Managing Threat Prevention
The Threat Prevention Overview Pane
In the Threat Prevention page, you can quickly see the gateways in your organization that are enforcing Threat Prevention Software Blades and malware details. Use the windows for the most urgent or commonly-used management actions.
To customize windows you see in the Overview pane:
- In the pane, click .
- Select or clear the windows to show or hide them.
- To restore the original view, click .
- Click .
My Organization
The window shows the Threat Prevention Software Blades that are enabled on the Security Gateways.
- Click to open the window in the Threat Prevention tab
- Click to open the window of a Security Gateway or to create a new one
Messages and Action Items
The window includes:
- A direct link to Check Point for reporting malicious files that were not identified as such.
- A search field that lets you enter a malware name to get a detailed description of the malware and severity, family name, and type details. The system queries the Threat Wiki for this information.
- Shows if a new Anti-Bot and Anti-Virus update package is available.
- Shows if Security Gateways require renewed licenses and/or contracts.
Statistics
The window shows up-to-the-minute statistics in timeline wheels for one of these malware threats:
- - The Anti-Bot Software Blade gives protection against bot attacks.
- - The Anti-Virus Software Blade gives protection against known malicious software and code.
- - The Threat Emulation Software Blade identifies and gives protection against new malicious software and code.
This window also shows statistics for:
- Incidents - Viruses or bots detected by the system.
- Detected hosts - Hosts that have been compromised with traffic containing a virus or bot. The number of detected hosts shown is related to the Protected Scope values (the network objects you want to protect) in the policy. For example, if the protected scope of a rule refers to the internal network, the number of detected hosts in the time wheels will be from the internal network.
The timeline wheels are grouped according to:
- Selected time interval - hour, day, week or month
- Severity - color-coded according to critical, high, medium and low
When you hover over a timeline wheel you get drilled-down information for the selected time interval. For example, if your selected time interval is , you will see 7 timeline wheels for each day. When you hover over a wheel, you will see the breakdown of the number of incidents or detected hosts according to each severity.
This window also has links to open to see Threat Prevention logs and to see traffic graphs and analysis.
The bottom part of the window shows a time-line of the selected time interval.
To show statistics by incidents or detected hosts:
- In the window, select the time interval from the list.
- Select whether to show incidents or detected hosts from the list.
- To refresh the list, click the refresh icon.
Malware Activity
The window shows you the originating regions of malware, their corresponding IP addresses and URLs, and outgoing emails that were scanned.
- - Pinpoints regions in the world that are attacking your organization and the corresponding number of incidents. This information comes from aggregated data on suspicious URLs and IPs.
- - Shows details for the pinpointed regions in the Attack Map. These details include the specified URLs or IP addresses, the number of attempts and the severity.
- - Shows the number of outgoing emails scanned from when the Anti-Bot and Anti-Virus Software Blades were activated. This window does not show the results of emails scanned by Threat Emulation.
RSS Feeds
Shows RSS feeds with malware related information. When you click a link, it opens the Check Point Threat Wiki.
The Check Point ThreatCloud
To continuously improve our Threat Prevention products, Security Gateways can automatically send anonymous information about feature usage, infection details, and end-user product customization to the Check Point . The Security Gateway does not collect or send any personal data.
Participating in Check Point information collection is a unique opportunity for Check Point customers to be a part of a strategic community of advanced security research. Your participation in this network allows you to contribute data to Check Point for security research. This research aims to improve coverage, quality, and accuracy of security services and obtain valuable information for organizations.
Data Check Point Collects
When you enable information collection, the Check Point Security Gateway collects and securely submits event IDs, URLs, and external IPs to the Check Point Lab regarding potential security risks.
For example:
<entry engineType="3" sigID="-1" attackName="CheckPoint - Testing Bot" sourceIP="7a1ec646fe17e2cd" destinationIP="d8c8f142" destinationPort="80" host="www.checkpoint.com" path="/za/images/threatwiki/pages/TestAntiBotBlade.html" numOfAttacks="20" />
The above is an example of an event that was detected by a Check Point Security Gateway. It includes the event ID, URL, and external IP addresses. Note that the above data does not contain any confidential information or internal resource information. The source IP address is obscured. Information sent to the Check Point Lab is stored in an aggregated form.
To configure the Security Gateway to share information with the Check Point ThreatCloud:
- Double-click the Security Gateway.
The gateway window opens and shows the page.
- Configure the settings for the Anti-Bot and Anti-Virus Software Blades.
- From the navigation tree click .
The page opens.
- To configure a Security Gateway to share Anti-Bot and Anti-Virus information with the ThreatCloud, select .
- To disable the Security Gateway to share Anti-Bot and Anti-Virus information with the ThreatCloud, clear .
- Configure the settings for the Threat Emulation Software Blade.
Note: These settings are not relevant when you are using the ThreatCloud emulation service, the files and information are sent to the ThreatCloud service for emulation.
- From the navigation tree click .
The page opens.
- To configure a Security Gateway to share Threat Emulation information with the ThreatCloud, select .
- Select to send malware files that the Threat Prevention Software Blade identifies to the ThreatCloud
- To disable the Security Gateway to share Threat Emulation information with the ThreatCloud, clear .
- Click .
The ThreatCloud Repository
The ThreatCloud repository contains more than 250 million addresses that were analyzed for bot discovery and more than 2,000 different botnet communication patterns. The ThreatSpect engine uses this information to classify bots and viruses.
For the reputation and signature layers of the ThreatSpect engine, each Security Gateway also has:
- A local database, the Malware database that contains commonly used signatures, URLs, and their related reputations. You can configure automatic or scheduled updates for this database.
- A local cache that gives answers to 99% of URL reputation requests. When the cache does not have an answer, it queries the ThreatCloud repository.
- For Anti-Virus - the signature is sent for file classification.
- For Anti-Bot - the host name is sent for reputation classification.
Access the ThreatCloud repository from:
- - From the Anti-Bot and Anti-Virus Rule Base in SmartDashboard, click the plus sign in the column, and the Protection viewer opens. From there you can add specific malwares to rule exceptions when necessary.
- - A tool to see the entire Malware database. Open it from the Threat Wiki pane in the Threat Prevention tab or from the Check Point website.
The Threat Wiki
The Threat Wiki is an easy to use tool that lets you search and filter the ThreatCloud repository to find more information about identified malware.
- Learn about malware.
- Filter by category, tag, or malware family.
- Search for a malware.
You can access the Threat Wiki from:
- The Threat Prevention tab
- The Check Point website
- SmartEvent
- Right-click an event and select .
- Click the malware protection link in the event log.
- Select from the Anti-Virus or Anti-Bot tab in the event log.
- SmartView Tracker - Click the malware protection link in the field of a log record.
Updating the Malware database
The Malware database automatically updates regularly to make sure that you have the most current data and newly added signatures and URL reputations in your Anti-Bot and Anti-Virus policy.
The Malware database only updates if you have a valid Anti-Bot, Threat Emulation and/or Anti-Virus contract.
By default, updates run on the Security Gateway every two hours. You can change the update schedule or choose to manually update the Security Gateway. The updates are stored in a few files on each Security Gateway.
Connecting to the Internet for Updates
The Security Gateway connects to the internet to get the Malware database updates. To make sure that it can get the updates successfully:
- Make sure that there is a DNS server configured.
- Make sure a proxy is configured for each gateway, if necessary.
To configure a proxy:
- The > pane shows if the Security Gateway uses a proxy to connect to the internet or not.
- Click and select a gateway from the list.
- Click and configure the proxy for the gateway.
- Click .
Scheduling Updates
You can change the default automatic scheduling. If you have Security Gateways in different time zones, they will not be synchronized when one updates and the other did not yet update.
To change the update schedule:
- Select > >
The page opens.
- Make sure that is selected.
- Next to the option, click .
The window for the Anti-Bot and Anti-Virus database opens.
- Configure the automatic update settings to update the database:
- To update once a day, select and enter the time of day
- To update multiple times a day, select and set the time interval
- To update once or more for each week or month:
- Select and enter the time of day.
- Click .
- Click or .
- Select the applicable days.
- Click and then install the Threat Prevention policy.
Exception Groups Pane
The pane lets you define exception groups. When necessary, you can create exception groups to use in the Rule Base. An exception group contains one or more defined exceptions. This option facilitates ease-of-use so you do not have to manually define exceptions in multiple rules for commonly required exceptions. You can choose to which rules you want to add exception groups. This means they can be added to some rules and not to others, depending on necessity.
The pane shows a list of exception groups that have been created, what rules are using them, and any comments associated to the defined group. The Exceptions Groups pane contains these options:
Option
|
Meaning
|
New
|
Creates a new exception group.
|
Edit
|
Modifies an existing exception group.
|
Delete
|
Deletes an exception group.
|
Search
|
Search for an exception group.
|
Global Exceptions
The system comes with a predefined group named Global Exceptions. Exceptions that you define in Global Exceptions are automatically added to every rule in the Rule Base. For other exception groups, you can decide to which rules to add them.
Exception Groups in the Rule Base
Global exceptions and other exception groups are added as shaded rows below the rule in the Rule Base. Each exception group is labeled with a tab that shows the exception group's name. The exceptions within a group are identified in the column using the syntax:
E - <rule number>.<exception number>, where E identifies the line as an exception. For example, if there is a Global Exceptions group that contains two exceptions, all rules will show the exception rows in the Rule Base column as E-1.1 and E-1.2. Note that the numbering of exception varies when you move the exceptions within a rule.
To view exception groups in the Rule Base:
Click the plus or minus sign next to the rule number in the . column to expand or collapse the rule exceptions and exception groups.
Creating Exception Groups
When you create an exception group, you create a container for adding one or more exceptions. After you create the group, add exceptions to them. You can then add the group to rules that require the exception group in the Threat Prevention Rule Base.
To create an exception group:
- In the Threat Prevention tab, select .
- Click .
- From the window, enter:
- - Mandatory, cannot contain spaces or symbols
- - Optional color for SmartDashboard object mapping
- - Optional free text
- Click .
Adding Exceptions to Exception Groups
To use exception groups, you must add exception rules to them. For details on the columns, see Parts of the Rules.
To add exceptions to an exception group:
- In the Threat Prevention tab, select .
- From the tree, select the group to which you want to add exceptions.
A pane opens showing the exception group name.
- Use the and icons to add exceptions.
Adding Exception Groups to the Rule Base
To add an exception group to the Rule Base:
- In the pane, select the rule to which you want to add an exception group.
- Click >.
- Select the , , or option according to where you want to place the exception group.
The window opens.
- Select the group from the list and click .
The exception group is added to the Threat Prevention policy.
- Click to install the Anti-Bot, Threat Emulation,
 and Anti-Virus policy. and Anti-Virus policy.The Anti-Bot, Threat Emulation and Anti-Virus Software Blades have a dedicated policy. You can install this policy installation separately from the policy installation of the other Software Blades.
You can update the Anti-Bot, Threat Emulation and Anti-Virus Rule Base to give immediate coverage for new malware threats. Install only the Threat Prevention policy to minimize the impact on the Security Gateways.
To install the Anti-Bot and Anti-Virus policy:
- From the tab > pane, click .
- Select the relevant options:
- Installs the policy on all Security Gateways that have Anti-Bot, Threat Emulation, and Anti-Virus enabled.
- - Select the applicable Security Gateways.
- - Install the policy on the selected Security Gateways without reference to the other targets. A failure to install on one Security Gateway does not affect policy installation on other gateways.
If the gateway is a member of a cluster, install the policy on all the members. The Security Management Server makes sure that it can install the policy on all the members before it installs the policy on one of them. If the policy cannot be installed on one of the members, policy installation fails for all of them.
- - Install the policy on all installation targets. If the policy fails to install on one of the Security Gateways, the policy is not installed on other targets of the same version.
- Click .
Creating Exceptions from Logs or Events
In some cases, after evaluating a log in SmartView Tracker or an event in SmartEvent, it may be necessary to update a rule exception in the SmartDashboard Rule Base. You can do this directly from within SmartView Tracker or SmartEvent. You can apply the exceptions to a specified rule or apply the exception to all rules that shows under Global Exceptions.
To update a rule exception or global exception:
- Right-click a SmartView Tracker log entry or a SmartEvent event.
- Select .
SmartDashboard opens and shows an window in the Threat Prevention Rule Base. These details are shown:
- - The name of the protection. Details are taken from the ThreatCloud repository or, if there is no connectivity, from the log.
- - The scope is taken from the log. If there is no related host object, an object is created automatically after you click . Click the plus sign to add additional objects.
- - Shows by default. You can use the plus sign to add gateways.
- Select an option:
- - If you want the to apply only to the related rule.
- - If you want the to apply to all rules. The exception is added to the > pane.
- Click .
The exception is added to the Rule Base. The is set to by default. Change if necessary.
- Click to install the Anti-Bot, Threat Emulation,
 and Anti-Virus policy. and Anti-Virus policy.The Anti-Bot, Threat Emulation and Anti-Virus Software Blades have a dedicated policy. You can install this policy installation separately from the policy installation of the other Software Blades.
You can update the Anti-Bot, Threat Emulation and Anti-Virus Rule Base to give immediate coverage for new malware threats. Install only the Threat Prevention policy to minimize the impact on the Security Gateways.
To install the Anti-Bot and Anti-Virus policy:
- From the tab > pane, click .
- Select the relevant options:
- Installs the policy on all Security Gateways that have Anti-Bot, Threat Emulation, and Anti-Virus enabled.
- - Select the applicable Security Gateways.
- - Install the policy on the selected Security Gateways without reference to the other targets. A failure to install on one Security Gateway does not affect policy installation on other gateways.
If the gateway is a member of a cluster, install the policy on all the members. The Security Management Server makes sure that it can install the policy on all the members before it installs the policy on one of them. If the policy cannot be installed on one of the members, policy installation fails for all of them.
- - Install the policy on all installation targets. If the policy fails to install on one of the Security Gateways, the policy is not installed on other targets of the same version.
- Click .
Gateways Pane
The page lists the Security Gateways that use one or more of these Software Blades: Anti-Bot, Threat Emulation, and Anti-Virus. The left pane shows the Security Gateways that use these Software Blades, the right pane shows the Threat Prevention details for the selected Security Gateway. Threat Emulation is supported only on Security Gateways and Emulation appliance in the internal network.
Option
|
Meaning
|
Add
|
Add a Security Gateway or create a new Security Gateway
|
Edit
|
Modify an existing Security Gateway
|
Remove
|
Disable the Threat Prevention Software Blades on the selected Security Gateway
|
Actions > Update Threat Emulation Images
|
Connect to the ThreatCloud to download new operating system images
|
Search
|
Search for a Security Gateway
|
The left pane shows the name, IPv4 and IPv6 address for each Security Gateway. These columns also show the following information about the Security Gateways:
Column
|
Description
|
Anti-Bot
|
If Anti-Bot is enabled
|
Anti-Virus
|
If Anti-Virus is enabled
|
Threat Emulation
|
If Threat Emulation is enabled
|
Update Status
|
If the Malware database is up to date on the Security Gateway or if an update is necessary
|
The right pane shows the details for the Threat Prevention Software Blades that are enabled on the Security Gateway.
Protections Browser
The Protections browser shows the Threat Prevention Software Blades protection types and a summary of important information and usage indicators.
Column
|
Description
|
Protection
|
Shows the name of the protection type. A description of the protection type is shown in the bottom section of the pane.
The Malicious Activity and Unusual Activity protections contain lists of protections. Click the plus sign to see them.
|
Blade
|
Shows if the protection type belongs to the Anti-Bot, Threat Emulation or Anti-Virus Software Blade.
|
Engine
|
Shows the layer of the ThreatSpect engine that handles the protection type.
|
Known Today
|
Shows the number of known protections.
|
Performance Impact
|
Shows how much the group of protections affects the performance of the Security Gateway. If possible, shows an exact figure.
|
<Profile Name>
|
Shows the activation setting of the protection type for each defined profile. The values shown here are calculated based on the settings of the confidence levels in the profile and the specified protections that match that confidence level.
You can right-click the activation setting and select a different setting if required. This overrides the setting in the original profile.
|
Searching Protections
You can search the Protections page by protection name, engine, or by any information type that is shown in the columns.
To filter by protection name:
Sorting Protections
You can sort the Protection, Blade, Engine, Known Today columns in the Protections list.
To sort the protections list by information:
- Click the column header of the information you want.
The Policy Rule Base
The Threat Prevention policy determines how the system inspects connections for bots and viruses. The primary component of the policy is the Rule Base. The rules use the Malware database and network objects.
If you enable Identity Awareness on your gateways, you can also use Access Role objects as the scope in a rule. This lets you easily make rules for individuals or different groups of users.
There are no implied rules in the Rule Base. All traffic is allowed unless it is explicitly blocked.
For examples of how to create different types of rules, see the applicable section for the Threat Prevention Software Blade:
Predefined Rule
When you enable a Threat Prevention Software Blade, a predefined rule is added to the Rule Base. The rule defines that all traffic for all network objects, regardless of who opened the connection, (the protected scope value equals any) is inspected for all protections according to the recommended profile. By default, logs are generated and the rule is installed on all Security Gateways that use a Threat Prevention Software Blade.
The result of this rule (according to the Recommended_Profile) is that:
- All protections that can identify an attack with a high or medium confidence level and have a medium or lower performance impact are set to mode.
- All protections that can identify an attack with a low confidence level and have a medium or lower performance impact are set to mode.
You can see logs related to Threat Prevention traffic in SmartView Tracker and SmartEvent. Use the data there to better understand the use of Threat Prevention Software Blades in your environment and create an effective Rule Base. From SmartEvent, you have an option to directly update the Rule Base.
You can add more rules that prevent or detect specified protections or have different tracking settings.
Exception Rules
When necessary, you can add an directly to a rule. An exception lets you set a protection or protections to either detect or prevent for a specified protected scope. For example, if you want to prevent specified protections for a specific user in a rule with a profile that only detects protections. Another example, if you want to detect all protections in an R and D lab network in a rule with a prevent profile.
You can add one or more exceptions to a rule. The exception is added as a shaded row below the rule in the Rule Base. It is identified in the No. column with the rule's number plus the letter E and a digit that represents the exception number. For example, if you add two exceptions to rule number 1, two lines will be added and show in the Rule Base as E-1.1 and E-1.2.
You can use exception groups to group exceptions that you want to use in more than one rule. See the Exceptions Groups Pane.
You can expand or collapse the rule exceptions by clicking on the minus or plus sign next to the rule number in the . column.
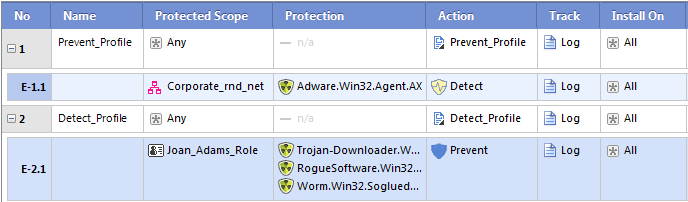
To add an exception to a rule:
- In the pane, select the rule to which you want to add an exception.
- Click
- Select the , , or option according to where you want to place the exception.
- Enter values for the columns. Including these:
- Change it to reflect the relevant objects.
- - Click the plus sign in the cell to open the Protections viewer. Select the protection(s) and click .
- Click to install the Anti-Bot, Threat Emulation,
 and Anti-Virus policy. and Anti-Virus policy.The Anti-Bot, Threat Emulation and Anti-Virus Software Blades have a dedicated policy. You can install this policy installation separately from the policy installation of the other Software Blades.
You can update the Anti-Bot, Threat Emulation and Anti-Virus Rule Base to give immediate coverage for new malware threats. Install only the Threat Prevention policy to minimize the impact on the Security Gateways.
To install the Anti-Bot and Anti-Virus policy:
- From the tab > pane, click .
- Select the relevant options:
- Installs the policy on all Security Gateways that have Anti-Bot, Threat Emulation, and Anti-Virus enabled.
- - Select the applicable Security Gateways.
- - Install the policy on the selected Security Gateways without reference to the other targets. A failure to install on one Security Gateway does not affect policy installation on other gateways.
If the gateway is a member of a cluster, install the policy on all the members. The Security Management Server makes sure that it can install the policy on all the members before it installs the policy on one of them. If the policy cannot be installed on one of the members, policy installation fails for all of them.
- - Install the policy on all installation targets. If the policy fails to install on one of the Security Gateways, the policy is not installed on other targets of the same version.
- Click .
Copying an Exception to an Exception Group
You can copy an exception you have created to be a part of an existing exception group or multiple groups. If necessary, you can create a new group with this option.
To copy an exception to an exception group:
- In the pane, select the exception rule in the Rule Base.
- Select > .
The Select Exception Group window opens.
- Select the group or groups from the list or click to create a new group.
- Click .
Converting Exceptions into an Exception Group
You can select multiple exceptions in the Rule Base and create an exception group. The exceptions can be from different rules. When you convert exceptions into a group, they are removed from the Rule Base as individual exceptions and exist only as a group.
To create an exception group from multiple exceptions:
- In the pane, select the exception rules in the Rule Base.
- Select > .
The New Exception Group window opens.
- Enter a and (optional).
- Click .
Parts of the Rules
The columns of a rule define the traffic that it matches and what is done to that traffic.
Number (No.)
The sequence of rules is important because the first rule that matches traffic according to a protected scope and profile is applied.
For example, if rules 1 and 2 share the same protected scope and a profile in rule 1 is set to detect protections with a medium confidence level and the profile in rule 2 is set to prevent protections with a medium confidence level, then protections with a medium confidence level will be detected based on rule 1.
Name
Give the rule a descriptive name. The name can include spaces.
Double-click in the column of the rule to add or change a name and click .
Protected Scope
Anti-Bot, Threat Emulation, and Anti-Virus rules include a Protected Scope parameter. Threat Prevention inspects traffic to and/or from all objects specified in the , even when the specified object did not open the connection. This is an important difference from the object in Firewall rules, which defines the object that opens a connection.
For example, the Protected Scope includes a Network Object named MyWebServer. Threat Prevention inspects all files sent to MyWebServer for malware threats, even if MyWebServer did not open the connection.
Protected Scope objects can be:
- Network objects, such as Security Gateways, clusters, servers, networks, IP ranges, and so on
- Network object groups
- IP address ranges
- Roles
- Zones
You can set the parameter to . This option lets Threat Prevention inspect traffic based on the direction and interface type as defined by the Profile assigned to the applicable rule. By default, the predefined sets the to .
Traffic Direction and Interface Type Settings
You can configure the traffic direction and Security Gateway interface types that send files to Threat Prevention for inspection. You do this in the section of the or window. The options are:
When you select the option in the section of a rule, the traffic direction and interface type are defined by the assigned to that rule. If you add objects to the Protected Scope in a rule, files that match these objects are inspected for all connections.
Using Protected Scope with SPAN and TAP Configurations
The default global parameter for SPAN and TAP configuration is set to . You can use these commands to configure the Security Gateway to use the Protected Scope settings for SPAN and TAP with Threat Emulation.
fw ctl set int - Changes current settings for SPAN and TAP, does not survive reboot- Change
$FWDIR/module/fwkern.conf - This changes the settings after reboot.
Run these commands to set the SPAN port to use the Policy instead of the global default setting ():
# fw ctl set int te_handle_span_port_interfaces_according_to_topolgy 1
# echo “te_handle_span_port_interfaces_according_to_topolgy=1” >> $FWDIR/module/fwkern.conf
|
Limitations and Troubleshooting
- If no topology is defined for the Security Gateway interfaces, all traffic is inspected or sent for emulation
- When you upgrade from R76 and earlier, the option is set to by default
- When the topology of the interfaces is defined and you are using SPAN or TAP modes, it is possible that some of the connections are not defined correctly
Protection
The Protection column shows the Anti-Bot, Threat Emulation, and Anti-Virus protections that you choose to include.
- For , this field is always set to and cannot be changed. Protections for Rule Base rules are defined in the configured profile (in the Action column).
- For and , this field can be set to one or more specified protections.
To add a protection to an exception:
- Put your mouse in the column and click the plus sign to open the Protection viewer.
For each protection, the viewer shows a short description, malware family, type and severity level.
- To add a protection to the exception, click the checkbox in the list.
- To see the details of an item without adding it to the rule, click the name of the Available item.
- To see all malwares in a risk level, select the level from the field in the toolbar.
- Click .
To search for a malware in the Protection viewer:
- Put your mouse in the column and click the plus sign to open the Protection viewer.
- Enter the malware name in the search box.
The results show in the list.
Action
Action refers to how traffic is inspected.
- For , this is defined by the profile. The profile contains the configuration options for different confidence levels and performance impact.
- For and , the action can be set to or .
To select a profile for a rule:
- Click in the column.
- Select an existing profile from the list, create a new profile, or edit the existing profile.
Track
Choose if the traffic is logged in SmartView Tracker or if it triggers other notifications. Click in the column and the options open. The options include:
- - Logs the event and executes a command, such as show a popup window, send an email alert, or run a user-defined script as defined in > > > .
- - Records event details in SmartView Tracker. This option is useful for getting general information on network traffic.
- - Does not record the event.
- - Allows the packets relevant to the connection to be captured for analysis at a later time. The packet capture can be viewed from the event in SmartView Tracker. This can be configured only for rules (not rule exceptions). To configure packet capture, select any tracking action other than and then select .
Install On
Choose which gateways the rule will be installed on. The default is All (all gateways that have Anti-Bot, Threat Emulation, and Anti-Virus enabled). Put your mouse in the column and a plus sign shows. Click the plus sign to open the list of available gateways and select.
Threat Prevention and UserCheck
For more about using UserCheck objects and settings, see the UserCheck chapters in the R77 Data Loss Prevention Administration Guide. For each Threat Prevention profile, you can define the action that is taken when a malicious file or activity is identified.
Action
|
Description
|
Ask
|
The Software Blade blocks the file or traffic and until the user verifies that it should be sent. The user decides whether the file or traffic should be allowed or not. The decision itself is logged in SmartView Tracker under the User Actions category.
|
Prevent
|
The Software Blade blocks the file or traffic. You can show a UserCheck Prevent message to the user.
|
Detect
|
The Software Blade allows the file or traffic. The event is logged in SmartView Tracker and is available for your review and analysis in SmartReporter and SmartEvent.
|
Using the Threat Prevention UserCheck Pane
On the page, you can create, edit, and preview UserCheck interaction objects and their messages. It has these options:
Option
|
Meaning
|
New
|
Creates a new UserCheck object
|
Edit
|
Modifies an existing UserCheck object
|
Delete
|
Deletes an UserCheck object
|
Clone
|
Clones the selected UserCheck object.
|
These are the default UserCheck messages:
Name
|
Action Type
|
Description
|
|
|
Block
|
Shows when a request is blocked.
|
|
|
Ask
|
Shows when the action for the rule is . It informs users what the company policy is for that site and they must click to continue to the site.
|
|
|
Cancel
|
Shows after a user gets an Inform or Ask message and clicks Cancel.
|
and pages include a button that users can click to cancel the request.
You can preview each message page in these views:
- - How the message shows in a web browser on a PC or laptop
- - How the message shows in a web browser on a mobile device
Configuring the Security Gateway for UserCheck
Enable or disable UserCheck directly on the Security Gateway. The page in the Software Blade tab shows the Security Gateways that use that Software Blade. Make sure the UserCheck is enabled on each Security Gateway in the network. The Security Gateway has an internal persistence mechanism that preserves UserCheck notification data if the Security Gateway or cluster reboots. Records of a user answering or receiving notifications are never lost.
When you configure the Main URL of the UserCheck portal, if it is set to an external interface, the option must be set to one of these:
If users connect to the Security Gateway remotely, make sure that the Security Gateway internal interface (in the page) is the same as the Main URL for the UserCheck portal.
If you are using internal encrypted traffic, add a new rule to the Firewall Rule Base. This is a sample rule:
|
|
|
|
|
|
|
Source
|
Destination
|
VPN
|
Service
|
Action
|
Any
|
Security Gateway on which UserCheck client is enabled
|
Any Traffic
|
UserCheck
|
Accept
|

|
Note - When you enable UserCheck on an IP appliance, make sure to set the Voyager management application port to a port other than 443 or 80.
|
To configure UserCheck on a Security Gateway:
- From the tree, double-click to Security Gateway.
The window opens.
- From the navigation tree, click UserCheck.
The page opens.
- Select .
- Enter the settings for the UserCheck portal:
- In the field, enter the primary URL for the web portal that shows the UserCheck notifications.
Note - The field must be manually updated if:
- The Main URL field contains an IP address and not a DNS name.
- You change a gateway IPv4 address to IPv6 or vice versa.
- In , enter the IP address for the portal.
- Optional: Click to add URL aliases that redirect different hostnames to the .
The aliases must be resolved to the portal IP address on the corporate DNS server
- In the area, click to import a certificate that the portal uses to authenticate to the server.
By default, the portal uses a certificate from the Check Point Internal Certificate Authority (ICA). This might generate warnings if the user browser does not recognize Check Point as a trusted Certificate Authority. To prevent these warnings, import your own certificate from a recognized external authority.
- In the area, click to configure interfaces on the Security Gateway through which the portal can be accessed. These options are based on the topology configured for the Security Gateway. Users are sent to the UserCheck portal if they connect:
- Click .
- Install the Policy.
Creating Threat Prevention UserCheck Objects
Create a UserCheck Interaction object from the page or Threat Prevention Software Blade profile . You can create these objects for Threat Prevention profiles:
- - Message that is shown for traffic that matches the Prevent action
- - Message that is shown for traffic that matches the Ask action
You can write the UserCheck message with formatting buttons, like Bold and bullets, or directly enter HTML code.
To change text input modes:
Right-click a text field and select the option:
- - Enter HTML code
- - Enter text with formatting buttons and options
This procedure shows how to create an object from the page in the Threat Prevention tab.
To create a new Threat Prevention UserCheck object:
- From the tab, click .
The page opens and shows the UserCheck objects for Threat Prevention rules.
- Click > or .
The window opens.
- Enter a .
- Optional: Click and select one or more languages for the message.
The default language for messages is English.
- Enter the text for the message.
-
-
- - Dynamic text such as: Original URL, Source IP address, and so on
- t - Such as: Confirm check box, Report Wrong Category and so on
- Optional: Click to add a graphic to the message.
The size of the graphic must be 176 x 52 pixels.
- Click to see the message in the default Internet browser.
- You can also configure one or more of these options for UserCheck messages:
- Click .
Using a Fallback Action
Configure the default action for an Ask UserCheck object if the user cannot see the message. You can select one of these options:
- - The connection or traffic is blocked and does not enter the internal network
- - The connection or traffic is allowed to enter the internal network
To configure a fallback action for an Ask object:
- From the navigation tree, click .
- Select to or traffic when the user cannot see the UserCheck message.
Redirecting to an External Portal
You can configure UserCheck to redirect the user to an external UserCheck portal and the user does not see this UserCheck message.
To redirect a user to an external portal:
- From the navigation tree, click .
- Select .
- In , enter the URL for the external portal.
The specified URL can be an external system that obtains authentication credentials from the user, such as a user name or password. It sends this information to the Security Gateway.
- Optional: Select to add an incident ID to the end of the URL query.
Configuring User Interaction
You can configure the necessary user interaction for an Ask UserCheck object. The traffic is allowed only after the user does the necessary actions.
The UserCheck message can contain these items that require user interaction (shown with sample messages):
- - I am ignoring the warning
- - Enter the reason that you are ignoring the Threat Prevention warning
To configure the necessary user interaction for an Ask object:
- From the navigation tree, click .
- Select one or more of these options:
The traffic or connection is blocked until the user does the necessary actions.
Profiles Pane
The pane lets you configure profiles. These profiles are used in enforcing rules in the Rule Base.
The pane shows a list of profiles that have been created, their confidence levels, and performance impact settings. The Profiles pane contains these options:
Option
|
Meaning
|
New
|
Creates a new profile.
|
Edit
|
Modifies an existing profile.
|
Delete
|
Deletes a profile.
|
Search
|
Search for a profile.
|
Actions > Clone
|
Creates a copy of an existing profile.
|
Actions > Where Used
|
Shows you reference information for the profile.
|
Actions > Last Modified
|
Shows who last modified the selected profile, when and on which client.
|
A profile is a set of configurations based on:
- Activation settings (prevent, detect, or inactive) for each confidence level of protections that the ThreatSpect engine analyzes
- Anti-Bot Settings
- Anti-Virus Settings
- Threat Emulation Settings
- Indicators configuration
- Malware DNS Trap configuration
- Links inside mail configuration
Without profiles, it would be necessary to configure separate rules for different activation settings and confidence levels. With profiles, you get customization and efficiency.
Activation Settings
- - The protection action that blocks identified virus or bot traffic from passing through the gateway. It also logs the traffic, or tracks it, according to configured settings in the Rule Base.
- - The protection action that allows identified virus or bot traffic to pass through the gateway. It logs the traffic, or tracks it, according to configured settings in the Rule Base.
- - The protection action that deactivates a protection.
Confidence Level
The confidence level is how confident the Software Blade is that recognized attacks are actually virus or bot traffic. Some attack types are more subtle than others and legitimate traffic can sometimes be mistakenly recognized as a threat. The confidence level value shows how well protections can correctly recognize a specified attack.
Performance Impact
Performance impact is how much a protection affects the gateway performance. Some activated protections might cause issues with connectivity or performance. You can set protections to not be prevented or detected if they have a higher impact on gateway performance.
There are three options:
- High or lower
- Medium or lower
- Low
The system comes with a Recommended_Profile. It is defined with these parameters and is used in the predefined rule:
- All protections that can identify an attack with a high or medium confidence level and have a medium or lower performance impact are set to mode.
- All protections that can identify an attack with a low confidence level and have a medium or lower performance impact are set to mode.
Creating Profiles
When you create a profile, you create a new SmartDashboard object. Protections that match one of the confidence levels can be set to , or to allow the profile to focus on identifying certain attacks. The profiles can then be used in the Rule Base.
When HTTPS inspection is enabled on the Security Gateway, Threat Emulation and Anti-Virus can analyze the applicable HTTPS traffic.
To create a Threat Prevention profile:
- In the tab, select .
- Click .
- From the window, configure:
- Click .
- Install the Threat Prevention policy.
General Properties
Set the general properties of the profile:
- - Mandatory, cannot contain spaces or symbols
- - Optional color for SmartDashboard object mapping
- - Optional free text
- - Select the Software Blades that this profile defines
Protection Activation
- , , and - The default action that Threat Prevention protections do when they are enabled
- - Traffic is blocked until the user confirms that it is allowed
- - Protections block traffic matching the protection type's definitions
- - Protections allow and track traffic matching the protection type's definitions
- - Protections are deactivated
- - Set the Security Gateway performance impact level when these protections are active
Configuring Anti-Bot Settings
To configure the Anti-Bot settings for a profile:
- Configure the UserCheck settings:
- - Select the UserCheck message that opens for a action.
- - Select the UserCheck message that opens for an action.
- Configure the Suspicious Mail Detection setting:
- - Set the kilobytes for each email that the ThreatSpect engine inspects to check for bot activity.
Note - The feature requires an Anti-Spam license.
Configuring Anti-Virus Settings
You can configure Threat Prevention to exclude files from inspection, such as internal emails and internal file transfers. These settings are based on the interface type (internal or external, as defined in SmartDashboard) and traffic direction (incoming or outgoing).
Before you define the scope for Threat Prevention, you must make sure that your DMZ interfaces are configured correctly. To do this:
- In SmartDashboard, double-click the applicable Security Gateway object.
- In the window, select and then double-click a DMZ interface.
- In the window, select the option.
Do this procedure for each interface that goes to the DMZ.
You can configure the Anti-Virus profile to enable . The Anti-Virus engine unpacks archives and applies proactive heuristics. If you use this feature, it can have an impact on network performance.

|
Note - The MIME Nesting settings are the same for Anti-Virus and Threat Emulation.
|
To configure the Anti-Virus settings for a profile:
- On the tab, select and double-click the applicable Profile.
- Select the options:
- - Select the UserCheck message that opens for a action.
- - Select the UserCheck message that opens for an action.
- In the section, select an interface type and traffic direction option:
- Select the applicable that Anti-Virus scans.
- Optional: Configure how Anti-Virus inspects SMTP traffic.
- Click .
The window opens.
- Configure the settings.
- - For emails that contain nested MIME content, Set the maximum number of levels that the ThreatSpect engine scans in the email.
- - If there are more nested levels of MIME content than the configured amount, select to or the email file.
- Select :
Select , if needed. Remember, it impacts performance.
Click , and in the window that opens, for each file type, select one of the actions:
Click to exit the window.
- Click .
- Click .
To enable Archive Scanning:
- Select
- Click .
- Set the amount in seconds to . The default is 30 seconds.
- Set to block or allow the file . The default is allow.
- Click .
- Click .
Configuring Threat Emulation Settings
You can configure Threat Prevention to exclude files from inspection, such as internal emails and internal file transfers. These settings are based on the interface type (internal or external, as defined in SmartDashboard) and traffic direction (incoming or outgoing).
Before you define the scope for Threat Prevention, you must make sure that your DMZ interfaces are configured correctly. To do this:
- In SmartDashboard, double-click the applicable Security Gateway object.
- In the window, select and then double-click a DMZ interface.
- In the window, select the option.
Do this procedure for each interface that goes to the DMZ.
If there is a conflict between the Threat Emulation settings in the profile and for the Security Gateway, the profile settings are used.

|
Note - The MIME Nesting settings are the same for Anti-Virus and Threat Emulation.
|
To configure the Threat Emulation settings for a profile:
- On the tab, select and double-click the applicable Profile.
- Configure the settings for :
- - Select the UserCheck message that opens for a action
- - Select the UserCheck message that opens for an action
- In the section, select an interface type and traffic direction option:
- Select the applicable to be emulated.
- Configure how Threat Emulation does emulation for SMTP traffic.
- Click .
The window opens.
- Configure the settings.
- - For emails that contain nested MIME content, Set the maximum number of levels that the ThreatSpect engine scans in the email.
- - If there are more nested levels of MIME content than the configured amount, select to or the email file.
- Select the to be emulated.
Configuring the Virtual Environment (Profile)
You can use the window to configure the emulation location and images that are used for this profile.
The section lets you select where the  emulation is done. emulation is done.
- - Files are sent to the Check Point ThreatCloud for emulation. The emulation in the ThreatCloud is identical to a local emulation but it does not use CPU, RAM, and disk space on a local appliance. When you configure ThreatCloud emulation, a secure SSL connection is created between the company's Security Gateway and the ThreatCloud. Files are sent to the ThreatCloud over this secure connection for emulation. The results are sent back to the Security Gateway and the applicable action is done to the file.
- - The Emulation appliance that does the emulation and file analysis. Threat Emulation uses the CPU, RAM and disk space of the appliance to do the emulation.
- - Enable Threat Emulation on a Security Gateway and select the Emulation appliance that does the emulation.
The section lets you select operating system images for emulation. If the images defined in the profile and the Security Gateway or Emulation appliance are different, the profile settings are used.
These are the options to select the emulation images:
- Check Point automatically updates images and adds new ones
- Select the images that are closest to the operating systems for the computers in your organization
To configure the virtual environment settings for the profile:
- From the navigation tree, select > .
The page opens.
- Set the setting:
- To use the Security Gateway settings for the location of the virtual environment, click
- To configure the profile to use a different location of the virtual environment, click and select the applicable option
- Set the setting:
- To use the emulation environments recommended by Check Point security analysts, click
- To select one or more images that are used for emulation, click
Excluding Emails
You can enter email addresses that are not included in Threat Emulation protection. SMTP traffic that is sent to or from these addresses is not sent for emulation.
You can also use a wildcard character to exclude more than one email address from a domain.

|
Note - If you want to do emulation on outgoing emails, make sure that you set the Protected Scope to .
|
To exclude emails from Threat Emulation:
- Select > .
The pane opens.
- Right-click the profile and select .
The page of the profile window opens.
- From the navigation tree, select > .
- In the section, you can enter one or more emails.
Emails and attachments that are sent to these addresses are not sent for emulation.
- In the section, you can enter one or more emails.
Emails and attachments that are received from these addresses are not sent for emulation.
Configuring a Malware DNS Trap
The Malware DNS trap works by configuring the Security Gateway to return a false (bogus) IP address for known malicious hosts and domains. You can use the Security Gateways external IP address as the DNS trap address but:
- Do not use a gateway address that leads to the internal network
- Do not use the gateway internal management address
- If the gateway external IP address is also the management address, select a different address for the DNS trap.
You can also add internal DNS servers to better identify the origin of malicious DNS requests.
Using the Malware DNS Trap you can then detect compromised clients by checking logs with connection attempts to the false IP address.
At the Security Gateway level, you can configure to use the settings defined for the profiles or a specified IP address that is used by all profiles used on the specific gateway.
To set the Malware DNS Trap parameters for the profile:
- - Select to use a Malware DNS Trap to identify compromised clients attempting to access known malicious domains and select which IP address to use:
- - Select and enter a user-defined DNS trap IP address
- - Select or add a new internal DNS server to identify the origin of malicious DNS requests
Use these options to work with the internal DNS server list:
- or - Click to add or edit an internal DNS server to identify the origin of malicious DNS requests.
- - Select a DNS server in the list and click Remove to remove it from the list
- - Enter the name of a DNS server to search for in the list. Results are shown highlighted.
To set the Malware DNS Trap parameters per gateway:
- In SmartDashboard, right-click the gateway object and select .
- From the navigation tree, select .
- In the DNS Redirect Mode section, choose one of the options:
- - Use the Malware DNS Trap IP address configured for each profile.
- - Configure an IP address to be used by all profiles used by this Security Gateway.
- Click .
Configuring Inspection of Links Inside Mail
Inspection of Links Inside Mail scans URL links in the body of email messages, subject, or .txt attachments, and checks them against the URL reputation database. The email messages that contain malicious URL links are blocked.
Inspection of Links Inside Mail is on by default, and scans incoming mail with Anti-Virus Software Blade and outgoing mail with Anti-Bot Software Blade.
To turn Inspection of Links Inside Mail off:
- From the navigation tree in the tab, select .
The page opens.
- Right-click on or for , and select .
Note - for each Software Blade - and , you must turn the separately.
To turn Inspection of Links Inside Mail on:
- From the navigation tree in the tab, select .
The page opens.
- Right-click on or for , and select one of these -
To configure Link Inspection Inside Mail:
- From the navigation tree in the tab, select .
The page opens.
- Select a profile.
- Click .
- In the window that opens, select .
The page opens.
- Configure the settings.
- Click .
Copying Profiles
You can create a copy of a selected profile and then make necessary changes.
To copy a profile:
- In the Threat Prevention tab, select .
- Select the profile you want to copy.
- Click > .
The field shows the name of the copied profile plus . Rename the profile.
- Configure:
- General Properties
- Anti-Bot Settings
- Anti-Virus Settings
- Threat Emulation Settings
- Malware DNS Trap
- Click .
Deleting Profiles
You can delete a profile (except for the profile). But do this carefully, as it can affect Security Gateways, other profiles or SmartDashboard objects.
To delete a profile:
- In the tab, select .
- Select the profile you want to delete and click
 . .This message is shown:
- Click .
If the profile contains references to/from other objects you cannot , another message is shown:
- Click .
The window opens.
- For each object that references the profile, there is a value in the column. If the value is , you can safely delete the profile. If not, find the relationship before you decide to delete this profile.
Sites Pane
The pane shows custom sites, categories and groups that you defined. Select an object in the list and click to change its properties. You can use the toolbar buttons to create, look for, and delete objects.
Creating Threat Prevention Sites
You can create a custom site to use in the Threat Prevention Policy. You can enter the URLs manually or use a CSV (comma separated values) file to add many URLs at one time from an external source.
The .csv file syntax is one URL for each line in the text file. When you use the .csv file option, the URLs are imported when you click . If it is necessary to edit the URLs, click the Applications/Site object in the list and click Edit.
To create a site:
- In the pane, click.
The wizard opens.
- Enter a name for the site.
- Select one of the options:
- - To manually enter a URL.
- - To upload a CSV file with URLs.
- Click .
- Add the URLs to the Site object:
- window - Enter a URL and click .
If you used a regular expression in the URL, click .
Note - Select the checkbox only if the application or site URL is entered as a regular expression using the correct syntax.
- Upload a Sites file window - Browse to the CSV file and upload it.
- Click .
The window opens.
- Click .
You can use this custom site in the Threat Prevention Policy.
Creating Threat Prevention Site Groups
You can create a group of sites to use in the Threat Prevention Policy. The group members can include categories, applications and widgets from the Application Database and also custom applications, sites and categories.
To create an application or site group:
- In the pane, click>.
The window opens.
- Enter a for the group.
- Click .
The Application viewer opens.
- Select the categories, applications, widgets, and custom items to add as members to the group.
- Click .
The selected items are shown in the list of .
- Click .
The Site Group object is created.
|



