028
ENTERPRISE SECURITY BLUEPRINT
CONTROL LAYER
02
Risks may be considered at a high level as described above or may be detailed in relation
to potential attack methods. A set of security controls is defined to mitigate each risk,
reducing exposure to a level that is acceptable to the enterprise.
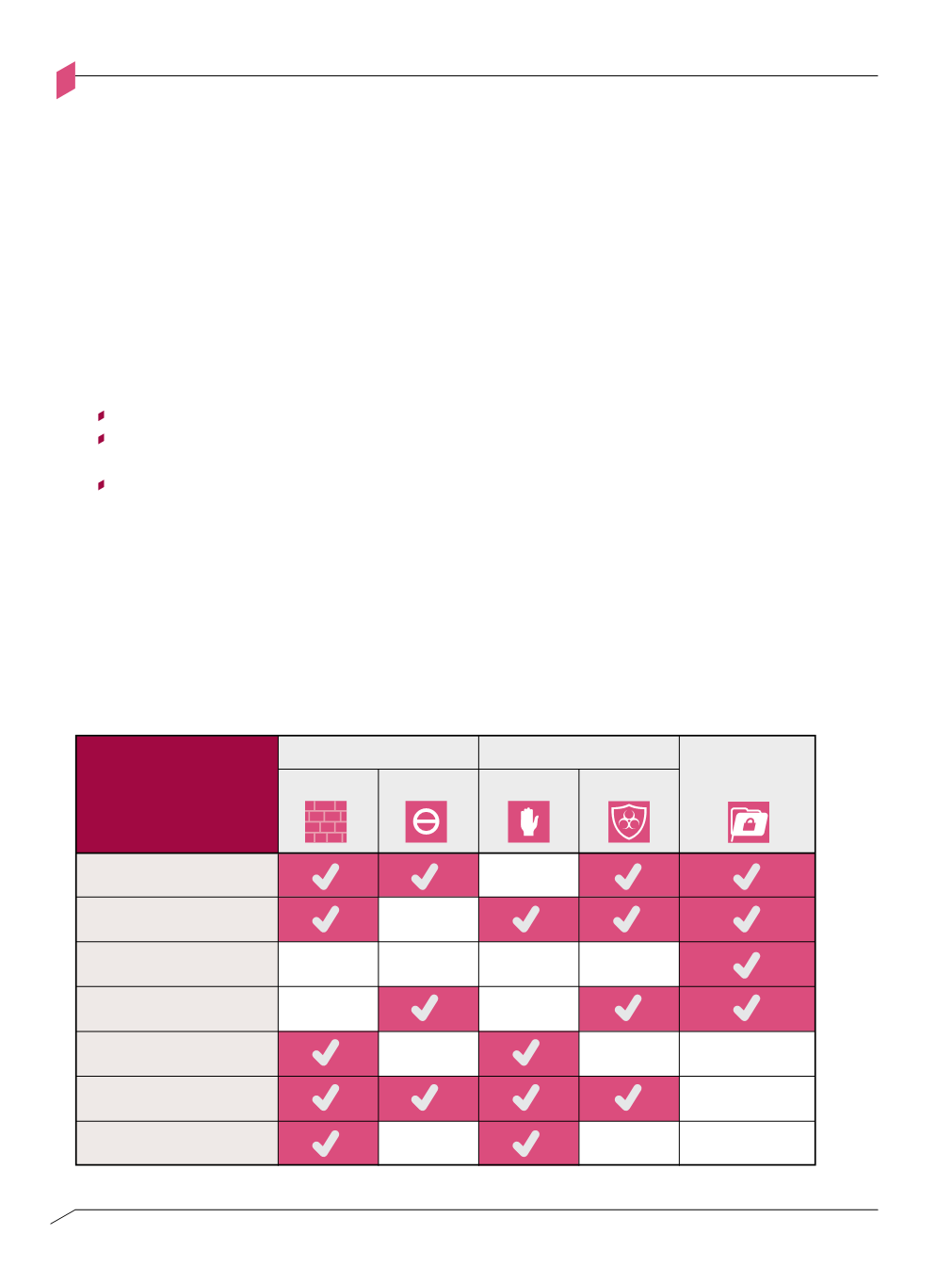
A simplified view of mapping risks to protections can be seen in Figure 2-C below. Each
row describes a high-level risk or detailed attack method (e.g., malware-delivered-as-a-link-
in-an-email); each column identifies a mitigating protection package (e.g., pre-infection
threat prevention) or specific protection (e.g., reputation-based filtering for URLs).
Mapping protections to risks can help:
To ensure that all risks are sufficiently mitigated
To determine which enforcement points should apply which security control
when considering interactions that go through multiple enforcement points
To identify residual risk and adjust security controls when a given control
proves to be ineffective, too expensive or requires excessive resources
As described in the "Step 2 - Segment Grouping" section, hierarchical grouping implies that a
single interaction may traverse multiple enforcement points. This means that controls should
be applied at multiple points along the interaction path in order to mitigate corresponding
risks. For example, anti-malware controls that match incoming email messages against known
malware signatures can be applied at a security gateway enforcement point into a DMZ hosting
the mail relay, on the mail relay itself, on the internal mail server or on the client host.
Hierarchical
grouping implies
that a single
interaction may
traverse multiple
enforcement
points
Risk
Insider
Data access
Exploit
External attack
Data leakage
Malware
Denial of service
ACCESS CONTROL
Outbound
THREAT PREVENTION
Pre-
Post-
DATA
PROTECTION
Inbound
Mapping security controls to risks
Figure 2-C


