Web & Files Protection
This category includes URL Filtering![]() Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF., Download (web) Emulation & Extraction, Credential Protection, Safe Search and Files Protection.
Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF., Download (web) Emulation & Extraction, Credential Protection, Safe Search and Files Protection.
URL Filtering
URL Filtering rules define which sites you can access in your organization. The URL Filtering policy is composed of the selected sites and the mode of operation applied to them.
To create the URL Filtering policy:
-
Go to Policy > Threat Prevention > Policy Capabilities. In the Capabilities & Exclusions pane, select Web & Files Protection.
-
In the Web & Files Protection tab, scroll-down to URL Filtering.
-
Select the URL Filtering Mode of operation:
-
Prevent - Currently supported only in Hold mode. The request to enter a site is suspended until a verdict regarding the site is received.
-
Detect - Allows access if a site is determined as malicious, but logs the traffic.
-
Off - URL Filtering is disabled.
-
-
Select the categories to which the URL Filtering policy applies:
-
Go to Web & Files Protection > Advanced Settings > URL Filtering > Categories.
-
Select the required categories:
-
 Bandwidth Consumption
Bandwidth Consumption
-
Media Streams
-
File Storage and Sharing
-
P2P File Sharing
-
Media Sharing
-
-
 General Use
General Use
-
Computers / Internet
-
Education
-
Entertainment
-
Financial Services
-
Government / Military
-
Greeting Cards
-
Health
-
Political / Legal
-
Job Search / Careers
-
News / Media
-
Newsgroups / Forums
-
Uncategorized
-
Real Estate
-
Recreation
-
Religion
-
Restaurants / Dining / Food
-
Sex Education
-
Shopping
-
Alcohol & Tobacco
-
Art / Culture
-
Blogs / Personal Pages
-
Business / Economy
-
Software Downloads
-
Sports
-
Translation
-
Travel
-
Vehicles
-
Fashion
-
Non-profits & NGOs
-
General
-
Nature / Conservation
-
URL Filtering
-
Lifestyle
-
Lingerie and Swimsuit / Suggestive
-
Very Low Risk
-
Low Risk
-
Email
-
Web Advertisements
-
Search Engines / Portals
-
-
 Legal Liability / Regulatory Compliance
Legal Liability / Regulatory Compliance
-
Gambling
-
Hacking
-
Hate / Racism
-
Illegal / Questionable
-
Illegal Drugs
-
Nudity
-
Pornography
-
Tasteless
-
Violence
-
Weapons
-
Sex
-
Child Abuse
-
Marijuana
-
-
 Productivity
Productivity
-
Personals / Dating
-
Instant Messaging
-
Games
-
Social Networking
-
Instant Chat
-
-
 Service
Service
-
Phishing
-
Spyware / Malicious Sites
-
Botnets
-
Spam
-
Inactive Sites
-
Suspicious Content
-
Medium risk
-
High risk
-
Critical risk
-
Anonymizer
-

Note - For each category, click Edit to see the sub-categories you can select. You can either select the whole category or some sub-categories as per the requirement.
-
-
Click OK.
-
-
Optional. You can select specific URLs to which access is denied. See Deny List.
-
Configure Network URL Filtering:
-
To verify and filter all the URLs accessed by an application or a process, select Enable Network URL Filtering. If this option is not selected, the URL filtering is applied only to the URLs accessed through a browser.
-
To disable Harmony Endpoint client notifications for network URL filtering, select Disable Network URL filtering pop-up notifications if they originate from a browser session.
 Note - This option is applicable only when the Harmony Endpoint Browser extension is installed in the client device.
Note - This option is applicable only when the Harmony Endpoint Browser extension is installed in the client device.
-
The selected mode of operation now applies to the selected categories.
The user can access any site which was not selected in one of the categories or which was not in the Deny List.
You can Allow user to dismiss the URL Filtering alert and access the website - This option is selected by default. This lets you access a site determined as malicious, if you think that the verdict is wrong. To do this, go to Advanced Settings > URL Filtering.
Deny List
You can add specific URLs or domains to the Deny List which blocks the users from accessing them. These URLs/domains will be blocked automatically, while other traffic will be inspected by the URL Filtering rules. You can add the URLs/domain names manually or upload a CSV file with the URLs/domain names you want to include in the deny list.
To add a URL to the Deny List:
-
Go to Advanced Settings > URL Filtering > Deny List > Edit.
-
In the URLs pane, for each required URL, enter the URL and click the + sign
-
click OK.
|
|
Notes: You can use
|
To search for a URL:
-
Go to Advanced Settings > URL Filtering > Deny List > Edit.
-
In the search box, enter the required URL.
The search results appear in the URLs pane.
You can edit or delete the URL.
To import URLs from an external source:
-
Go to Advanced Settings > URL Filtering > Deny List > Edit.
-
Next to the search box, click the
 sign (import domains list from a CSV file).
sign (import domains list from a CSV file). -
Find the required file and click Open.
-
Click OK.
To export a list of URLs to from the Endpoint Security Management Server to an external source:
-
Go to Advanced Settings > URL Filtering > Deny List > Edit.
-
Next to the search box, click the
 sign (export domains list to a CSV file).
sign (export domains list to a CSV file). -
Click OK.
Download (Web) Emulation & Extraction
Harmony Endpoint browser protects against malicious files that you download to your device. For the browsers supported with the Harmony Endpoint Browser extension, see Harmony Browse Administration Guide.
Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. detects zero-day and unknown attacks. Files on the endpoint computer are sent to a sandbox for emulation to detect evasive zero-day attacks. The following files types are supported:
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. detects zero-day and unknown attacks. Files on the endpoint computer are sent to a sandbox for emulation to detect evasive zero-day attacks. The following files types are supported:
|
Threat Emulation Supported File Types |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|
Notes:
|
Threat Extraction![]() Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX. proactively protects users from malicious content. It quickly delivers safe files while the original files are inspected for potential threats.
Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX. proactively protects users from malicious content. It quickly delivers safe files while the original files are inspected for potential threats.
To see the list of file types which are supported by Threat Emulation and Threat Extraction:
-
Go to Policy > Threat Prevention > Policy Capabilities. In the Capabilities & Exclusions pane, select Web & Files Protection.
-
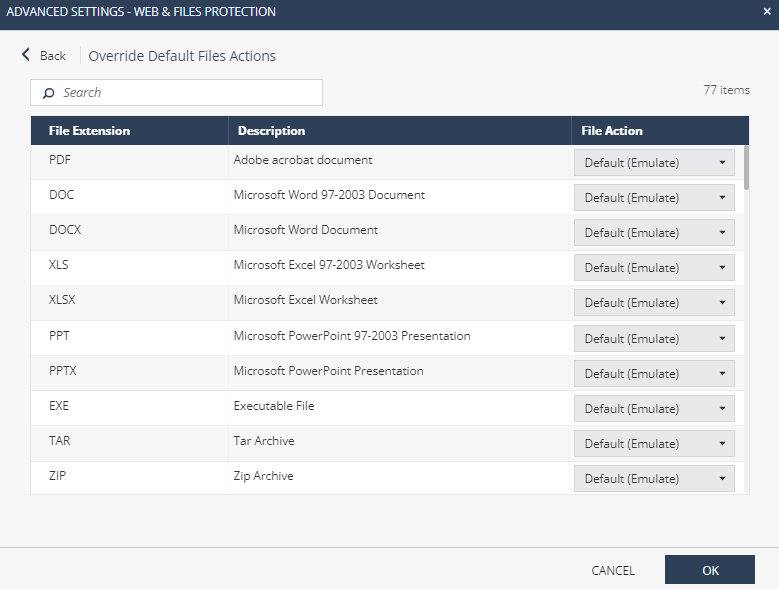
In the Web & Files Protection tab, go to Advanced Settings > Threat Emulation > Override Default File Actions > Edit.
These are the configuration options for supported file types:
- Prevent - Send files for emulation and extraction. For further configuration for supported files, go to Advanced Settings > Supported Files:
Get extracted copy before emulation completes - You can select one of these two options. The system appends .cleaned to the file name. For example, xxx.cleaned.
Extract potential malicious elements - The file is sent in its original file type but without malicious elements. Select which malicious parts to extract. For example, macros, Java scripts and so on.
Convert to PDF - Converts the file to PDF, and keeps text and formatting.

Best Practice - If you use PDFs in right-to-left languages or Asian fonts, preferably select Extract files from potential malicious parts to make sure that these files are processed correctly.
Suspend download until emulation completes - The user waits for Threat Emulation to complete. If the file is benign, the gateway sends the original file to the user. If the file is malicious, the gateway presents a Block page and the user does not get access to the file. This option gives you more security, but may cause time delays in downloading files. The system downloads the file with the original file name.
Emulate original file without suspending access - The gateway sends the original file to the user (even if it turns out eventually that the file is malicious).
Allow - All supported files are allowed without emulation. This setting overrides the Prevent setting selected in the main page.
-
Detect - Emulates original file without suspending access to the file and logs the incident. The file is blocked if it is malicious or blocked by file extension (Advanced Settings > Download Protection). If not, the file is downloaded before the emulation is complete.
-
Off - Allow file. No emulation or extraction is done. The download of all supported files is allowed.
Unsupported Files
File types which are not supported by Threat Emulation and Threat Extraction. Unsupported files types can be allowed or blocked. To configure, go to Advanced Settings > Download Protection > Unsupported Files. The settings selected here override the settings selected in the main page.
Additional Emulation Settings:
Emulation Environments
To define the maximum size of files that are sent for emulation, go to Advanced Settings > Download Protection > Emulation Environments and specify the file size for Upload and emulate files under.
|
|
Notes -
|
To select the operating system images on which the emulation is run, go to Advanced Settings > Download Protection > Emulation Environments, and select one of these options:
-
Use Check Point recommended emulation environments
-
Use the following emulation environments - Select other images for emulation, that are closest to the operating systems for the computers in your organization. This is supported only if configured from the SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on..
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on..
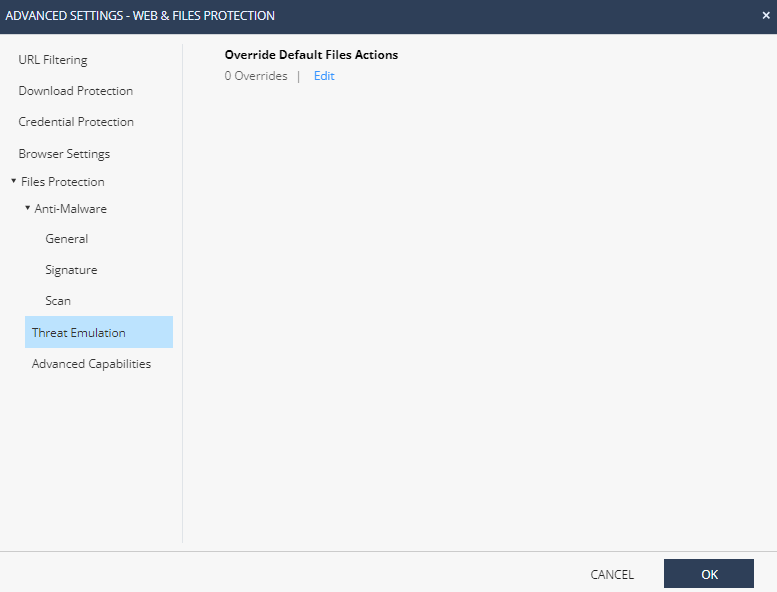
Override Default Files Actions
Harmony Endpoint allows you to override the default file action for the supported and unsupported files.
To override the default file actions, navigate to Advanced Settings > Download Protection > Override default file actions (download).
To override the file action for supported files:
-
In the Supported Files section, click Edit.
-
Select the File action and Extraction Mode.
-
Click OK.
To override the file action for unsupported files:
-
In the Unsupported Files section, click Edit.
-
To add a file type, click
 and enter the File type.
and enter the File type. -
To edit a file type, select the file type and click
.
-
To delete a file type, select the file type and click
.
-
-
Select the Download action for the file:
-
Default - The action specified in Unsupported Files.
-
Allow
-
Block
-
-
(Optional) In the Comments field, enter a comment.
-
Click OK.
Custom Settings
Download Emulation and Extraction
-
Block downloads when emulation fails due to size limit or connectivity problem - Select the checkbox to block download of a file if the Threat Emulation of the file fails due to technical reasons, such as file size limit, no internet connectivity and invalid licenses.
-
Block downloads when emulation fails due to file encryption - Select the checkbox to block download of a file if the Threat Emulation of the file fails to extract the file due to the file encryption.
Credential Protection
To configure the credential protection policy:
-
Go to Policy > Threat Prevention > Policy Capabilities. In the Capabilities & Exclusions pane, select Web & Files Protection.
-
In the Web & Files Protection tab, scroll-down to Credential Protection.
This protection includes two components:
Zero Phishing
Phishing prevention checks different characteristics of a website to make sure that a site does not pretend to be a different site and use personal information maliciously.
There are three configuration options for this protection:
-
Prevent - If the site is determined to be a phishing site, users cannot access the site. A log is created for each malicious site.
-
Detect - When a user uses a malicious site, a log is created.
-
Off - Phishing prevention is disabled.
For further configuration of the Zero Phishing![]() Check Point Software Blade on a Security Gateway (R81.20 and higher) that provides real-time phishing prevention based on URLs. Acronym: ZPH. protection, go to Advanced Settings > Credential Protection:
Check Point Software Blade on a Security Gateway (R81.20 and higher) that provides real-time phishing prevention based on URLs. Acronym: ZPH. protection, go to Advanced Settings > Credential Protection:
-
Allow user to dismiss the phishing alert and access the website - Users can select to use a site that was found to be malicious.
-
Send log on each scanned site - Send logs for each site that users visit, whether malicious or not.
-
Allow user to abort phishing scans - Users can stop the phishing scan before it is completed.
-
Scan local HTML files - By default, the Harmony Endpoint extension in Chromium-based browsers (Chrome, Microsoft Edge, and Brave) cannot access the local HTML files opened by the browser to scan them for phishing attacks. This setting prompts users to grant permission to Chromium-based browsers to access and scan local HTML files on your PC.

Notes:
-
You can customize the prompt page. For more information, seeCustomized Browser Block Pages.
-
This feature is not supported with Safari and Internet Explorer browser extensions.
-
This feature is supported with the Endpoint Security Client version E86.50 and higher.
To grant permission to access and scan the local HTML files:
-
When a user opens a local HTML file, the Harmony Browse request access to file URLs prompt appears. Click Click to copy.
-
Paste the copied path in the address bar of the Chrome browser and press Enter.
-
Scroll down and turn on Allow access to file URLs.
-
If the HTML file has an input field, Harmony Browse scans the file and blocks it, if identified as phishing.
-
-
Disable notifications - Allows you to disable the browser zero-phishing scan notification that appears when users try to enter in an input field.

Note - Only the notification is disabled but the browser zero-phishing scan is performed in the background indicated by the yellow highlight around the input field.
Password Reuse Protection
Alerts users not to use their corporate password in non-corporate domains.
To set the Password Reuse mode:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
In the Capabilities & Exclusions pane, select Web & Files Protection.
-
In the Web & Files Protection tab, scroll-down to Credential Protection.
-
In the Credential Protection section, under Password Reuse, select a mode:
-
Prevent mode - Blocks the user from entering the corporate password and opens the blocking page in a new tab. If you enable Allow users to dismiss the password reuse alert and access the website, then it allows the user to dismiss the blocking page and continue to enter the corporate password.
-
Detect & Alert - Blocks the user from entering the corporate password and opens the blocking page in a new tab and allows the user to dismiss the blocking page and continue to enter the corporate password.

Notes:
-
This option is available only in older releases of Harmony Endpoint. In the newer releases, it is deprecated by Prevent mode.
-
If you enable this option, then Harmony Endpoint automatically disables Allow users to dismiss the password reuse alert and access the website.
-
-
Detect mode - The system does not block the user from entering the corporate password. If a user enters the corporate password, it is captured in the Harmony Browse logs.
-
Off - Turns off password reuse protection.
-
-
For Advanced Settings, see Credential Protection.
For further configuration options for password reuse protection, click Edit > Protected Domains:
Add domains for which Password Reuse Protection is enforced. Harmony Endpoint keeps a cryptographic secure hash of the passwords used in these domains and compares them to passwords entered outside of the protected domains.
Safe Search
Search Reputation
Search Reputation is a feature added to search engines that classifies search results based on URL's reputation.
|
|
Notes:
|
To set the Search Reputation mode:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Select the rule.
-
In the Capabilities & Exclusions pane, select Web & Files Protection.
-
In the Web & Files Protection tab, scroll-down to Search Reputation section and select a mode:
-
On - Turns on the feature.
-
Off -Turns off the feature.
-
When you enable this feature, the icon across the URL in the search results indicate the classification:
|
Icon |
Classification |
|---|---|
|
|
The website is safe. Example:
|
|
|
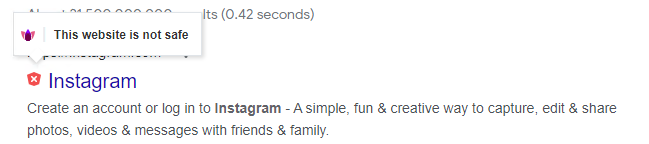
The website is not safe. Example:
|
|
|
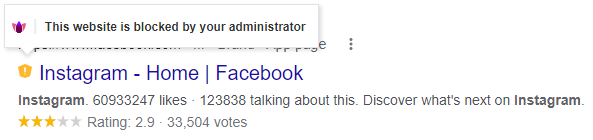
The website is blocked by the Administrator. Example:
|
|
|
Note - If the Search Reputation cannot classify a URL, then it does not display an icon across the URL. If you want such URLs to be classified and blocked, then enable the Uncategorized checkbox in URL Filtering > Categories > General Use. The Search Reputation classifies Uncategorized URLs as The website is blocked by the Administrator. |
Force Safe Search
Force Safe Search is a feature in search engines that acts as an automated filter for potentially offensive and inappropriate content.
To set the Force Search Reputation mode:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Select the rule.
-
In the Web & Files Protection tab, under Force Safe Search, select a mode:
-
On - Hides explicit content from the search results.
-
Off - User sees the most relevant results for their search, which may include explicit content like images consisting of violence.
-
Main features:
-
When ‘Force Safe Search’ is on, Harmony Browse turns on Safe Search on the supported search engines.
-
It is supported with Google, Bing, and Yahoo search engines.
-
Force Safe Search is off by default.
-
Force Safe Search is supported with Google Chrome, and Microsoft Edge browsers.
Files Protection
Protects the files on the file system. To configure the Files Protection policy:
-
Go to Policy > Threat Prevention > Policy Capabilities. In the Capabilities & Exclusions pane, select Web & Files Protection.
-
In the Web & Files Protection tab, scroll-down to Files Protection.
This protection has two components:
-
Anti-Malware Mode - Protection of your network from all kinds of malware threats, ranging from worms and Trojans to adware and keystroke loggers. Use Anti-Malware
 A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. to manage the detection and treatment of malware on your endpoint computers.
A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. to manage the detection and treatment of malware on your endpoint computers.There are three configuration options for this protection:
-
Prevent - Protects your files from malware threats.
-
Detect - Detects the threats, so they appear in the logs, although the virus or malware are still executable. Use this mode with caution.
-
Off - No protection from malware.

Notes -
-
Starting from the Endpoint Security Client E83.20, Check Point certified the E2 client version (the Anti-Malware engine is DHS compliant) for Cloud deployments.
-
The E1 Anti-Malware blade can scan these archive file formats:
-
ZIP
-
Z
-
LZIP
-
7Z
-
RAR
-
ISO
-
CAB
-
JAR
-
BZIP2
-
GZIP
-
DMG
-
XAR
-
TAR
-
ACE
-
-
The E2 DHS Anti-Malware blade can scan these archive file formats:
-
ZIP
-
Z
-
7Z
-
RAR
-
ISO
-
CAB
-
JAR
-
BZIP2
-
GZIP
-
DMG
-
XAR
-
TAR
-
ACE
-
-
-
Files Threat Emulation Mode - Emulation of files on the system.
There are three configuration options for this protection:
-
Prevent - Detects a malicious file, logs the event and deletes the file.
-
Detect - Detects a malicious file and logs the event.
-
Off - Files Threat Emulation mode is off. Does not run the Threat Emulation on the file.
This is supported with Endpoint Security client version E86.80 and higher.
-
-
Advanced Capabilities - You can set an action for each of these capabilities separately:

Note - This is supported only with the Harmony Endpoint Security client version E88.30 and higher.
Advanced Capability
Description
ThreatCloud Reputation Verifies the reputation of files based on their hash in Check Point Cloud-Based Database. This feature is supported from E88.50 and later.
Offline Reputation Verifies file reputation by hash using local data. When connected to the network, the data gets updated with ThreatCloud's common hashes for offline verification.
Vulnerable Driver Protection
Provides protection against potentially malicious drivers by blocking the vulnerable drivers introduced to the device. This also includes drivers that are downloaded, extracted, or copied to the device.
 Note - This feature is supported in Harmony Endpoint Security Client version E88.50 and higher.
Note - This feature is supported in Harmony Endpoint Security Client version E88.50 and higher.Static Signatures
Inspects files using YARA (Yet Another Recursive Acronym) signatures to protect against malware.

Notes:
-
For Static Signatures (YARA) to work, the Anti-Malware security blade must be in Prevent/Detect mode.
-
Supports E89.00 Harmony Endpoint Security Client for Windows and 1.22.x for Linux.
-
Harmony Endpoint records YARA logs within the Anti-Malware logs. For more information, see Static Signature (YARA) Logs.
-
Supported actions are:
- Prevent - Detects a malicious file, logs the event and quarantines the file.
-
Detect - Detects a malicious file and logs the event.
-
Off - No protection from malicious file.
Office Files Performs static analysis¹ on Microsoft Office files. Executables Files Performs static analysis¹ on executable files. DDL Files Performs static analysis¹ on DLL files. ¹Analyzes files without executing them against data models to identify potentially malicious files.
The supported actions are:
-
Prevent - Detects a malicious file, logs the event and quarantines the file.
-
Detect - Detects a malicious file and logs the event.
-
Off - No protection from malicious file.
For more information, see Advanced Capabilities.
To enable Advanced Capabilities:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Select a rule.
-
In the Web & Files Protection tab, in the Advanced Capabilities list, select On.
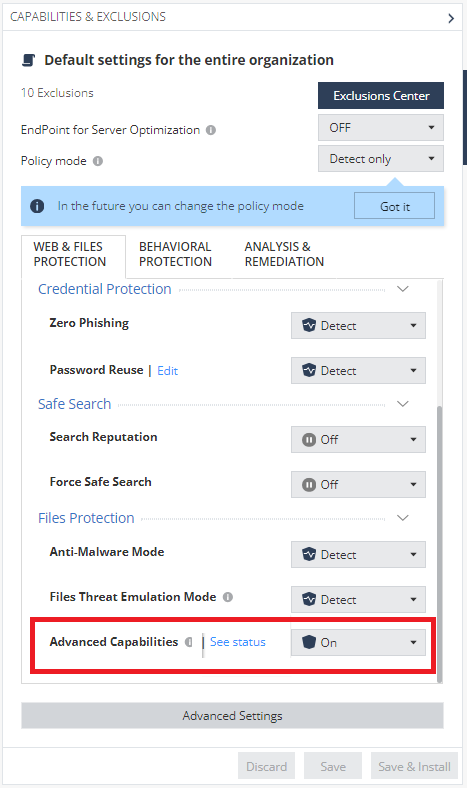

Note - To view the set action for each capability, click See status.
-
Advanced Settings
To configure the advanced settings of the threat prevention policy:
-
Go to Policy > Threat Prevention > Policy Capabilities. In the Capabilities & Exclusions pane, select Web & Files Protection.
-
In the Web & Files Protection tab, click Advanced Settings.
-
Use the following sections to modify the respective settings.
Files Protection
To configure the advanced settings for files protection, go to Advanced Settings > Files Protections.
General
-
Malware Treatment - The malware treatment options let you select what happens to malware that is detected on a client computer:
-
Quarantine file if cure failed - If Endpoint Security cannot repair the file, it is deleted and put in a secure location from where it can be restored if necessary.
-
Delete file if cure failed - If Endpoint Security cannot repair the file, it is deleted.
-
-
Riskware Treatment - Riskware is a legal software that might be dangerous.
- Treat as malware - Use the option selected for Malware.
-
Skip file - Do not treat riskware files.
-
Detect unusual activity - Use behavior detection methods to protect computers from new threats whose information were not added to the databases yet. It does not monitor trusted processes.
-
Enable reputation service for files, web resources & processes - Use cloud technologies to improve precision of scanning and monitoring functions. If you enable or disable this setting, it takes affect after the client computer restarts.
Connection timeout - Change the maximum time to get a response from Reputation Services (in milliseconds). Default is 600.

Note - If you decrease this value, it can improve the performance of the Anti-Malware component but reduces security, as clients might not get a reputation status that shows an item to be zero-day malware.
-
Enable web protection - Prevents access to suspicious sites and execution of malicious scripts Scans files, and packed executables transferred over HTTP, and alerts users if malicious content is.found.
-
Threat Cloud Knowledge Sharing - To share infected information, statistics and infected file samples with Check Point for analysis, select any of these:
-
Allow sending infection info and statistics to Check Point servers for analysis
-
Allow sending infected file samples to Check Point servers for analysis

Note - This is supported only with a DHS compliant Harmony Endpoint Security client.
-
-
Mail Protection - Enable or disable scans of email messages when they are passed as files across the file system.
Signature
-
Frequency
Anti-Malware gets malware signature updates at regular intervals to make sure that it can scan for the newest threats. These actions define the frequency of the signature updates and the source:
-
Update signatures every [x] hours - Signature updates occur every [x] hours from the Endpoint Policy Server
 Endpoint Policy Server improves performance in large environments by managing most communication with the Endpoint Security clients. Managing the Endpoint Security client communication decreases the load on the Endpoint Security Management Server, and reduces the bandwidth required between sites. The Endpoint Policy Server handles heartbeat and synchronization requests, Policy downloads, Anti-Malware updates, and Endpoint Security client logs. and the External Check Point Signature Server.
Endpoint Policy Server improves performance in large environments by managing most communication with the Endpoint Security clients. Managing the Endpoint Security client communication decreases the load on the Endpoint Security Management Server, and reduces the bandwidth required between sites. The Endpoint Policy Server handles heartbeat and synchronization requests, Policy downloads, Anti-Malware updates, and Endpoint Security client logs. and the External Check Point Signature Server.
-
Signature update will fail after [x] seconds without server response - The connection timeout, after which the update source is considered unavailable.
-
-
Signature Sources
-
External Check point Signature Server - Get updates from a dedicated, external Check Point server through the internet.
-
Other External Source - Get updates from an external source through the internet. Enter the URL.
-
-
Shared signature source - Get updates from a shared location on an Endpoint Security client that acts as a Shared Signature Server. This solution is curated for Virtual Desktop Infrastructure (VDI) environments, but can be leveraged for other scenarios as well. This makes it possible to protect non-persistent virtual desktops in Virtual Desktop Infrastructure (VDI) environments. Each non-persistent virtual desktop runs an Endpoint Security, and gets Anti-Malware and Threat Prevention signatures from a shared folder on the Shared Signature Server that is a persistent virtual machine.
-
Second Priority - Set a fallback update source to use if the selected update source fails. Select a different option than the first signature source.
-
Third Priority - Set a fallback update source to use if the other sources fail.

Note - If only update from local Endpoint Servers is selected, clients that are disconnected from an Endpoint Security server cannot get updates.
-
-
Shared Signature Server - To set the server as a Shared Signature Server, select the Set as shared signature server checkbox and enter the local path of the folder. For example, C:\Signatures. For more information, see Shared Signatures Server.
Scan
Anti-Malware scans computers for malware at regular intervals to make sure that suspicious files are treated, quarantined, or deleted.
-
Perform Periodic Scan - Select one of these options to define the frequency of the scans:
-
Every Month- Select the day of the month on which the scan takes place and the Scan start hour.
-
Every Week - Select the day of the week on which the scan takes place and the Scan start hour.
-
Every Day - Select the scan start hour.
-
Scan on Idle - Specify the idle time duration for the endpoint. The Harmony Endpoint Security client initiates the initial or periodic Anti-Malware scan only when the endpoint remains idle for the specified duration. If the device is not idle, the scan is postponed for 24 hours. After this 24-hour period, the Harmony Endpoint Security client initiates the initial or periodic Anti-Malware scan, irrespective of whether the device is idle or in use.

Note - Scan on Idle is only supported by Endpoint Security Client E87.60 and higher.
Optional :
-
Randomize scan time - Mandatory for Virtual Desktop Infrastructure (VDI). Select this option to make sure that not all computers do a scan for malware at the same time. This makes sure that network performance is not affected by many simultaneous scans. In Start scan and End scan, specify the time range during which the scan can start and end.
-
Run initial scan after the Anti-Malware blades installation.
-
Allow user to cancel scan.
-
Prohibit cancel scan if more than X Days passed since last successful scan.
-
-
Scan Targets - Select the target for the Anti-Malware scan:
-
Critical areas
-
Optical drives
-
Local drives
-
Mail messages
-
Removable drives
-
Unrecognized devices
-
Network devices

Notes:
-
Mail messages is not supported with the DHS compliant Anti-Malware blade in macOS.
-
Critical areas is supported with the DHS compliant Anti-Malware blade from E88.00 and higher.
-
-
Scan Target Exclusions - Select the checkboxes to skip scanning of certain files.
-
Skip archives and non executables - Skips scanning of archive file formats (for example, .zip, 7zip, tar.gz, rar, and so on) and non-executable files (files without the execute permission).

Note - Skip archives and non executables are not supported with the DHS compliant Anti-Malware blade.
-
Do not scan files larger than - Specify the file size limit. If the file size is larger than the specified limit, then the system skips scanning the file. The default file size limit is 20 MB.

Note - The maximum supported file size for the Anti-Malware scan depends on the endpoint's system specifications, such as CPU, RAM and so on.
-
Threat Emulation
You can define the default file action for threat emulation.
To override the default file actions:
-
In the Override Default Files Actions section, click Edit.
-
From the File action list, select an action.
-
Click OK.
Advanced Capabilities
In the Advanced Capabilities window, select an action for these capabilities:
-
ThreatCloud Reputation
-
Offline Reputation
-
Vulnerable Driver Protection
 Note - This feature is supported in Harmony Endpoint Security Client versions E88.50 and higher.
Note - This feature is supported in Harmony Endpoint Security Client versions E88.50 and higher. -
Static Analysis:
-
Static Signatures

Note - This feature is supported in Harmony Endpoint Security Client version E89.00 and higher.
-
Office Files
-
Executables Files
-
DDL Files
-
Browser Settings
Pin Extension
This feature enables the administrator to configure to allow users to pin or unpin the browser extension to the toolbar.
|
|
Notes -
|
To allow users to unpin the browser extension, clear Always pin the browser extension to the tool bar under Pin Extension.
Control Browser Notifications
This feature allows administrators to control the following browser notifications:
-
Disable Zero-Phishing notifications - Select the checkbox to disable the zero-phishing scan notification that appears when users try to enter in an input field.

Note - Only the notification is disabled but the browser zero-phishing scan is performed in the background indicated by the yellow highlight around the input field.
-
Disable Download Emulation & Extraction notifications - Select the checkbox to disable the download emulation and extraction notifications whenever a file is downloaded.
Incognito Mode
This feature allows administrators to control the availability of incognito mode for users. The default option is Off.
|
|
Note - This feature is supported only for Endpoint Security client versions E88.60 and higher. |
-
Off - The feature does not control the availability of incognito mode.

Note - Users can access incognito mode depending on the organization policies.
-
Enable - Forces incognito mode to be available for users, overriding any existing settings that might restrict its availability.
-
Disable - Prevents users from accessing incognito mode by disabling it completely.