031
ENTERPRISE SECURITY BLUEPRINT
CONTROL LAYER
02
On March 17, 2011, computer security vendor RSA announced that its network had been hacked
through an APT, and that the hackers had stolen confidential data related to RSA’s SecurID
authentication token. By June 2011, after several successful follow-on customer attacks, RSA was forced to
field-replace 40 million SecurID tokens. The attack cost RSA millions of dollars, as well as a tremendous
loss of reputation.
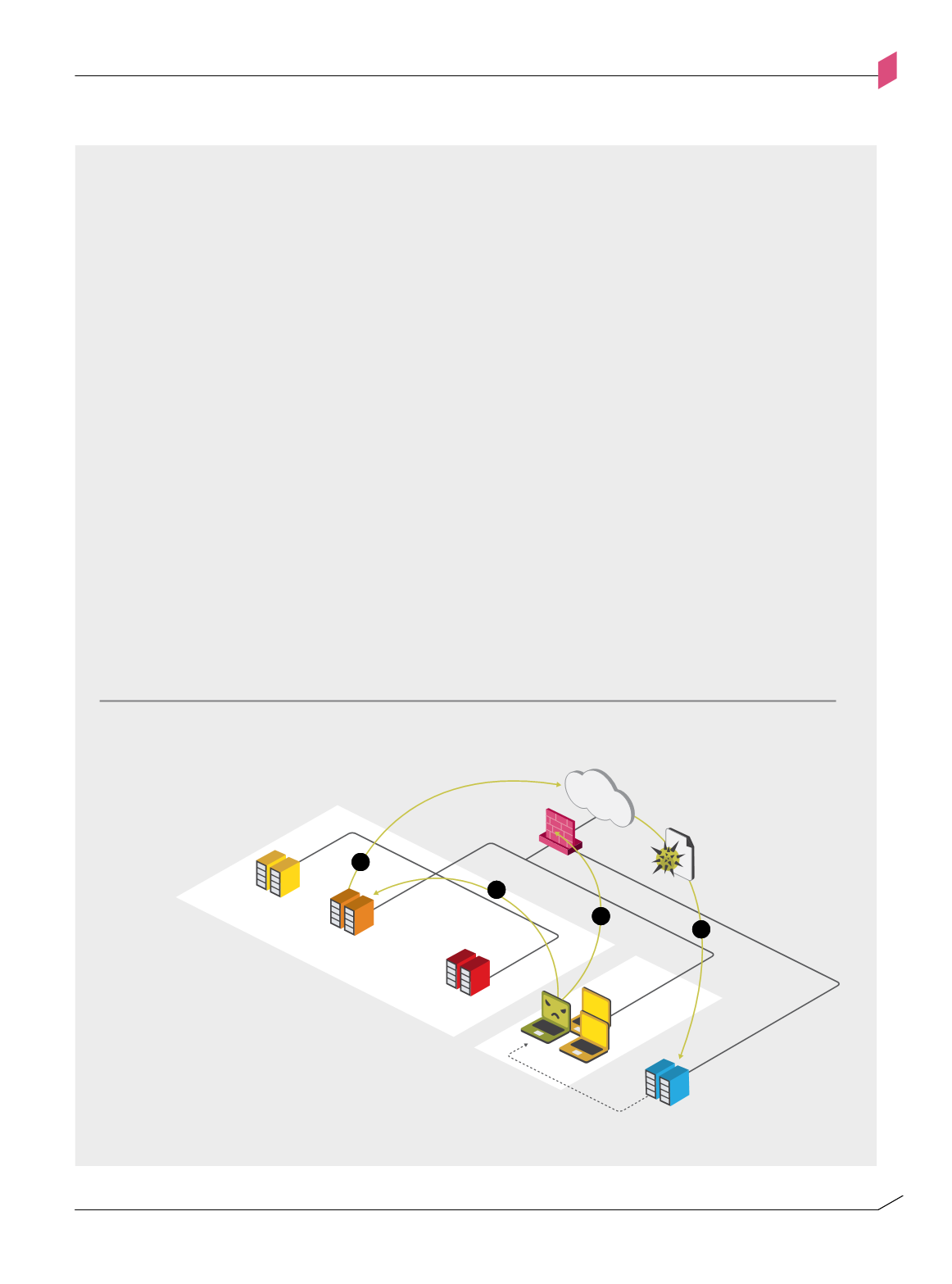
The attack sequence was as follows: (1) two different targeted phishing emails were sent to two
small groups of employees. The emails were titled “2011 Recruitment Plan”; (2) one employee was
tricked into opening the email. The message included an Excel spreadsheet attachment containing an
Adobe Flash zero-day exploit that installed a Poison Ivy variant – a Remote Access Tool (RAT). The
malware connected to a C&C server and provided the attackers with entry to the RSA network; (3)
the attackers moved laterally within the RSA network, harvesting user credentials until they obtained
privileged access; (4) RSA SecurID data was stolen and extracted to a drop zone for the attacker to
retrieve later.
Figures 2-E and 2-F use this case study to demonstrate how security control selection can counter
multi-vector attacks.
RSA Case Study
Anatomy of an Advanced Persistent Threat (APT) attack
RSA attack
Figure 2-E
Figure 2-e: RSA attack
DATA CENTER
DMZ
LAN
DEPARTMENTAL
SERVERS
SENSITIVE
SERVERS
INTERNAL
SERVERS
1
4
INTERNET
3
2


