Monitoring Threat Prevention with SmartView Tracker
Log Sessions
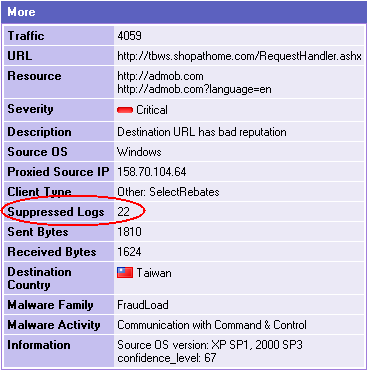
Gateway traffic generates a large amount of activity. To make sure that the amount of logs is manageable, by default, logs are consolidated by session. A session is a period that starts when a user first accesses an application or site. During a session, the gateway records one log for each application or site that a user accesses. All activity that the user does within the session is included in the log.
To see the number of connections made during a session, see the field of the log in SmartView Tracker.
In SmartEvent the number of connections during the session is in the field of the Event Details.
Session duration for all connections that are prevented or detected in the Rule Base, is by default 10 hours. You can change this in SmartDashboard from the tab > > > .
Threat Prevention Logs
Logs from Anti-Bot, Threat Emulation and Anti-Virus are shown in SmartView Tracker. A log is generated if you set the option in a Rule Base rule to .
Viewing Logs
To open SmartView Tracker:
- From the tab > Navigation Tree > link
- From the SmartDashboard menu bar, select >
Updating the Anti-Bot and Anti-Virus Rule Base
In some cases, after evaluating a log, it may be necessary to update a rule or rule exception in the SmartDashboard Rule Base. You can do this directly from within SmartView Tracker.
To update a rule in the Anti-Bot and Anti-Virus Rule Base:
- Right-click the log entry.
- Select .
SmartDashboard opens showing the related rule in the Anti-Bot and Anti-Virus Rule Base.
- Make related changes.
- Click to install the Anti-Bot, Threat Emulation,
 and Anti-Virus policy. and Anti-Virus policy.The Anti-Bot, Threat Emulation and Anti-Virus Software Blades have a dedicated policy. You can install this policy installation separately from the policy installation of the other Software Blades.
You can update the Anti-Bot, Threat Emulation and Anti-Virus Rule Base to give immediate coverage for new malware threats. Install only the Threat Prevention policy to minimize the impact on the Security Gateways.
To install the Anti-Bot and Anti-Virus policy:
- From the tab > pane, click .
- Select the relevant options:
- Installs the policy on all Security Gateways that have Anti-Bot, Threat Emulation, and Anti-Virus enabled.
- - Select the applicable Security Gateways.
- - Install the policy on the selected Security Gateways without reference to the other targets. A failure to install on one Security Gateway does not affect policy installation on other gateways.
If the gateway is a member of a cluster, install the policy on all the members. The Security Management Server makes sure that it can install the policy on all the members before it installs the policy on one of them. If the policy cannot be installed on one of the members, policy installation fails for all of them.
- - Install the policy on all installation targets. If the policy fails to install on one of the Security Gateways, the policy is not installed on other targets of the same version.
- Click .
To update a rule exception in the Anti-Bot and Anti-Virus Rule Base:
- Right-click the log entry.
- Select .
SmartDashboard opens and shows an window in the Threat Prevention Rule Base. These details are shown:
- - The name of the protection. Details are taken from the ThreatCloud repository or, if there is no connectivity, from the log.
- - The scope is taken from the log. If there is no related host object, an object is created automatically after you click . Click the plus sign to add additional objects.
- - Shows by default. You can use the plus sign to add gateways.
- Select an option:
- - If you want the to apply only to the related rule.
- - If you want the to apply to all rules. The exception is added to the > pane.
- Click .
The exception is added to the Rule Base. The is set to by default. Change if necessary.
- Click to install the Anti-Bot, Threat Emulation,
 and Anti-Virus policy. and Anti-Virus policy.The Anti-Bot, Threat Emulation and Anti-Virus Software Blades have a dedicated policy. You can install this policy installation separately from the policy installation of the other Software Blades.
You can update the Anti-Bot, Threat Emulation and Anti-Virus Rule Base to give immediate coverage for new malware threats. Install only the Threat Prevention policy to minimize the impact on the Security Gateways.
To install the Anti-Bot and Anti-Virus policy:
- From the tab > pane, click .
- Select the relevant options:
- Installs the policy on all Security Gateways that have Anti-Bot, Threat Emulation, and Anti-Virus enabled.
- - Select the applicable Security Gateways.
- - Install the policy on the selected Security Gateways without reference to the other targets. A failure to install on one Security Gateway does not affect policy installation on other gateways.
If the gateway is a member of a cluster, install the policy on all the members. The Security Management Server makes sure that it can install the policy on all the members before it installs the policy on one of them. If the policy cannot be installed on one of the members, policy installation fails for all of them.
- - Install the policy on all installation targets. If the policy fails to install on one of the Security Gateways, the policy is not installed on other targets of the same version.
- Click .
Accessing the Threat Wiki
You can open the Threat Wiki from within SmartView Tracker to get more information about a specified protection.
To open the Threat Wiki:
- Click the malware protection link in the field of a log record.
Viewing Packet Capture Data
If you set a rule with the Packet Capture track option, you can see the captures in SmartView Tracker.
To see packet captures in SmartView Tracker:
- Locate the log entry with the packet capture.
- Right-click the entry and select .
- Select and click .
The packet is shown in the Viewer Output window.
You can also use a third-party capture application by selecting and entering the application in the field.
Using Predefined Queries
There are multiple predefined queries in > > > . You can filter the queries to focus on logs of interest.
- - Shows all Anti-Bot and Anti-Virus traffic, including all prevented and detected connections
- - Shows Anti-Bot traffic (prevented and detected connections)
- - Shows Anti-Virus traffic (prevented and detected connections)
- -Shows all Anti-Bot and Anti-Virus blocked (prevented) traffic
- - Shows all traffic that are sent to ThreatCloud or Emulation appliance for emulation
- - Shows files that Threat Emulation identified as malware
- - Shows updates and installed policies for Threat Emulation
|
|



