Compliance
The Check Point Compliance![]() Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. blade is a dynamic solution that continuously monitors the Check Point security infrastructure. The blade uses the Continuous Compliance Monitoring (CCM) technology to examine Security Gateways, Software Blades, policies, and configuration settings against an extensive database of regulatory standards and security best practices. The blade suggests corrective measures in case of deficiency. The Compliance blade incorporates visual representations and reports that describe Compliance to the compliance standards.
Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. blade is a dynamic solution that continuously monitors the Check Point security infrastructure. The blade uses the Continuous Compliance Monitoring (CCM) technology to examine Security Gateways, Software Blades, policies, and configuration settings against an extensive database of regulatory standards and security best practices. The blade suggests corrective measures in case of deficiency. The Compliance blade incorporates visual representations and reports that describe Compliance to the compliance standards.
The Compliance blade performs these automatic scans:
-
Daily - One automatic scan per day, which finds changes to gateway and policy configurations made with CLI or scripts.
-
SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. changes - Automatic scan when an administrator changes objects that have an effect on Security Gateway
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. changes - Automatic scan when an administrator changes objects that have an effect on Security Gateway Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. or policy configuration (the scan occurs after you publish the changes.)
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. or policy configuration (the scan occurs after you publish the changes.)
You can also run manual scans, as necessary.
To enable the Compliance blade on your Security Management Server:
-
In SmartConsole, go to the Gateways & Servers view, and double-click on the Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. object.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. object.The Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. editor opens.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. editor opens. -
In the General Properties page, go to Management, and select Compliance.
-
Click OK.
To view the Compliance dashboard:
-
In SmartConsole, go to the Logs & Monitor view, and click + sign to open a new tab.
The New Tab opens.
-
Click Compliance.
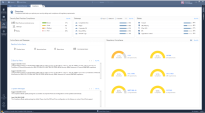
The Compliance View
The Compliance view includes 5 widgets:
The Compliance Scoring System
The Compliance blade calculates a numeric score for each best practice test. The numeric score is the average of the results for each object examined. Average scores are given for the organization Security Gateways, Software Blades, and regulations.
This is the Check Point Compliance blade scoring system:
|
Security Status |
Score in % |
Comments |
|---|---|---|
|
Poor |
0-50 |
0=non-compliant |
|
Medium |
50-75 |
|
|
Good |
75-99 |
|
|
Secure |
100 |
Compliant |
|
N/A |
Not Applicable |
Given if:
|
This chapter explains how to work with each Compliance view. For details about system requirements, troubleshooting and debugging, see sk120256.