2013 CHECK POINT ANNUAL SECURITY REPORT
03
_ APPLICATIONS IN THE ENTERPRISE WORKSPACE
022
Usage of Anonymizer
Applications by Region
(% of Organizations)
49
%
Americas
40
%
EMEA
35
%
APAC
Web
Server
Ultrasurf
Proxy
Ultrasurf
Client
Ultrasurf
Connects to
One of Its
Proxy Servers
Internet
destination URLs/sites. By using anonymizers, the user
appears to be on a different IP address accessing a different
destination. The organization’s security policies and
defenses may not be able to enforce a user using an altered
IP address trying to reach an altered IP destination. In
some cases, anonymizers may also be used to hide criminal
activities.
43% of the organizations in our study had at least one
anonymizer application used by an employee, with Tor
being the most prominent. 86% of the organizations where
anonymizer usage was found claimed that the usage was
illegitimate and that it conflicted with corporate guidelines
and security policies. Closer analysis of anonymizer
application usage by geographical region revealed that
this type of application was most popular in the Americas
and less so in Asia Pacific.
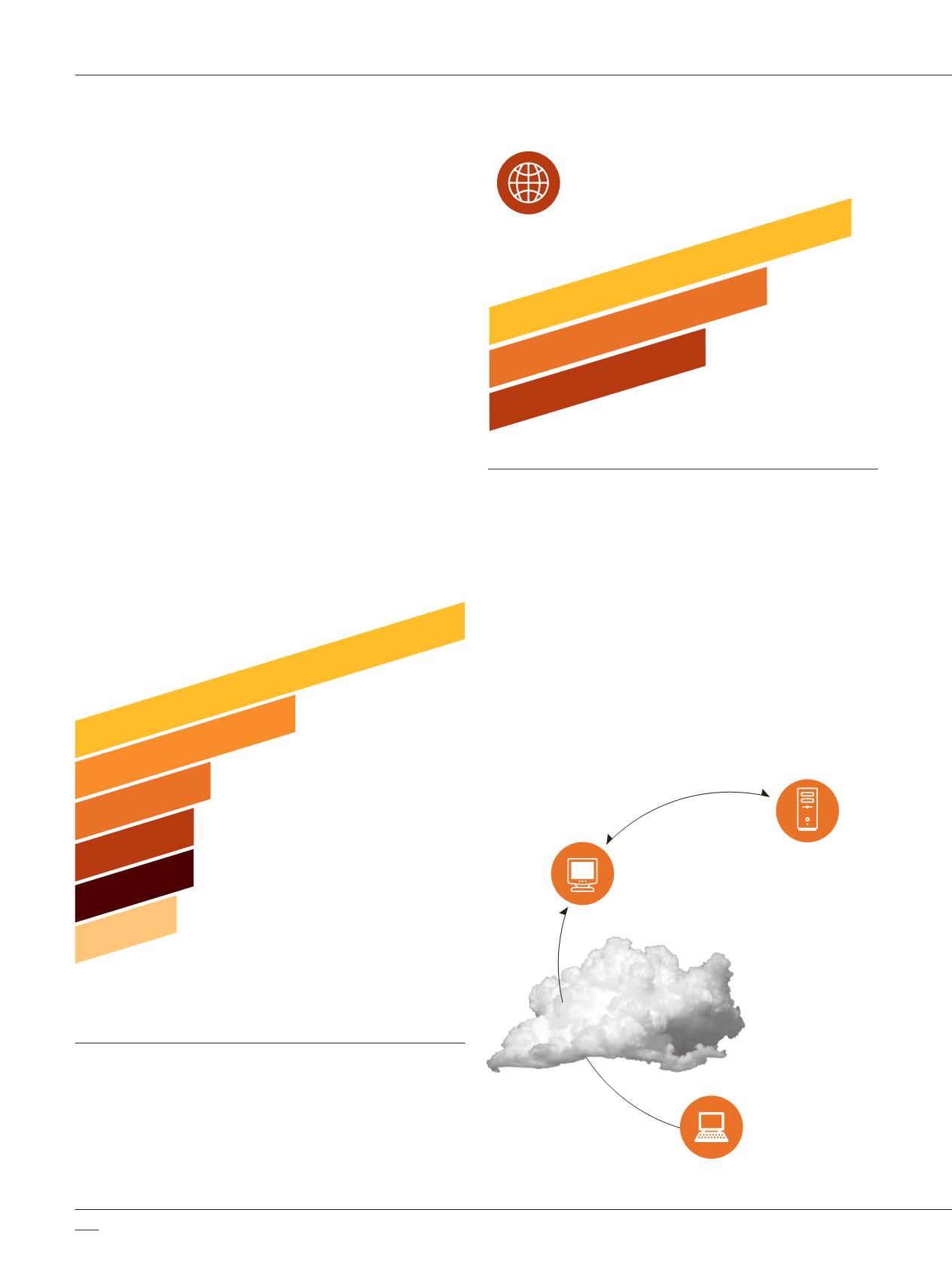
How does the Ultrasurf Anonymizer Work?
Ultrasurf is a very sophisticated anonymizer that works
as a proxy client. It creates an encrypted HTTP tunnel
between the user’s computer and a central pool of proxy
servers, thus enabling its users to bypass firewalls and
censorship. Ultrasurf has a very advanced design for
discovering proxy servers including a cache file of proxy
server IPs and DNS requests. These return encoded IPs
of proxy servers, encrypted documents on Google Docs
and a hard coded list of proxy server IPs built into the
program. Such techniques make it very difficult to detect
by security devices.
Chart 3-D
Source: Check Point Software Technologies
13
%
CGI-Proxy
8
%
Ultrasurf
7
%
Hopster
7
%
Hide My Ass
6
%
Hamachi
Most Popular Anonymizer Applications
(% of Organizations)
More info on top anonymizer applications is available in Appendix B.
Chart 3-C
23
%
Tor
Source: Check Point Software Technologies


