Remote Access to the Network
Overview
Check Point Mobile Access Software Blade extends the functionality of a Firewall and lets remote users easily and securely use the Internet to connect to internal networks. Remote users start a standard HTTPS request to the Mobile Access Security Gateway. They can then authenticate with multiple options such as: user name/password, certificates, or SecurID.
SmartDashboard lets you easily create user groups and give the users access to the applicable applications. These are some of the different corporate applications that users can access:
- Web applications - A set of URLs that are accessed with an Internet browser. For example: inventory management or HR management applications.
- File share - A collection of files that are available with a specified protocol, such as SMB for Windows. Users can read, write, and delete files that are stored on the network.
- Citrix clients - Users can connect to internal XenApp servers.
- Web mail services - Mobile Access provides a front end for email servers that support IMAP and SMTP protocols. You can also configure other Web-based mail services, such as OWA (Outlook Web Access) and iNotes (IBM Lotus Domino Web Access).
For more about using the Mobile Access Software Blade, see R76 Mobile Access Administration Guide.
Check Point Mobile Access Solutions
Check Point Mobile Access has a range of flexible clients and features that let users access internal resources from remote locations. All these solutions include these features:
- Enterprise-grade, secure connectivity to corporate resources
- Strong user authentication
- Granular access control
For more information about the newest versions of Mobile Access solutions and clients, go to sk67820.
Client-Based vs. Clientless
Check Point remote access solutions use IPsec and SSL encryption protocols to create secure connections. All Check Point clients can work through NAT devices, hotspots, and proxies in situations with complex topologies, such as airports or hotels. These are the types of installations for remote access solutions:
- - Client application installed on endpoint computers and devices. Clients are usually installed on a managed device, such as a company-owned computer. The client supplies access to most types of corporate resources according to the access privileges of the user.
- - Users connect through a web browser and use HTTPS connections. Clientless solutions usually supply access to web-based corporate resources.
- - Users connect through a web browser and a client is installed when necessary. The client supplies access to most types of corporate resources according to the access privileges of the user.
Mobile Access Clients
- Check Point Mobile - An app that creates a secure container on the mobile device to give users access to internal websites, file shares, and Exchange servers.
- Mobile VPN - A full L3 tunnel app that gives users network access to all mobile applications.
- Check Point Mobile for Windows - A Windows IPsec VPN client that supplies secure IPsec VPN connectivity and authentication.
Mobile Access Web Portal
The Mobile Access Portal is a clientless SSL VPN solution that supplies secure access to web-based resources. After users authenticate to the portal, they can access Mobile Access applications such as Outlook Web App and a corporate wiki.
SSL Network Extender
SSL Network Extender is an on-demand SSL VPN client and is installed on the computer or mobile device from an Internet browser. It supplies secure access to internal network resources.
Configuring Remote Access to Network Resources
Sample Mobile Access Workflow
This is a high-level workflow to configure remote access to the internal applications and resources.
- Use SmartDashboard to enable the Mobile Access Software Blade on the Security Gateway.
- Follow the steps in the Mobile Access Configuration wizard to configure these settings:
- Select mobile device access clients
- Define the Mobile Access portal
- Define the web applications, for example Outlook Web App
- Connect to the AD server for user information
- For VPN clients, add Firewall rules to allow the mobile device connections.
- Optional: Distribute client certificates to authenticate the mobile users.
For R76 and higher, use the Certificate Creation and Distribution Wizard.
- Users download the Check Point Mobile app.
- Users open the Check Point Mobile app and enter the Mobile Access Site Name and necessary authentication, such as user name and password.
From SmartDashboard, enable Mobile Access
|
è
|
Configure settings in Mobile Access wizard
|
è
|
Add rules for mobile devices to Firewall
|
è
|
Generate a certificate for the clients
|
|
|
|
|
|
|
ê
|
|
|
Users can access internal resources
|
ç
|
Users open app and enter settings
|
ç
|
Users download app
|
Sample Mobile Access Deployment
This is a sample deployment of a Mobile Access Security Gateway with an AD and Exchange server in the internal network.
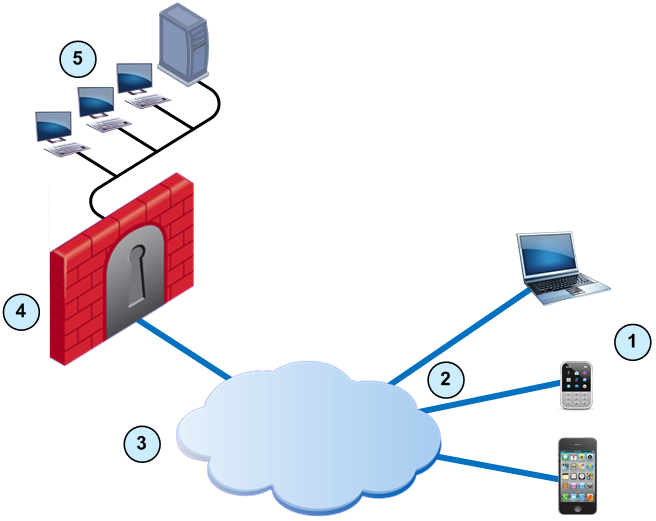
Item
|
Description
|
1
|
Mobile devices
|
2
|
Mobile Access tunnels
|
3
|
Internet (external networks)
|
4
|
Mobile Access Security Gateway
|
5
|
Internal network resources, AD and Exchange servers
|
In this sample Mobile Access deployment, a mobile device uses a Mobile Access tunnel to connect to the internal network. The Mobile Access Security Gateway decrypts the packets and authenticates the user. The connection is allowed and the mobile device connects to the internal network resources.
Using the Mobile Access Configuration Wizard
This procedure describes how to enable and configure the Mobile Access Software Blade on a Security Gateway with the Configuration wizard. For this sample configuration, the AD user group contains all the users that are allowed to connect to the internal network. The deployment is based on the Sample Mobile Access Deployment.
This configuration lets these clients connect to internal resources:
- Android and iOS mobile devices
- Windows and Mac computers
- Internet browsers can open a SSL Network Extender connection to the internal network
To configure Mobile Access:
- In SmartDashboard, from the tree, double-click the Security Gateway.
The window opens.
- In , select .
The page of the opens.
- Configure the Security Gateway to allow connections from the Internet and mobile devices. Select these options:
- Click .
The page opens.
- Enter the primary URL for the Mobile Access portal. The default is
https://<IPv4 address of the gateway>/sslvpn. - Click .
The page opens.
- Configure the applications that are shown:
- In , make sure is selected.
- , enter the domain for the Exchange server and select these options:
The Mobile Access portal shows links to the Demo web and Outlook Web App applications. The client on the mobile device shows links to the other applications.
- Click .
The page opens.
- Select the AD domain and enter the user name and password.
- Click .
The Security Gateway makes sure that it can connect to the AD server.
- Click .
The page opens.
Click and then select the group .
- Click and then click .
The closes.
- Click .
The window closes.
Allowing Mobile Connections
The Mobile Access Configuration Wizard, enables and configures the Mobile Access Software Blade. It is necessary to add Firewall rules to allow connections from the VPN clients on the computers and devices. Create a Host Node object for the Exchange server, all of the other objects are predefined.
Name
|
Source
|
Destination
|
VPN
|
Service
|
Action
|
Install On
|
Track
|
Mobile Access Users
|
Any
|
Exchange_
Server
|
RemoteAccess
|
HTTP
HTTPS
MSExchange
|
Accept
|
MobileAccess_
Gateway
|
Log
|
All connections from the RemoteAccess VPN community to the Exchange server are allowed. These are the only protocols that are allowed: HTTP, HTTPS, and MSExchange. This rule is installed on the MobileAccess_Gateway Security Gateway.
Defining Access to Applications
Use the page to define rules that let users access Mobile Access applications. The applications that are selected in the Configuration wizard are automatically added to this page. You can also create and edit the rules that include these SmartDashboard objects:
- Users and user groups
- Mobile Access applications
- Mobile Access Security Gateways
Sample Mobile Access Policy
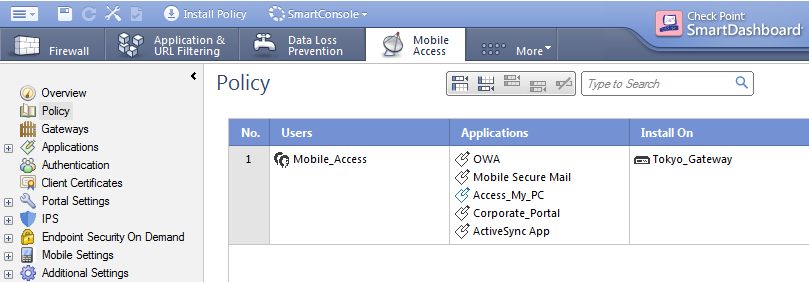
The Mobile Access rule lets the users in the Mobile_Access AD group access these applications on the Tokyo_Gateway:
- OWA - Outlook Web Access
- Mobile Secure Mail - Check Point Mobile clients can connect to the Exchange mail server to use email applications
- Access_My_PC - Remote Desktop application
- Corporate_Portal - Connect to the internal corporate web portal
- ActiveSync App - Connect to the Exchange mail server to use email applications such as Outlook
Activating Single Sign On
Enable the SSO (Single Sign On) feature to let users authenticate one time for applications that they use during Mobile Access sessions. The credentials that users enter to log in to the Mobile Access portal can be re-used automatically to authenticate to different Mobile Access applications. SSO user credentials are securely stored on the Mobile Access Security Gateway for that session and are used again if users log in from different remote devices. After the session is completed, the credentials are stored in a database file.
By default, SSO is enabled on new Mobile Access applications that use HTTP. Most Web applications authenticate users with specified Web forms. You can configure SSO for an application to use the authentication credentials from the Mobile Access portal. It is not necessary for users to log in again to each application.
To configure SSO:
- In the tab, select .
The page opens.
- Select an application and click .
The application properties window opens and shows the page.
- For Web form applications, do these steps:
- In the section, select and click .
The window opens.
- Select .
- Click .
- Select .
- Click .
- Install the policy.
Connecting to a Citrix Server
Citrix Services
The Mobile Access Software Blade integrates the Firewall Citrix clients and services. It is not necessary to use STA (Secure Ticketing Authority) servers in a Mobile Access Security Gateway deployment because Mobile Access uses its own STA engine. You can also use Mobile Access in a deployment with STA and CSG (Citrix Secure Gateway) servers.
The Mobile Access server certificate must use a FQDN (Fully Qualified Domain Name) that is issued to the FQDN of the Mobile Access Security Gateway.
Sample Deployment with Citrix Server
This is a sample deployment of a Mobile Access Security Gateway and a Citrix web server in the DMZ. The Citrix XenApp server is connected to the internal network.
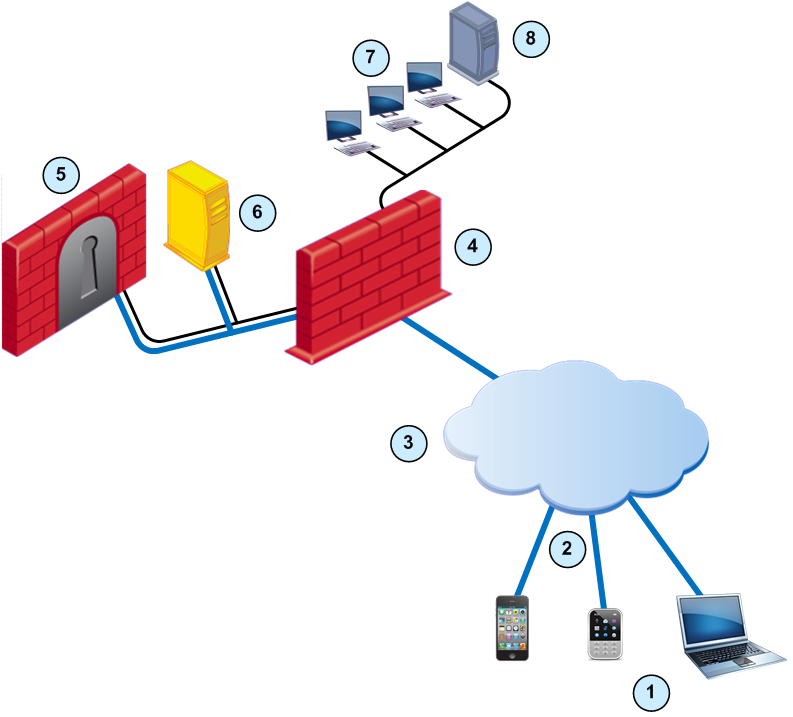
Item
|
Description
|
1
|
Mobile devices
|
2
|
Mobile Access tunnels
|
3
|
Internet (external networks)
|
4
|
Security Gateway for the internal network
|
5
|
Mobile Access Security Gateway in the DMZ
|
6
|
Citrix web interface
|
7
|
Internal network resources
|
8
|
Citrix XenApp (MetaFrame) server
|
Configuring Citrix Services for Mobile Access
This procedure describes how to configure Mobile Access to let remote users connect to Citrix applications. The deployment is based on the Sample Deployment with Citrix Server.
To configure Citrix services:
- In the tab, select .
- Click .
The page of the window opens.
- Enter the for the Citrix server object.
- From the navigation tree, click .
- Create a new object for the Citrix web interface server, in , click .
The window opens.
- Enter the settings for the Citrix web interface server and the click .
- In Services, select one or more of these services that the Cirtrix web interface server supports:
- From the navigation tree, click .
- Configure the settings for the link to the Citrix services in the Mobile Access portal:
- - The text that is shown for the Citrix link
- - The URL for the directory or subdirectory of the Citrix application
- - Text that is shown when the user pauses the mouse pointer above the Citrix link
- From the navigation tree, select .
- Enable Single Sign On for Citrix services, select these options:
- Click .
The Citrix server object is added to .
- From the Mobile Access navigation tree, select .
- Add the Citrix services object to the applicable rules.
- Right-click on the Applications cell of a rule and select .
- Select the Citrix services object.
- Install the policy.
Endpoint Compliance Check
The Mobile Access Software Blade lets you use the Endpoint Security on Demand feature to create compliance policies and add more security to the network. Mobile devices and computers are scanned one time to make sure that they are compliant before they can connect to the network.
The Endpoint Compliance scanner is installed on mobile devices and computers with ActiveX (for Internet Explorer on Windows) or Java. The scan starts when the Internet browser tries to open the Mobile Access Portal.
Compliance Policy Rules
The Endpoint Compliance policy is composed of different types of rules. You can configure the security and compliance settings for each rule or use the default settings.
These are the rules for an Endpoint Compliance policy:
- Windows security - Microsoft Windows hotfixes, patches and Service Packs.
- Anti-spyware protection - Anti-spyware software.
- Ant-virus protection - Anti-virus software version and virus signature files.
- Firewall - Personal firewall software.
- Spyware scan - Action that is done for different types of spyware.
- Custom - Compliance rules for your organization, for example: applications, files, and registry keys.
- OR group - A group of the above rules. An endpoint computer is compliant if it meets one of the rules in the group.
Creating an Endpoint Compliance Policy
The default setting for Endpoint Security on Demand is that all endpoint computers cannot log in to the Mobile Access portal until they are compliant with the Endpoint Compliance policy. Use the window to create or edit an Endpoint Compliance policy.
This procedure shows how to configure a sample policy for company laptop computers.
To create an Endpoint Compliance policy:
- In the tab, select .
- Click .
The window opens.
- Click .
The window opens.
- Enter the and for the policy.
- Click .
The window opens.
- Select the rules for the policy.
These are the rules for the sample laptop computer policy:
- Default Windows Security rule
- High security Anti-Spyware applications check
- High security Anti-Virus applications check
- High security spyware scan
- Medium security Firewall applications check
- Click .
The window shows the rules for the policy.
- Select .
When this feature is selected, the scan for endpoint computers that are compliant with the Anti-Virus or Anti-Spyware settings is changed. These computers do not scan for spyware when they connect to a Mobile Access Security Gateway.
- Click .
The window opens.
- Click .
Configuring Compliance Settings for a Security Gateway
The Firewall on a Mobile Access Security Gateway only allows access to endpoint computers that are compliant with the Endpoint Compliance policy.
This procedure shows how to configure the Laptop Computer policy for a Security Gateway.
To configure the Endpoint Compliance settings:
- In the tab, select .
- Select the Security Gateway and click .
The page of the Security Gateway properties window opens.
- Select .
- Click policy and from the drop-down menu select .
- Click .
- Install the policy on the Mobile Access Security Gateway.
Using Secure Workspace
Secure Workspace is a security solution that allows remote users to connect to enterprise network resources safely and securely. The Secure Workspace virtual workspace provides a secure environment on endpoint computers that is segregated from the "real" workspace. Users can only send data from this secure environment through the Mobile Access portal. Secure Workspace users can only access permitted applications, files, and other resources from the virtual workspace.
Secure Workspace creates an encrypted folder on the computer called My Secured Documents and can be accessed from the virtual desktop. This folder contains temporary user files. When the session terminates, Secure Workspace deletes this folder and all other session data.
For more about configuring Secure Workspace, see the R76 Mobile Access Administration Guide.
To enable Secure Workspace on a Mobile Access Security Gateway:
- In the tab, select .
- Select the Security Gateway and click .
The page of the Security Gateway properties window opens.
- Select .
- Click and then install the policy.
|

