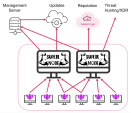
Installation and Deployment
Technical Prerequisites
-
Harmony Endpoint Management Platform service is registered and up:
Check Point Infinity Portal(Note the data residency selection - EU, US, UAE, and so on).
-
Proper EVAL licensing per the expected features are attached to the tenant (For example, Harmony Endpoint Elite includes Posture Management, DLP, and Infinity XDR/XPR).
-
Harmony Endpoint clients are deployed and communicating with the management portal. See Connectivity Requirements.
-
Anti-Malware
 A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. blade is enabled and updated for latest signatures.
A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. blade is enabled and updated for latest signatures.-
Third-party AV engines are completely disabled or uninstalled. Side-by-side installation of Endpoint Security Client Anti-Malware feature and any other third-party Anti-Virus
 Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. solution is not supported. For more details, see sk162735.
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. solution is not supported. For more details, see sk162735. -
On Windows workstations (laptops and desktops), deployment of Harmony Endpoint Security clients with Anti-Malware capability automatically sets Windows Defender to Passive or Disabled mode. See sk181318.
You can verify its status in Windows Security Center which should explicitly list Harmony Endpoint as the antivirus on the machine.
-
On Windows servers, it is mandatory to manually uninstall Windows Defender because they lack Windows Security Center Service (wscsvc). See sk159373.
-
-
The logs are generated and monitored through the Logs tab.
-
Browser extension is enabled and running on supported browsers (Microsoft Edge, Chrome, Firefox, Safari, Brave).
Connectivity Requirements
URLs and Ports
-
Outbound network connectivity between clients and the Endpoint Management tenant platform over port 443.
-
Clients should have uninterrupted Internet access per sk116590. Explicit allow rules and HTTPS decryption exclusions by destination FQDNs should be configured on the customer firewall and proxy.
-
To verify the connectivity, a connectivity test executable script is available on the client in this location:
C:\Program Files (x86)\CheckPoint\Endpoint Security\Endpoint Common\bin\CheckConnectivity.exe
Proxy, Semi-Isolated Environments and Super Nodes
If required, you can configure authenticated proxy under Client Settings policy > General settings. The customer can create a service account and specify its credentials in Harmony Endpoint policy.
A Super Node is a Windows machine running a specially configured Endpoint Security Client that also provides updates and client proxy services. It listens on port TCP/4434 and port TCP/3128 by default. Super Node is a light-weight proxy (based on NGNIX) that allows admins to reduce network bandwidth consumption and enable offline updates where only the Super Node needs connectivity to the management and update servers.
|
|
Note - Sizing recommendation: 4 CPU cores and 32GB of RAM per each 1000 concurrent client sessions. |
Platform-Specific Support and Exclusions
VDI and Terminal Servers
-
Persistent and Non-Persistent VDI (VMware, Citrix)
See Harmony Endpoint for Windows Virtual Desktop Infrastructure (VDI).
-
Terminal Servers (Microsoft, Citrix)
See Harmony Endpoint for Terminal Server / Remote Desktop Services.
Windows Servers
Rule base
Servers are more complicated endpoints than workstations and demand a different treatment. Create different rules for different server roles as in the following example:
There are separate rules for DCs, Exchange Servers, RAS and IAS servers, and so on.
|
|
Note - Do not apply a single policy to all servers. It may create unnecessary exclusions and unwanted performance reduction. |
-
Server Optimization
Each server role needs to be treated differently.Turn on server optimization and add the relevant role to optimize performance. See sk179816.
-
Most servers do not require Media Protection, Disk Encryption, and VPN client. The recommendation is to avoid installing those engines under Software Deployment policy.
-
Endpoint firewall can be deployed to implement micro-segmentation and to enable machine self-isolation. However, Endpoint firewall capability must not be deployed on Microsoft failover clusters. See sk169192.
-
You can safely disable browser protection (URLF, downloads protection, Zero Phishing
 Check Point Software Blade on a Security Gateway (R81.20 and higher) that provides real-time phishing prevention based on URLs. Acronym: ZPH.) on most servers (unless it is a terminal server used for Internet access by users).
Check Point Software Blade on a Security Gateway (R81.20 and higher) that provides real-time phishing prevention based on URLs. Acronym: ZPH.) on most servers (unless it is a terminal server used for Internet access by users).
-
-
Exclusions
Every zero-day product needs to have exclusions set for it to function properly.
-
Create exclusions based on real events in logs:
-
Right-click on a log you want to exclude.
-
Choose to create exclusion for all rules/effective rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..
-
-
In case of another security product running alongside with Harmony Endpoint (For example, third-party DLP, VPN clients), it is recommended to configure mutual exclusions.
-
Trusted third-party security software can be excluded from all supported capabilities by software developer certificate CN (see vendor executables properties).
-
Make exclusions in forensic monitoring with caution. Forensic monitoring exclusions help to reduce performance impact, but it also means that relevant process operations will not be recorded and will be missing in forensic reports and threat hunting.
-
Harmony Endpoint processes and infrastructure on Windows can be excluded by Check Point signer certificate CN (see Harmony Endpoint executables properties) and/or following directories:
-
C:\Program Files (x86)\CheckPoint\Endpoint Security\ -
C:\ProgramData\CheckPoint\Endpoint Security\ -
*:\HarmonyBackup\The * wildcard indicates that the system creates an Anti-Ransomware backup folder on all disk volumes and external media.
-
OS Support
For the list of features (blades) per OS for Harmony Endpoint, see sk169996.
Onboarding and Deployment
The deployment of Harmony Endpoint varies from different organization based on their license, specific needs, and hardware resources. There are various ways to install and distribute Harmony Endpoint.
POC (Pilot) Groups
Different environments have different needs. Therefore, Harmony Endpoint needs to be adjusted to the customer’s environment and be configured differently in each environment.
First, create a POC (pilot) group which is a pre-selected group of devices used for running the deployment. In the pilot group, we perform the customization and the fine-tuning. After everything is configured and adjusted to the environment, proceed to the next step.
The POC group should include one device of each department/user role (one device from R&D, Finance, IT, and so on). The reason is that Harmony Endpoint needs to be adjusted to all different behaviors. If we use only IT devices in the POC, Harmony Endpoint policy and exclusions will not be customized and adjusted for each department, potentially leading to avoidable issues.
However, Servers need to be treated differently than workstations. Therefore, put servers in their own designated POC groups by their server role (Exchange, DCs). It is recommended to start deploying Harmony Endpoint security clients in Test server farms before Production.
Order of Deployment

|
|
Note - AD scanner, Super Node and remote Deployment Agent roles can be combined on a pair of dedicated virtual machines operating 24/7 and serving other Harmony Endpoint clients protecting customer machines. |
Onboarding
There are two types of on-boarding groups:
-
The Staging/Pilot Groups should be used in the initial policies enforced on pilot machines.
-
The Entire Organization Group includes the rest of machines in the production environment.
The main idea is to test Harmony Endpoint on the devices of a certain behavior and adjust the products based on their behavior. Once it is ready, deploy it to the rest of the devices of the same behavior.
|
|
Note - Each server role requires its own pilot group and configuration policy, as each role has distinct behavior, the services it utilizes, and the access it requires. |
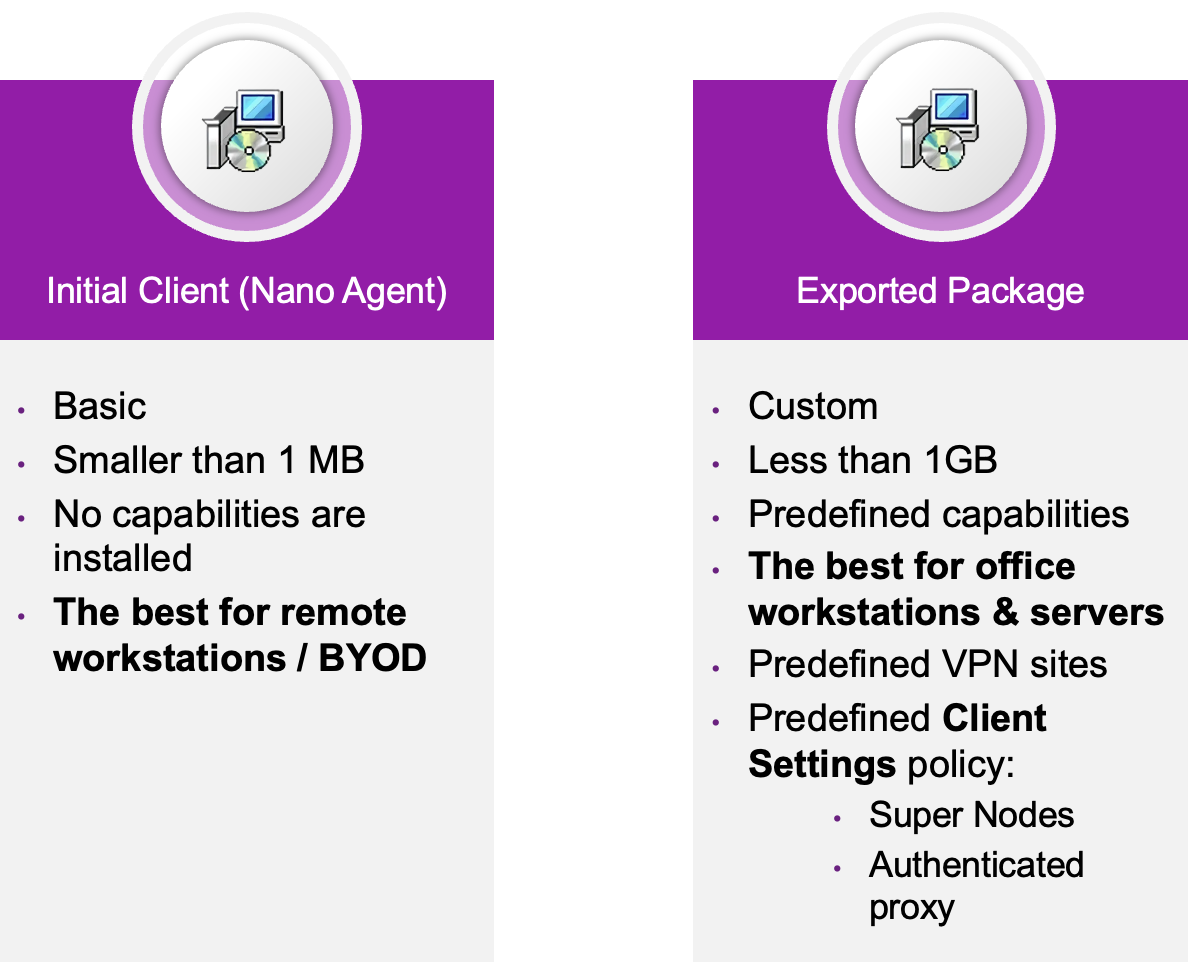
Deployment by Tiny Agent (aka Initial Client) vs Exported Package
There are two installation packages available:
-
Tiny Agent
-
Exported packages
|
|
Note - Both Tiny Agent and Exported packages support pre-assignment to Virtual Groups. |
It is a good add-on or alternative to AD/Entra-ID org. structure.
Creating empty virtual groups and their assignment to downloaded installation packages help to organize machine groups properly and use them in Threat Protection and Software Deployment policies.
If you have multiple virtual groups, you can export the same installation package multiple times while assigning it to different virtual groups.
Thus, once deployed, Harmony Endpoint clients will automatically join relevant pre-assigned virtual groups and start enforcing relevant policy rules.
Tiny Agent (aka Initial Client)
The installation file is lightweight (less than 1MB) and includes the initial client only (without the rest of the capabilities).
Once the client is installed and the connection to the management is established, the system downloads and installs the engines from the management to the client side.
Recommended for:
-
POC on several test machines.
-
Newly created and roaming workstations (desktops/laptops/BYOD).
Not recommended for:
-
Massive rollout in offices and datacenters. Opt for complete exported package to avoid excessive bandwidth consumption.
-
Sensitive/business-critical machines (servers, C-level devices, data centers).
-
Semi-isolated and air-gapped environments.
To download:
-
Go to Harmony Endpoint Administrator Portal and do one of these:
-
In the Overview tab, go to Unified Dashboard and click Download Endpoint.
-
Go to Policy > Software Deployment.
-
-
Click Download.
The following screen appears.
-
Choose one of these:
-
To download the initial client installation to this device
-
To copy a download link
-
To send installer link by email

Note - Choose the same version you are using in the Software Deployment section.
-
Full Exported Package
It is a customizable installation file of the agent. You can choose the capabilities to be included in the installation file. Unlike the initial package, it does not depend on network connectivity to be fully installed. The installation file is a few hundred megabytes in size.
Recommended for:
-
Massive rollout in offices and datacenters via GPO, SCCM, UEM (Microsoft Intune, VMware Workspace One, JAMF).
-
Sensitive/business-critical machines (servers, C-level devices, data centers).
-
Semi-isolated and air-gapped environments when Client Settings policy must be included into the installation package.
To download:
-
Go to Harmony Endpoint Administrator Portal.
-
Go to Policy > Export Package > Endpoint Client.
-
Click the + sign and start creating your own custom installation package.
-
Choose a name, OS and a version.

Note - Choose the same version as in the software deployment.
-
Choose the capabilities to be installed.
-
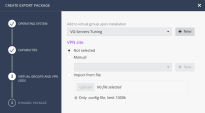
(Optional) Add a virtual group (recommended when AD/Entra-ID org. structure is not sufficient) and VPN sites (Check Point Quantum Gateway addresses).
-
Select the Minimize package size checkbox to minimize the installation package size by removing redundant components, include AV signatures.
-
Under General settings, disable the Endpoint Security Client
 Application installed on end-user computers to monitor security status and enforce security policies. user interface for unattended machines, such as ATMs. It saves some CPU and RAM on low-spec machines. See sk133174.
Application installed on end-user computers to monitor security status and enforce security policies. user interface for unattended machines, such as ATMs. It saves some CPU and RAM on low-spec machines. See sk133174. -
Under Dependencies settings, select the required components:
-
.NET Framework 4.8 Installer (111 MB) – Recommended for Windows 7 computers without .NET installed. Not required on modern Windows 10/11.
-
32-bit support (40MB) – Recommended for 32-bit computers.
-
Visual Studio Tools for Office Runtime 10.050903 (40 MB) – Only with Capsule Docs
 A component on Endpoint Security Windows clients. This component provides security classifications and lets organizations protect and share documents safely with various groups - internal and external..
A component on Endpoint Security Windows clients. This component provides security classifications and lets organizations protect and share documents safely with various groups - internal and external.. -
FDE Smart preboot (190MB) – Enables the Easy Unlock feature via One-Time Network Logon. Required only when FDE capability is deployed.
-
-
Under Anti-Malware settings, select the signatures to be included in the package.
-
Click Finish.
The installation file is now ready for use. Optionally, EXE can be converted to MSI.
AD and Entra-ID Integration
See Directory Scanner page in Harmony Endpoint EPMaaS Administration Guide.