Settings
In the Settings tab, you can view and manage the dashboard settings, customize the detailed view of the private information for users, applications and devices.
Audit Trail
The Audit Trail screen shows the logs for the system.
You can search the audit logs by Time, Severity, Admin User, Module, Category, Event, and Event details.
Select one or more drop-down search options to produce a report of specific log entries.
-
You can filter every column in the table:
-
Click Filter
 above the table.
above the table. -
On the Filters pane on the right side of the window, adjust information you want to view.
-
-
You can also export
 the information from the table to CSV file, which will create a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use filter to select the required information for the file.
the information from the table to CSV file, which will create a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use filter to select the required information for the file. If the number of audit logs exceeds 10,000, processing the data may take time. So the export is performed offline and an email is sent to the registered address with the link to download the CSV file. The link is valid for 7 days.
-
You can set the number of the rows to list on the screen, and scroll to view previous items.
Customization
Block Page
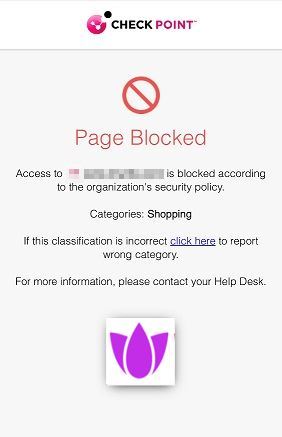
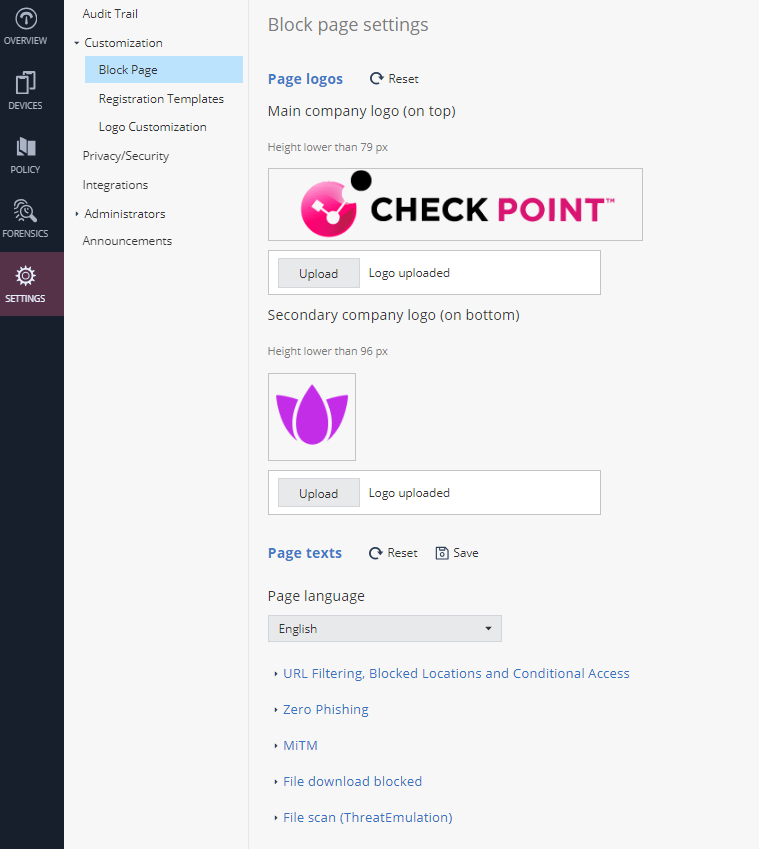
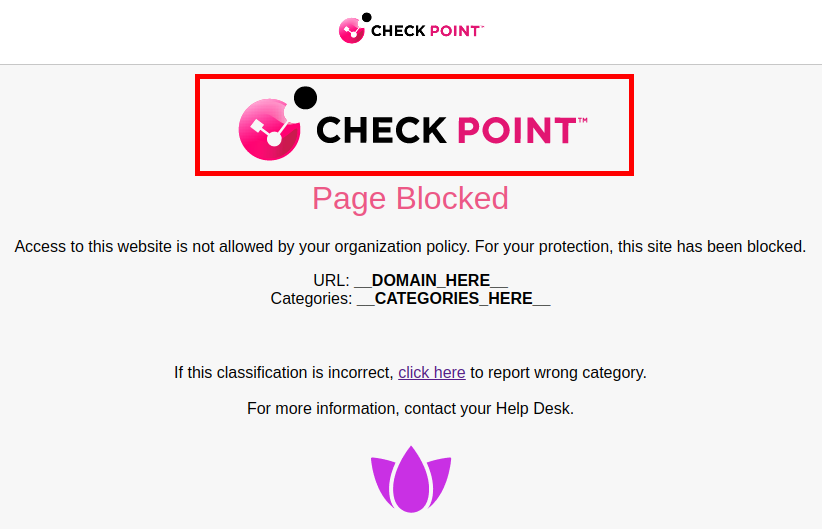
The Block Page setting allows you to customize the content displayed on the block page that appears when a user accesses a web page blocked by the organization's security policy.
To customize, go to Settings > Customization > Block Page.
|
|
Note - To prevent Cross-Site Scripting (XSS) attacks, the text on the Block Page is always sanitized. Any hyperlinks or URLs added to this page are displayed as plain text on mobile devices. |
To customize the block page:
-
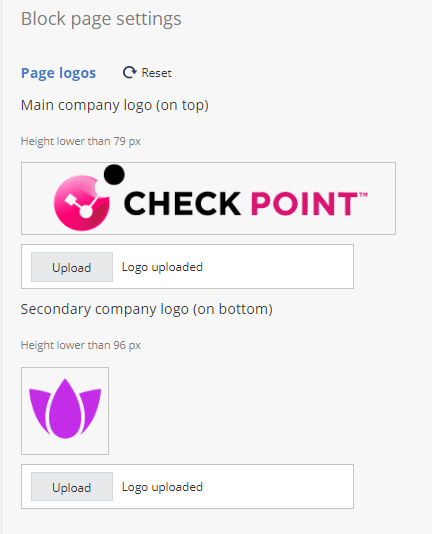
To add the main logo, in the Main company logo section, click Upload and upload the image for the main logo. Check Point logo is the default.

Note - The height of the logo must be less than 79 pixels. Supported file types are .png and .jpeg, with a maximum size of 150KB.
-
To add the secondary logo, in the Secondary company logo section, click Upload and upload the image for the secondary logo.

Note - The height of the logo must be less than 96 pixels. Supported file types are .png and .jpeg, with a maximum size of 150KB.
-
In the Page texts section, select the language of text to be displayed on the block page and click Save.
The default language is English.
To reset to default language, click Reset and then Save.

Note - If the mobile OS is configured in an unsupported language, the block page is displayed in English.
-
Expand any of these:
-
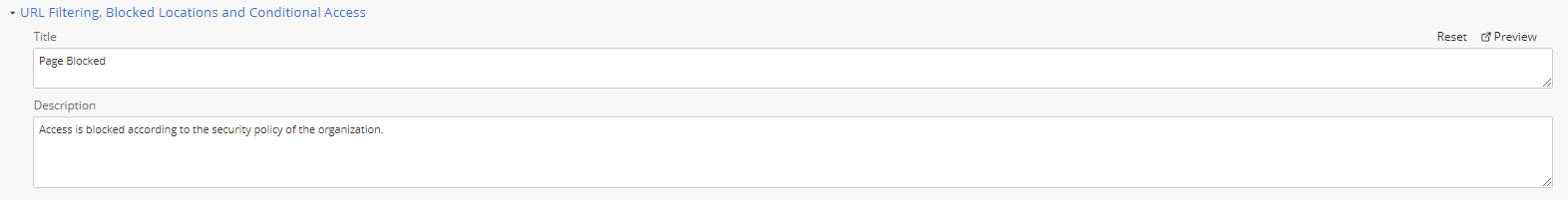
URL Filtering, Blocked Locations and Conditional Access
-
MiTM
-
File download blocked
-
In the Title field, enter the title for the block page.
-
In the Description field, enter the reason for blocking the page.
-
To preview the changes, click Preview.
-
To reset the values to default, click Reset.
-
-
To save the page text in the current language, in the Page texts section, click Save.
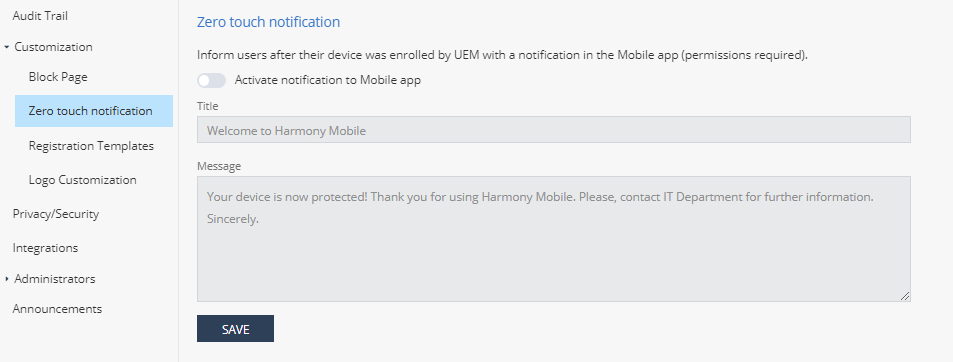
Zero Touch Notification
The Zero touch notification setting allows you to notify users when Harmony Mobile Protect App is automatically installed on their device.
|
|
Note - The system sends a Zero Touch notification only if the UEM |
To enable Zero touch notification:
-
Go to Settings > Customization > Zero touch notification.
-
Turn on the Activate notification to Mobile app toggle button.
-
If required, customize the text in Title and Message fields.
-
Click Save.
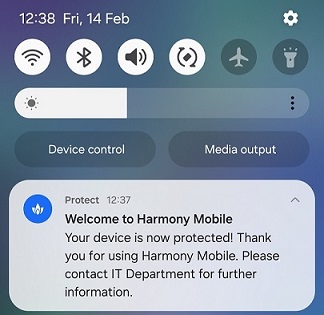
The system displays this message:
After the Harmony Mobile Protect App is installed and activated on the device, the user receives a notification from the Protect App.
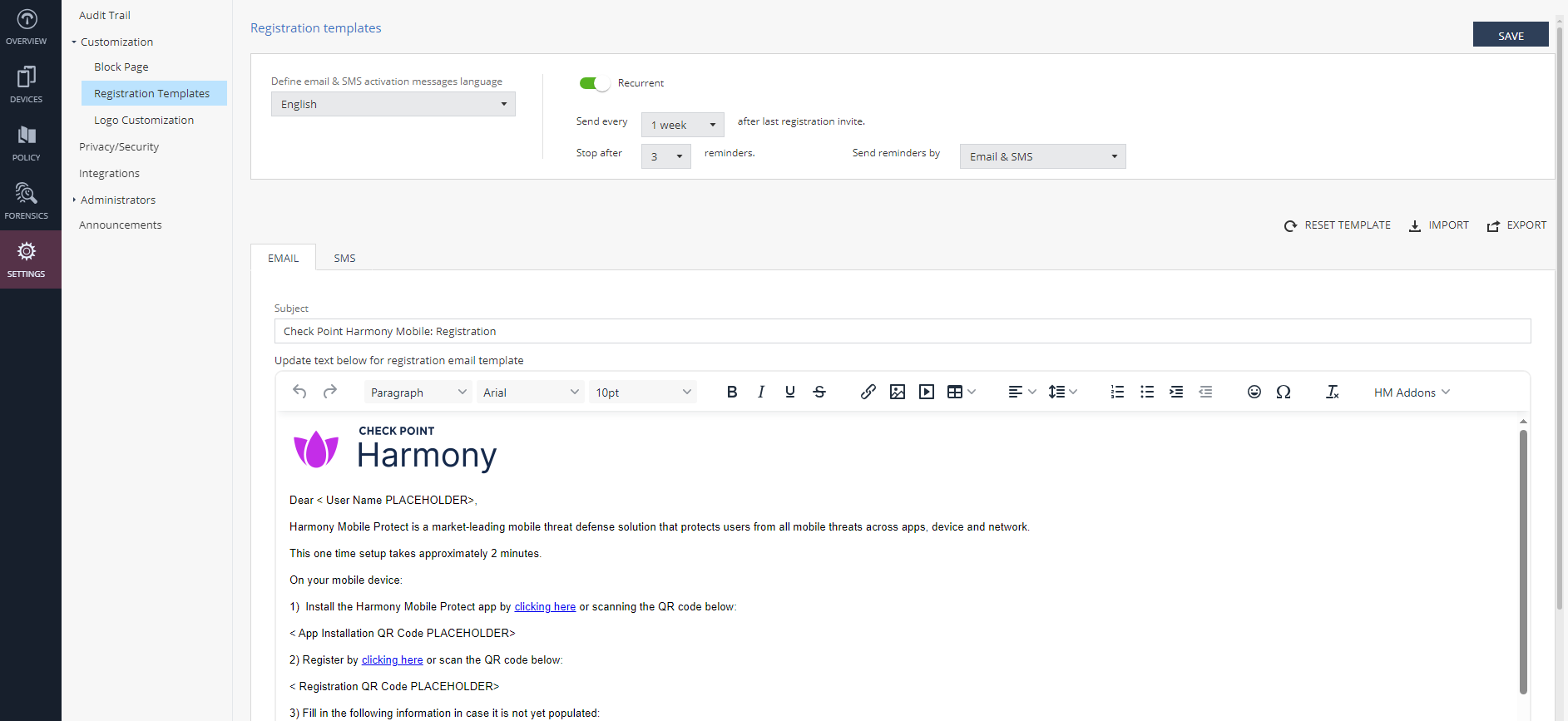
Registration Templates
Registration Templates allows you to customize the content of the registration email and SMS sent from the Infinity Portal to users when they register their mobile device to Harmony Mobile. This lets organizations to use their unique corporate message for device registration.
To configure the registration message templates, go to Settings > Customization > Registration Templates.
To change the default language of your email or SMS (English or Japanese), select the language from the list.
Sending Reminders for Device Registration
If users do not complete the Harmony Mobile registration on their devices, you can remind them by resending the registration invitation at specific intervals.
To send registration reminders to users:
-
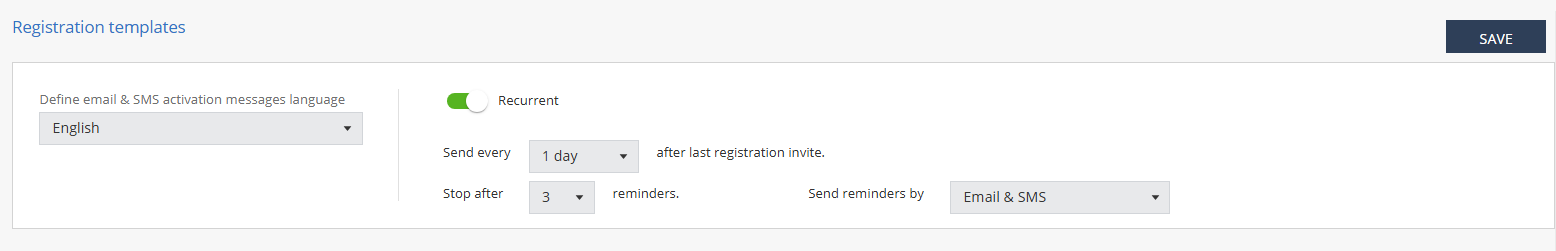
In the Registration templates section, turn on the Recurrent toggle button.
-
From the Send every list, select the frequency to send the registration invitation.
-
From the Stop after list, select the number of times the invitation should be sent (maximum of 10).
-
From the Send reminders by list, select the method to send the registration invitation.
-
Email & SMS
-
Email
-
SMS
-
-
Click Save.
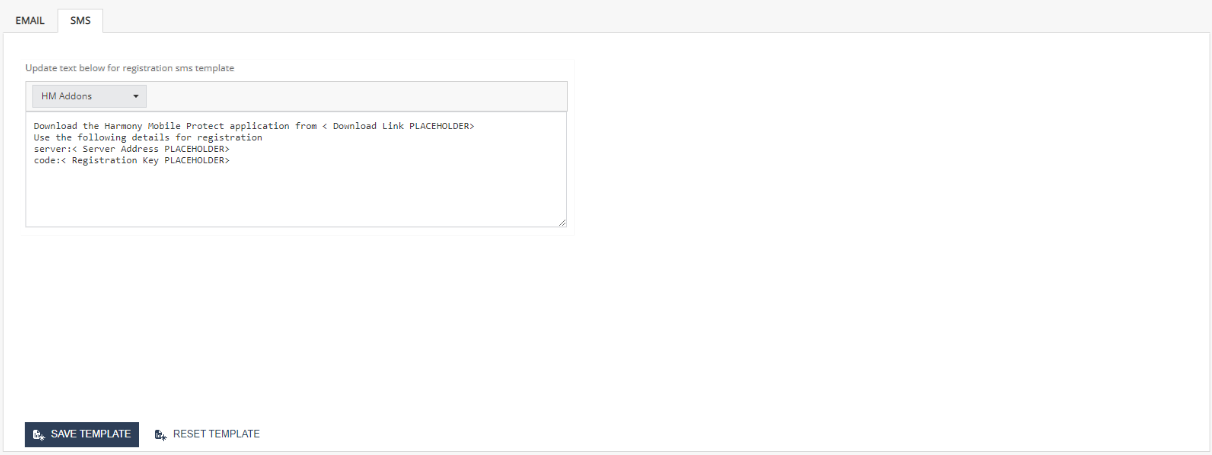
Configuring Email and SMS Templates
In the EMAIL and SMS tabs, you can view the default email and SMS templates. To customize the content, make the necessary changes and click Save.
To reset to the default template, click Reset Template.
You can also export and import the registration templates.
Email template example:
SMS template example:
Logo Customization
Go to Settings > Customization > Logo Customization to change the logo that appears in the upper left-hand corner of the Harmony Mobile Protect App on user devices.
Privacy/Security
Central HTTPS Inspection Root CA
You can generate a centralized root CA certificate for HTTPS inspection to use across all policies in your account. Once generated, you can upload the certificate to your UEM for deployment to end-user devices.
Prerequisite
To generate the centralized CA certificate, you must have one of these roles:
-
Admin role in Global Role
-
Admin or Super User role in Specific Service Roles
To generate a centralized root CA certificate:
-
Go to Settings > Privacy/Security.
-
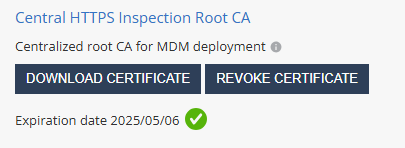
In the Central HTTPS Inspection Root CA section, click Generate Certificate.
-
Do one of these:
-
To generate a CA certificate issued by Check Point, click Generate CA Certificate.
The system generates a certificate valid for one year from the generation date, as shown in Expiration date.

Note - Check Point recommends you renew the CA certificate at least two weeks before the expiration date. To renew the CA certificate, see sk181288.
-
To use a self-signed or a third-party CA certificate, click Upload CA Certificate.
-
In the pop-up window, upload the certificate.

Note -
For the Transport Layer Security (TLS
 Transport Layer Security. A security protocol designed to facilitate privacy and data security for communications over the Internet.) certificate to be valid:
Transport Layer Security. A security protocol designed to facilitate privacy and data security for communications over the Internet.) certificate to be valid:-
The certificate must have a lifecycle of at least 30 days and not longer than 390 days.
-
The certificate must be valid for more than 30 days from the time it is uploaded to the Harmony Mobile Administrator Portal.
-
-
Enter the certificate password.
-
Click Verify.
-
If there are no errors, click Add.
-
-
-
If you have generated a CA certificate by Check Point, click Download Certificate.
The system downloads the certificate to your computer.

-
Upload the new certificate to the UEM.
For more information, see CA Certificate Deployment Using the UEM section for the relevant UEM in Harmony Mobile Integration Guide.
-
To revoke the certificate, click Revoke Certificate.

Important - Revoking the centralized certificate will remove it from all policies that use it.
To apply the centralized CA certificate to multiple policies in your tenant, go to HTTPS Settings in Network Protection settings.
BYOD Privacy Mode
When you enable BYOD Privacy Mode, administrators can only see that a malicious threat exists, but they cannot see the user affected by it. This ensures the highest user privacy when needed.
BYOD Privacy Mode Disabled:
When BYOD Privacy Mode is disabled, the Events & Alerts tab shows the Device Owner and Device Number fields as configured in the Devices tab.
BYOD Privacy Mode Enabled:
When BYOD Privacy Mode is enabled, the Events & Alerts tab does not show the Device Owner and Device ID Number field.
Example:
BYOD Privacy Mode Disabled:
When BYOD Privacy Mode is disabled, the Device Details show the app(s) that put this device at high risk.
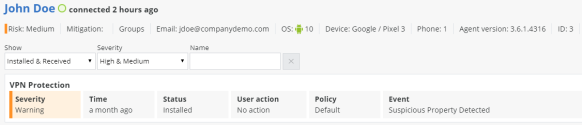
BYOD Privacy Mode Enabled:
When BYOD Privacy Mode is enabled, the Device Details does not show the app(s) that put this device at high risk. The administrator will only see that the device is at risk, and its risk level, but not the reason.
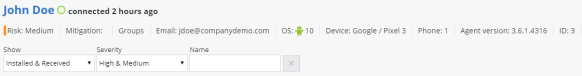
BYOD Privacy Mode Disabled:
When BYOD Privacy Mode is disabled, the drill-down into the App Analysis information about the App at Risk displays the app Owner Details.
BYOD Privacy Mode Enabled:
When BYOD Privacy Mode is enabled, the drill-down into the App Analysis information about the App at Risk does not display the app Owner Details.
Enable PII Decryption
Select this checkbox to enable the decryption of Personal Identifiable Information (PII) when you integrate with a Check Point Harmony Mobile Connector installed on-premises. For more information on Harmony Mobile Connector installation, see Harmony Mobile Connector Installation Guide.
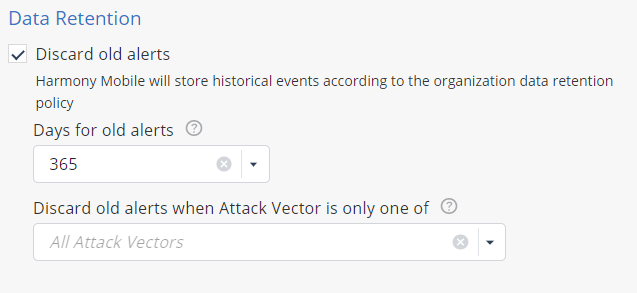
Data Retention
In this section, you can set the time period to discard old alerts. You can also configure it by attack vector.
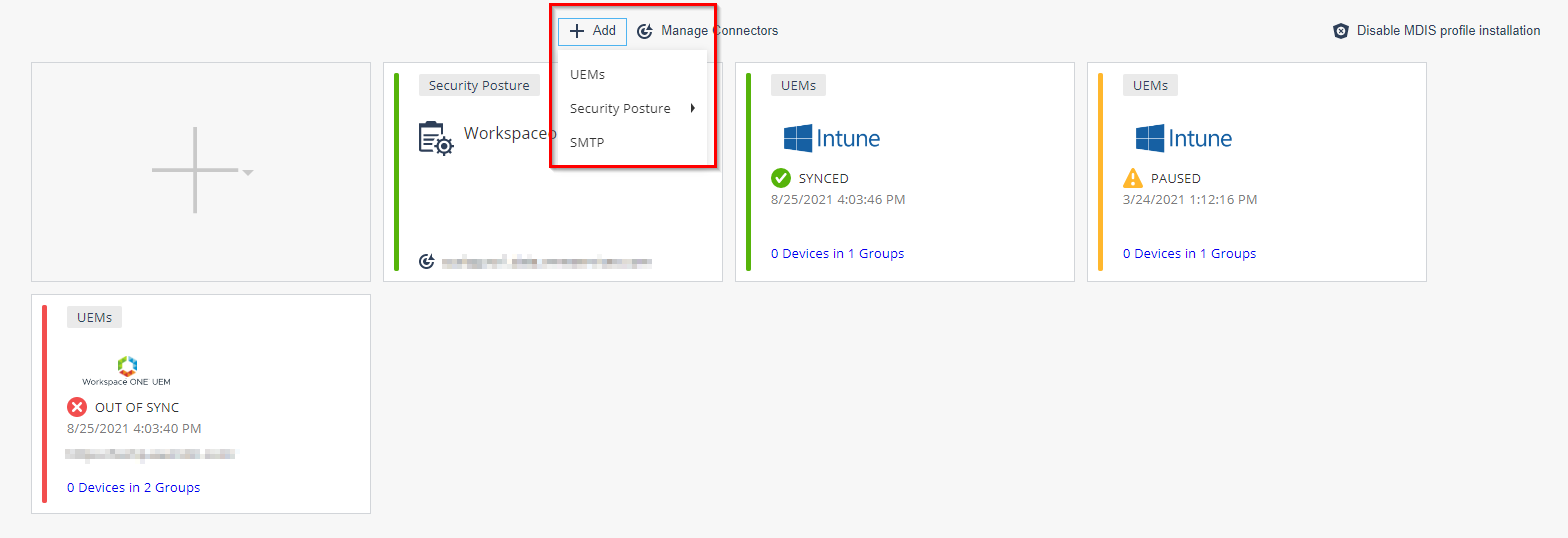
In the Integrations tab, you can manage your UEM integrations, other security posture systems such as Microsoft Defender ATP or Syslog, and SMTP servers. Harmony Mobile supports multiple integrations simultaneously. You can integrate Harmony Mobile to several UEMs in parallel, and to external security posture system such as Microsoft Defender ATP.
Click the +Add icon and choose to integrate Harmony Mobile with UEMs, with a Security Posture system, or with a SMTP server.
UEM Integration
|
|
Note - For more information on the integration procedure for different UEMs, see Harmony Mobile UEM Integration Guide. |
Select the UEMs option to integrate Harmony Mobile to any of the below supported UEMs or partner supported UEMs.
-
Workspace ONE (Formerly AirWatch UEM)
-
Microsoft Intune
-
MobileIron Core
-
IBM MaaS360
-
Citrix Endpoint Management (Formerly XenMobile)
-
MobileIron Cloud
-
BlackBerry UEM On-Premises
-
Jamf Pro
-
Google Cloud
-
Samsung Knox Manage / Samsung SDS EMM
 Enterprise Mobility Management. A set of tools and processes to secure and manage company-owned or employee-owned (BYOD) devices irrespective of their locations.
Enterprise Mobility Management. A set of tools and processes to secure and manage company-owned or employee-owned (BYOD) devices irrespective of their locations. -
SOTI MobiControl
Integration with Partner Supported UEMs
Partner supported UEMs are the UEMs that support integration with Harmony Mobile and tested by the partner.
The partner supported UEMs are:
-
mdport solution
-
SevenPrinciples (7P)
-
Essentials MDM
 Mobile Device Manager. A security software that enable organizations to implement policies that secure, monitor, and manage end-user mobile devices. (Techstep/FAMOC)
Mobile Device Manager. A security software that enable organizations to implement policies that secure, monitor, and manage end-user mobile devices. (Techstep/FAMOC) -
Hexnode
-
Scalefusion
-
Codeproof
For more information, see Integration with Partner Supported UEMs.
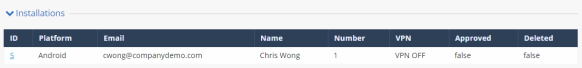
UEM Managed and Unmanaged Devices Management
Harmony Mobile supports managing UEM managed devices and unmanaged devices on the same dashboard. You can synchronize users and devices with an UEM and simultaneously manage the manually registered users and devices on the same Harmony Mobile dashboard.
-
Different device groups must be created for the ‘Non-UEM managed Devices’ and for the ‘UEM Managed’ devices.
-
Manually registered devices must be labeled as ‘Non-UEM managed Devices’. The UEM managed devices are synchronized to their relevant groups.
Mobile Device Integration Service (MDIS) Profile
Harmony Mobile's MDIS profile communicates with iOS devices that are not managed by a third-party UEM to retrieve the list of apps installed, certificates, profiles and so on. It is installed on the device with the Harmony Mobile Protect App.
|
|
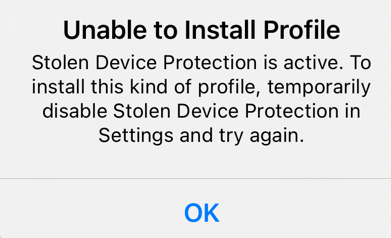
Note - For iOS 17.3 and higher, make sure to turn off Stolen Device Protection on the device before you install the Harmony Mobile Protect App. You can turn it on after you install the app. Otherwise, Unable to Install Profile error appears.
|
Security Posture Integration
The Security Posture option allows you to integrate Harmony Mobile to an external security posture and management system.
|
|
Note - The Workspace One Intelligence Hub integration requires configuring both Syslog to Intelligence Hub and Workspace One UEM. |
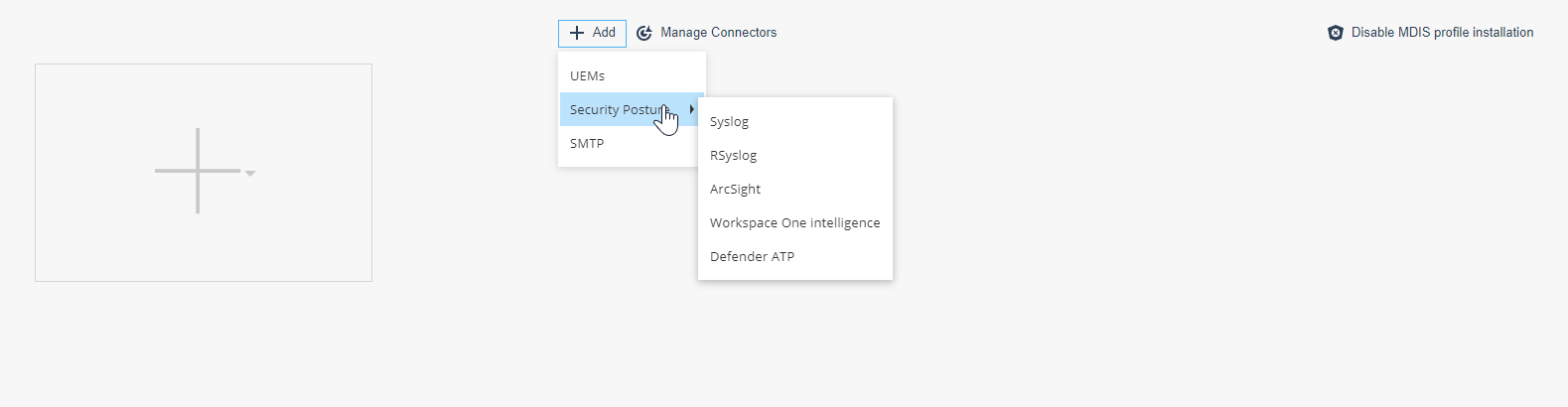
Syslog Integration
The administrator can set the dashboard to send Syslog events to a Syslog server. The Harmony Mobile dashboard must communicate to your Syslog server through your firewall.
To view the source IP addresses, see Appendix A - Harmony Mobile Communication Information.
To configure Syslog:
-
Go to Settings > Integrations and click +Add.
-
Click Security Posture > Syslog.
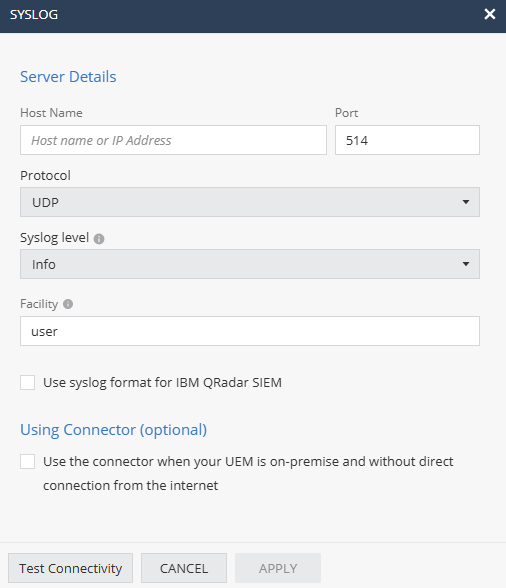
The Syslog window appears.
-
Enter these:
Setting
Description
Host Name
Host name or IP Address of Syslog server
Protocol
UDP or TCP
Port
Port that the Syslog server is listening on.
Syslog level
Severity level of events to be sent to the server. Events with the selected severity level or higher will be sent.
Supported values:
-
Info
-
Warn
-
Error
-
Debug
Facility
Type of program generating the log message. Messages from different facilities may be processed differently. Default value is user.
-
-
If you are using IBM QRadar SIEM, select the Use syslog format for IBM QRadar SIEM checkbox to format log messages according to QRadar's syslog requirements.
-
Click Apply.
For more information on the structure of the Syslog event sent by Harmony Mobile, see Appendix B - Harmony Mobile Syslogs.
Rsyslog Integration
Rsyslog is an open-source software utility used on UNIX and Unix-like computer systems for forwarding log messages in an IP network. It implements the basic syslog protocol, extends it with content-based filtering, rich filtering capabilities, flexible configuration options and adds features such as using TCP for transport and SSL![]() Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser.\TLS for encryption.
Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser.\TLS for encryption.
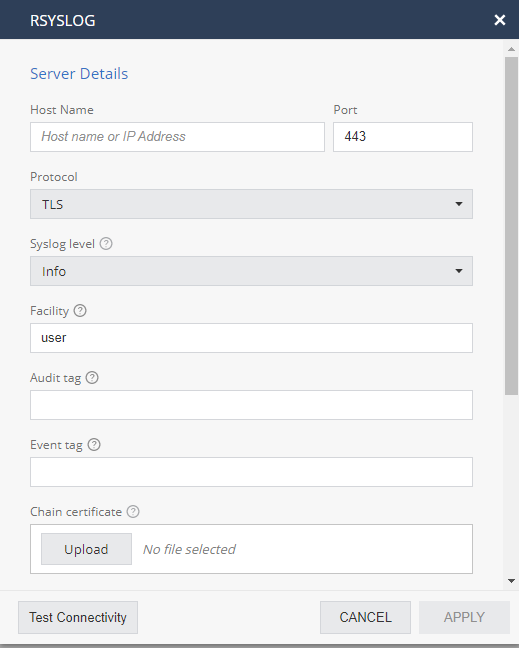
To configure Rsyslog:
-
In the pop-up window, enter these values:
Setting
Description
Host Name
Host name or IP Address of rsyslog server
Protocol
TLS
Port
Port that the rsyslog server is listening on.
Default SSL port: 443.
Syslog level
Severity level of events to send to the server.
Acceptable Values are:
-
Info
-
Warn
-
Error
-
Debug
Facility
Facility is used to specify the type of program that is logging the message. Messages with different facilities may be handled differently. Defaults to "user".
Audit TAG
Because Harmony Mobile can send 2 formats of logs, Event logs and Audit logs, the receiving rsyslog system publishes 2 parsers for these types.
When Harmony Mobile sends an Event type it will add the Event Tag to the message.
When Harmony Mobile sends an Audit type it will add the Audit Tag to the message.
Event TAG
Because Harmony Mobile can send 2 formats of logs, Event logs and Audit logs, the receiving rsyslog system publishes 2 parsers for these types.
When Harmony Mobile sends an Event type it will add the Event Tag to the message.
When Harmony Mobile sends an Audit type it will add the Audit Tag to the message.
Chain certificate
The rsyslog server needs to publish unique certificates to establish the secure connection from Harmony Mobile.
The chain certificate is the X.509 certificate used to secure the rsyslog server. The root CA of the rsyslog system to which we are going to send logs.
Certificate
The rsyslog server needs to publish unique certificates to establish the secure connection from Harmony Mobile.
This is the certificate used for the TLS handshake. It is obtained from the rsyslog system that was generated specifically for the integration with Harmony Mobile.
Key certificate
The rsyslog server needs to publish unique certificates to establish the secure connection from Harmony Mobile.
This the Private Key certificate used for the TLS handshake. It is obtained from the rsyslog system that was generated specifically for the integration with Harmony Mobile.
-
-
Click Apply.
ArcSight Integration
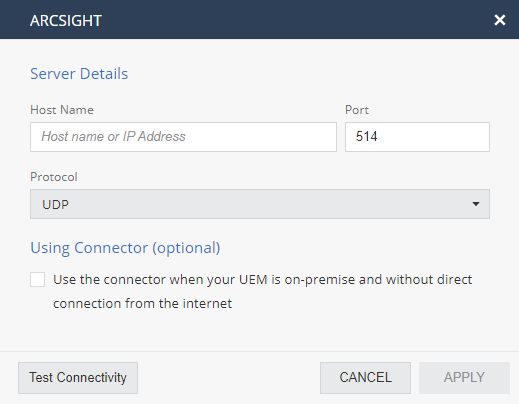
To configure ArcSight:
-
In the pop-up window, enter these values:
Setting
Description
Host Name
Host name or IP Address of ArcSight server
Protocol
UDP or TCP
Port
Port that the ArcSight server is listening on.
-
Click Apply.
For more information on the structure of the ArcSight event sent by Harmony Mobile, see Appendix C - Harmony Mobile ArcSight.
WorkSpace One Intelligence Integration
Harmony Mobile supports integration with VMWARE Workspace ONE Intelligence. When connected to Workspace ONE Intelligence, the Harmony Mobile sends the security event logs (syslog) messages. It allows security/SOC administrators to use other services that run over the Workspace ONE Intelligence. These additional services can use the advanced security indicators from the Harmony Mobile that come from the organization’s mobile devices and create additional reports and insights.
For more information on Workspace ONE Intelligence refer to VMWARE Workspace ONE Intelligence WEB site.
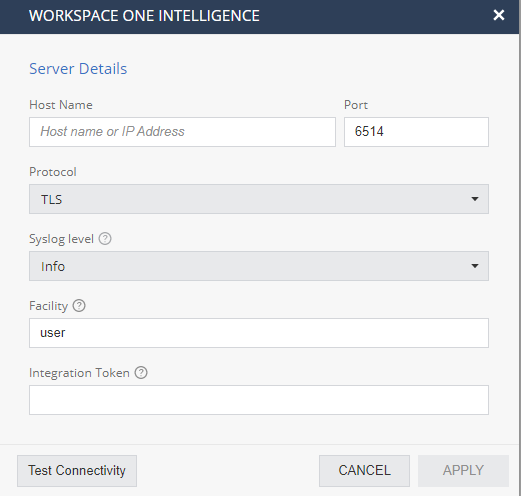
-
Before starting to integrate Workspace ONE Intelligence, Harmony Mobile must be first integrated with Workspace ONE UEM.
-
For more information on Harmony Mobile integration with Workspace ONE Intelligence, see Integration with Workspace ONE UEM.
-
On the Harmony Mobile Dashboard, go to ‘Settings/Syslog Settings’ and select the ‘Workspace ONE Intelligence’ option.
-
Harmony Mobile sends Syslog messages to the Workspace ONE Intelligence service. You must configure the Workspace ONE Intelligence service details and verify the two systems are connected
-
When the connection is established, you can view the Harmony Mobile threats insights on the Workspace ONE Intelligence dashboards and use the powerful Intelligence platform to automate the threats handling. For example, you can create a response to a new detected malware by sending a Slack message to the group of security analysts, or use a callback to any remote service that offers a web hook API.
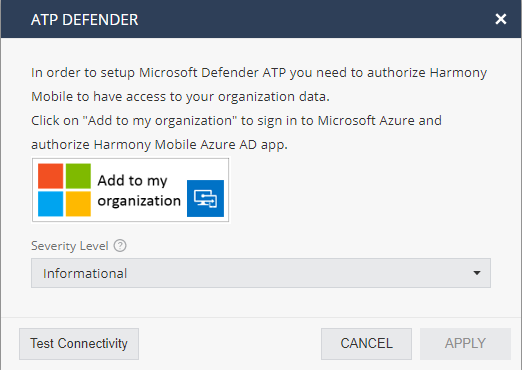
Microsoft Defender ATP Integration
Choosing to integrate with Microsoft Defender ATP, you will need to decide the minimum events severity to be sent to Microsoft Defender ATP and to log-in to your organization’s account of Microsoft Defender ATP. Once connected – Harmony Mobile sends all events to Microsoft Defender ATP, both security events and device activation events.
To learn more about integration with each of the 3rd party systems – please read the relevant integration guide.
To adjust the default settings implemented for their UEM, see the integration guides dedicated for each UEM.
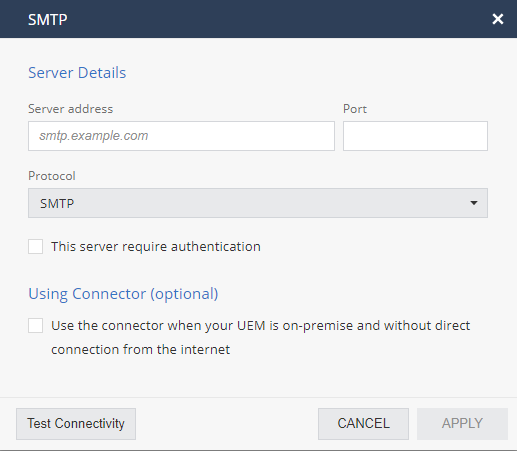
SMTP Integration
Go to Settings > Integrations > + > SMTP to configure the dashboard to send emails from the customer’s local domain instead of using the Harmony Mobile email server.
There are two transport settings: SMTP and SMTPS.
To configure SMTP Settings:
-
Click Add.
The SMTP Settings pop-up window appears.
 =
=
-
Select SMTP or SMTPS.
-
Enter the required information and click Save.
|
|
Note - You must configure the Firewall settings on the Enterprise’s firewall to allow SMTP or SMTPS from Harmony Mobile to the enterprise’s SMTP server. The allowed IP addresses are listed in Harmony Mobile Communication Information. |
SMS Sender Name
You cannot configure the SMS sender name. If you previously configured a sender name, the SMS card may still appear in your dashboard; however, it can no longer be edited. To reset it to a default value based on your local regulation, contact Check Point Support.
Administrators
Security Group Roles
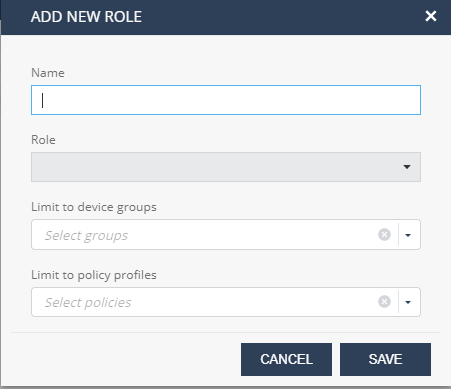
Security Group Roles allows you to add, remove, or edit Administrator roles.
To create security group roles restricted to specific groups and policy profiles, click +New and select:
-
Role Name
-
Role between Group Security Manager and Group Security Manager Viewer
-
Select the device groups the admin can access
-
Select the policy profiles the admin can access
This new role will be available under Specific Harmony Mobile roles when creating a new Admin User in the Infinity Portal (under Global Settings).
Other admin roles are available such as Basic Support or Device Administrator. For more information about these roles, go to Settings > Administrators > Roles Definitions.
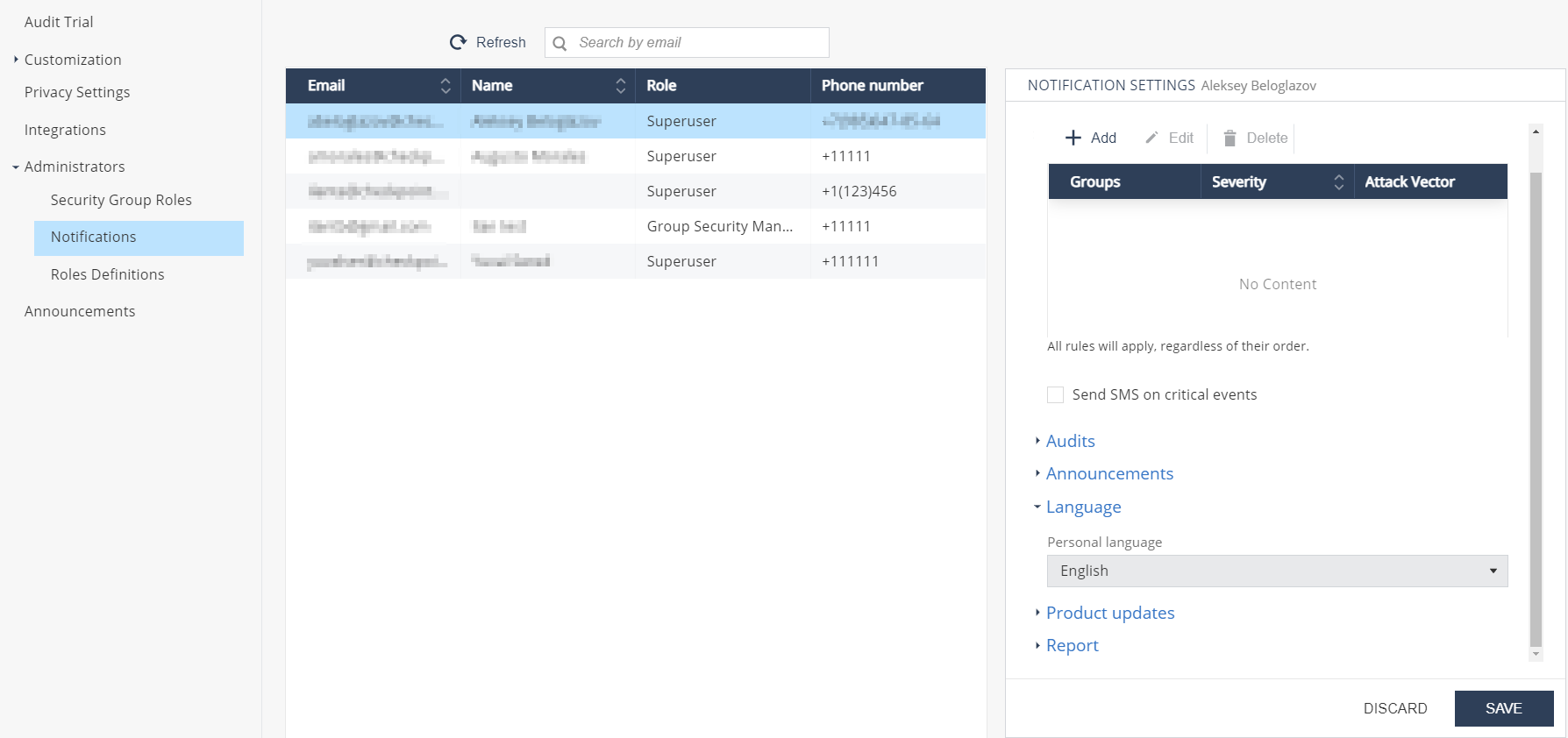
Notifications
In the Notifications tab, you can configure, how the administrator want to be alerted in case of security or audit events, dashboard announcements, product updates, scheduled mobile security reports and so on.
You can send Harmony Mobile notifications to a Microsoft Teams channel. For more information, see sk183491.
Scheduling Mobile Security Report
|
|
Note - You can also generate and download the Mobile Security report in PDF format whenever needed. To do that, go to Forensics > Events & Alerts and click PDF Report above the Events & Alerts table. For more information, see Generating the Mobile Security Report. |
To schedule a Mobile Security Report:
-
Go to Settings > Administrators.
-
Click Notifications.
The Notification Settings pane appears.
-
Expand Report.
-
Select the Send scheduled report checkbox.
-
From the Report type list, select one of these:
-
Full report
-
Operational report
-
-
Select the weekly or monthly option and set the day or date to generate the report.
-
From the Classification Level list, select the audience with whom you can share the report.

Note - The Classification Level does not impact the content of the generated report. It is for informational purpose only and is displayed in the PDF report.
-
Click Save.
The system generates the report at 00:00 UTC on the scheduled day and sends it through email to the administrator who set up the schedule.
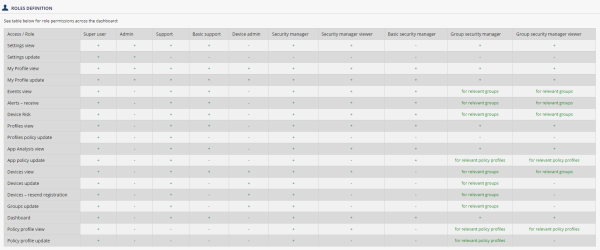
Roles Definitions
The Roles Definitions tab shows the different roles and their permissions in the Harmony Mobile Administrator Portal.
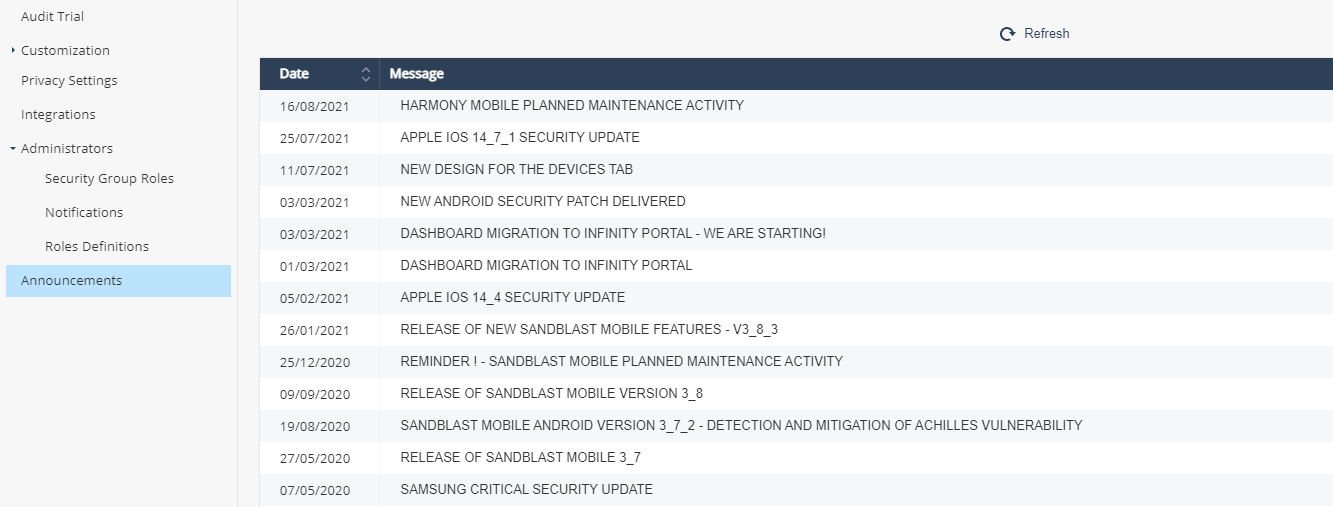
Announcements
Go to Settings > Announcements to view all system messages sent from Check Point.