

In This Section: |
SmartConsole lets you transform log data into security intelligence. Search results are fast and immediately show the log records you need. The Security Gateways send logs to the Log Servers on the Security Management Server or on a dedicated server. Logs show on the SmartConsole Logs & Monitor Logs tab. You can:
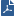
This is a sample procedure that shows how to do an analysis of a log of a dropped connection.
To show a log of a dropped connection:
This shows the logs for connections that were dropped by the Rule Base.
The Log Details window opens.
This is an example of the Log view.
Item |
Description |
|---|---|
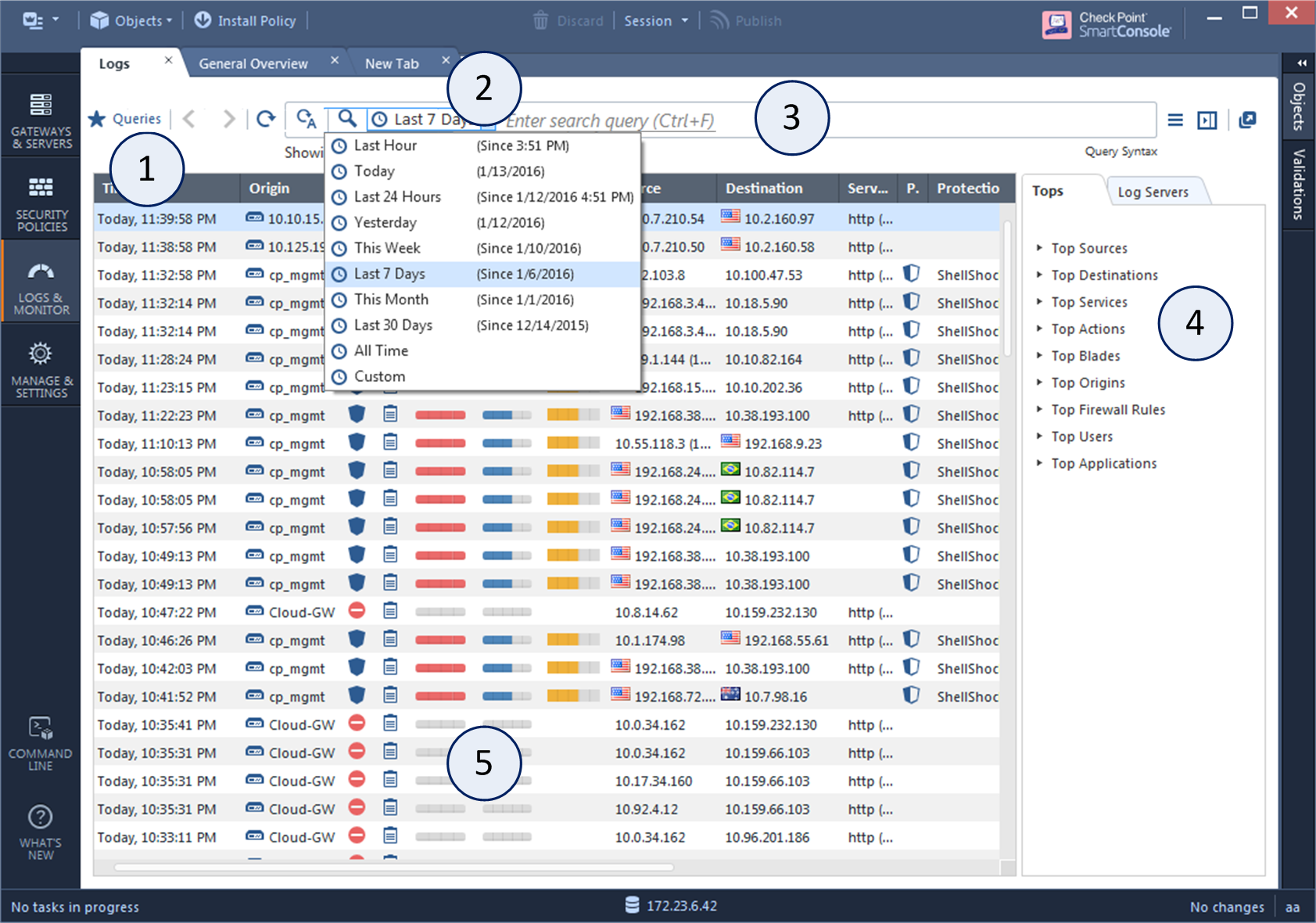
1 |
Queries - Predefined and favorite search queries. |
2 |
Time Period - Search with predefined custom time periods. |
3 |
Query search bar - Define custom queries in this field. You can use the GUI tools or manually enter query criteria. Shows the query definition for the most recent query. |
4 |
Log statistics pane - Shows top results of the most recent query. |
5 |
Results pane - Shows log entries for the most recent query. |
In This Section: |
Logs are useful if they show the traffic patterns you are interested in. Make sure your Security Policy tracks all necessary rules. But when you track multiple rules, the log file will be large, and will require more disk space and management operations.
To balance these requirements, track rules that can help you improve your network security, help you understand of user behavior, and are useful in reports.
To configure tracking in a rule:
You can add these options to a Log, Full Log, or Network Log:
Alert:
If an Alert is selected, Log is selected automatically.
You can search for the logs that are generated by a specified rule, from the Security Policy or from the Logs & Monitor > Logs tab
To see logs generated by a rule (from the Security Policy):
To see logs generated by a rule (by Searching the Logs):
layer_uuid_rule_uuid:*_<UID>
For example, paste this into the query search bar and press Enter:
layer_uuid_rule_uuid:*_46f0ee3b-026d-45b0-b7f0-5d71f6d8eb10
SmartConsole lets you quickly and easily search the logs with many predefined log queries, and an easy to use language for custom queries.
To create and run a query:
The query runs automatically. When you add more criteria, results are updated dynamically.
To manually refresh your query:
|
Click Refresh (F5). |
To continuously refresh your query (Auto-Refresh):
|
Click Auto-Refresh (F6). The icon is highlighted when Auto-Refresh is enabled. |
The query continues to update every five seconds while Auto-Refresh is enabled. If the number of logs exceeds 100 in a five-second period, the logs are aggregated, and the summary view shows. To see all logs that have been aggregated in a specific time interval, click View.
Query results can include tens of thousands of log records. To prevent performance degradation, SmartConsole only shows the first set of results in the Results pane. Typically, this is a set of 50 results.
Scroll down to show more results. As you scroll down, SmartConsole extracts more records from the log index on the Security Management Server or Log Server, and adds them to the results set. See the number of results above the Results pane.
For example, on the first run of a query, you can see the first 50 results out of over 150,000 results. When you scroll down, you can see the first 100 results out of over 150,000.
By default, SmartConsole shows a predefined set of columns and information based on the selected blade in your query. This is known as the Column Profile. For example:
If no blade is specified, a column profile is assigned based on the blade that occurs most frequently in the query results. This is called Automatic Profile Selection, and is enabled by default.
The Column Profile defines which columns show in the Results Pane and in which sequence. You can change the Column Profile as necessary for your environment.
To use the default Column Profile assignments:
To manually assign Column Profile assignments by default:
To manually assign a different Column Profile:
To change a Column Profile:
The column is applicable to future sessions.
Queries can include one or more criteria. To create custom queries, use one or a combination of these basic procedures:
To create a new custom query, run an existing query, and use one of these procedures to change it. You can save the new query in the Favorites list.
When you create complex queries, the log search tool suggests, or automatically enters, an appropriate Boolean operator. This can be an implied AND operator, which does not explicitly show.
You can enter query criteria directly from the Query search bar.
To select field criteria:
The query runs automatically.
You can use the column headings in the Grid view to select query criteria. This option is not available in the Table view.
To select query criteria from grid columns:
To enter more criteria, use this procedure or other procedures.
You can type query criteria directly in the Query search bar. You can manually create a new query or make changes to an existing query that shows in the Query search bar.
As you type, the Search shows recently used query criteria or full queries. This helps you to search. To use these suggestions, select them from the drop-down list. If you make a syntax error in a query, the Search shows a helpful error message that identifies the error and suggests a solution.
A powerful query language lets you show only selected records from the log files, according to your criteria. To create complex queries, use Boolean operators, wildcards, fields, and ranges. This section refers in detail to the query language.
When you use the GUI to create a query, the applicable criteria show in the Query search bar.
The basic query syntax is [<Field>:] <Filter Criterion>.
To put together many criteria in one query, use Boolean operators:
[<Field>:] <Filter Criterion> AND|OR|NOT [<Field>:] <Filter Criterion> ...
Most query keywords and filter criteria are not case sensitive, but there are some exceptions. For example, Risk:High is case sensitive (Risk:high does not match). If your query results do not show the expected results, change the case of your query criteria, or try upper and lower case.
When you use queries with more than one criteria value, enter a Boolean operator.
Criteria values are written as one or more text strings. You can enter one text string, such as a word, IP address, or URL, without delimiters. Phrases or text strings that contain more than one word must be surrounded by quotation marks.
One word string examples:
Phrase examples
"John Doe""Log Out""VPN-1 Embedded Connector"IPv4 and IPv6 addresses used in log queries are counted as one word. Enter IPv4 address with dotted decimal notation and IPv6 addresses with colons. You can also use the '*' wildcard character with IP addresses.
Example:
You can use NOT <field> values with field keywords in log queries to find logs for which the value of the field is not the value in the query.
Syntax
NOT <field>:<value>
Example
NOT src:10.0.4.10
You can use the standard wildcard characters (* and ?) in queries to match variable characters or strings in log records. The wildcard character cannot be the first character in a query criterion. You can use more than the wildcard character.
Wildcard syntax
Examples:
If your criteria value contains more than one word, you can use the wildcard in each word. For example, 'Jo* N*' shows Joe North, John Natt, Joshua Named, and so on.
The wildcard character is useful when used with IPv4 addresses. It is a best practice to put the wildcard character after an IP address delimiter.
Examples:
You can use predefined field names as keywords in filter criteria. The query result only shows log records that match the criteria in the specified field. If you do not use field names, the query result shows records that match the criteria in all fields.
This table shows the predefined field keywords. Some fields also support keyword aliases that you can type as alternatives to the primary keyword.
Keyword |
Keyword Alias |
Description |
|---|---|---|
|
|
Severity of the event |
|
|
Potential risk from the event |
|
|
Name of the protection |
|
|
Type of protection |
|
|
Level of confidence that an event is malicious |
|
|
Action taken by a security rule |
|
|
Software Blade |
|
|
Traffic destination IP address, DNS name or Check Point network object name |
|
|
Name of originating Security Gateway |
|
|
Service that generated the log entry |
|
|
Traffic source IP address, DNS name or Check Point network object name |
|
|
User name |
Syntax for a field name query:
<field name>:<values>|(<value><operator><value>)
Examples:
source:192.168.2.1action:(Reject OR Block)You can use the OR Boolean operator in parentheses to include multiple criteria values.
Important - When you use fields with multiple values, you must:
You can use the Boolean operators AND, OR, and NOT to create filters with many different criteria. You can put multiple Boolean expressions in parentheses.
If you enter more than one criteria without a Boolean operator, the AND operator is implied. When you use multiple criteria without parentheses, the OR operator is applied before the AND operator.
Examples:
blade:"application control" AND action:block 192.168.2.133 10.19.136.101 192.168.2.133 OR 10.19.136.101 (blade:Firewall OR blade:IPS OR blade:VPN) AND NOT action:drop AND NOT criterion.source:(192.168.2.1 OR 192.168.2.2) AND destination:17.168.8.2 17.168.8.2. This example also shows how you can use Boolean operators with field criteria.