CHECK POINT 2013 SECURITY REPORT
03
_ APPLICATIONS IN THE ENTERPRISE WORKSPACE
027
Recommendations for Securing Web
Application Usage in your Network
Enabling Effective Web 2.0 Protection?
The first step to secure web applications usage in an
organization is to use a security solution that provides
control and enforcement for all aspects of web usage. Full
visibility of all applications running in the environment
is needed, along with the ability to control their usage.
This level of control has to be maintained over client
applications such as Skype, and also over more traditional
URL-based aspect of the web such as websites. As many
sites enable the operation of numerous applications based
on their URLs (e.g. Facebook runs Facebook chat and
other gaming applications through the Facebook URL),
it is essential to have granularity beyond the URL level.
Once this is achieved, organizations should be able to
effectively block applications that can endanger their
corporate security.
Enabling Social Media for Businesses
There are situations where organizations block Facebook
access entirely. But Facebook is considered to be an
essential business tool for many businesses as companies
often publish information about upcoming webinars,
events, new product-related articles, pictures and videos
on their corporate Facebook page. Thus a total social
media ban would negatively impact business performance.
So the question then becomes: How can companies
enable social media usage in the workplace without
compromising system security? The answer lies in
controlling features and widgets within social media apps
and blocking out the less business-relevant portions of
the program. The combination of these actions makes
it possible for corporations to utilize social media with
minimal security risks.
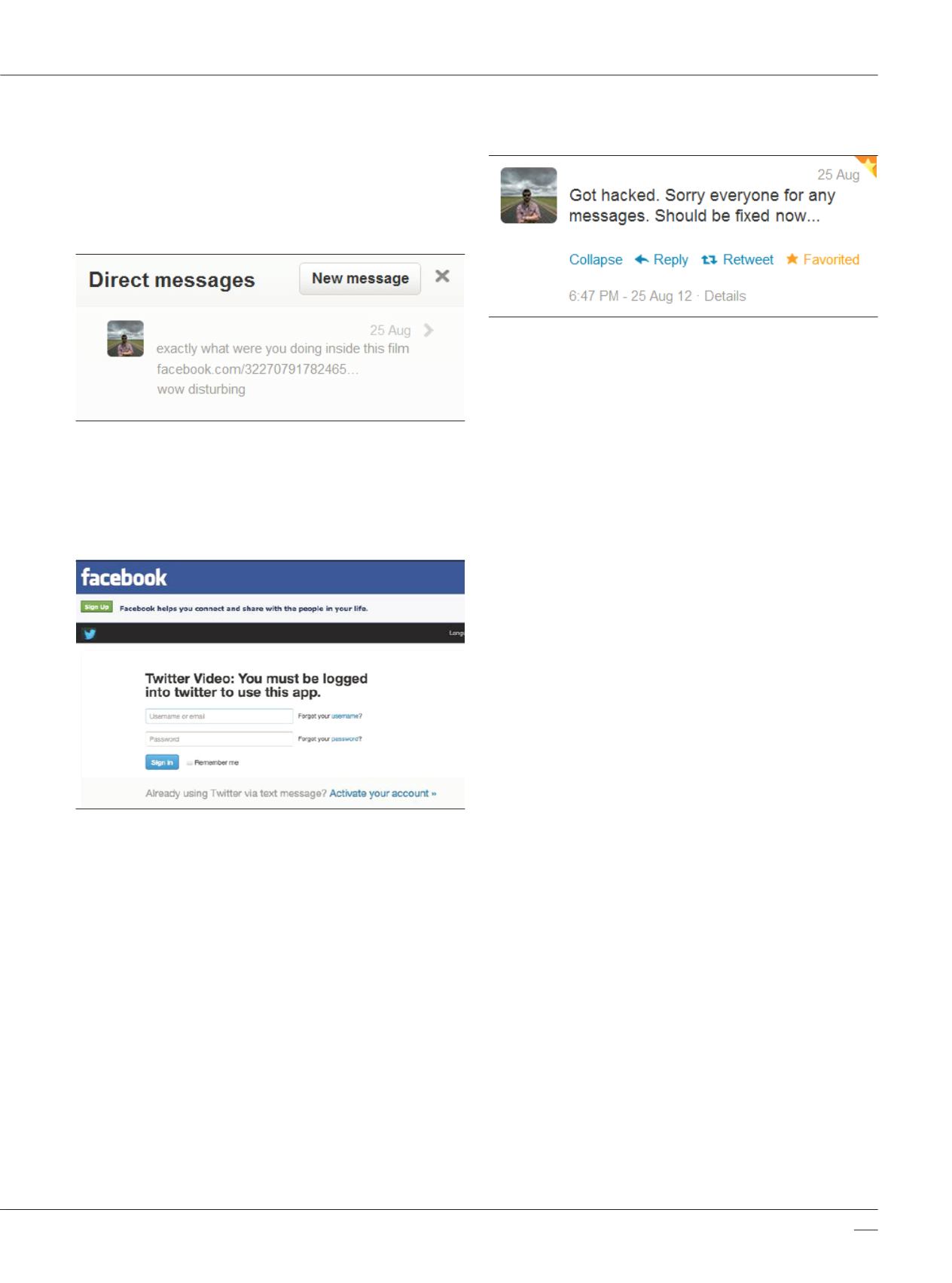
the hacker sent the following message to all of the account’s
followers. "Exactly what were you doing inside this film
[Facebook-URL]… wow disturbing”.
The URL pointed to a Facebook app which required
“Twitter Login”. The login screen was actually a web
server owned by the hacker that was used to harvest the
recipient’s Twitter credentials.
The hacker can repeat the process by using the newly
hacked Twitter accounts to steal even more passwords.
The hacker can also use the stolen credentials to access
other services such as Gmail, Facebook, etc. Even
worse, stolen personal credentials can be used to log
into bank accounts or business-related services such as
SalesForce.
After the malicious message was redistributed to the
followers of the hacked account, the only effective
recourse was to post a polite apolog y.


