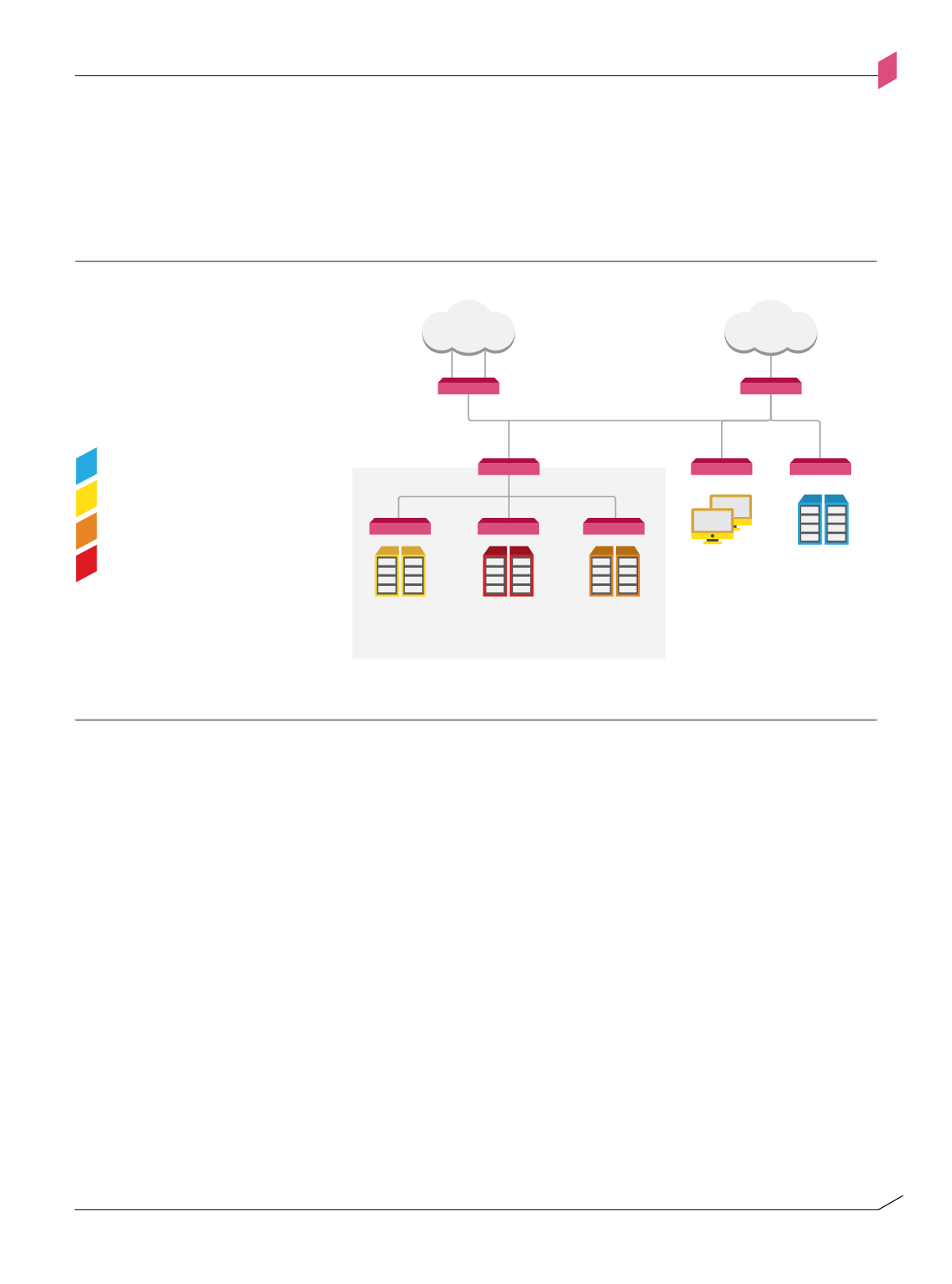
segments receive security services from a centralized system and network management
infrastructure within the server segments. Internet and WAN accesses are controlled by
dedicated enforcement points. The Internet enforcement point also controls access into
and out of the DMZ.
Within a hierarchical grouping, interactions may traverse multiple enforcement points.
For example, a server in the “Internal Servers” segment that connects to a resource on
the Internet (e.g., content update service) might be mediated by the following sequential
enforcement points:
1.
Security software installed on “Internal Servers” segment hosts
2.
“Internal Servers” segment boundary enforcement point
3.
Enforcement point located on the boundary of the Data Center
4.
Internet-facing enforcement point
Interactions through proxies located on the DMZ segment would traverse additional control
paths including the DMZ segment enforcement point into and out of the DMZ segment.
By repeating the process of grouping segments on consecutively larger parts of the
network, enterprises can ensure all assets have been included in a protected segment. The
hierarchical lines of defense established according to grouping segments compartmentalize
the internal network and provide superior protection.
Segment grouping
Figure 1-A
Figure 1-a: Segment grouping
Public
Internal
Sensitive
Departmental
Segment
Classification
INTERNET
Enforcement
Point
Enforcement
Point
LAN
DMZ
DATA CENTER
MPLS
DEPARTMENTAL
SERVERS
SENSITIVE
SERVERS
INTERNAL
SERVERS
Figu e 1-a: Segme t grouping
Public
Internal
Sensitive
Departmental
Segment
Classification
INTERNET
Enforcement
Point
Enforcement
Point
LAN
DMZ
DATA CENTER
MPLS
DEPARTMENTAL
SERVERS
SENSITIVE
SERVERS
INTERNAL
SERVERS


