017
ENTERPRISE SECURITY BLUEPRINT
ENFORCEMENT LAYER
01
Step 4: Trusted Channels
Segment enforcement points prevent unauthorized inter-segment interactions. However,
authorized interactions must also be protected. When two network segments have co-located
elements, a security gateway can be physically connected to both segments in order to mediate
inter-segment interactions. When they are physically separated, such interactions must be
secured while they travel through the network infrastructure.
If interactions between segments are established by a hierarchical segment within a trusted
network, then the hierarchical segment is responsible for securing the data in transit. However,
if the network is “untrusted” relative to the security profiles of the two segments, attackers
could access or modify data flowing between the two segments. Therefore, a trusted channel
should be established between the segments and should use encryption for inter-segment
interactions. Such a channel would prevent unauthorized access to any data traveling through
it, while also detecting and blocking any information modification attempts.
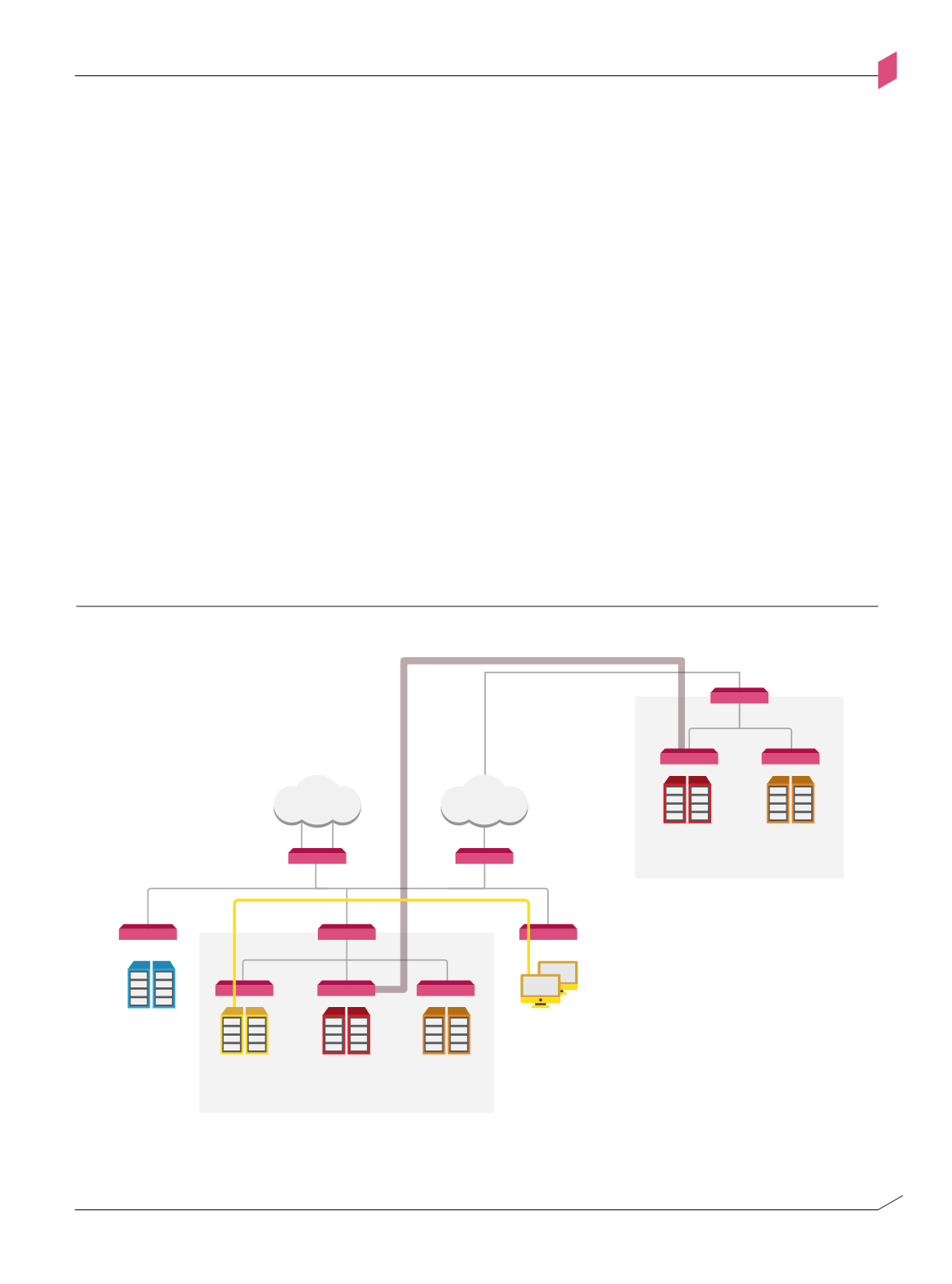
The following example depicts two departmental segments located at different sites and
interacting over a trusted channel. In this example, internal users can access internal
servers directly.
Figure 1-h: Encrypted trusted channel between two segments
DATA CENTER
TRUSTED CHANNEL
LAN
MPLS
DATA CENTER
INTERNET
DEPARTMENTAL
SERVERS
SENSITIVE
SERVERS
INTERNAL
SERVERS
DEPARTMENTAL
SERVERS
SENSITIVE
SERVERS
DMZ
Enforcement
Point
Enforcement
Point
Encrypted trusted channel
between two segments
Figure 1-H
A trusted
channel should
be established
between
segments
to secure
interactions
over untrusted
networks


