Check Point Firewall Security Solution
Overview of Firewall Features
Firewalls control the traffic between the internal and external networks and are the core of a strong network security policy. Check Point Software Blades are a set of security features that makes sure that the Security Gateway or Security Management server gives the correct functionality and performance. The Check Point Firewall is part of the Software Blade architecture that supplies "next-generation" firewall features, including:
- VPN and mobile device connectivity
- Identity and computer awareness
- Internet access and filtering
- Application control
- Intrusion and threat prevention
- Data Loss Prevention
Components of the Check Point Solution
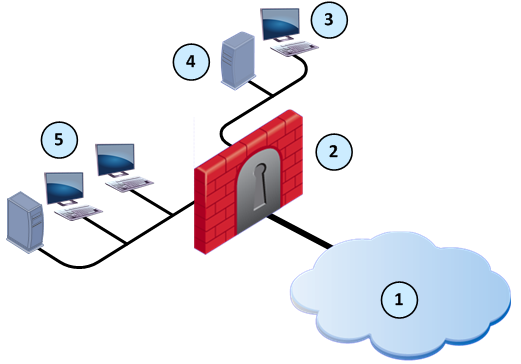
Item
|
Description
|
1
|
Internet and external networks
|
2
|
Security Gateway
|
3
|
SmartDashboard
|
4
|
Security Management server
|
5
|
Internal network
|
These are the primary components of the Check Point solution:
- Security Gateway - The security engine that enforces the organization’s security policy and acts as a security enforcement point. The Security Gateway is managed by the Security Management server and sits on the network as an entry point to the LAN.
- Security Management server - The server used by the system administrator to manage the security policy. The organization’s databases and security policies are stored on the Security Management server and downloaded to the Security Gateway.
- SmartDashboard - A SmartConsole GUI application that is used by the system administrator to create and manage the security policy.
Dual Stack (IPv4 and IPv6) Network Configuration
You can easily configure the Firewall to support a dual stack network that uses IPv4 and IPv6 addresses. Configure one or more interfaces with the applicable IPv4 and IPv6 addresses.
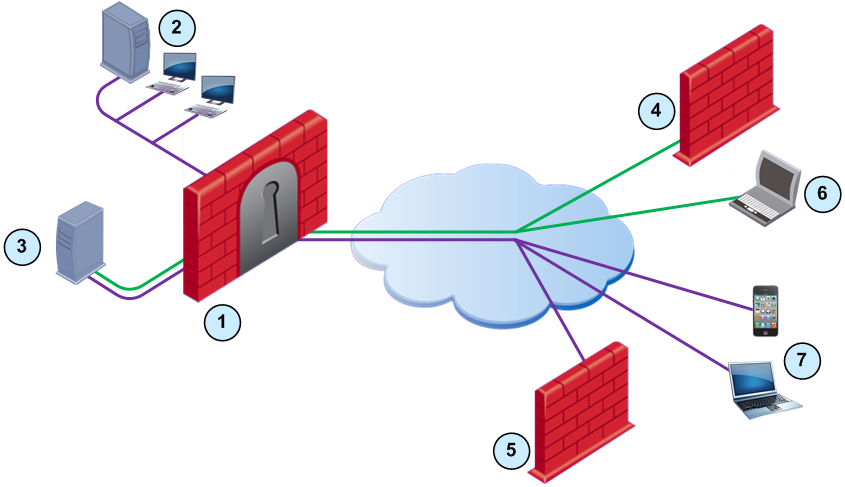
|
|
|
|
Item
|
Description
|

|
IPv4 network traffic
|

|
IPv6 network traffic
|
1
|
Security Gateway for dual stack network
|
2
|
Internal network (IPv6 traffic)
|
3
|
Dual stack web server in the DMZ
|
4
|
Security Gateway for IPv4 network
|
5
|
Security Gateway for IPv6 network
|
6
|
Mobile device (IPv4 traffic)
|
7
|
Mobile devices (IPv6 traffic)
|

|
Note - For R76 Security Gateways, you can configure the interfaces to use only IPv6 addresses.
|
Access Control and the Rule Base
A primary goal of a firewall is to control access and traffic to and from the internal and external networks. The Firewall lets system administrators securely control access to computers, clients, servers and applications. The Firewall Rule Base defines the quality of the access control and network performance. Rules that are designed correctly make sure that a network:
- Only allows authorized connections and prevents vulnerabilities in a network
- Gives authorized users access to the correct internal networks
- Optimizes network performance and efficiently inspects connections
How to Use this Guide
When you configure a Firewall, it is necessary that you understand how it is connected to the other Software Blades. For example, you must add a rule for the Firewall to allow remote users to connect to the internal network. In addition, you can enable Software Blades to supply advanced protection for the network, such as IPS and Anti-Bot.
Some of the sections in this guide tell you how to enable a sample configuration of a Software Blade. Make sure that you read the applicable Administration Guide for the Software Blade before you configure the feature for a production environment. Each section also explains rules that you must add to the Firewall Rule Base to complete the configuration for that feature.
Software Blades in this Guide
SmartDashboard Toolbar
You can use the SmartDashboard toolbar to do these actions:
Icon
|
Description
|

|
Open the SmartDashboard menu.
When you are instructed to selected menu options, click this button first.
For example, if you are instructed to select > , click this button to open the Manage menu and then select the Users and Administrators option.
|

|
Save current policy and all system objects.
|

|
Open a policy package, which is a collection of policies saved together with the same name.
|

|
Refresh policy from the Security Management Server.
|

|
Open the Database Revision Control window.
|

|
Change global properties.
|

|
Verify rule base consistency.
|
|
Install the policy on Security Gateways or VSX Gateways.
|

|
Open SmartConsoles.
|
|

