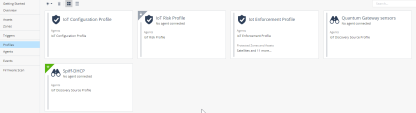
Profiles
Quantum IoT Protect automatically creates a profile for the gateway that is connected to the IoT assets in your network. A profile shows the source and the technologies used to discover IoT assets, and the Quantum Security Gateways that function as sensors.
When you complete onboarding IoT assets, Quantum IoT Protect creates these profiles by default:
-
Enforcement Profile
-
IoT Risk Profile
-
IoT Configuration Profile
-
Quantum Gateway Sensor Profile (with Security Gateway Sensor as Discovery source type)
The Profiles page shows the default profiles and profiles that you manually create. Spiff-DHCP is an example of a manually created profile.
Enforcement Profile
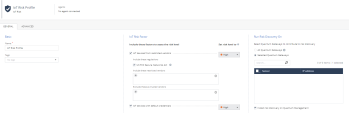
The Enforcement profile (or IoT Enforcement profile) maps the IoT policy to the Assets and Zones discovered in other profiles, for enforcement on Security Gateway(s).
|
|
Note - Assets and Zones are tied to the Enforcement profile when they are discovered by other profile(s). |
You can select the policy package and the Security Gateway(s) in the profile configuration settings explained below.
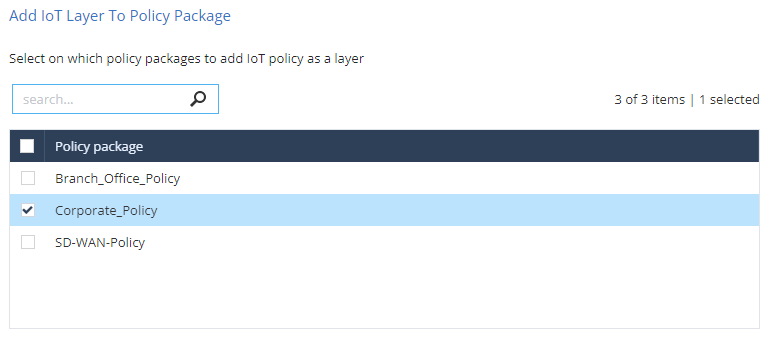
Add IoT Layer To Policy Package
Select a policy package to enforce on the onboarded IoT assets.
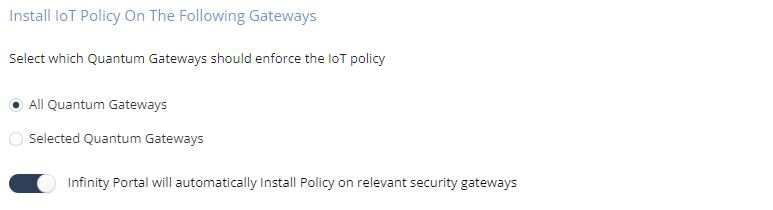
Install IoT Policy on the Following Gateways
Select the gateway to install the policy package. The Infinity Portal will automatically install policy on relevant security gateways option is enabled by default.
IoT Risk Profile
IoT Risk Profile shows the different factors that are considered to evaluate the risk of IoT assets and allows you to set a risk level for these factors. You can view the risk value of assets in the Assets page.
IoT Risk Factor
The risk level of an IoT asset is assessed based on the risk values set for these factors:
Restricted Vendors
You can define the list of restricted IoT vendors and set a risk level. When a restricted IoT vendor is detected, the system applies the set risk level and enforces the responsive action configured in Infinity Playblocks or Threat Prevention.
To define the list of restricted IoT vendors and set a risk level:
-
Select the IoT devices from restricted vendors option and set one of these risk levels:
-
(Recommended) High
-
Critical
-
Medium
-
Low
-
-
To include vendors restricted by the US FCC Secure Network Act to the restricted vendors list, select the US FCC Secure Networks Act option.
The restricted vendors are:
-
Huawei
-
ZTE
-
Hytera
-
Hikvision
-
Dahua
-
-
To add a vendor to the restricted list:
-
In the Include these restricted vendors section, click +.
-
Select the vendors that you want to add to the restricted vendors list.
-
Click OK.
-
Click Enforce.
The vendor is now considered as a restricted vendor and the assets from this vendor will be set with risk level.
-
-
To remove a vendor from restricted list:
-
In the Exclude these as trusted vendors section, click +.
-
Select the vendors that you want to exclude from the restricted list.
-
Click OK.
-
Click Enforce.
The vendor is now considered as a trusted vendor and the assets from this vendor are not assigned any risk level.
-
Default Credentials
You can set a risk level for IoT assets that use commonly exploited login credentials or use default credentials supplied by the manufacturer.
Check Point maintains an up-to-date database of commonly exploited login credentials and the default credentials supplied by the manufacturer. It attempts to log in to the IoT assets using these credentials through protocols, such as SSH, Telnet, FTP and so on. A successful attempt implies a significant risk of compromise and allows you to set a risk level for such IoT assets.
To assign a risk level, select the IoT devices with default credentials option and set one of these risk levels:
-
(Recommended) High
-
Critical
-
Medium
-
Low
Run Risk Discovery On
Shows the Quantum Security Gateways used to discover IoT assets with risk.
To run risk discovery on Quantum Management Server, select the Install risk discovery on Quantum Management option.
|
|
Note - Risk Discovery is not supported on VSX Gateways. |
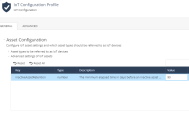
IoT Configuration Profile
The IoT Configuration Profile shows the asset types that should be discovered as IoT assets, advanced configuration, and default settings for zones.
-
Asset Configuration:
-
Collector Configuration:
Shows settings for the IoT discovery engines.
-
Zone Matcher Configuration:
Shows settings for the IoT zones.
|
|
Note - We recommend not to modify these settings. If you want to modify, contact Check Point Support. |
IoT Discovery Profile
-
Discovery Source - Shows the discovery source name and source type.
-
Discovery Source Settings - Shows the technologies used to discover IoT assets.
-
Active Probing - See Active Probing
-
Run Discovery On - Shows the Quantum Security Gateways used to discover IoT assets.
Profiles for Advanced IoT Discovery Engines
You can manually create a profile if you want to use a different discovery source type. For more information, see: