

In This Section: |
This chapter includes a step by step guide for creating a sample deployment with a QoS Policy. We recommend that you have a working knowledge of these Check Point products and concepts to use this tutorial effectively:
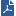
Item |
Description |
|---|---|
1 |
Oxford - Security Management Server |
2 |
Cambridge - SmartConsole client |
3 |
Local area network - Engineering and Marketing |
4 |
London - Security Gateway with QoS |
4a |
Interface eth2 - 199.199.199.32 |
4b |
Interface eth1 - 199.32.43.32 |
4c |
Interface eth0 - 199.32.32.32 |
5 |
DMZ with Web and FTP servers |
6 |
Internet |
This scenario is an organization with offices located in London, Oxford and Cambridge. The QoS Security Gateway is in London and has three interfaces, one of which is connected to the Internet. The Security Management Server is in Oxford and the SmartConsole is in Cambridge. The local network includes the Marketing and Engineering departments.
This tutorial is a simplified exercise that shows you how to do these QoS activities:
To install and configure system components for this tutorial:
This section describes how to open SmartDashboard and access the QoS tab.
This name cannot:
Note: There are some limitations that can prevent you from enabling SecureXL or CoreXL with QoS Policies.
For more, see: QoS Policy limitations.
The system saves the new Policy and SmartDashboard opens automatically. You can start to define your rules here.
To implement a good QoS Policy, find out how the network is used. Identify and prioritize the types of traffic. Identify users and their needs. For example:
Define these Network Objects:
To define the London Security Gateway:
Field |
Value |
Notes |
|---|---|---|
Name |
London |
This is the name by which the object is known on the network; the response to the hostname command. |
Platform |
Select an appliance type or Open Server |
The platform must be supported for R80.30. |
SIC |
Click Communication |
Establishes a secure communication channel between the Security Gateway and the management server. |
Version |
R80 |
|
OS |
Gaia |
|
IP Address |
192.32.32.32 |
This is the interface associated with the host name in the DNS — get this by clicking Get Address. For gateways, this should always be the IP address of the external interface. |
Network Security Tab |
Firewall and QoS |
|
In this step you configure each interface and its QoS properties.
To configure interface properties:
The interfaces show in the Network Management window.
eth0
Field |
Value |
Notes |
|---|---|---|
Net Address |
192.32.32.32 |
|
Net Mask |
255.255.255.0 |
|
Topology Settings (Click Modify) |
Internet External |
This interface connects to the Internet. |
Anti-Spoofing |
Perform Anti-Spoofing based on interface topology |
Each incoming packet is examined to make sure that the source IP address is valid. |
Spoof Tracking |
Log |
Log Anti-Spoofing events. |
eth1
Field |
Value |
Notes |
|---|---|---|
Net Address |
192.32.42.32 |
|
Net Mask |
255.255.255.0 |
|
Topology Settings (Click Modify) |
Internet External |
This interface connects to the Internet. |
Anti-Spoofing |
Perform Anti-Spoofing based on interface topology |
Each incoming packet is examined to make sure that the source IP address is valid. |
Spoof Tracking |
Log |
Log Anti-Spoofing events. |
eth2
Field |
Value |
Notes |
|---|---|---|
Net Address |
192.199.199.32 |
|
Net Mask |
255.255.255.0 |
|
Topology Settings (Click Modify) |
Internet External |
This interface connects to the Internet. |
Anti-Spoofing |
Perform Anti-Spoofing based on interface topology |
Each incoming packet is examined to make sure that the source IP address is valid. |
Spoof Tracking |
Log |
Log Anti-Spoofing events. |
To configure interface QoS properties:
The QoS Policy required for this tutorial does not require the definition of new proprietary services. The commonly used services HTTP and RealAudio are already defined in QoS.
After you define your network objects and services, the next step is to create your QoS policy rules. This tutorial shows you how to create two simple QoS rules. A new QoS Policy always includes a Default Rule (see Default Rule).
The New Policy window opens.
The new Policy is created together with a Default Rule and is displayed in the QoS tab.
When you create a new QoS Policy, the system automatically adds a default rule, which must always be the last rule in the Policy. Make sure that you add your new rules above the default rule.
Create these two rules: Web Rule and RealAudio Rule.
Do this procedure again for RealAudio Rule.
A new rule has the default values assigned by the administrator. The next procedure describes how to change these rules to the values shown in the table below.
Changing Rules Default Values
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Web Rule |
Any |
Any |
HTTP |
Weight 35 |
RealAudio Rule |
Any |
Any |
RealAudio |
Weight 5 |
Default |
Any |
Any |
Any |
Weight 10 |
The system automatically assigns the default parameters as defined in the Global Properties > QoS to new rules. Use this procedure to change these rules to the values shown in the table below.
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Web Rule |
Any |
Any |
HTTP |
Weight 35 |
RealAudio Rule |
Any |
Any |
RealAudio |
Weight 5 |
Default |
Any |
Any |
Any |
Weight 10 |
To change the properties in a rule:
Select Add Objects, and then select HTTP from the list.
Do this procedure again for the RealAudio and Default rules.
Usually, a full Rule Base will not explicitly define rules for all the "background" services (such as DNS and ARP). Background services are handled by the Default rule.
The structure of the Rule Base is shown at the left of the window as a tree, with the Default Rule at the bottom. (For a description of the Rule Base window, see Basic Policy Management).
Connections receive bandwidth according to the weights (priority) assigned to the rules that apply to them. The table below describes what occurs when there are four active connections. Note that bandwidth allocation is constantly changing.
Service Rules - Four Active Connections
Connections |
Relevant rule |
Bandwidth |
Comments |
|---|---|---|---|
HTTP |
Web Rule |
70% |
35 / 50 (the total weights) |
RealAudio |
RealAudio Rule |
10% |
5 / 50 |
FTP |
Default |
sharing 20% |
10 /50; a rule applies to all the connections together |
TELNET |
Default |
sharing 20% |
10 /50; a rule applies to all the connections together |
Bandwidth is allocated between connections according to relative weight. As connections are opened and closed, QoS changes the bandwidth allocation according to the QoS Policy.
For example:
Service Rules - Two Active Connections
Connections |
Relevant rule |
Bandwidth |
Comments |
|---|---|---|---|
HTTP |
Web Rule |
87/5% |
35 / 40 (the total weights) |
RealAudio |
RealAudio Rule |
12.5% |
5 / 40 |
Although RealAudio is assigned a very small weight compared to HTTP, it will not be starved of bandwidth no matter how heavy the HTTP traffic.
In practice, you will probably want to give a high relative weight to interactive services such as TELNET, which transfers small amounts of data but involves users issuing commands.
The second part of the QoS Policy (Marketing must be allocated more bandwidth than Engineering) is implemented by these rules:
Marketing is Allocated More Bandwidth Than Engineering
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Marketing Rule |
Marketing |
Any |
Any |
Weight 30 |
Engineering Rule |
Engineering |
Any |
Any |
Weight 20 |
Default |
Any |
Any |
Any |
Weight 10 |
Using the same principles described in To Create a New Rules and To Modify New Rules, create new rules in SmartConsole and change them to match the values shown in the table above. The effect of these rules is equivalent to the rules shown here:
Connections |
Relevant rule |
Bandwidth |
Comments |
|---|---|---|---|
HTTP |
Web Rule |
70% |
35 / 50 (the total weights) |
RealAudio |
RealAudio Rule |
10% |
5 / 50 |
FTP |
Default |
sharing 20% |
10 /50 A rule applies to all the connections together |
TELNET |
Default |
sharing 20% |
10 /50 A rule applies to all the connections together |
Except for:
The table below shows all the rules in one Rule Base.
All the Rules Together
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Web Rule |
Any |
Any |
HTTP |
Weight 35 |
RealAudio Rule |
Any |
Any |
RealAudio |
Weight 5 |
Marketing Rule |
Marketing |
Any |
Any |
Weight 30 |
Engineering Rule |
Engineering |
Any |
Any |
Weight 20 |
Default |
Any |
Any |
Any |
Weight 10 |
In this Rule Base, bandwidth allocation is based both on sub-networks and on services.
In the Rule Base shown below:
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Web Rule |
Any |
Any |
HTTP |
Weight 35 |
RealAudio Rule |
Any |
Any |
RealAudio |
Weight 5 |
Marketing Rule |
Marketing |
Any |
Any |
Weight 30 |
Engineering Rule |
Engineering |
Any |
Any |
Weight 20 |
Default |
Any |
Any |
Any |
Weight 10 |
In a production environment, a connection can match more than one rule. QoS works according to a first rule match principle. Each connection is examined against the QoS Policy and receives bandwidth according to the Action defined in the first rule that is matched.
If a user in Marketing initiates an HTTP connection, the connection matches the Web Rule and the Marketing Rule. The Web Rule comes before the Marketing Rule in the Rule Base, so the connection is matched to the Web Rule and given a weight of 35.
To differentiate HTTP traffic by source, create sub-rules for the Web Rule. See Sub-Rules.
Bandwidth allocation can also be defined using guarantees and limits. You can define guarantees and limits for rules or for individual connections in a rule.
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Web Rule |
Any |
Any |
HTTP |
Weight 35 |
RealAudio Rule |
Any |
Any |
RealAudio |
Weight 5 |
Marketing Rule |
Marketing |
Any |
Any |
Weight 30 |
Engineering Rule |
Engineering |
Any |
Any |
Weight 20 |
Default |
Any |
Any |
Any |
Weight 10 |
The Web Rule shown in the Rule Base allocates 35% of available bandwidth to all the HTTP connections combined. The actual bandwidth allocated to connections that match this rule depends on:
Note: 35% of available bandwidth (specified in the example above) is assured to Web Rule. Web Rule will get more bandwidth if there are fewer connections matched to other rules, but never less than 35%.
As an alternative to relative weights, a guarantee can be used to specify bandwidth as an absolute value (in Bytes per second). In this table, Web Rule is guaranteed 20 KBps:
Guarantee Example
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Web Rule |
Any |
Any |
HTTP |
Guarantee 20 KBps Weight 35 |
RealAudio Rule |
Any |
Any |
RealAudio |
Weight 5 |
Marketing Rule |
Marketing |
Any |
Any |
Weight 30 |
Engineering Rule |
Engineering |
Any |
Any |
Weight 20 |
Default |
Any |
Any |
Any |
Weight 10 |
Connections matched to Web Rule will receive a total bandwidth of 20 KBps. Remaining bandwidth will be allocated to all the rules, Web Rule included, according to their weights.
For more on guarantees and limits, see Examples: Guarantees and Limits and Bandwidth Allocation and Rules.
Sub-rules are rules nested in a rule. For example, you can create a sub-rule that allocates more bandwidth to HTTP connections that originate in Marketing. Connections whose Source is marketing receive more bandwidth than other HTTP traffic. In this example, the marketing sub-rule and default sub-rule is below the Web Rule:
Defining Sub-Rules
Rule Name |
Source |
Destination |
Service |
Action |
|---|---|---|---|---|
Web Rule |
Any |
Any |
|
Weight 20 |
Start of Sub-Rule |
||||
Marketing HTTP |
Marketing |
Any |
Any |
Weight 10 |
Default |
Any |
Any |
Any |
Weight 1 |
End of Sub-Rule |
||||
Bandwidth is allocated to Web Rule according to its weight (20). This weight is divided between its sub-rules in a 10:1 ratio. Connections below Web Rule are allocated bandwidth according to the weights specified:
Note:
To create a sub-rule:
To install a QoS Policy:
Note - By default, no gateways are selected for QoS. You must select them manually.
If the installation is successful, the new Policy is enforced by the Security Gateways on which it is installed. If installation fails, do these steps to see the error messages:
In the Install Policy Details window, click the ^ icon in the Status column to see the error messages. You must resolve all errors before you can successfully install the Policy.