Using Cisco ISE as Discovery Source
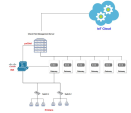
You can set up an IoT discovery engine on the Check Point Security Gateway or Management Server to discover IoT assets in your network. The IoT discovery engine uses the network devices in the network, such as switches, routers, gateways, or Network Access Control (NAC) devices to discover IoT assets.
You can use Cisco Identity Services Engine (ISE) as an IoT discovery engine. It is a NAC device that:
-
Allows organizations to provide highly secure network access to users and devices.
-
Uses a proprietary WebSocket-based protocol called Platform Exchange Grid (pxGrid) to share vital contextual data with integrated solutions. For pxGrid-related REST and WebSocket communication, pxGrid uses port 8910 over TCP on Cisco ISE.
-
Subscribes to Cisco ISE's session events. With this subscription, Quantum IoT Protect is notified of any event in which a network device is authenticated by Cisco ISE. The notification includes the MAC address and IP address of the device.
This network diagram shows the setup to use Cisco ISE as the IoT discovery engine.
|
|
Note - Quantum IoT Protect integration with Cisco ISE is based on pxGrid - Platform Exchange Grid 2.0, which is officially supported starting from ISE 2.4. The procedures described in this document are tested on Cisco ISE versions 2.6 and 2.7.0.356, on a virtual machine. |
Prerequisites
- Set the relevant rules in the Access Control policy to allow pxGrid traffic between the Check Point Management Server and the Cisco ISE server.
-
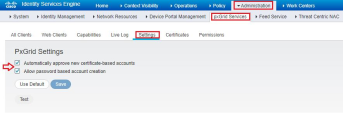
Configure pxGrid services on Cisco ISE:
Setting Up Cisco ISE as the IoT Discovery Engine
To set up Cisco ISE as the IoT Discovery Engine:
-
Log in to Cisco ISE Web Management portal.
-
Go to Administration > pxGrid Services > Certificates.
-
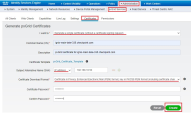
Enter these:
-
I want to - Select Generate a single certificate (without a certificate signing request).
-
Common name (CN) - FQDN [Host.Domain] of the pxGrid client, the subscriber of Cisco ISE server's sessions (the Management Server on which the integration is installed).
-
Subject Alternative Name (SAN) - Select IP Address and enter the IP Address of the pxGrid client, the subscriber of the Cisco ISE server's sessions (the Management Server on which the integration is installed).
-
Certificate Download Format - Select Certificate in Privacy Enhanced Electronic Mail (PEM) format, key in PKCS8 PEM format (including certificate chain).
-
Certificate Password - Enter the certificate password of the pxGrid client.
-
Click Create.
The system creates a ZIP file of the certificates and downloads it to the path selected in the Windows Explorer dialog box.
-
-
Extract the ZIP file and download three certificate files.
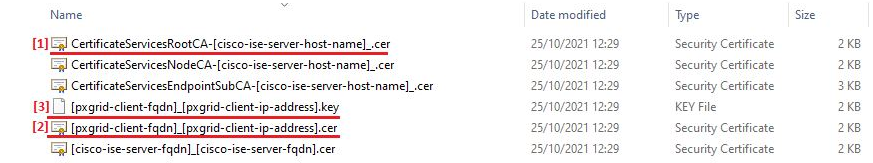
-
[1] - pxGrid Server certificate - Root CA (Cisco ISE server)
-
[2] - pxGrid Client certificate (Management Server)
-
[3] - pxGrid Client Key (Management Server)
-
-
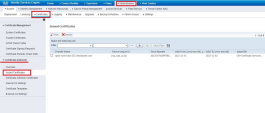
To view the certificates issued by the Cisco ISE server, go to Administration > System > Certificates > Certificate Authority > Issued Certificates.
-
Log in to Check Point Infinity Portal.
-
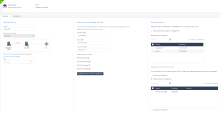
In the Quantum section, go to IoT Protect > IoT > Profiles.
-
Click
 and select IoT Discovery Source Profile.
and select IoT Discovery Source Profile.
-
In the Discovery Source section, from the Discovery source type list, select Cisco ISE.
-
In the Discovery Source Settings section:
-
In the IP address field, enter the IP address of the Cisco ISE Server.
-
In the FQDN field, enter the Full Qualified Domain (FQDN) of the Cisco ISE Server.
-
In the Client FQDN field, enter the FQDN of the client connected to the Cisco ISE Server.
-
-
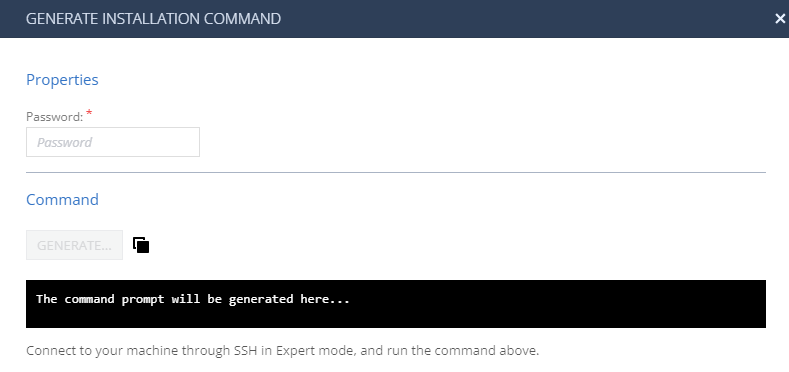
Click Generate Installation Command.
The Generate Installation Command window appears.
-
In the Properties section, enter the pxGrid client certificate password.

Note - Cisco ISE discovery engine uses pxGrid certificates issued by the Cisco ISE server. See Step 1 - Obtain pxGrid certificatesertificates.
-
In the Command section, click Generate.
The system generates the command to configure the Cisco ISE discovery engine on the Check PointSecurity Gateway / Management Server.
-
Copy the generated command.
-
Access your Check PointSecurity Gateway / Management Server through SSH, for example using PuTTY.
-
Log in to Expert mode.
-
Paste the generated command.
-
If the integration is installed on a cluster gateway or Management Server with High Availability (HA) or Multi-Domain Server (MDS) with HA:
-
Access each member through SSH and log in to Expert mode.
-
Paste the generated command.
-
-
In the Run Discovery On section, select the Management Server on which the integration should be installed.
-
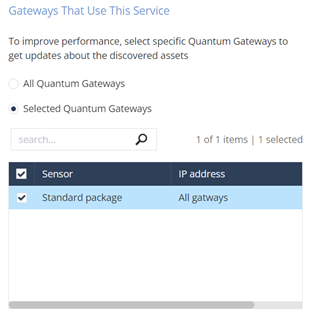
In the Gateways That Use This Service section, select the gateways relevant to your discovered assets, or select the policy-package for all gateways.
-
Click Enforce.
-
Before you copy, rename the pxGrid certificate file names as per the table below.
File Type
File Name
pxGrid server certificate (Cisco ISE)
server-cer.pem
pxGrid client certificate (Management Server)
client-cer.pem
pxGrid client key (Management Server)
client-key.pem
-
Use a file transfer application, such as WinSCP, to copy the pxGrid certificate files to your Check Point Security Gateway / Management Server.
Copy the pxGrid certificates to the following path:
Product
Path
Security Gateway / Management Server
/etc/cp/conf/iot-discovery/ciscoIse/cert/${cisco_ise_integration_id}VSX
/etc/cp/vs<vs_id>/conf/iot-discovery/ciscoIse/cert/${cisco_ise_integration_id}VS0
/etc/cp/conf/iot-discovery/ciscoIse/cert/${cisco_ise_integration_id}
Testing the Cisco ISE IoT Discovery Engine
-
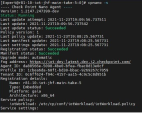
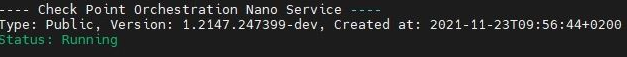
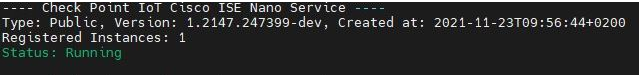
Access the Check Point Security Gateway / Management Server through SSH and run:
cpnano -sSample output:
-
Make sure these nano services are running:
-
Check Point Orchestration
-
Check Point IoT Cisco ISE
-
Troubleshooting the Cisco ISE IoT Discovery Engine
-
Access the Check Point Security Gateway / Management Server through SSH.
-
To ensure that the network and access rules have enabled pxGrid traffic between the Security Gateway / Management Server(pxGrid client) and Cisco ISE (pxGrid) server, run:
-
ping <Cisco ISE's IP Address> -
ping <Cisco ISE's FQDN> -
telnet <Cisco ISE's FQDN> 8910
-
-
Make sure that the certificate files are copied and named correctly:
File Type
File Name
pxGrid server certificate (Cisco ISE)
server-cer.pem
pxGrid client certificate (Management Server)
client-cer.pem
pxGrid client key (Management Server)
client-key.pem
-
If the certificate files are not copied, repeat these procedures:
-
Create pxGrid certificate files in Cisco ISE. See Step 1 - Obtain pxGrid certificates.
-
Copy pxGrid certificate files to the Management Server. See Step 3 - Copy the pxGrid certificates to your Check Point Security Gateway / Management Server.
-
-
Verify that the log file exists:
Product
File
Security Gateway / Management Server
/etc/cp/scripts/iot/ciscoIse/cisco_ise.logVSX
/etc/cp/vs<vs_id>scripts/iot/ciscoIse/cisco_ise.logVS0
/etc/cp/scripts/iot/ciscoIse/cisco_ise.log