

In This Section: |
This section covers topology restrictions.
QoS can manage up to the maximum number of interfaces supported by the Security Gateway, subject to these restrictions:
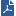
For example, in the configuration depicted in the following diagram, the routers can pass traffic to each other through the hub without the QoS gateway being aware of the traffic.

Item |
Description |
|---|---|
1 |
Internal network |
2 |
Security Gateway with QoS enabled |
3 |
Hub |
4 |
Routers |
5 |
Internet |
You cannot manage two networks connected to a single router since traffic may pass from one line to the other directly through the router, without the QoS gateway being aware of the traffic:
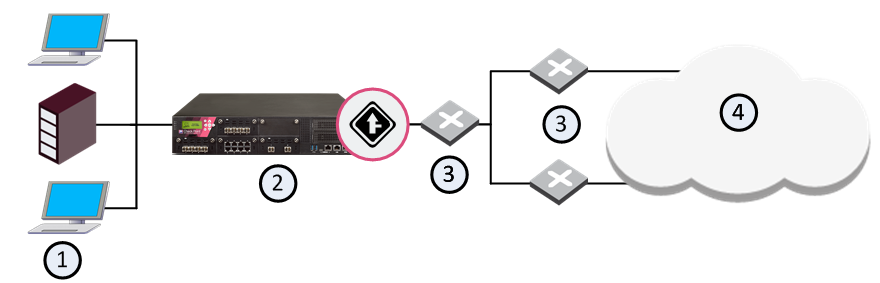
Item |
Description |
|---|---|
1 |
Internal network |
2 |
Security Gateway with QoS enabled |
3 |
Routers |
4 |
Internet |
In a correct configuration, the routers connect directly to the QoS gateway.
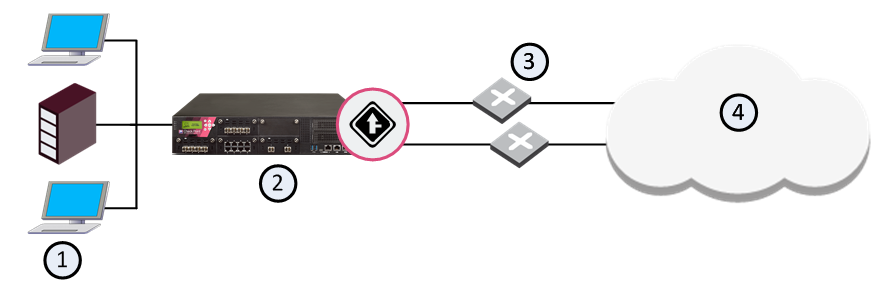
Item |
Description |
|---|---|
1 |
Database server |
2 |
Web server |
3 |
Security Gateway with QoS enabled |
4 |
Internet |
5 |
Branch office |
The previous diagram shows that the branch office communicates with the central site and the opposite. It only communicates directly with the Internet through the central site. The Web server makes important company documents available to the branch office, and the database server supports the company's mission-critical applications.
The problem is that most of the branch office traffic is internal and external Web traffic, and the mission-critical database traffic suffers as a result. The network administrator has considered upgrading the 56K lines, but is reluctant to do so, not only because of the cost but also because upgrading would probably not solve the problem. The upgraded lines would still be filled mostly with Web traffic.
The goals are as follows:
These goals are accomplished with the following Rule Base:
Main Rules
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Office 1 |
Office 1 |
Any |
Any |
Weight 10 Limit 56KBps |
|
||||
Office n |
Office n |
Any |
Any |
Weight 10 Limit 56KBps |
Default |
Any |
Any |
Any |
Weight 10 |
Each office has sub-rules, as follows:
Office Sub-Rules
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Start of Sub-Rule |
||||
Database Rule |
Any |
Database server |
Database service |
Weight 50 |
Web Rule |
Any |
Web Server |
http |
Weight 10 |
Branch Offices |
Any |
Any |
Any |
Weight 10 |
End of Sub Rule |
||||
The sub-rules give database traffic priority over Web traffic and other traffic.
The following assumptions are made in this example:
Note that QoS shapes the branch office lines in the outbound direction only. QoS shapes inbound traffic only on directly controlled interfaces (that is, interfaces of the QoS machine).
The architecture and flow control of QoS is similar to firewall.
QoS has three components:
The components can be installed on one machine or in a distributed configuration on a number of machines.
Bandwidth policy is configured using SmartConsole. On the Security Management Server, the policy is verified and installed on the QoS gateways. The QoS Security Gateway uses:
Logging information is created using the firewall kernel API.
The primary role of the QoS blade is to:
QoS has two components:
The kernel driver is the heart of QoS operations. It is in the kernel driver that IP packets are examined, queued, scheduled and released, enabling QoS traffic control abilities.
The QoS daemon is a user mode process that:
You use the R80.30 SmartConsole and SmartDashboard to create "bandwidth rules" for the QoS policy. Use the Logs & Monitor features in SmartConsole to see information about the active QoS Security Gateways and their Policies.
Use SmartConsole to create and change QoS Policies. Use SmartDashboard to work with rules, together with their related network objects and services.
The QoS Policy rules are shown the QoS Rule Base.
The Security Management Server and the QoS Security Gateway can be installed on the same machine or on two different machines. When they are installed on different machines, the configuration is known as distributed.
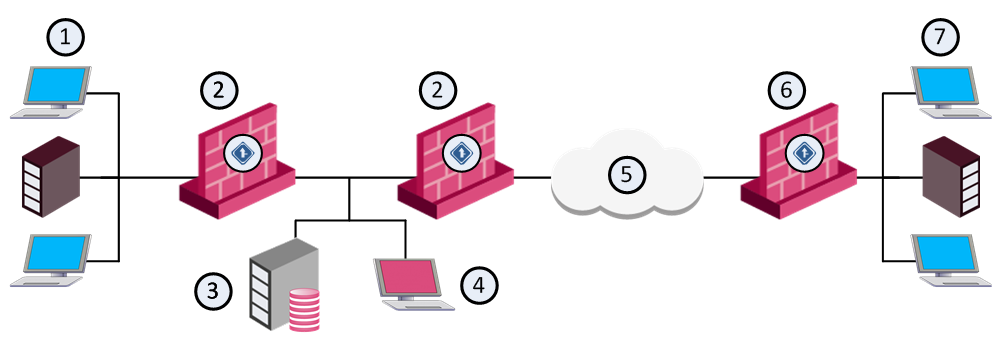
Item |
Description |
|---|---|
1 |
Internal network (main office) |
2 |
Security Gateway with QoS enabled |
3 |
Security Management Server |
4 |
SmartConsole |
5 |
Internet |
6 |
Security Gateway with QoS enabled (branch office) |
7 |
Internal network (branch office) |
The example shows a distributed configuration, in which one Security Management Server (consisting of a Security Management Server and a SmartConsole controls four QoS gateways. The four QoS gateways manage bandwidth allocation on three QoS enabled lines.
One Security Management Server can control and monitor multiple QoS gateways. The QoS Security Gateway operates independently of the Security Management Server. QoS gateways can operate on more Internet gateways and interdepartmental gateways.
SmartConsole and the Security Management Server can be installed on the same machine or on two different machines. When they are installed on two different machines, QoS implements the Client/Server model, in which a SmartConsole controls a Security Management Server.
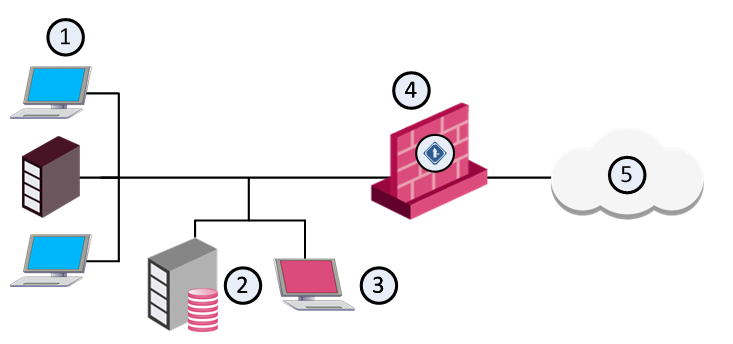
Item |
Description |
|---|---|
1 |
Internal network (main office) |
2 |
Security Management Server |
3 |
SmartConsole |
4 |
Security Gateway with QoS enabled |
5 |
Internet |
In the configuration depicted in the above figure, the functionality of the Security Management Server is divided between two workstations (Tower and Bridge). The Security Management Server with the database is on Tower. The SmartConsole is on Bridge.
The user, working on Bridge, maintains the QoS Policy and database, which reside on Tower. The QoS Security Gateway on London enforces the QoS Policy on the QoS enabled line.
The Security Management Server is started with the cpstart command, and must be running if you wish to use the SmartConsole on one of the client machines.
A SmartConsole can manage the Server only if both the administrator logged into SmartConsole and the computer on which the SmartConsole is running have been authorized to access the Security Management Server. Use cpconfig to:
More than one administrator can work with QoS Policies at the same time, each in a different session. A locking mechanism prevents administrators from working on the same object at one time. After you complete you work in a session, click Publish to make your changes available to other sessions and administrators.
QoS and firewall share many core technology components. The same user-defined network objects can be used in both solutions. The integration of an organization's security and bandwidth management policies gives easy policy definition and system configuration. For efficient traffic inspection and enhanced performance, the blades share state table information. The QoS blade and firewall blade let users define bandwidth allocation rules for encrypted and NATed traffic.
QoS uses the Security Management Server and shares the objects database (network objects, services and resources) with the firewall. Some objects have properties that are product specific. For example, the Firewall has encryption properties which are not related to QoS. A QoS network interface has speed properties that are not related to the firewall.