Installing Security Management Server and Security Gateways
Check Point software runs on many platforms and pre-configured appliances. Installations differ by deployment option, platform and operating system.
During installation, an automatic check is done to make sure that there is enough disk space for the installation.
For more about supported deployments, platforms, hardware requirements and operating systems, see the R77 Release Notes.

|
Note - You must install, configure and activate the TCP/IP network protocol before you run the installation program.
|
Installing Standalone
- The Security Management Server and the Security Gateway are installed on the same computer or appliance.

|
Item
|
Description
|
1
|
Standalone computer
|

|
Security Gateway component
|

|
Security Management Server component
|
Installing Standalone on Appliances
You can install a Standalone deployment on UTM-1 appliances, certain 2012 Models, and IP appliances. You can install the SecurePlatform operating system. For more about supported appliances, see the R77 Release Notes.
UTM-1 and 2012 Models
In UTM-1 and 2012 model appliances, the first step to installation is to install the operating system.
Download the R77 ISO file for the relevant operating system and create a removable USB device, or burn it on a DVD disc. Use the ISO to do a clean install of SecurePlatform on the appliance.
To install R77 SecurePlatform:
- Download the ISO file with the R77 image for the Operating System: SecurePlatform.
- Create a removable USB device (see sk65205) or burn the ISO file on a DVD.
- Turn off the appliance.
- Connect the installation media to the USB socket on the appliance.
If using a DVD, connect an external DVD drive and make sure that the DVD with the R77 ISO file is in the drive.
- Connect the supplied DB9 serial cable to the console port on the front of the appliance.
- Connect to the appliance using a terminal emulation program such as Microsoft HyperTerminal or PuTTY.
- Configure the terminal emulation program:
- In the HyperTerminalwindow, select a port from the list.
- In PuTTY select the connection type.
- Define the serial port settings: 9600 BPS, 8 bits, no parity, 1 stop bit.
- From the list, select .
- Turn on the appliance.
The appliance begins the boot process and status messages show in the terminal emulation program.
- Press . You must press the Enter key within 90 seconds or the appliance boots from the hard drive.
The R77 ISO file is installed on the appliance.
- Reboot the appliance. For SecurePlatform - Turn off the appliance and then turn it on again.
When the model number is shown on the LCD screen, the installation process is complete.
SecurePlatform
Use the SecurePlatform First Time Configuration Wizard to configure the new image on the appliance.

|
Note - The internal interface (INT) on a UTM-1 appliance is used as the management interface.
|
To start the First Time Configuration Wizard:
- Connect a standard network cable to the appliance management interface and to your management network.
The management interface is marked .
- Open Internet Explorer to the default management IP address,
https://192.168.1.1:4434 - Log in to the system using the default login name/password: .
Note - You can use the Portal menu to configure the appliance settings. Navigate to https://<appliance_ip_address>:4434
- Set the username and password for the administrator account.
- Click .
The First Time Configuration Wizard opens.
To configure SecurePlatform standalone:
- In the First Time Configuration Wizard, set the date and time and then click .
- Configure the settings for the management and other interfaces and then click .
- Configure the settings for the routing table and then click .
- Set the , , and and then click .
- Select and then click .
- Do not configure the appliance as part of a cluster and then click .
- Set the clients that can manage the appliance using a web or SSH connection and then click .
- Download SmartConsole and then click .
The window shows the settings for the appliance.
- Click .
SecurePlatform R77 is installed on the appliance.
IP Appliances
For the IP Appliance models that are supported for this release, see the R77 Release Notes.
Gaia
You can install the Gaia operating system and Check Point Standalone, Security Management Server, and Security Gateway deployments on IP appliances.
This section tells you how to do a clean installation of R77 Gaia on an IPSO platform in a Standalone deployment.
IPSO and Check Point product configurations are not imported. To keep your IPSO configuration, see the instructions for upgrading an IPSO Security Gateway IP appliance from IPSO to Gaia.

|
Note - You cannot upgrade an IPSO Standalone or Security Management Server appliance to Gaia.
|
You can install R77 on all IP appliance platforms (IP150, IP280, IP290, IP390, IP560, IP690, IP1280, IP2450) using FTP over a network connection. You can also install R77 on all of these IP Appliance platforms except IP390 and IP560 using a USB removable device and the Check Point ISOmorphic utility.
- To install using a removable device see sk83200.
- To install over the network using FTP, continue with these instructions.
Preparing for Installation
Set up this environment.
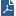
Item
|
|
1
|
IP Appliance with
- IPSO
- IPSO to Gaia installation package or upgrade package.
|
2
|
FTP Server with a Gaia ISO image mounted. The ISO is copied to the IP Appliance as part of the installation or upgrade process. The FTP server can be Linux-based or Windows-based.
In this example, the FTP Server is at 192.0.2.2.
|
3
|
Optional: FTP Server used as a location for one or more of the following:
- Backup of IPSO and the Security Gateway configuration. (recommended)
- A special SmartUpdate package that can be used to distribute the IPSO to Gaia installation and upgrade package to multiple Security Gateways.
- A special package that can be used to install or upgrade Security Gateways, one at a time, without having to answer any questions. This package is created using the answers supplied when running the installation and upgrade package.
You can use the same FTP server as for the Gaia ISO, or a different one. In this example, the FTP Server is at 192.0.2.3.
|
4
|
Computer with console access to the IP appliance and to the FTP server(s).
Console access is recommended because it allows you to keep the connection to the IP Appliance throughout the installation or upgrade. If you connect via SSH you lose the connection after the IP Appliance reboots, and you will not be able to track the installation or upgrade progress.
|
Installation Procedure Overview
|
|
|

|
Important - This is an overview of the steps, not the actual instructions. Detailed instructions follow.
|
Step 1: Get the IPSO to Gaia installation and upgrade package (tgz) and the Gaia ISO image.
Step 2: Put the Gaia ISO on an FTP server.
Step 3: Install the installation and upgrade package on the IP Appliance using Network Voyager or Clish.
Step 4: Run the script:
- Clean install -
run-install-gaia - Upgrade -
run-upgrade-to-Gaia
Step 5: Enter FTP server details and the ISO location. The script tests the FTP Server environment:
- Route to the FTP server
- Interface speed and duplex settings
- FTP access with the given credentials
- FTP access to the specified path
- Path contains the Gaia ISO and the user has Read/Write access to the directory
- Multiple simultaneous connections (>20) to the FTP server are allowed
- Timeout on FTP server is not too low
- FTP access to files downloaded by the Gaia boot manager
Step 6: Optional, but recommended: Enter data for an FTP server to hold IPSO system and configuration backup.
Step 7: Optional: Enter data to make a customized IPSO to Gaia upgrade package. Use this to upgrade multiple Security Gateways with SmartUpdate.
- Upgrade one Security Gateway with the standard IPSO to Gaia upgrade package. Enter the required data to create the special upgrade package.
- Upgrade all other Security Gateways simultaneously, using the special upgrade package, without more data. All IP Appliances must be able to access the same ftp servers as the first Security Gateway.
Step 8: Confirm your selections.
Step 9: The installation or upgrade package now runs automatically:
- If you made a backup package: The backup tar files are copied from the IP Appliance to the FTP server.
- If you made a customized installation or upgrade package: The package is copied from the IP Appliance to the FTP server.
- The Gaia image is copied from the FTP server to the IP Appliance.
- The Gaia image is installed.
- The Gaia boot manager is installed.
- The IP Appliance reboots.
You see the Gaia prompt on the IP Appliance.
|
Step 10: Run the First Time Configuration Wizard and select the products to install.
|
Step 1: Getting the Upgrade Package and the Gaia Image
- Download the Gaia packages for IP Appliance from the R77 home page on the Check Point Support Center.
You will see two packages:
- Gaia ISO image
- IPSO to Gaia installation and upgrade package. The file name is
Check_Point_Install_and_Upgrade_IPSO6.2_to_Gaia_R77.tgz
- Prepare the installation and upgrade packages:
Copy the packages to an FTP server, in a directory of your choice. Or transfer the packages by FTP to the IP Appliance.
Step 2: Putting the Gaia ISO on an FTP Server
Network Requirements

|
Important - High network traffic or large transfers (more than 10/100 Mbps links) can interfere with the FTP transfers for installation.
|
- Make sure the appliance can reach the FTP server.
- Make sure there is no Firewall which blocks incoming FTP requests from the appliance to the FTP server.
- Configure the FTP server to allow more than 100 (or an unlimited number of) concurrent connections.
- Make sure the Gaia ISO file is mounted on a directory to which the user has access permissions.
On a Linux-based FTP Server:
- Upload the Gaia ISO file to the FTP server
- On the FTP server, run:
mount -o loop -t iso9660 <ISO_filename> <mounting_destination_dir>
On a Windows-based FTP Server:
- Upload the Gaia ISO file to the FTP server
- Extract the Gaia ISO file to a folder on the FTP Server. Use 7-zip, Winzip, WinRAR or similar.
- In the folder, run the file
copyrpms.batThis batch file copies installation files, to give a required workaround to Windows' inability to support soft links.
- Give FTP credentials to the folder, so the folder can be accessed via FTP.
|
Step 3: Installing the Package on the IP Appliance
- Log in to the IP Appliance using a console.
- Run
Clish - Install the IPSO to Gaia installation and upgrade package on the IPSO appliance using
Clish or using Network Voyager (see the Network Voyager Reference Guide.
To use Clish:Note - If using anonymous ftp, change ftp anonftp
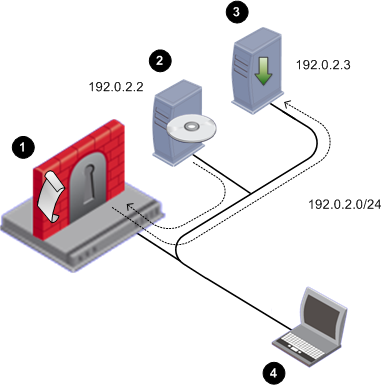
The installation and upgrade package is installed.
Trying to install package: ./.tgz
Package Information --
Name : IPSO to Gaia Upgrade
Version : <version>
Release : <Release>
Description: IPSO to Gaia Upgrade Package (<package_version>)
Package will be installed under: /opt
Package installed and activated successfully.
End of package installation.
|
The installation success message is Package installed and activated successfully
The package is reported to be activated, but there are no background processes running.
- Show the installed and active packages by running:
show package active
Name Ver Rel Dir Desc
{Check Point CPinfo } 10 00 /opt/CPinfo-10 {Check Point CPinfo}
{Check Point R70} R70 00 /opt/CPsuite-R70 {Check Point R70}
{IPSO to Gaia Upgrade} <ver> <rel> /opt/<package_name> {IPSO to Gaia Upgrade Package (<upgrade_package_version>)}
|
- Exit Clish. Run:
exit
Step 4: Running the Installation and Upgrade Script
- Go to the location of the package
cd /opt/<package_name>/
- To upgrade, run
./run-upgrade-to-Gaia To do a clean installation, run
./run-install-Gaia
If you are upgrading multiple appliances from a special upgrade package that was previously saved, the installation or upgrade runs automatically. Continue with Step 9.
If you are upgrading or installing one appliance, continue here.
The script runs. The following shows an upgrade. If you do a clean installation, the IPSO configuration is not transferred to Gaia.
Welcome to the IPSO to Gaia Install/Upgrade procedure.
Checking platform...OK
Checking IPSO OS version ...OK
Checking hostname ...
Checking your configuration
Summary:
Errors: 0
Warnings: 0
Information: 14
Total Grade: 94
Details in file "/var/tmp/verify-IPSO-for-Gaia.msgs".
A newer version of this script may be available.
Contact the Check Point UserCenter at https://usercenter.checkpoint.com
and see SK66569.
Do you want to continue with the upgrade ? [y] y
=========================================================
The following types of information are needed to prepare
your IPSO appliance for the upgrade:
- info about downloading the Gaia image.
- info about transferring the verification reports (optional).
- info about transferring an IPSO backup (optional).
- info about transferring a special upgrade package with your answers (optional).
Answer the prompts for this info and then the upgrade is performed.
Hit 'Enter' to continue or Ctrl-C to exit
|
- Supply the information for downloading the Gaia image

|
Note - If you have run the upgrade script before, the previously entered values are shown in square brackets [ ]. Press Enter to accept the values, or type in the new values and press Enter.
|
Step 5: Verifying the FTP Server
Enter the requested FTP server data and the path to the Gaia installation file.
|
Required Directory Value
|
If ISO is mounted to a non-FTP directory
|
Enter full path to ISO.
A relative path or shortcut link will not work.
Example: if , ./gaia
|
If ISO is mounted to , and FTP user account is used to install
|
Enter path to ISO. A shortened path will work.
Example: if , gaia
|
If ISO is mounted to , and non-FTP user account is used to install
|
Enter full path to ISO.
A relative path or shortcut link will not work.
|
The script runs some tests to verify the FTP environment. If errors are detected, correct the FTP server configuration and then instruct the program to verify the FTP environment again.
Here is an example of a successful test:
Info for download of the Gaia image:
Info for download of the Gaia image:
IP address of FTP server [192.0.2.2]:
User name [gwhite]:
Password [******]:
Directory [/mnt/gaia_image]:
Performing tests of access to FTP server and Gaia ISO
Checking route to 192.0.2.2 ... OK
Interface: eth-s4p1 speed 100M, duplex full
Checking FTP access with given credentials ... OK
Checking FTP access to /mnt/gaia_image ... OK
Checking /mnt/gaia_image is Gaia ISO ... Yes
Checking multiple simultaneous connections to 192.0.2.2 ... OK
Checking timeout to 192.0.2.2 ... OK
Checking FTP access to files downloaded by Gaia boot-manager
system/ramdisk.pxe ... OK
system/base/stage2.img ... OK
|
Step 6 (Optional, Recommended): Supplying Reports and Backup Server Information
The script will request details of the FTP server to store reports and backup data. The same path-rules apply here as in Step 5. The backup creates two tgz files, for:
- IPSO operating system configuration files, user directories, and log files.
- Security Gateway backup files.
Here is an example:
A complete backup of the IPSO system can performed
including system configuration, user home directories,
log files and files from packages.
Do you want to perform this backup ? [y]
Use IP address '192.0.2.2' and user 'root' for the backup? [n]
Details for transferring the IPSO Backup:
IP address of FTP server []: 192.0.2.3
User name []: ftp
Password []: ***
Directory []: /backupdir
Checking FTP access to 192.0.2.3 (it may take a minute) ... done
|
Step 7: (Optional): Supplying Special Package Server Information
Enter data of the destination FTP server for the special upgrade package. Enter a destination directory, with the same rules as in Step 5.
A package with your answers to the previous prompts can be created.
This package can be used on other IPSO Gateways for
unattended conversion to Gaia.
Do you want to create such a package? [y]
Details for transferring the package with your answers:
IP address of FTP server [192.0.2.3]:
User name [ftp]:
Password [***]:
Directory [packagedir]:
Checking FTP access to 192.0.2.3 (it may take a minute) ... done
|
Step 8: Confirming Your Selections
You see a summary of all your answers.
Information for download of the Gaia image:
FTP Server IP Address = 192.0.2.2
FTP Server user name = root
Directory on FTP Server = /imagedir
Information for transferring the IPSO Backup:
FTP Server IP Address = 192.0.2.3
FTP Server user name = ftp
Directory on FTP Server = /backupdir
Information for transferring the package with your answers:
FTP Server IP Address = 192.0.2.3
FTP Server user name = ftp
Directory on FTP Server = /packagedir
Are these values correct? [y]
|
- Click
nThe backup file and the special upgrade package file, if you chose to create them, are created.
Writing values to file
Performing IPSO backup (file <ipso_backup_file_name>.tgz) ... done
Performing Check Point Security Gateway backup (file <Security Gateway_backup_file_name>.tgz) ... done
Transferring IPSO and Check Point Security Gateway backup files ... done
Creating a package with your answers (<package_name>_AUTO.tgz) ... done
Transferring package with your answers ... done
Installing Gaia Boot Manager ... done
|
- You have 30 seconds to abort. To stop the upgrade, press .
IP appliance reboots in 30 seconds to complete the upgrade.
Hit 'Enter' to abort.
|

|
Important - If you want to make changes, press Enter now.
This stops the upgrade to Gaia. To complete the upgrade to Gaia, reboot the IP Appliance.
|
Step 9: Installation Runs Automatically
The installation runs unattended.
- The IP Appliance reboots.
- The Gaia Boot Manager runs.

|
Important - After reboot, the system sometimes shows the Boot Manager prompt.
To complete installation, type INSTALL
|
- The Gaia image is installed.
- The IPSO and R77 configurations are not imported into Gaia.
- The Gaia prompt shows.

|
Important - The HTTPS port for the WebUI is set to 443 after an installation or upgrade.
To change this, you must use SmartDashboard > > .
|
Step 10: Selecting Check Point Products
To configure Check Point products on Gaia, use the First Time Configuration Wizard. Configure the operating system and install the products in one wizard.
To configure standalone products on Gaia:
- Using your Web browser, go to the Portal:
https://
- In the window, log in using the administrator name and password that you defined during the installation procedure.
- The Portal shows the . Click .
- Select .
- Click .
- Change the default administrator password.
- Click .
- Set an IPv4 and an IPv6 address for the management interface, or set one IP address (IPv4 or IPv6).
If you change the management IP address, the new IP address is assigned to the interface. The old IP address is added as an alias and is used to maintain connectivity.
- Set the for the appliance.
Optional:
- Set the , and IPv4 or IPv6 addresses for the .
- Set the IP Address and Port for a Proxy Server
- Click .
- Set the date and time manually, or enter the hostname, IPv4 address or IPv6 address of the NTP server.
Click .
- Set the username and password for the Security Management Server administrator account and then click .
- Select and and then click .
- Define IP addresses from which SmartConsole clients can log in to the Security Management Server.
- If you select or , define an IPv4 or an IPv6 address.
- You can also select a range of IPv4 addresses.
- Click .
- Get a license automatically from the UserCenter and activate it, or use the trial license.
If there is a proxy server between the appliance and the Internet, enter its IP address and port.
- Click .
- Review the summary and, if correct, click .
- To start the configuration process, click .
A progress bar tracks the configuration of each task.
- Click .
- If the window shows, click or .
After some minutes, you can use the Portal to configure your standalone environment.
Rollback from Gaia to IPSO
You can roll back from Gaia to IPSO 6.2. You can also restore the Check Point Security Gateway and/or Security Management Server configuration.
Before doing a rollback from Gaia to IPSO:
Make sure that:
- The IPSO boot manager installer is available. Download it from the R77 home page.
- An IPSO image is available. Put the IPSO image on an FTP server, and make sure that the FTP server is accessible from the Gaia IP Appliance.
- A backup of the Check Point Security Gateway on the Gaia IP Appliance is available. Put the backup tar file on an FTP server, and make sure the FTP server is accessible from the Gaia IP Appliance.
To roll back from Gaia to IPSO:
- At the Gaia command line prompt, login as the administrator.
- Go to expert mode. Type
expert. - From the R77 home page on the Support Center, download the IPSO boot manager installer:
Check_Point_R77_Install_IPSOBootmanager.sh
- Copy the IPSO boot manager installer to the Gaia IP Appliance. For example, to:
/var/tmp - Change file attributes to give executable permissions. Run:
chmod 777 Check_Point_R77_Install_IPSOBootmanager.sh
- Install the IPSO boot manager by running:
./Check_Point_R77_Install_IPSOBootmanager.sh
The script asks if you want to roll back to:
1. IPSO 4.2
2. IPSO 6.2
- Choose
2. - Type
reboot.After the reboot, the system is running the IPSO boot manager.
- At the
BOOTMGR>install - Enter the:
- IP address of the IP Appliance.
- Default gateway of the IP Appliance.
- IP address of the FTP server with the IPSO image.
- User credentials.
- Directory path.
- Answers to various configuration questions regarding:
- The chassis serial number
- Whether the system is part of a VRRP cluster
- Whether IGMP and BGP are enabled
The system automatically reboots into IPSO.
- Configure the IP Appliance:
- Hostname
- New password for
admin - The management port physical interface (enable)
- IP address for the management interface
- Default gateway
To restore the Check Point Security Gateway configuration:
In the following example:
CP_archive_<hostname and timestamp>.tgz i2g_backup_<hostname and timestamp>.tgz

|
Important - If the IPSO backup contains IPSO and Check Point configuration data, the Check Point packages must be restored before the IPSO configuration.
|
To Restore:
- Make sure the backup IPSO and CP archives are on an FTP server with connectivity to the IP appliance.
- Log in to the IP Appliance as
admin. - Copy the backup archive file containing the Check Point Security Gateway to the IP Appliance:
cd /var/tmp
ftp <ftp-address>
username: <ftp-user>
password: <ftp-password>
>bin
>cd <PATH>
>get CP_archive_<hostname and timestamp>.tgz
>bye
|
- Unpack the archive to the root directory
tar xzf CP_archive_<hostname and timestamp>.tgz -C /
|
- Copy and restore the IPSO backup file to the appliance using the
set restore
Clish
set restore remote ftp-site <ftp-address>
set restore remote ftp-user <username>
set restore remote ftp-pass <password>
set restore remote ftp-dir <PATH>
set restore remote filename i2g_backup_<hostname and timestamp>.tgz
|
IPSO automatically reboots.
- Log out.
- Log in as
admin - Verify the configuration has been restored.
IPSO

|
Note - IPSO 6.2 MR4 or above is:
- Required to install R77. To learn how to upgrade IPSO, see the IPSO 6.2 MR4 Release Notes.
- Backwardly compatible with older versions except R75.40VS. R75.40VS does not support IPSO
|
To Install R77 on IPSO using Network Voyager:
- Log on to your platform by using Check Point Network Voyager.
- In the Network Voyager navigation tree, select .
- Enter the name or IP address of the FTP server.
- Enter the path to the directory on the FTP server where the packages are stored.
- If necessary, enter the appropriate user name and password.
- Click .
- The names of the available packages appear in the window.
- Select the installation package.
- Click .
- The selected package is downloaded to the platform. When the download is complete, the package appears in the field.
- Select the package in the field.
- Click .
- Click the link to install or upgrade the package.
- (Optional) To display all installed packages, click ; then click .
- (Optional) To perform a first-time installation, click ; then click .
- (Optional) To upgrade a package, click .
- (Optional) To upgrade a package, click the button of the package that you want to upgrade under .
- Click .
- Click to make your changes permanent.

|
Important - After installing a package Using Network Voyager, you see this
message:
Voyager environment has been updated with the latest package info. The telnet session environment will be updated by:logging out and logging in again the telnet session.
This message might not be accurate.
- Click to verify that the package is installed.
- Refresh the page periodically until you see that the installation is complete.
|
The packages are automatically activated as part of the installation process. To confirm the package installation and activation, check the page.
To activate:
- A package that was not automatically activated
- Optional packages that were deactivated when you added a new version of Check Point IPSO by running the
newimage
Do this:
- Log on to the platform using Check Point Network Voyager.
- In the Network Voyager navigation tree, select .
- Click next to the packages you want to activate
- Click .
- Click .
- Reboot.
After you install R77 on an IP appliance, you must configure it. Before you begin, get the IP address of the SmartConsole (GUI client) that will connect to this server.
To configure standalone IP appliance for the first time:
- From the IPSO command line, run
cpconfig - Read and accept the license agreement.
- Select Stand Alone.
A Security Management Server and a Security Gateway will be installed on this computer. You can also install a log server.
- On the Configuring Licenses and Contracts pane, press N to enter your licenses later (recommended) using SmartUpdate or the WebUI.
- Add administrators accounts.
- Add GUI clients.
- Configure permissions.
- Enter an administrator group name or press Enter to accept the default value (superuser).
- Save the certificate fingerprint to a text file.
- Press Enter.
- Restart the computer when prompted.
After restart, define and install a policy for this Security Management Server.
Installing Standalone on Open Servers
A standalone deployment can be installed on any computer that meets the minimum requirements (see the Release Notes). For Gaia and SecurePlatform, first install and configure the operating system. Then install Check Point products. You can also install on Windows.
SecurePlatform

|
Important - Installing the SecurePlatform operating system deletes all data on the hard drive.
|
To install on SecurePlatform using removable media:
- Put the installation removable media into the drive and boot the computer from the removable media.
- When the SecurePlatform window opens, press Enter.
You must press Enter in 90 seconds, or the computer starts from the hard drive.
- If error messages show during the hardware compatibility scan, correct the problems and then restart the procedure from step 1.
- Optional: Click to resolve hardware compatibility issues.
- Click to continue with the installation.
- Select a keyboard language and then click OK.
- Select as the management interface (networking device) and then click .
- Configure the settings for the interface (NIC) and then click .
- Not for Multi-Domain Server: Configure the clients that can connect to the Portal and then click OK.

|
Note - If you are going to deploy remote access or Endpoint Security software, do not use the default port, 443
|
- Click to install SecurePlatform.
- When the window opens, disconnect the removable media from the computer.
- Click to complete the installation process and restart the computer.
When the computer restarts, configure the operating system. You can use the Portal or using the CLI.
To configure SecurePlatform using the Portal:
- Open a browser to the administration IP address:
- For appliances - https://<IP_address>:4434
- For open servers - https://<IP_address>

|
Note - Pop-ups must always be allowed on https://<IP_address>.
|
The login page appears.
- Login with the default login name () password () and click .
- Download the password recovery login token file. Save it in a safe place.
- Change the default login name and password.
- Click .
In the First Time Configuration Wizard, configure these settings:
- Network connections. The management interface has the administration IP address.
- Routing table.
- DNS servers.
- Host and domain name.
- Date, time, and time zone.
- Allowed IPs of SSH and administration Portal clients.
- Products to install. For standalone, select and .
- Security Management Installation Type.
- Security Management GUI Clients.
- Security Management administrators.
- Click
To configure SecurePlatform using the CLI:
- Log in to the system using the default login name/password: .
- Set the username and password for the administrator account.
- Run:
sysconfigThe first-time system configuration wizard starts. Enter n to continue.
- Set the , , and .
- Configure the settings for the management and other interfaces (network connections).
- Configure the settings for the routing table and then enter .
- Set the date and time and then enter .
After you install and configure the SecurePlatform operating system on an open server, install the Check Point products for Security Management Server and Security Gateway.
When you complete this procedure, IP forwarding is automatically disabled on the Security Gateway. A default security policy is enforced. This policy blocks all inbound connections, except for control connections. This policy is used until you install a new security policy.
To install products on a standalone SecurePlatform computer using the CLI:
- To import a product configuration file from a TFTP server, enter 1 and do the on-screen instructions. Otherwise, enter n to continue.
- In the Welcome window, enter n to continue.
- Enter to accept the End User License agreement.
- Do one of these actions:
- New product installation - Select New Installation and then enter n.
- Use the imported installation file - Select Installation Using Imported Configuration and then enter n.
- Select the Check Point Security Gateway and Security Management Server Software Blades to install, and enter n.
- Select Security Gateway and Security Management and enter n.
- SelectPrimary Security Management.
- In the Validation window, enter n.
- Enter n
- Optional: Enter y to save the certificate fingerprint to a file. Otherwise press n.
- Press Enter.
- Restart the computer.
To install a Secondary Security Management Server on a SecurePlatform open server:
Use the same procedure as for the Primary Security Management Server, with these changes:
- Use a different IP address for the management interface.
- Portal Configuration:
- In the First Time Configuration Wizard, in the page, select Secondary Security Management.
- In the Secure internal Communication page, define the Use this key to configure the secondary Security Management Server object in SmartDashboard.
- CLI Configuration:
- When installing Products after running
sysconfig - When prompted, define the Activation Key. Use this key to configure the secondary Security Management Server object in SmartDashboard.
Windows
You can do a clean installation of Check Point products on a Windows open server. If you have a configuration file from a supported upgrade path, you can import the configuration to the new R77 installation.

|
Note - If the required version of Microsoft.Net framework is not installed, it is installed during installation. This can take several minutes.
If necessary, the Windows Imaging Component is installed during installation.
|
To install on Windows:
- Log in to Windows using credentials.
- Put the installation media in the drive.
The installation wizard starts automatically.
Click .
- Accept the
Click .
- Select
Click .
- Select .
Click .
- Select , and .
- Optional: Select .
Click .
- If prompted, confirm or change the destination folder
Click .
- Select Alternatively, in a Management High Availability deployment, to install the second Security Management Server, select
Click .
- Review your selections
Click .
- Click .
- Restart the computer.
To install on Windows with a configuration file:
- In the first window after the License Agreement, select and click .
- Select the path of the imported configuration file and click .
- Select an option for obtaining the latest upgrade utilities and click .
- Continue with step 6 above.
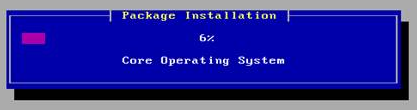
Installing Security Management Server
- The Security Gateway and the Security Management Server are installed on different computers.
|
Item
|
Description
|
1
|
Security Management Server
|
2
|
Network connection
|
3
|
Security Gateway
|

|
Security Gateway component
|

|
Security Management Server component
|
This section explains how to install the Security Management Server.
Installing Security Management Server on Appliances
You can install a Security Management Server on a Smart-1 appliances with SecurePlatform. For more about supported appliances, see the R77 Release Notes.
Smart-1
- Make sure that you have the correct ISO file.
- Install the SecurePlatform operating system on Smart-1. See instructions in UTM-1 and 2012 Models.
- Smart-1 50 only: Smart-1 50 appliances have two images: Security Management Server and Multi-Domain Server. To select the Security Management Server image:
- While the appliance is restarting, open the terminal emulation program.
- When prompted, press any key to enter the boot menu.
- Select and press .
- Type and press .
The Security Management Server image is selected for the appliance and then the appliance resets.
- Install the Security Management Server using the First Time Configuration Wizard.
SecurePlatform
To install the Security Management Server on Smart-1 appliances, use the First Time Configuration Wizard.
To start the First Time Configuration Wizard:
- Connect a standard network cable to the appliance management interface and to your management network.
The management interface is marked .
- Open Internet Explorer to the default management IP address,
https://192.168.1.1:4434 - Log in to the system using the default login name/password: .
Note - You can use the Portal menu to configure the appliance settings. Navigate to https://<appliance_ip_address>:4434
- Set the username and password for the administrator account.
- Click .
The First Time Configuration Wizard opens.
To configure a SecurePlatform Security Management:
- In the First Time Configuration Wizard, set the date and time and then click .
- Configure the settings for the management and other interfaces and then click .
- Configure the settings for the routing table and then click .
- Set the , , and and then click .
- For Security Management installation type, select and then click .
- Set the clients that can manage the appliance using a web or SSH connection and then click .
- Download SmartConsole and then click .
The window shows the settings for the appliance.
- Click .
SecurePlatform R77 is installed on the appliance.
To configure a SecurePlatform Secondary Security Management on Smart-1:
Use the same procedure as for the Primary Security Management Server, with these changes:
- Use a different IP address for the management interface.
- In the First Time Configuration Wizard, in the page, select Secondary Security Management.
- In the Secure internal Communication page, define the Use this key to configure the secondary Security Management Server object in SmartDashboard.
IP Appliances
For the IP Appliance models that are supported for this release, see the R77 Release Notes.
IPSO

|
Note - IPSO 6.2 MR4 or above is:
- Required to install R77. To learn how to upgrade IPSO, see the IPSO 6.2 MR4 Release Notes.
- Backwardly compatible with older versions except R75.40VS. R75.40VS does not support IPSO
|
To Install R77 on IPSO using Network Voyager:
- Log on to your platform by using Check Point Network Voyager.
- In the Network Voyager navigation tree, select .
- Enter the name or IP address of the FTP server.
- Enter the path to the directory on the FTP server where the packages are stored.
- If necessary, enter the appropriate user name and password.
- Click .
- The names of the available packages appear in the window.
- Select the installation package.
- Click .
- The selected package is downloaded to the platform. When the download is complete, the package appears in the field.
- Select the package in the field.
- Click .
- Click the link to install or upgrade the package.
- (Optional) To display all installed packages, click ; then click .
- (Optional) To perform a first-time installation, click ; then click .
- (Optional) To upgrade a package, click .
- (Optional) To upgrade a package, click the button of the package that you want to upgrade under .
- Click .
- Click to make your changes permanent.

|
Important - After installing a package Using Network Voyager, you see this
message:
Voyager environment has been updated with the latest package info. The telnet session environment will be updated by:logging out and logging in again the telnet session.
This message might not be accurate.
- Click to verify that the package is installed.
- Refresh the page periodically until you see that the installation is complete.
|
The packages are automatically activated as part of the installation process. To confirm the package installation and activation, check the page.
To activate:
- A package that was not automatically activated
- Optional packages that were deactivated when you added a new version of Check Point IPSO by running the
newimage
Do this:
- Log on to the platform using Check Point Network Voyager.
- In the Network Voyager navigation tree, select .
- Click next to the packages you want to activate
- Click .
- Click .
- Reboot.
After you install R77 on an IP Appliance, you must configure it.
To configure the Security Gateway IP Appliance for the first time:
- From the IPSO command line, run
cpconfig - Read and accept the license agreement.
- Select Distributed configuration.
- Select Security Management Server.
- At the end of the First Time Configuration Wizard, restart the computer.
Installing Security Management Server on Open Servers
A Security Management Server can be installed on any computer that meets the minimum requirements listed in the Release Notes.
First install and configure the operating system, then install Check Point products.
SecurePlatform
This procedure explains how to install a Security Management Server in a distributed deployment when you install the operating system.
To install Security Management Server on SecurePlatform:
- To import a product configuration file from a TFTP server, enter 1 and do the instructions on the screen. Otherwise, enter n to continue.
- In the Welcome window, enter n to continue.
- Enter to accept the End User License agreement.
- Do one of these actions:
- New product installation - Select New Installation and then enter n.
- Use the imported installation file - Select Installation Using Imported Configuration and then enter n.
- Select the Check Point management Software Blade to install, and enter n.
- In the window, select the components to install and enter n.
- Enter to enter your licenses later (recommended) using SmartUpdate or the WebUI.
- Do the on-screen instructions to add administrators and GUI clients.
- Press Enter.
- Restart the computer.
To install a Secondary Security Management Server on a SecurePlatform open server:
Use the same procedure as for the Primary Security Management Server, with these changes:
- Use a different IP address for the management interface.
- Portal Configuration:
- In the First Time Configuration Wizard, in the page, select Secondary Security Management.
- In the Secure internal Communication page, define the Use this key to configure the secondary Security Management Server object in SmartDashboard.
- CLI Configuration:
- When installing Products after running
sysconfig - When prompted, define the Activation Key. Use this key to configure the secondary Security Management Server object in SmartDashboard.
Linux
You can do a clean installation of Security Management Server on a Linux open server. Use these instructions to install one Security Management Server, or the primary server in a High Availability environment.
Before Installing the Security Management Server on Linux:
- Make sure that the installed Linux version is supported. See the R77 Release Notes. To show the installed version of Red Hat Linux, run:
# more /etc/redhat-release - Install the
sharutils-4.6.1-2- See if you have the package installed by running:
rpm -qa | grep sharutils-4.6.1-2 - If the package is not installed:
- Find the package on CD 3 of RHEL 5.
- Copy it to the Linux computer.
- Install it by running:
rpm –i sharutils-4.6.1-2.i386.rpm
- Install the c
ompat-libstdc++-33-3.2.3-61- See if you have the package installed by running:
rpm –qa | grep compat-libstdc++-33-3.2.3-61 - If the package is not installed:
- Find the package on CD 2 of RHEL 5.
- Copy it to the Linux computer.
- Install it by running:
rpm –i compat-libstdc++-33-3.2.3-61.i386.rpm
- Disable SeLinux:
- See if SeLinux is disabled by running:
getenforce - If is enabled:
- Edit the file
/etc/selinux/config - Set
SELINUX=disabled - Reboot.
- Configure interfaces using util netconfi. If not available
- Run
# cd /etc/sysconfig/network-scripts/ - Edit the interfaces configuration file:
#vi ifcfg-eth0 - Configure the IP address and netmask. Give values to these fields:
IPADDR=
NETMASK=
For example:
DEVICE=ETH0
ONBOOT=yes
IPADDR =192.0.2.123
NETMASK=255.255.255.0
HWADDR=00:50:60:70:1a:2b
|
- Save and exit the file.
- Configure the default gateway and the hostname.
- Run:
# cd /etc/sysconfig - Edit the
network
# vi network - Give values for these fields:
HOSTNAME=
GATEWAY=
For example:
NETWORKING=yes
NETWORKING_ipv6=yes
HOSTNAME=mng-linux5
GATEWAY=192.0.2.1
|
- Save and exit the file.
- Add an external IP address and hostname to
/etc/hosts- Run:
# cd /etc - Edit the
network
# vi hosts - Add a line to the file, for example, add:
192.0.2.123 mng-linux5 - Save and exit the file.
- Reboot.
- Make sure the hostname is the one configured in step 6. Run:
#hostname
To install the Security Management Server on Linux:
- Download the ISO file for Linux from the R77 home page.
- Copy the ISO to the Linux computer. Alternatively, burn it to a DVD and use a removable DVD drive:
To copy the ISO to the Linux computer:
To put the ISO on a DVD:
- Burn the ISO to a DVD.
- Insert the DVD into the drive.
- Log in as a user with root authority.
- At the root prompt, create a mount point and mount the DVD. Run:
# mkdir /mnt/cdrom
# mount -t iso9660 -o ro /dev/cdrom /mnt/cdrom - Go to the DVD mount directory. Run:
# cd /mnt/cdrom
- Run:
./UnixInstallScript - In the window, press to continue.
- Read and accept the terms of the End User License Agreement.
- Select and press to continue.
- Select and the other products you need. Press to continue.
- Select and press to continue.
- Select the . Press to continue.
- In the window, press to continue.
The products and components are installed.
- If you are installing a Security Management Server, follow the instructions on the screen to configure:
- Licenses
- Administrators (name and password)
- GUI clients
- Random pool of data for cryptographic operations
- Certificate authority
- Fingerprint save
- Press y to start the installed products.
- After the products have started, press E to Exit.
- Log out and then log in again as the root administrator.
- If you did not start the installed products, run: #
cpstart
Windows
You can do a clean installation of Security Management Server on a Windows open server. If you have a configuration file from a supported upgrade path, you can import the configuration to the new R77 installation.

|
Note - If the required version of Microsoft.Net framework is not installed, it is installed during installation. This can take several minutes.
If necessary, the Windows Imaging Component is installed during installation.
|
To install on Windows:
- Log in to Windows using credentials.
- Put the installation media in the drive.
The installation wizard starts automatically.
Click .
- Accept the
Click .
- Select
Click .
- Select .
Click .
- Select and .
- Optional: Select .
Click .
- If prompted, confirm or change the destination folder
Click .
- Select or applicable.
Click .
- Review your selections.
Click .
- Click .
- Restart the computer.
To install on Windows with a configuration file:
- In the first window after the License Agreement, select and click .
- Select the path of the imported configuration file and click .
- Select an option for obtaining the latest upgrade utilities and click .
Continue with step 6 above.
Installing Log Server
You can install a log server for a distributed deployment. Install the operating system and start to install the products as for a Security Management Server, but stop at the step where you select components.
To install a Log Server:
Do the steps to install a Security Management Server with these changes:
- When selecting the products to install, select .
- Define the Security Management as a .
- In Windows: Do not select .
Installing Endpoint Security
In all non-standalone deployments, the Network Security Management Server can also be an Endpoint Security Management Server.
Installing Endpoint Security Servers
Use the installation instructions in this guide to install Security Management Servers. You can enable the Endpoint Security Management Server after the Security Management Server installation is completed. Endpoint Security E80.50 is installed with R77.
For R77 and R77.10 Security Management Servers, see the E80.50 Endpoint Security Administration Guide for more information.
For R77.20 Security Management Servers, see the Endpoint Security on R77.20 Management Administration Guide for more information.
To enable an Endpoint Security Management Server:
- Use the instructions in this guide to install a Security Management Server.
- In SmartDashboard, open the Security Management Server object.
- Enable the blade in the page.
- Select.
Check Point Cloud Services for Endpoint
After the Endpoint Security Management Server is enabled on the Security Management Server, these components communicate with the Check Point cloud services:
- Endpoint Anti-Malware Software Blade – Downloads updates from the Check Point Malware Update Server.
These updates are mandatory for the correct functioning of the Anti-Malware Software Blade. Preventing them causes severe security issues, because the blade does not operate with the latest malware information database.
- Endpoint Anti-Malware Software Blade – Sends suspected malware to the Check Point ThreatCloud Server.
These updates increase the accuracy of malware detection by Check Point Endpoint Security clients and Check Point Security Appliances. To turn them off, modify the Anti-Malware rule in the Organizational Security Policy in SmartEndpoint.
- Endpoint Application Control Software Blade – Downloads information about classified known applications from the Check Point ThreatCloud Server and sends unknown applications for analysis.
These updates are mandatory for the correct functioning of the Endpoint Application Control Software Blade. Without these updates, the blade is unable to classify malicious applications and automatically distinguish between them and non-malicious ones.
To enable an Endpoint Policy Server:
- Use the instructions in this guide to install a .
- Connect from SmartDashboard to the Endpoint Security Management Server and create a new Log Server object:
- In the tree, right-click and select .
- Enter a and for the Log Server.
- Click to create SIC with the Security Management Server.
- In the tab, select:
- Select.
When the Endpoint Policy Management blade is enabled, the SecurePlatform/Gaia Portal port changes from 443 to 4434. If you disable the blade, the port changes back to 443.
Disk Space for Endpoint Security
We recommend that you have at least 10 GB available for Endpoint Security in the Root disk partition.
- In Gaia and SecurePlatform, client packages and release files are stored under the Root partition.
- In Windows, client packages and files are usually stored on the C drive.
The files include:
- 4 GB - Security Management Server installation files.
- 2 GB or more - Client files (each additional version of client packages requires 1GB of disk space).
- 1 GB - Logs.
- 1 GB - High Availability support (more can be required in large environments).
|
Note - To make future upgrades easier, we recommend that you use a larger disk size than necessary in this deployment.
|
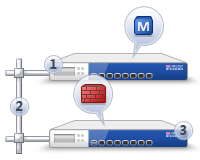
Installing Security Gateway
- The Security Gateway and the Security Management Server are installed on different computers.

|
Item
|
Description
|
1
|
Security Management Server
|
2
|
Network connection
|
3
|
Security Gateway
|

|
Security Gateway component
|

|
Security Management Server component
|
This section explains how to install the Security Gateway.
Installing Security Gateways on Appliances
You can install a Security Gateway on UTM-1 appliances, Power-1 appliances, certain 2012 Models, and IP appliances. The appliance operating system can be Gaia or SecurePlatform. For more about supported appliances, see the Release Notes.
UTM-1, Power-1, and 2012 Models
After you install the Gaia or SecurePlatform operating system, install the Security Gateway.
SecurePlatform
To install the Security Gateway on SecurePlatform appliances, use the First Time Configuration Wizard.

|
Note - The internal interface (INT) on a UTM-1 appliance is used as the management interface.
|
To start the First Time Configuration Wizard:
- Connect a standard network cable to the appliance management interface and to your management network.
The management interface is marked .
- Open Internet Explorer to the default management IP address,
https://192.168.1.1:4434 - Log in to the system using the default login name/password: .
Note - You can use the Portal menu to configure the appliance settings. Navigate to https://<appliance_ip_address>:4434
- Set the username and password for the administrator account.
- Click .
The First Time Configuration Wizard opens.
To configure a Security Gateway on SecurePlatform appliance:
- In the First Time Configuration Wizard, set the date and time and then click .
- Configure the settings for the management and other interfaces and then click .
- Configure the settings for the routing table and then click .
- Set the , , and and then click .
- Select and then click .
- Set the clients that can manage the appliance using a web or SSH connection and then click .
- Select the type of gateway for the appliance and then click .
- Define the Secure Internal Communication (SIC) that is used by the gateway object in SmartDashboard and then click .
- Click .
SecurePlatform R77 is installed on the appliance.
IP Appliances
IPSO

|
Note - IPSO 6.2 MR4 or above is:
- Required to install R77. To learn how to upgrade IPSO, see the IPSO 6.2 MR4 Release Notes.
- Backwardly compatible with older versions except R75.40VS. R75.40VS does not support IPSO
|
To Install R77 on IPSO using Network Voyager:
- Log on to your platform by using Check Point Network Voyager.
- In the Network Voyager navigation tree, select .
- Enter the name or IP address of the FTP server.
- Enter the path to the directory on the FTP server where the packages are stored.
- If necessary, enter the appropriate user name and password.
- Click .
- The names of the available packages appear in the window.
- Select the installation package.
- Click .
- The selected package is downloaded to the platform. When the download is complete, the package appears in the field.
- Select the package in the field.
- Click .
- Click the link to install or upgrade the package.
- (Optional) To display all installed packages, click ; then click .
- (Optional) To perform a first-time installation, click ; then click .
- (Optional) To upgrade a package, click .
- (Optional) To upgrade a package, click the button of the package that you want to upgrade under .
- Click .
- Click to make your changes permanent.

|
Important - After installing a package Using Network Voyager, you see this
message:
Voyager environment has been updated with the latest package info. The telnet session environment will be updated by:logging out and logging in again the telnet session.
This message might not be accurate.
- Click to verify that the package is installed.
- Refresh the page periodically until you see that the installation is complete.
|
The packages are automatically activated as part of the installation process. To confirm the package installation and activation, check the page.
To activate:
- A package that was not automatically activated
- Optional packages that were deactivated when you added a new version of Check Point IPSO by running the
newimage
Do this:
- Log on to the platform using Check Point Network Voyager.
- In the Network Voyager navigation tree, select .
- Click next to the packages you want to activate
- Click .
- Click .
- Reboot.
After you install R77 on an IP Appliance, you must configure it.
To configure the Security Gateway IP Appliance for the first time:
- From the IPSO command line, run
cpconfig - Read and accept the license agreement.
- Select Distributed configuration.
- Select Security Gateway.
- At the end of the First Time Configuration Wizard, restart the computer.
Installing Security Gateway on Open Servers
A Security Gateway can be installed on any computer that meets the minimum requirements (see the Release Notes). For Gaia and SecurePlatform, first install and configure the operating system. Then install Check Point products. You can also install on Windows.
SecurePlatform
This procedure explains how to install a Security Gateway in a distributed deployment when you install the operating system.
When you complete this procedure, IP forwarding is automatically disabled on the Security Gateway. A default security policy is enforced. This policy blocks all inbound connections, except for control connections. This policy is used until you install a new security policy.
To install products on a standalone SecurePlatform computer:
- To import a product configuration file from a TFTP server, enter 1 and do the instructions on the screen. Otherwise, enter n to continue.
- In the Welcome window, enter n to continue.
- Enter to accept the End User License agreement.
- Do one of these actions:
- New product installation - Select New Installation and then enter n.
- Use the imported installation file - Select Installation Using Imported Configuration and then enter n.
- Select the Check Point Security Gateway Software Blade to install, and enter n.
- Enter to enter your licenses later (recommended) using SmartUpdate or the WebUI.
- Press Enter.
- Restart the computer.
Windows
You can do a clean installation of Check Point products on a Windows open server. If you have a configuration file from a supported upgrade path, you can import the configuration to the new R77 installation.

|
Note - If the required version of Microsoft.Net framework is not installed, it is installed during installation. This can take several minutes.
If necessary, the Windows Imaging Component is installed during installation.
|
To install on Windows:
- Log in to Windows using credentials.
- Put the installation media in the drive.
The installation wizard starts automatically.
Click .
- Accept the
Click .
- Select
Click .
- Select and then click .
- Select Security Gateway and clear all other options.
Click .
- If prompted, confirm or change the destination folder
Click .
- Click .
- Click .
- In the screen, you can add a license now or use the trial period license. Make your selection and then click .
- In the window, specify whether or not this Security Gateway is cluster member. Click to continue.
- In the window, enter and confirm the activation key.
- Click .
- Restart the computer.
To install on Windows with a configuration file:
- In the first window after the License Agreement, select and click .
- Select the path of the imported configuration file and click .
- Select an option for obtaining the latest upgrade utilities and click .
- Continue with step 6 above.
Installing VSX Gateways
A VSX Gateway can be installed on certain Check Point appliances. You can also install it on any computer that meets the minimum requirements (see the Release Notes). Install and configure the Gaia operating system for a Security Gateway. Then install Check Point products and use SmartDashboard to change the Security Gateway to a VSX Gateway. The Security Gateway becomes virtual (VSX) when the VSX object is defined in SmartDashboard. The basic installation procedure for a Security Gateway and a VSX Gateway is the same.
For VSX Gateways on a Crossbeam platform, you must convert the gateway to VSX before you create the VSX object in SmartDashboard. For more about converting to VSX on a Crossbeam platform, see the Crossbeam Administration Guide (password required).
To install a VSX Gateway:
- Install and configure the R77 ISO file on the VSX Gateway.
The steps are different if the VSX Gateway is on an appliance or an Open Server.
In the window, make sure to only select .
- For a VSX Gateway on a Crossbeam platform, convert the gateway to VSX.
- Open SmartDashboard.
- From the tree, right-click and select >.
- Complete the on-screen instructions.
- Install the necessary licenses on the VSX Gateway.