Connecting Gateways and Clusters in Smart-1 Cloud
Connecting on-premises Security Gateway or CloudGuard Network Security Gateway
-
From the left navigation panel, click Gateways & Servers.
-
Click the New icon
 or a
or a  button and select Gateway....
button and select Gateway....The Check Point Gateway properties window opens.
-
Fill in the required fields for the Check Point Security Gateway:
-
Enter name - The name for the Security Gateway.
-
IP Address:
-
Automatic IPv4 address: Smart-1 Cloud assigns an internal IP address used for cloud communication over an outbound tunnel.
-
Custom IPv4 address: Assign a static IP address, except when configuring an SD-WAN Gateway.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-

Note - We recommend using a static IP address when available. This simplifies configuration for features such as UserCheck, NAT rules, and VPN configuration.
You can configure the Security Gateway object in Smart-1 Cloud to use a static IP address as its primary IP address. This configuration is similar to setting up a Security Gateway from an on-premises Security Management Server.
When the Security Gateway is configured with a Tunnel IP address, management traffic, control connections, and Smart-1 Cloud tenant communications use this main static IP address through the
maas_tunnelinterface.
Important - For a new CloudGuard Network (Public Cloud) deployment, configure the Security Gateway object in Smart-1 Cloud with a static IP address. Use the IP address from the Security Gateway's
eth0interface in the Custom IPv4 address field. -
-
-
In the Device section, click Connect.
The Connect Device window opens.
-
In the Security Gateway section, select Appliance/Open Server.
-
Connect to the CLI on the Security Gateway. In Clish, run the provided command to set the authentication token. The initial connection status is Pending connection. After the Security Gateway connects to Smart-1 Cloud, the status changes to Connected.
-
To establish Secure Internal Communication (SIC) between the Security Gateway and Smart-1 Cloud, enter the one-time password you set on the Security Gateway.
-
Click Next and wait until the Security Gateway connection process finishes. Then close the Connect Device window.
-
Click OK.
To connect an existing Security Gateway to Smart-1 Cloud:
-
After migration is complete, click Connect Gateways.
-
Go to Gateways & Servers, select the gateway you want to connect, and click Edit. The Check Point Gateway properties window opens.
-
In the Device section, click Connect.
-
In the Connect Device wizard window that opens, under Security Gateway, select Appliance/Open server.
-
Follow instructions in the wizard for Connecting your Gateway:
-
Open the CLI on the Security Gateway.
-
In Clish, run the command shown in the wizard to set the authentication token.
The gateway status initially shows Pending connection. When the gateway connects successfully to Smart-1 Cloud, the status changes to Connected.
-
Click Next.
-
-
Publish the changes.
To connect an existing Security Gateway object with a Tunnel IP address:
If you have an existing Security Gateway, follow these steps to change it to a static IP address:
-
Edit the Security Gateway object in SmartConsole:
|
|
Important - To regenerate the token, follow these steps: |
Connecting a Cluster
-
From the left navigation panel, click Gateways & Servers.
-
Click the New icon
 or a
or a  button and select Cluster....
button and select Cluster....The Check Point Cluster window opens.

Note - Web SmartConsole supports configuration of a Security Gateway/Cluster object for Gaia OS versions R80.10 and higher.
-
Fill in the required fields:
-
Enter Name: The Cluster name.
-
IP address: The Cluster VIP IP address.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-
-
-
Click Add... next to Member ID 1.
The Check Point Cluster Member window opens.
-
Enter the name and IP address of Member ID 1:
- Automatic IPv4 address: Smart-1 Cloud assigns an internal IP address used for cloud communication over an outbound tunnel.
-
Custom IPv4 address: Assign a static IP address, except when configuring an SD-WAN Gateway.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-
-
Click Connect in the Secure Internal Communication section.
The Connect Device window opens.
-
In the Security Gateway section, select the Cluster Gateway type.
-
Follow the on-screen instructions to connect the Cluster member to the Smart-1 Cloud management.
-
When the Connection Status changes to Connected, click Next.
-
To establish Secure Internal Communication (SIC) between the Cluster member and Smart-1 Cloud, enter the one-time password you set on the Cluster member.
-
Click Next and wait until the Cluster member connection process finishes. Then close the Connect Device window.
-
-
Click Add... next to Member ID 2.
Follow steps 4.a-4.g again for this member.
-
Navigate to the Network Management tab.
-
Click Get Interfaces > Get Interfaces With Topology.
-
Click the MaaS Tunnel interface, and in General > Network Type section, select Private.
-
On the same MaaS Tunnel settings page, in Advanced > Monitoring section, make sure the Monitored Interface checkbox is cleared.
-
Finalize the topology definitions for the cluster.
-
Install the policy.
-
From the left navigation panel, click Gateways & Servers.
-
Click the New icon
 or a
or a  button and select Cluster....
button and select Cluster....The Check Point Cluster window opens.

Note - Web SmartConsole supports configuration of a Security Gateway/Cluster object for Gaia OS versions R80.10 and higher.
-
Fill in the required fields:
-
Enter Name: The Cluster name.
-
IP address: The Cluster VIP IP address.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-
-
-
Click Add... next to Member ID 1.
The Check Point Cluster Member window opens.
-
Enter the name and IP address of Member ID 1:
- Automatic IPv4 address: Smart-1 Cloud assigns an internal IP address used for cloud communication over an outbound tunnel.
-
Custom IPv4 address: Assign a static IP address, except when configuring an SD-WAN Gateway.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-
-
Click Connect below the Secure Internal Communication.
The Connect Device window opens.
-
Select Appliance/Open Server in the Cluster Gateway type.
-
Copy the Token from the Connect Device screen.
-
-
Click Add... next to Member ID 2.
Follow steps 4.a-4.d again for this member.
-
In the Security Cluster deployment template:
-
Paste the Tokens you copied from the Smart-1 Cloud portal for each member into the appropriate fields.
-
Fill in all remaining fields in the template and start the deployment.
-
When the CloudGuard Network Security Gateway deployment completes:
-
A tunnel is established between the Security Gateway and the Smart-1 Cloud.
-
The status of the Security Gateway changes to Pending trust (SIC) establishment.
-
-
-
In SmartConsole or Streamed SmartConsole:
Follow the administration guide specific to your deployed solution to configure the Cluster object and Cluster members in SmartConsole.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x

Note - When you add cluster members to the cluster object, use the existing members created in step 1.
-
This step is required after the cluster's migration to Smart-1 Cloud. For more information, see Migrate.
-
After migration is complete, click Connect Gateways.
-
Go to Gateways & Servers, select the gateway you want to connect, and click Edit.
-
In the Device section, click Connect.
-
In the Connect Device wizard window that opens, under Security Gateway, select Appliance/Open server.
-
Follow instructions in the wizard for Connecting your Gateway:
-
Open the CLI on the Security Gateway.
-
In Clish, run the command shown in the wizard to set the authentication token.
The gateway status initially shows Pending connection. When the gateway connects successfully to Smart-1 Cloud, the status changes to Connected.
-
Click Next.
-
-
Publish the changes.
Onboarding a new Quantum appliance using Zero Touch deployment
Follow these steps to deploy a new appliance in Zero Touch mode and configure it as a Security Gateway or Cluster Member.
-
Remove your new appliance from the shipping carton, connect the power cable, and turn on the appliance.
-
Wait for the light on one of the network interface ports to start blinking, then:
-
If you have a DHCP server:
Connect the network cable to the blinking interface port.
Make sure this connection leads to the environment with a working DHCP server.
-
If you do not have a DHCP server:
Configure an interface with the appropriate networking settings:
-
Connect to the command line on the appliance.
-
In Expert mode, disable Zero Touch DHCP:
/opt/CPzetc/bin/zetc_setlaunch 0 -
In Gaia Clish, configure the IP address:
set interface <Name of Interface> onset interface <Name of Interface> ipv4-address <IPv4 Address> mask-length <Subnet Mask Length> -
In Gaia Clish, configure the default route:
set static-route default nexthop gateway address 192.168.1.254 offset static-route default nexthop gateway address <IPv4 Address> on -
In Gaia Clish, configure DNS servers:
set dns primary <IPv4 Address>set dns secondary <IPv4 Address>set dns tertiary <IPv4 Address> -
In Gaia Clish, save the configuration:
save config -
Plug the network cable into the configured interface port.
-
-
-
Go to the Connect Gateways page in the Smart-1 Cloud portal.
-
Wait for your appliance to appear (this typically takes 2-3 minutes).

Note - If your appliance does not appear, check the Service and Contract page.
-
Click on your appliance's card, enter the required information, and click OK.
To replace an existing Security Gateway, click the arrow next to the Configure Device button.
-
Follow the on-screen instructions in the portal.
-
After the card status changes to Registration completed, you can configure your new Security Gateway in SmartConsole.
Connecting a Quantum Spark Appliance
To connect Quantum Spark appliance to Smart-1 Cloud, follow these steps:
-
From the left navigation panel, click Gateways & Servers.
-
Click the New icon
 or a
or a  button and select Gateway... or Cluster....
button and select Gateway... or Cluster....The Check Point Gateway properties window opens.
-
Fill in the required fields for the Check Point Security Gateway:
-
Enter name - The name for the Security Gateway.
-
IP Address
- Automatic IPv4 address: Smart-1 Cloud assigns an internal IP address used for cloud communication over an outbound tunnel.
-
Custom IPv4 address: Assign a static IP address, except when configuring an SD-WAN Gateway.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x

Note - We recommend using a static IP address when available. This simplifies configuration for features such as UserCheck, NAT rules, and VPN configuration.
You can configure the Security Gateway object in Smart-1 Cloud with a static IP address as the primary IP address. This configuration is similar to setting up a Security Gateway from a self-hosted Security Management Server.
When the Security Gateway is configured with a Tunnel IP address, management traffic, control connections, and Smart-1 Cloud tenant communications use this main static IP address through the
maas_tunnelinterface.
-
-
Click Connect in the Device field.
The Connect Device window opens.
-
In the Security Gateway section, select Quantum Spark.
-
In the Connection preference section, select "Prepare the object now, connect the Security Gateway later". Click Next.
-
To establish trust between the Security Gateway and Smart-1 Cloud, configure the one-time password and enter it later on the Security Gateway. Click Next
-
Copy the authentication token to paste it later in the Security Management Server setup. Then close the Connect Device window.
-
Click OK.
-
Connect to the Quantum Spark WebUI, navigate to the Security Management tab, and click Setup.
-
Select the Use Security Management service checkbox and click Next.
-
Click Use the Infinity Portal to generate a new authentication token and paste the token. Click Connect.
-
Wait for the status to change to Connected successfully to the Security Management Server, then click Next.
-
Set the one-time password and click Next:

Important - Do not select the Initiate trusted communication without authentication option. Connecting an SMB device to Smart-1 Cloud without using the SIC password is not supported.
-
Check Connect to the Security Management Server now and click Connect.

Note - This message appears:
Security Policy Installation: Trust is established with the Security Management Server. However, unable to fetch the Security Policy from the Management Server
After the trust is established, you can continue with the process.
-
Click Finish.
-
Connect to the Smart-1 Cloud WebUI.
-
In Gateways & Servers, double-click the Quantum Spark device that was configured earlier. The device properties window opens.
-
Under Network Management, select General.
-
In the Interfaces menu, select Get Interfaces with Topology.
-
Once it is done, publish the changes and install the policy.
To connect a Quantum Spark Cluster appliance to Smart-1 Cloud, follow these steps:
1. Open Web SmartConsole.
2. From the left navigation panel, click Gateways & Servers.
3. Click the New icon![]() and select Cluster....
and select Cluster....
4. The Check Point Cluster window opens.
|
|
Note - The Web SmartConsole supports configuration of Security Gateway/Cluster objects on Gaia OS versions R80.10 and higher. |
-
Enter these details:
-
Name: Cluster name.
-
IP Address: Cluster Virtual IP (VIP) address.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-
-
-
Click Add... next to Member ID 1.
-
In the Check Point Cluster Member window, enter the name and IP address of Member ID 1.
- Automatic IPv4 address: Smart-1 Cloud assigns an internal IP address used for cloud communication over an outbound tunnel.
-
Custom IPv4 address: Assign a static IP address, except when configuring an SD-WAN Gateway.

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-
-
Click Connect in the Secure Internal Communication section.
The Connect Device window opens.
-
In the Security Gateway section, select Quantum Spark.
-
Save the Security Management Token displayed for the next step.
-
On Quantum Spark WebUI (Member 1):
-
Navigate to the Security Management tab.
-
Click Setup.
-
-
Select Use Security Management Services.
-
Paste the token you saved in Step 3 and click Connect.
-
Wait for the message of a successful connection and click Next.
-
Set a one-time password and click Next.
-
Select Connect to the Security Management Server Later and click Finish.
-
Back in Web SmartConsole:
-
Confirm that connection status is Connected.
-
Click Next and then OK.
-
-
Click Add... next to Member ID 2.
-
In the Check Point Cluster Member window, enter the name and IP address of Member 2.
- Automatic IPv4 address: Smart-1 Cloud assigns an internal IP address used for cloud communication over an outbound tunnel.
-
Custom IPv4 address: Assign a static IP address, except when configuring an SD-WAN Gateway.
-
Under Secure Internal Communication, click Connect.
-
In the Connect Device window:
-
Under Security Gateway, select Quantum Spark.
-
Save the token shown.
-
-
On Quantum Spark WebUI (Member 2):
-
Navigate to the Security Management tab.
-
Click Setup.
-
-
Select Use Security Management Services.
-
Paste the token you saved in Step 5 and click Connect.
-
Wait for the message of a successful connection and click Next.
-
Set a one-time password as for Member 1 and click Next.
-
Select Connect to the Security Management Server Later and click Finish.
-
In Web SmartConsole, verify that connection status is Connected.
-
Click Next and then OK.
-
Open a desktop version of SmartConsole.
-
Open the Cluster Object created earlier.
-
Under Cluster Members:
-
Select Member 1, click Communication, and enter the one-time password set earlier in Step 4.
-
Repeat for Member 2.
-
-
Go to the Topology section:
-
Click Edit Topology.
-
Click GET to fetch all interfaces and topology for both members.
-
-
Define the first Sync interface, then click OK.
-
Publish the changes.
Connecting an SMB Cluster
To connect an existing SMB Cluster to Smart-1 Cloud after its migration, follow these steps:
-
In Smart-1 Cloud, go to Gateways & Servers, select the cluster you want to connect, and click Edit.
-
The Check Point Cluster window opens with the existing cluster configuration.
-
In the Device section, edit the existing cluster members.
-
From the Options menu, select the member name and click Edit Member.
-
In the Check Point Cluster Member window, in the Secure Internal Communication section, click Connect.
-
In the Connect Device wizard window that opens, under Security Gateway, select Quantum Spark.
-
Copy the token and save it separately.
-
Follow the on-screen instructions to configure the Quantum Spark Gateway.
-
Connect to your Quantum Spark Appliance WebUI.
-
Open Home > Security Management page.
-
Under Security Management Server, click Advanced and then click Reinitialize Trusted Communication. A warning message appears.
-
Click Yes.
-
Click Setup. The Security Management Server Configuration Wizard opens.
-
Select Use Security Management Service and then click Next.
-
Below Authentication Token, paste the token you saved in Step 2-4 and click Connect.
-
When the status changes to Connected, click Next.
-
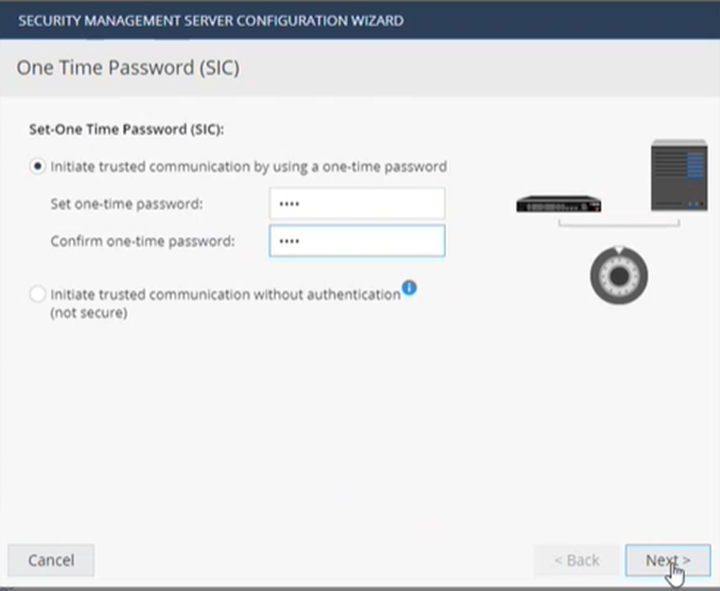
Create a one-time password (SIC):
-
Select Initiate trusted communication by using a one-time password.
-
Enter the password.
-
Confirm the password.
-
Click Next.
-
- Select Connect to the Security Management Server later and click Finish.
-
Get back to the Connect Device wizard in Smart-1 Cloud and wait until the connection status changes to Connected.
-
Click Next
-
Read the message and click Close.
-
In the Check Point Cluster Member window, click OK.
The preliminary configuration of the Member 1 is completed.
-
Repeat steps 2, 3, and 4 for Member 2 - Edit Member, Configure Quantum Spark Gateway, and Connect Member.
-
Make sure the preliminary configuration of the Member 2 is completed the same way as for Member 1.
-
Open Web SmartConsole.
-
Edit the SMB Cluster created earlier.
-
In the Gateway Cluster Properties window, select Cluster Members:
-
Select Member 1, click Edit and click then Communication. The Communication window opens with password details disabled.
-
Click Reset and then Yes to confirm.
-
Enter the one-time password set earlier for Member 1.
-
Click Initialize.
-
When Trust state changes to Trust established, click Close.
-
-
Repeat the previous step for Member 2.
-
Go to the Topology section:
-
Click Edit Topology.
-
Click GET and select All Members' Interfaces with Topology to fetch all interfaces and topology for both members.
-
Click Yes to confirm.
-
-
Make sure both interfaces are synchronized and click OK.
-
Publish and install the policy to complete the setup.
To verify the results, make sure the connection is established on your Quantum Spark Appliance.
-
In your Quantum Spark Appliance WebUI, open Home > Security Management page.
-
Under Security Policy, click Fetch Policy.
-
A confirmation message appears when the application fetches the policy.
Connecting a Maestro Security Group
|
|
Important - This procedure supports only Maestro Security Groups that run R81.10 and higher versions. |
Prerequisite
Install the required hotfixes on the Security Group Member before you add it to the Security Group that connects to Smart-1 Cloud. Make sure the maas_tunnel is active.
-
Smart-1 Cloud does not support Maestro Security Groups in the VSX mode.
-
The SMO Image Cloning is not supported if the Security Group R81.10 and higher contains different appliance models.
-
DAIP is not supported.
-
Automatic IP not supported with Maestro Security Group.
-
On the Maestro Orchestrator, configure the required Security Group - in Gaia Portal or Gaia Clish.
See the Quantum Maestro Getting Started Guide and the Maestro Administration Guide for your version.

Important - Write down the IP address of the Security Group. You must configure it later in Smart-1 Cloud.
-
Install the required Hotfixes on the Security Group: For details, refer to sk181495.
-
Connect to the Smart-1 Cloud Portal.
-
Add the Security Group as a new Security Gateway object:
From the left navigation panel, click Gateways & Servers.
-
Click the New icon
 and select Gateway.
and select Gateway.The Check Point Gateway properties window opens.
-
Fill in the required fields for the Check Point Security Gateway:
-
Enter name - The name for the Security Gateway.
-
IP Address - In the IP address field, enter the IP address of the Security Group as you configured it on the Maestro Orchestrator (this is the IP address assigned to the Mgmt interface of the Security Group).

Important - Do not use an IP address from the following subnets for the Cluster Virtual IP or Custom IPv4 address:
-
100.64.x.x
-
100.70.x.x
-
100.71.x.x
-
100.100.x.x
-
100.101.x.x
-
-
-
Click Connect in the Device field.
The Connect Device window opens.
-
In the Security Gateway type drop-down menu, select Appliance/Open Server.
-
Follow the on-screen instructions to connect your Security Group. The connection status is Pending connection, and when the Security Group connects to Smart-1 Cloud, the status changes to Connected.
-
-
Click Next to close the Connect Device window.
-
Click OK.
Using Clish Commands
-
Connect to the command line interface of the Security Group.
-
Run:
-
In Gaia gClish:
show security-gateway cloud-mgmt-service -
In the Expert mode:
maas status
-
-
Connect to the CLI on the Security Group.
-
Run:
-
In Gaia gClish:
set security-gateway cloud-mgmt-service off -
In the Expert mode:
maas off
-
-
Connect to the CLI on the Security Group.
-
Run:
-
In Gaia gClish:
set security-gateway cloud-mgmt-service on -
In the Expert mode:
maas on
-