03
_ APPLICATIONS IN THE ENTERPRISE WORKSPACE
021
which could bypass security, conceal identities, cause data
leakage or conspicuously introduce malware infections,
were used.
P2P Applications Open Back Doors
to your Network
Peer-to-peer (P2P) applications are used to share files
between users. P2P is increasingly favored by attackers
to spread malware among shared files. P2P applications
essentially open a back door to networks. They allow users
to share folders that could leak sensitive data, they also could
make organizations liable for users acquiring media illegally
through P2P networks. We recorded a high rate of P2P
applications usage in our research as more than half of the
organizations tested (61%) used P2P applications. The most
prominent P2P file sharing tools used were BitTorrent clients.
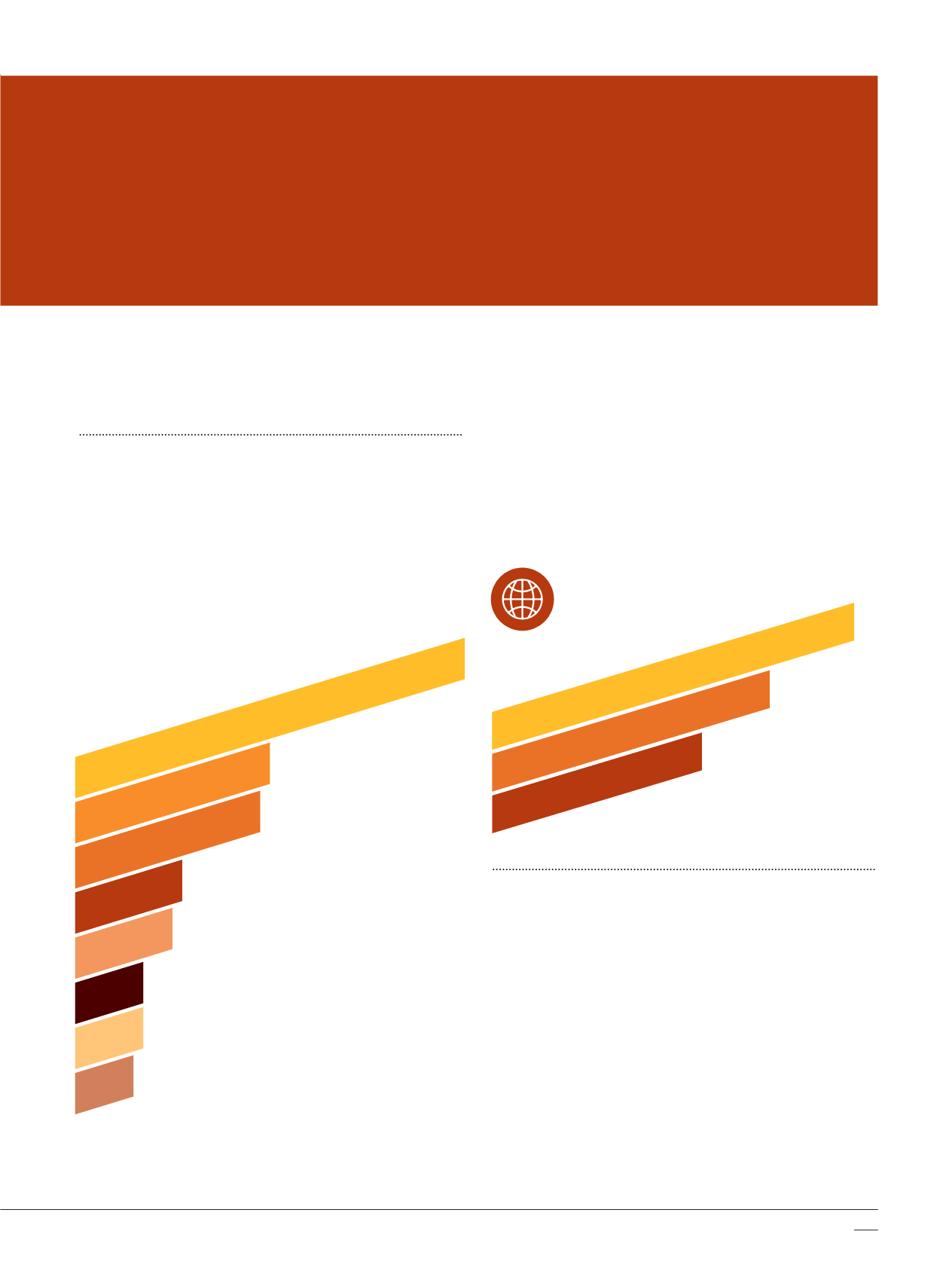
Chart 3-B below shows that P2P file sharing applications
were more popular in Asia Pacific than in other
geographical regions.
IN
61
%
OF ORGANIZATIONS TESTED, A
P2P FILE SHARING APPLICATION WAS USED
Top P2P File Sharing Applications
(% of Organizations)
More info on top P2P applications is available in Appendix B.
20
%
eMule
19
%
SoulSeek
7
%
Windows Live Mesh
6
%
BoxCloud
10
%
Sopcast
11
%
Gnutella
40
%
BitTorrent
7
%
iMesh
Chart 3-A
Usage of P2P File Sharing
Applications by Region
(% of Organizations)
72
%
APAC
62
%
Americas
55
%
EMEA
Chart 3-B
Source: Check Point Software Technologies
Source: Check Point Software Technologies
Anonymizer Applications Bypass
Organization‘s Security Policy
An anonymizer (i.e. anonymous proxy) is a tool that
attempts to make the user’s activity on the Internet
untraceable. The anonymizer application utilizes a proxy
server that acts as a privacymask between a client computer
and the rest of the Internet. It accesses the Internet on the
user’s behalf, hiding personal information by concealing
the client computer’s identifying information and the
destination the user is trying to reach. Anonymizer
applications can be used to bypass security policies
which are essentially built around users’ identities and


