Harmony Endpoint Logs
Harmony Endpoint Logs menu allows you to customize logs and views to effectively monitor all your systems from one location.
From the New Tab Catalog, select what you want to show in this tab:
|
Catalog Item |
Description |
||
|---|---|---|---|
|
Favorites |
Select one of the Logs or View that you marked with the Favorite icon ( |
||
|
Recent |
Select one of the Logs or Views that you opened recently |
||
|
Shared |
Select a view that was shared with you |
||
|
Logs |
Select one of the widgets with logs collected from all Harmony Endpoint clients
|
||
|
Views |
Select one of the Views with data from all available blades, services, and applications |
||
|
Reports |
Select one of the available reports |
|
|
Note - For custom views and reports through SmartView, see the Logging and Monitoring Administration Guide. |
You can open as many tabs as you want providing they show different views.
Use the toolbar on the top to open views, create new views and reports, export them to PDF and perform relevant actions.
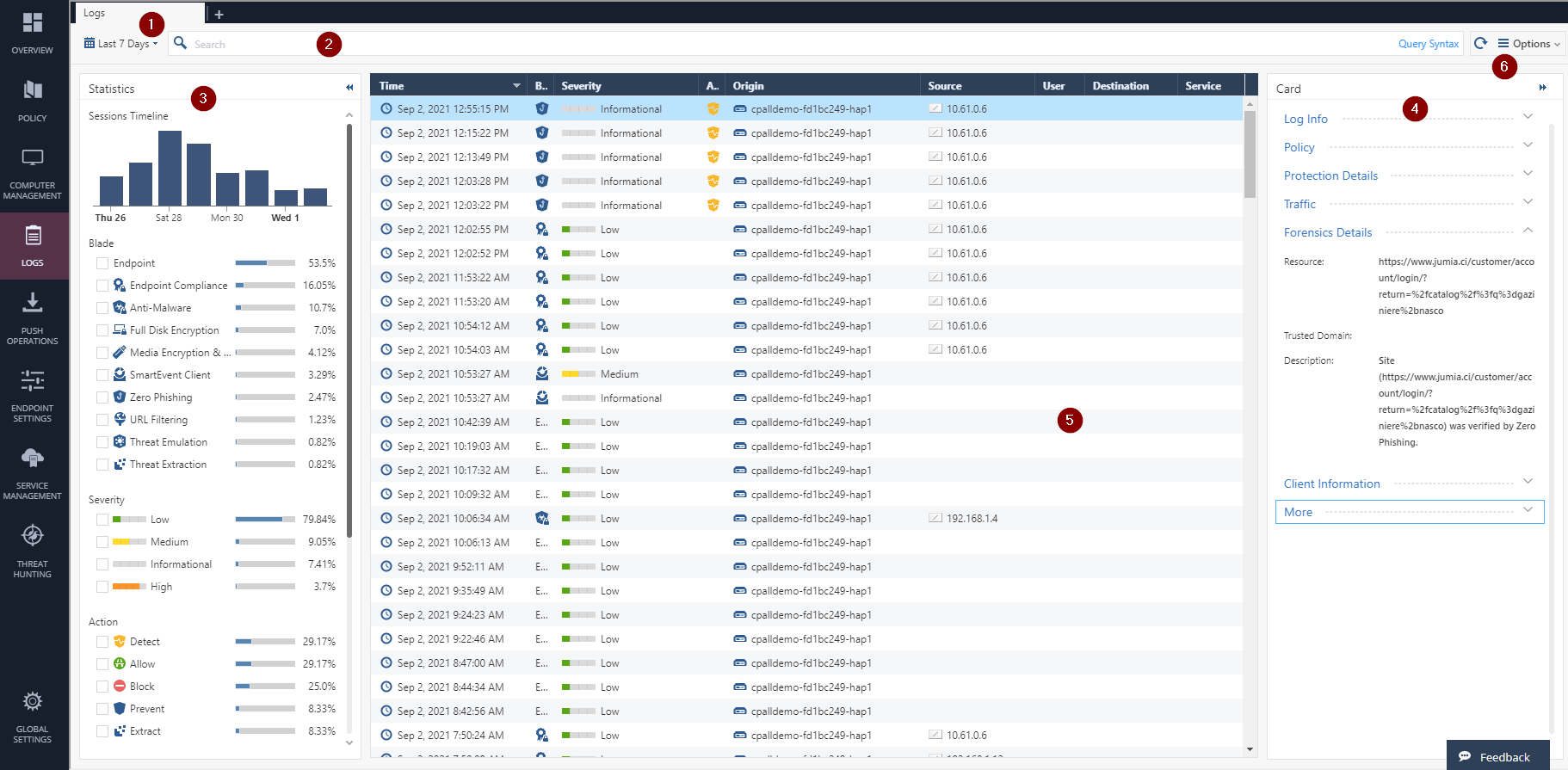
See all collected logs in the Harmony Endpoint Logs view:
Use the time filter (1) and select the relevant options on the Statistics pane (3) to set specific criteria and customize the search results. Alternatively, you can enter your query in the search bar. For more details about the Query Language, see Query Language Overview.
| Item | Description |
|---|---|
|
1 |
Time period - Search with predefined custom time periods or define another time period for the search. |
|
2 |
Query search bar - Enter your queries in this field. |
|
3 |
Statistics pane - Shows statistics of the events by Blades, Severity of the event and other parameters. |
|
4 |
Card - Log information and other details. |
|
5 |
Results pane - Shows log entries for the most recent query. |
|
6 |
Options - Hide or show a client identity in the Card, and export the log details to CSV. |
The information recorded in logs can be useful in these cases:
-
To identify the cause of technical problems.
-
To monitor traffic more closely.
-
To make sure that all features function properly.
|
|
Note - You can forward logs to expansion (SIEM). For more information, see Event Forwarding. |
Data Storage and Retention
-
Threat Hunting and Endpoint Data Retention is 90 days by default.
-
Ingestion limit is 110MB, per seat, per day.
-
Additional Data Retention is available for 1 year, by using the Threat Hunting Data Retention SKU/ Infinity Events SKUs.
For more information, see sk182394.
Static Signatures (YARA) Logs
|
Anti-Malware Mode |
Static Signatures (YARA) Mode |
Action |
Outcome |
|---|---|---|---|
| Detect | Detect | YARA detects the malicious file |
Harmony Endpoint logs the action as Anti-Malware |
| Prevent | YARA blocks the malicious file |
Harmony Endpoint logs the action as Anti-Malware Prevent even though the Anti-Malware is in Detect mode. |
|
| Prevent | Detect | YARA detects the malicious file |
Harmony Endpoint logs the action as Anti-Malware Detect even though the Anti-Malware is in Prevent mode. |
| Prevent | YARA blocks the malicious file |
Harmony Endpoint logs the action as Anti-Malware Prevent. |
|
| Off | Off | No protection |
No logs as Anti-Malware protection is disabled. |