Step 3 - Configuration on Security Gateways
This is a step in the On-Premises Management Deployment.
Part 1 - Prerequisites for Security Gateways
-
The required version of the Security Gateway / Cluster must be up and running.
Platform
Instructions
Security Gateways that run Gaia OS
-
Download the required image from sk180605.
-
Follow the Installation and Upgrade Guide for your version.
-
Install the applicable Jumbo Hotfix Accumulator.
Quantum Spark Appliances that run OS
-
R81.10.05 and higher (we recommend R81.10.17).
Refer to the corresponding Home Page SK article in sk179615.
-
Centrally Managed.

Note - For automatic on-boarding of supported SD-WAN Security Gateways, see the requirements in sk180557.
-
-
The Security Gateway / Quantum Spark Appliance / Cluster Members must connect to the Internet.
Part 2 - Configuration of SD-WAN interfaces on the Security Gateway
|
|
Note - For a Maestro Security Group, see Configuring a Maestro Security Group for SD-WAN. |
-
Configure the SD-WAN interfaces on the Security Gateway / each Cluster Member.
You can configure the required SD-WAN interfaces in Gaia Portal or Gaia Clish.

Notes:
-
This configuration also applies to VLAN interfaces.
If you configure SD-WAN on a VLAN interface, then it is not supported to configure SD-WAN on the parent physical interface.
-
This configuration also applies to clusters, in which the IP addresses of Cluster Members and the Cluster Virtual IP address belong on different subnets.
 Configuration of a Security Gateway in Gaia Portal
Configuration of a Security Gateway in Gaia Portal
-
Connect to Gaia Portal.
-
From the left tree, click Network Interfaces.
-
Configure the applicable interfaces that you plan to use for SD-WAN.
Enable the interfaces and configure the IPv4 address.
See the Gaia Administration Guide for your version > "Network Management" > "Network Interfaces" > "Physical Interfaces".
-
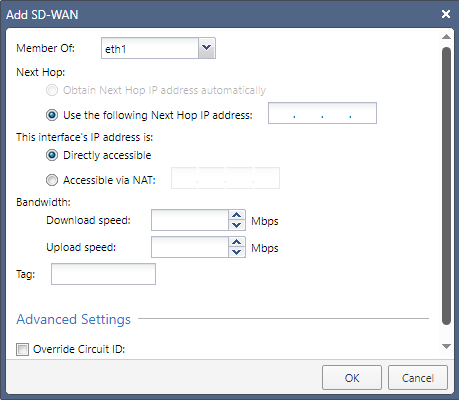
In the section SD-WAN Interfaces, click Add.
Example from R81.20 Jumbo Hotfix Accumulator, Take 79 and higher:
Example from R81.20:
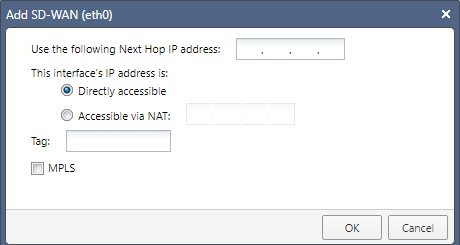
-
Select the applicable interface that connects to the applicable ISP.
-
In the section Next Hop, configure the applicable next hop IP Address for the ISP, to which this interface connects.
In the field Use the following Next Hop IP address, enter the applicable IP address.

Note - This section title "Next Hop" is available in these Security Gateway versions:
-
R82 and higher.
-
R81.20 Jumbo Hotfix Accumulator, Take 79 and higher (PRJ-53464).
-
-
In the section This interface's IP address is, configure how SD-WAN rules get the IP address of this interface:
-
Directly accessible
Specifies that this interface has a public IP address, to which peers can connect directly.
This applies to the interface with an IP address that is configured statically or by a DHCP server.

Note - You must select this option if an ISP assigns an IP address dynamically (for example, when a Security Gateway connects to the Internet through a modem).
For additional information, see SD-WAN Configuration for DAIP Security Gateways.
-
Accessible via NAT
Specifies that an external device or an ISP applies Static NAT on the IP address of this interface.
Enter the applicable static IP address after this external NAT, as the peers receive it.

Notes:
-
This option applies only to the "" configuration (see SD-WAN Connection Type - "Overlay").
This option configures the IP address that VPN peers must use to negotiate the Site to Site VPN tunnel with this Security Gateway.
-
You do not need to configure NAT rules in SmartConsole for this external NAT.
-
Summary:
Option in Gaia Portal
When to Select
Directly accessible
SD-WAN interface with a Static IP address that connects to your network directly (without a NAT device):
[Security Gateway] (SD-WAN interface with a Static IP address) --- (no NAT device) ---
SD-WAN interface with a Dynamically Assigned IP Address that connects to your network directly (without a NAT device):
[Security Gateway] (SD-WAN interface with DAIP) --- (no NAT device) ---
SD-WAN interface with a Static IP address that is located behind a Dynamic NAT device:
[Security Gateway] (SD-WAN interface with a Static IP address) --- [NAT device that assigns an IP address dynamically] ---
Accessible via NAT
This option applies only to the "" configuration (see SD-WAN Connection Type - "Overlay").
SD-WAN interface with a Static IP address that is located behind a Static NAT device:
[Security Gateway] (SD-WAN interface with a Static IP address) --- [NAT device that assigns a static IP address] ---
-
-
Optional: In the section Bandwidth, configure the applicable limits for the Download speed and Upload speed.

Note - This section is available only in these Security Gateway versions:
-
R82 and higher.
-
R81.20 Jumbo Hotfix Accumulator, Take 79 and higher (PRJ-53464).
You can use these limits in the SD-WAN Steering Behavior objects.
See Configuring Steering Behavior > Criteria > WAN Link Utilization > Link Aggregation > Selection Method.
-
-
Optional: In the Tag field, enter a desired interface tag. Example:
ISP1See the description and the example in WAN Link Mapping.
-
Select MPLS, if this interface connects to to a Private Link (for example, MPLS).

Note - This checkbox is available only in these Security Gateway versions:
-
R81.20 Jumbo Hotfix Accumulator, Take 76 and lower.
-
R81.20 without the Jumbo Hotfix Accumulator.
-
-
Optional: In the section Advanced Settings:

Note - This section is available only in these Security Gateway versions:
-
R82 and higher.
-
R81.20 Jumbo Hotfix Accumulator, Take 79 and higher (PRJ-53464).
-
Select Override Circuit ID.
See SD-WAN Circuit ID.
-
Enter a value between 0 and 255.

Important:
-
The value 0 is the default for Public WAN Links.
-
The value 1 is the default for Private WAN Links.
-
-
-
Click OK.
 Configuration of a Security Gateway in Gaia Clish
Configuration of a Security Gateway in Gaia Clish
For more information, see SD-WAN Configuration in Gaia Clish.
-
Connect to the command line on the Security Gateway / each Cluster Member.
-
Log in.
-
If your default shell is the Expert mode, go to Gaia Clish:
clish -
Configure the applicable interfaces that you plan to use for SD-WAN.
Enable the interfaces and configure the IPv4 address.
See the Gaia Administration Guide for your version > "Network Management" > "Network Interfaces" > "Physical Interfaces".
-
Configure the applicable next hop IP Address for the ISP, to which this interface connects:
set interface <Name of Interface> sdwan next-hop <IP Address of ISP Next Hop>Example:
set interface eth1 sdwan next-hop 192.168.20.1 -
Configure how SD-WAN rules get the IP address of this interface:
-
If this interface has a public IP address, to which peers can connect directly, do not configure anything.
This applies to the interface with an IP address that is configured statically or by a DHCP server.

Notes:
-
In Gaia Portal, this corresponds to the option "Directly accessible".
-
You must select this option if an ISP assigns an IP address dynamically (for example, when a Security Gateway connects to the Internet through a modem).
For additional information, see SD-WAN Configuration for DAIP Security Gateways.
-
-
If an external device or an ISP applies NAT on the IP address of this interface, then configure the applicable IP address after this external NAT, as the peers receive it:
set interface <Name of Interface> sdwan next-hop <IP Address> nat <IP Address after External NAT>Example:
set interface eth1 sdwan next-hop 192.168.20.1 nat 172.30.40.5
Notes:
-
In Gaia Portal, this corresponds to the option "Accessible via NAT".
-
This option applies only to the "" configuration (see SD-WAN Connection Type - "Overlay").
This option configures the IP address that VPN peers must use to negotiate the Site to Site VPN tunnel with this Security Gateway.
-
You do not need to configure NAT rules in SmartConsole for this external NAT.
-
Summary:
Option in Gaia Clish
When to Configure
Directly accessible
SD-WAN interface with a Static IP address that connects to your network directly (without a NAT device):
[Security Gateway] (SD-WAN interface with a Static IP address) --- (no NAT device) ---
SD-WAN interface with a Dynamically Assigned IP Address that connects to your network directly (without a NAT device):
[Security Gateway] (SD-WAN interface with DAIP) --- (no NAT device) ---
SD-WAN interface with a Static IP address that is located behind a Dynamic NAT device:
[Security Gateway] (SD-WAN interface with a Static IP address) --- [NAT device that assigns an IP address dynamically] ---
Accessible via NAT
This option applies only to the "" configuration (see SD-WAN Connection Type - "Overlay").
SD-WAN interface with a Static IP address that is located behind a Static NAT device:
[Security Gateway] (SD-WAN interface with a Static IP address) --- [NAT device that assigns a static IP address] ---
-
-
If this interface connects to a Private Link (for example, MPLS):
set interface <Name of Interface> sdwan next-hop <IP Address> is_mpls true
Note - This command is available only in these Security Gateway versions:
-
R81.20 Jumbo Hotfix Accumulator, Take 76 and lower.
-
R81.20 without the Jumbo Hotfix Accumulator.
Example:
set interface eth1 sdwan next-hop 192.168.20.1 is_mpls true -
-
Optional: Configure a desired interface tag:
See the description and the example in WAN Link Mapping.
set interface <Name of Interface> sdwan next-hop <IP Address> tag "<Tag Name>"Example:
set interface eth1 sdwan next-hop 192.168.20.1 tag "ISP1" -
Optional: Configure the download speed limit (in Mbps):
set interface <Name of Interface> sdwan download-speed <1 - 1000000>
Note - This command is available only in these Security Gateway versions:
-
R82 and higher.
-
R81.20 Jumbo Hotfix Accumulator, Take 79 and higher (PRJ-53464).
See Configuring Steering Behavior > Criteria > WAN Link Utilization > Link Aggregation > Selection Method.
Example:
set interface eth1 sdwan download-speed 500000> -
-
Optional: Configure the upload speed limit (in Mbps):
set interface <Name of Interface> sdwan upload-speed <1 - 1000000>
Note - This command is available only in these Security Gateway versions:
-
R82 and higher.
-
R81.20 Jumbo Hotfix Accumulator, Take 79 and higher (PRJ-53464).
You can use these limits in the SD-WAN Steering Behavior objects.
See Configuring Steering Behavior > Criteria > WAN Link Utilization > Link Aggregation > Selection Method.
Example:
set interface eth1 sdwan upload-speed <1 - 100000> -
-
Examine the SD-WAN configuration on the interface:
show interface <Name of Interface> sdwan -
Save the configuration:
save config
-
-
Configure the applicable default routes on the Security Gateway / each Cluster Member.
The Security Gateway / Cluster Member uses these default routes:
-
For traffic that does not match the configured SD-WAN rules.
-
For traffic that the Security Gateway / Cluster Member creates (for example, to connect to Check Point cloud).
See the Gaia Administration Guide for your version > "Network Management" > "IPv4 Static Routes".

Important:
-
For each Internet Service Provider (ISP), you must configure one default route with unique priority.
The reasons for this configuration are:
-
A legacy ISP backup that is based on the link availability, if the SD-WAN service does down on the Security Gateway / Cluster Member.
-
The Security Gateway / Cluster Member sends its traffic (local connections) to the Internet based on the operating system routing table and not based on SD-WAN Policy rules.
-
The Security Gateway / Cluster Member must have an active route to the destination of the packet to process it. This applies to both cleartext traffic and VPN traffic.
If only one ISP has a default route, and it goes down, then all overlay connections are lost and do not fail over.
This does not apply in Local Breakout, because its mechanism has its routing table that does not depend on the operating system routing.
-
-
The Security Gateway / Cluster Member cannot have different ISP default routes with the same priority.
When the Security Gateway / Cluster Member cannot use an ISP default route with the lowest priority (for example, cannot reach the ISP), it uses another ISP default route with the next higher priority.
-
It is not mandatory to configure static routes to branches, if they are part of the "" because the VPN clean up rule in the SD-WAN Policy is always matched.
-
If the Security Gateway / Cluster Member has a private line, such as MPLS, which is part of the overlay, then it is a best practice to configure such routes that send traffic for all the overlay destination networks to the MPLS next hop. In this case, even if all ISP links are down, and no active default route exist in the operating system kernel, the specific route on the MPLS makes sure that the "" traffic continues to work over the MPLS SD-WAN interface. Without an active route to the destination, the packet is lost in the routing table, before the VPN encryption takes place.
-
-
Configure the SD-WAN interfaces on the Quantum Spark Appliance / each Quantum Spark Cluster Member.

Note - This configuration also applies to VLAN interfaces.
If you configure SD-WAN on a VLAN interface, then it is not supported to configure SD-WAN on the parent physical interface.
You configure these SD-WAN interfaces in the WebUI, or Gaia Clish.
 Configuration of a Quantum Spark Appliance in the WebUI
Configuration of a Quantum Spark Appliance in the WebUI
See the R81.10.X Quantum Spark Centrally Managed Administration Guide for 1500, 1600, 1800, 1900, 2000 Appliances > "Managing the Device" > "Configuring Internet Connectivity".
-
Connect to the WebUI.
-
From the left tree, click Device.
-
In the middle pane, expand the section Network and click Internet.
-
Configure two Internet connections - one for each ISP:
-
Click Add an Internet connection.
The New Internet Connection window opens.
-
On the Configuration tab:
-
In the Connection name, enter the applicable name for this connection.
-
In the Interface field, select the applicable interface.
-
In the Connection type field, select the applicable type.
-
-
On the Connection Monitoring tab:
-
Select Automatically detect loss of connectivity to the default gateway.
-
Select Monitor connection state by sending probe packets to one or more servers on the Internet.
Local connections (originating from the Quantum Spark Appliance) use the main routing table and are not affected by SD-WAN Local Breakout routing.
-
-
On the Advanced tab:
Configure the applicable options based on the connection type.
In firmware versions R81.10.15 and higher:
-
Expand the section SD-WAN Settings.
-
Optional: Configure the applicable limits for the Download speed and Upload speed.

Note - You can use these limits in the SD-WAN Steering Behavior objects.
See Configuring Steering Behavior > Criteria > WAN Link Utilization > Link Aggregation > Selection Method.
-
Optional: Select Override circuit ID.
See SD-WAN Circuit ID.
Enter a value between 0 and 255.
-
-
Click Save.
-
 Configuration of a Quantum Spark Appliance in Gaia Clish - R81.10.10 and higher
Configuration of a Quantum Spark Appliance in Gaia Clish - R81.10.10 and higher

Important - The Quantum Spark Appliances configure the SD-WAN next hop based on the Internet configuration.
-
Connect to the command line on the Quantum Spark Appliance / each Quantum Spark Cluster Member.
-
If your default shell is the Expert mode, go to Gaia Clish:
clish -
Configure two Internet connections - one for each ISP.
Use this command:
add internet-connection name "<Name of Connection>" interface <Name of Interface>See the R81.10.X Quantum Spark CLI Reference Guide for 1500, 1600, 1800, 1900, 2000 Appliances > "Configuring the Internet Connections" > "Adding Internet Connections".
Example:
add internet-connection name Internet2 interface DMZ type static ipv4-address 192.168.223.5 subnet-mask 255.255.255.0 default-gw 192.168.223.4
 Configuration of a Quantum Spark Appliance in CLI - only R81.10.05, R81.10.07, and R81.10.08
Configuration of a Quantum Spark Appliance in CLI - only R81.10.05, R81.10.07, and R81.10.08

Important - The Quantum Spark Appliances configure the SD-WAN next hop based on the Internet configuration.
-
Connect to the command line on the Quantum Spark Appliance / each Quantum Spark Cluster Member.
-
If your default shell is the Expert mode, go to Gaia Clish:
clish -
Configure two Internet connections - one for each ISP.
Use this command:
add internet-connection name "<Name of Connection>" interface <Name of Interface> <options>See the R81.10.X Quantum Spark CLI Reference Guide for 1500, 1600, 1800, 1900, 2000 Appliances > "Configuring the Internet Connections" > "Adding Internet Connections".
Example:
add internet-connection name Internet2 interface DMZ type static ipv4-address 192.168.223.5 subnet-mask 255.255.255.0 default-gw 192.168.223.4
-
Part 3 - Installation of the Nano-Agent on the Security Gateway
The Nano-Agent connects the Security Gateway / each Cluster Member to Infinity Portal, and enable the automatic installation and update of the SD-WAN policy from Infinity Portal.
There are two possible onboarding options - automatic (recommended) and manual.
|
|
Note - For automatic on-boarding of supported SD-WAN Security Gateways, see the requirements in sk180557. |
-
In SmartConsole, make sure the Management Server is connected to Infinity Portal and automatic onboarding is enabled.
-
From the left navigation panel, click Infinity Services.
-
At the top, SmartConsole must show Connected to Infinity Portal and Status: Active.
-
In the bottom right corner, on the right of Gateways Connector, click Edit.
-
The option Connection between your Security Gateways and Infinity Portal isenabled must show ON.
-
-
In Infinity Portal, check if the Security Gateway is already connected:
-
In Infinity Portal, in the top left corner, click the button.
-
From the drop-down list, in the section Quantum, click SD-WAN.
-
From the left navigation panel, click Network.
-
In the middle section, click Agents.
Possible next steps:
-
If your Security Gateway appears on this page, then skip to "Part 4 - Configuration of the Security Gateway object in SmartConsole" below.
-
If your Security Gateway does not appear on this page, then in SmartConsole, connect this Security Gateway:
-
In the bottom right corner, on the right of Gateways Connector, click Edit.
-
In the section Select Security Gateways to connect, select Specific and select this Security Gateway.
-
In the section Establish connection to Security Gateways, select Immediately.
-
At the bottom, click OK.
-
Wait for several minutes.
-
In Infinity Portal, check the Agents page again.
-
-
-
|
|
Note - For a Maestro Security Group, see Configuring a Maestro Security Group for SD-WAN. |
-
Get the Authentication Token from the Quantum Profile in SD-WAN Application.
-
In the Infinity Portal, in the top left corner, click the button.
-
From the drop-down list, in the section Quantum, click SD-WAN.
-
In the middle section, click Profiles.
-
Click Quantum Profile to open it.

Note - The SD-WAN Application creates this Quantum Profile automatically in these cases:
-
You connect your on-premises Management Server to Infinity Portal and configure Object Sharing.
-
You enable the Smart-1 Cloud Application and configure Object Sharing.
-
-
From the top of the page, click the Enforce button.
Note - Although you did not configure the SD-WAN Policy yet, this step is necessary.

In the popup window that opens, click Publish & Enforce Policy.
-
In the middle pane, in the section Authentication, the field Token must be populated (dots appear instead the actual token value).
This means the service generated the required token.
Example:
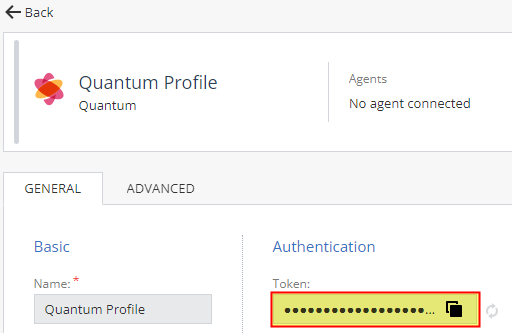
-
Save your token:
-
In the section Authentication, in the field Token, click the Copy icon on the right.
-
Save this string.
You use this token to install the Nano-Agent.

Best Practice - Connect all SD-WAN Security Gateways to Infinity Portal with the same token (to make the policy configuration easier).
-
-
-
Connect to the command line on the Security Gateway / each Cluster Member.
-
Log in.
-
If your default shell is Gaia Clish, go to the Expert mode:
expert -
Install the Nano-Agent:
nano-egg --install --token <Authentication Token you copied earlier from your Quantum Profile>
|
|
Important:
|
Part 4 - Configuration of the Security Gateway object in SmartConsole
-
Connect with SmartConsole to the Security Management Server / Domain Management Server.
-
From the left navigation panel, click Gateways & Servers.
-
Create a new / configure the existing object for the Security Gateway / Cluster in SmartConsole.
-
On the General Properties page (of the Security Gateway / Cluster object), you must enable and configure these Software Blades:
-
Application Control
-
URL Filtering
-
IPsec VPN (if this Security Gateway / Cluster must participate in VPN - see SD-WAN Connection (Steering Behavior) Types).

Note - Installation of an Access Control Policy fails on a Security Gateway / Cluster Member when a Nano-Agent is installed, but the Application Control and URL Filtering Software Blades are not enabled.
See the:
-
Quantum Security Management Administration Guide for your version.
-
Quantum Spark Appliances Centrally Managed Administration Guide for your version.
-
Site to Site VPN Administration Guide for your version.
-
-
On the Network Management page:
(In the Quantum Spark Gateway object, this page is called Topology.)
-
Write down the topology configuration of each existing interface.
-
From the top toolbar, click Get Interfaces and click Get Interfaces With Topology.
-
Accept the imported topology.
-
Make sure for the SD-WAN interfaces, the Network Type column shows External.

Important - The names of SD-WAN interfaces on the Network Management (Topology) page must be the same as the names of these interfaces on the Security Gateway / each Cluster Member.
-
-
Configure the SD-WAN interfaces - Topology and Anti-Spoofing:
-
On the Network Management page (in the Quantum Spark Gateway object, this page is called Topology), select the SD-WAN interface and click Edit.
-
In the Topology section, click Modify.
-
In the Leads To section:
-
Make sure to select Internet (External).
-
-
In the Anti-Spoofing section:
-
Select Perform Anti-Spoofing based on interface topology.
-
Select the applicable Anti-Spoofing action.
-
Optional: Select Don't check packets from and select the applicable Network, Network Group, or Address Range object.
-
Select the applicable Spoof Tracking option.
-
-
Click OK to close the Topology Settings window.
-
Click OK to close the Interface window.
-
-
Make sure the ISP Redundancy configuration is disabled in the Other section > on the ISP Redundancy page.

Note - SD-WAN does not support the ISP Redundancy configuration.
You must disable ISP Redundancy in the Security Gateway object in SmartConsole.
-
Click OK to close the Security Gateway / Cluster properties window.
Part 5 - Configuration of VPN and Security Policy in SmartConsole
If this Security Gateway / Cluster must participate in VPN (see SD-WAN Connection (Steering Behavior) Types), configure the applicable VPN Community of type Star:
-
You must configure the Headquarters Security Gateways that work as Center VPN Gateways.
Configure the applicable Encryption Domain.
-
You must configure the Branch Security Gateways that work as Satellite VPN Gateways:
-
Configure the applicable Encryption Domain.
-
Configure the correct Link Selection.
See VPN - Link Selection.
The correct configuration makes sure you do not lose all VPN connectivity in these scenarios:
-
The main IP address of the Security Gateway object is not one of the link selections.
-
SD-WAN Policy is not loaded.
-
-
On the VPN Routing page of the VPN Community object, select the required setting:
-
If you configure only an SD-WAN Connection Type "" (without "Backhaul"), then select To center only or To center and to other satellites through center.
-
If you configure an SD-WAN Connection Type "Backhaul", then select To center or through the center to other satellites, to Internet and other VPN targets.
-
|
|
Note - SD-WAN does not support Permanent Tunnels. |
See the:
-
Site to Site VPN Administration Guide for your version.
-
Quantum Security Management Administration Guide for your version.
Part 6 - Configuration of Security Policy in SmartConsole
See the Quantum Security Management Administration Guide for your version.
-
Configure the applicable Access Control rules.

Important:
-
You must add an explicit rule to allow the service "
echo-request" between the Security Gateways that participate in this VPN Community.-
This explicit rule is necessary for the WAN Link probing.
-
The position of this explicit rule must be above all rules that may drop this traffic.
-
-
If you selected Accept ICMP requests in SmartConsole > button > Global properties > FireWall page, then you must:
-
Select Last or Before Last for this option on the FireWall page.
-
Configure an explicit rule to allow ICMP requests between the Security Gateways - this probing traffic must be encrypted, which requires an explicit rule.
-
For more information, see SD-WAN Best Practices > sections about ICMP Probing.
-
-
Configure the applicable NAT rules to hide internal networks behind this Security Gateway / Cluster.

Important - If you configure an SD-WAN Connection Type "", then it is best to avoid NAT on traffic between internal networks when you configure "Hide NAT".
Do one of these, based on your requirements:
-
Add an explicit Manual NAT rule (above all Automatic NAT rules) to forbid NAT for traffic between the applicable Source and Destination networks:
-
In the Original columns, select the applicable Source and Destination networks.
-
In the Translated columns, remove all objects so that these cells show "
=Original".
-
-
In the properties of the VPN Community object > on the Advanced page, select Disable NAT inside the VPN Community.
-
-
Install the Access Control Policy on the Security Gateway / Cluster.
What is Next?
Follow Step 4 - SD-WAN Wizard.
