011
ENTERPRISE SECURITY BLUEPRINT
ENFORCEMENT LAYER
01
Multiple modeled
enforcement
points can be
consolidated
into a single
security gateway
appliance
This bottom-up modeling process provides the flexibility and modularity necessary to
determine required enforcement points for anything from a single business application to
an entire organization. Security engineers determine where to start (e.g., process, host and
network) and where to stop. The enforcement points will then establish hierarchical lines
of defense that provide protections for data and systems hosted within the corresponding
segment boundaries.
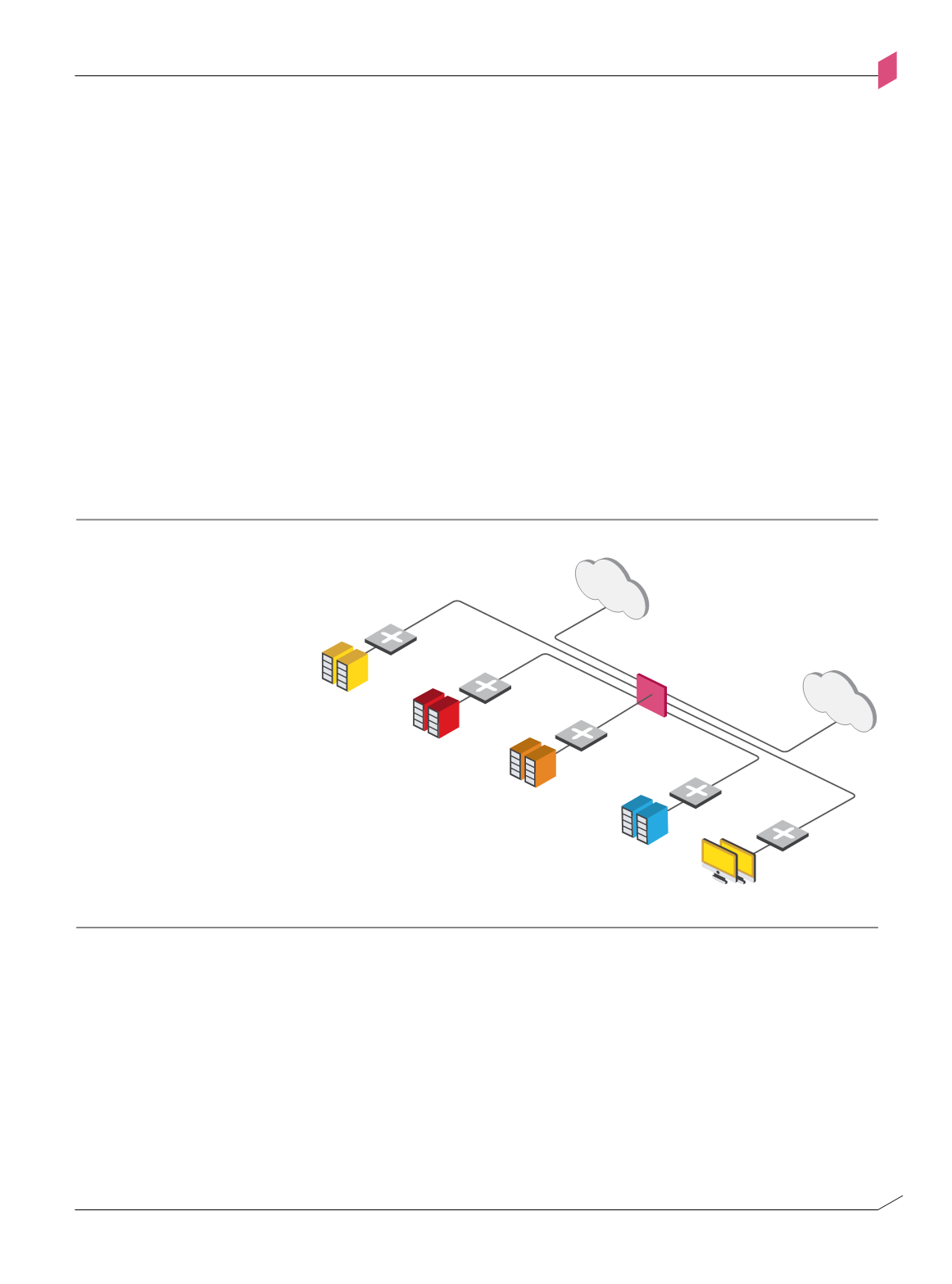
Gateway Consolidation
Whereas the model in Figure 1-A depicts eight different network segment boundary
enforcement points (not including the host-based security software enforcement points
in the LAN segment), the implementation would not typically reflect eight security
gateway appliances. Depending on security, financial and performance constraints, multiple
enforcement points can be consolidated into a single multi-homed security gateway
appliance within each site. Figure 1-C presents a simple configuration of a unified security
gateway used to control all inter-segment interactions.
Figure 1-c: A single security gateway consolidates enforcement points for multiple segments
DMZ
LAN
SENSITIVE
SERVERS
INTERNAL
SERVERS
SECURITY
GATEWAY
INTERNET
MPLS
DEPARTMENTAL
SERVERS
A single security gateway
consolidates enforcement points
for multiple segments
Figure 1-C


