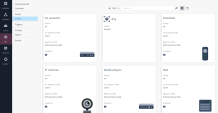
Zones
A zone is a group of IoT assets categorized by their function. Quantum IoT Protect automatically adds the onboarded assets to the relevant zones.
To access the Zones page, go to IoT > Zones.
For example, IP cameras are added to the IP cameras zone.
|
|
Note - The default is the card view. To switch to table view, click |
|
Item |
Description |
|---|---|
|
|
Create a new zone. |
|
|
Delete a zone. |
|
|
Create a clone of the selected zone. |
| Card view | |
|
Family |
Family in which the assets in the zone belong.
|
|
IoT practice mode |
Practice mode of the zone. |
|
Agent's profile |
Profile of the agent. |
|
Practices |
Sub-practice mode of the zone:
|
|
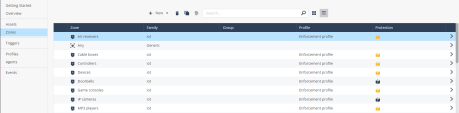
Table view |
|
|
Zone |
Name of the zone. |
|
Family |
Family in which the assets in the zone belong.
|
|
Profile |
Profile of the agent. |
|
Protection |
Sub-practice mode of the zone
|
|
> |
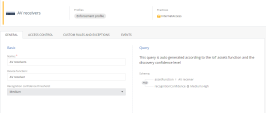
Click to view detailed information about the zone in these tabs: |
General
Shows the basic information about the zone and the query run to add the asset to the zone.
|
Item |
Description |
|---|---|
|
Basic |
|
|
Query |
Query that the system runs to categorize a discovered IoT asset to a zone. By default, the asset discovery confidence level (recoginitionConfidence parameter) is set to Medium and High. To update the query, change the required field value(s) under the Basic section. |
Access Control
You can define the access control mode for the zone that is applied to all the assets in the zone.
The mode for a zone is set through practice and sub-practice(s). A sub-practice inherits the mode from its parent practice by default.
In this example, New Practice 14 is the parent practice and Access to Internet is the sub-practice.
To define the access control mode:
-
In the New Practice > Mode, select a mode:

Note - The default mode is Learn / Detect.
-
Prevent - Allows access only to the domains in the approved destinations list. Access to all other domains is blocked. For more information, see Approved Destinations.
-
Disabled - Does not monitor and secure the asset.
-
Learn / Detect - Monitors the traffic without blocking it.This is the recommended mode for the initial three to six months after you provision the asset. This helps in analyzing the traffic and setting up policies. Once the policies are configured, the mode should be switched to Prevent.
-
-
Select a Mode for the sub-practice(s):

Note - The default mode is Learn / Detect.
-
As Top Level - Applies the same access mode as its parent practice.
-
Disabled - Does not monitor and secure the asset.
-
Learn / Detect - Monitors the asset traffic but does not block it even if it violates the policy.
-
Prevent - Allows access only to the domains in the approved destinations list. Access to all other domains is blocked.
-
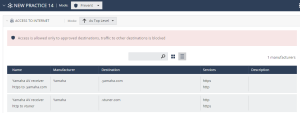
Approved Destinations
Check Point maintains a list of approved destinations for every zone. The access to the approved destinations depends on the mode you set.
To view the approved destinations for a zone:
- In card view, on the zone card, hover the cursor over the approved destinations text.
-
In table view, see the Destination column.
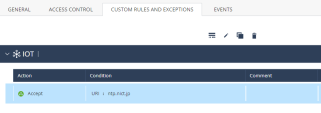
To allow access to a destination not in the approved destination list, add a custom rule or exception. To add or edit a custom rule or exception, expand the Custom Rules and Exceptions drop-down and follow the steps in Custom Rules and Exceptions.
|
|
Note - For Quantum IoT Protect, the data fields in the Triggers section are automatically populated. Do not make any changes in this section. |
Threat Prevention
Threat Prevention allows you to set a mode of action when an asset's risk level matches the specified risk level. The supported modes are:
-
Learn / Detect - Monitors the traffic without blocking it.This is the recommended mode for the initial three to six months after you provision the asset. This helps in analyzing the traffic and setting up policies. Once the policies are configured, the mode should be switched to Prevent.
-
Prevent - Blocks the traffic if the asset's risk level matches the specified level.
-
Disabled - Threat Prevention is disabled. No action is taken if the asset's risk level matches the specified level.
|
|
Notes:
|
To set a mode for an IoT asset with a certain risk level:
-
Go to Threat Prevention and set the practice Mode to one of these:
-
Learn / Detect
-
Prevent
-
Disabled
-
-
In the Activate when risk is drop-down list, select the risk level.
-
Click Enforce.
All the IoT assets in the zone with the selected risk level are blocked.
-
To allow traffic to an asset identified as risky, add an exception in Custom Rules and Exceptions. For more information, see Custom Rules and Exceptions.
|
|
Note - For Quantum IoT Protect, the data fields in the Triggers section are automatically populated. Do not make any changes in this section. |
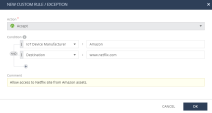
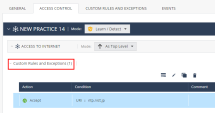
Custom Rules and Exceptions
You can create custom rules and exceptions, for example, to allow or block traffic between an IoT asset and destination.
To add a new custom rule or exception:
-
Click
 .
. -
In the New Custom Rule / Exception window:
-
Click OK.
To edit, clone and delete an existing custom rule or exception:
-
To edit:
-
Click
 .
. -
In the Edit Exception window, enter the required changes.
-
Click OK.
-
-
To clone, click
 .
. The existing exception is cloned and added to the list.
-
To delete, select the exception and click
 .
.
Events
View the events logged for all the assets in the zone.
To view the event statistics, click  in the Statistics bar on the left.
in the Statistics bar on the left.
For card view, click  in the Card bar on the right.
in the Card bar on the right.
|
Event Parameter |
Description |
|---|---|
|
Time |
Time of the event. |
|
Blade |
Software blade which triggered the logs:
|
|
Action |
Action enforced on the event:
|
|
Type |
|
|
Machine Name |
Name of the asset. |
|
Source |
IP address of the IoT asset. |
|
Resource |
Resource accessed by the asset. |
|
Destination |
IP address of the destination. |
|
Destination Machine Name |
Name of the destination asset. |
|
Service |
Service that generated the event. |
|
Rule |
Rule number from the relevant policy package and Rulebase (Examples - 7.1, 11.5). |
|
Rule Name |
Name of the rule (Examples - Internet IoT all, IoT DNS to internal). |
Practices
Shows the different Access Control and Threat Prevention practices applied on the zone.

 .
.
 to specify the operator (AND or OR) and repeat the steps from a to c.
to specify the operator (AND or OR) and repeat the steps from a to c.