Microsoft Teams
Overview
Microsoft Teams is a communication platform developed by Microsoft as part of the Microsoft 365 family of products. It offers employees and external collaborators to chat, meet online, and share files. Harmony Email & Collaboration adds security, privacy, and compliance to Microsoft Teams by scanning messages and files shared on a chat or a team for malicious content and data loss prevention (DLP) and generates actionable events on malicious content.
Harmony Email & Collaboration scans the messages and files shared through direct messaging or a team.
How it works
Harmony Email & Collaboration adds a layer of security that provides these security features for Microsoft Teams:
-
Data Leak Prevention (DLP): Protecting sensitive text messages and files
-
Anti-Malware: Scanning of files for malicious content
-
URL Reputation: Blocking malicious links within files and messages
-
User Behavior Anomaly: Identifying suspicious login and compromised accounts
-
Remediation: Tombstoning malicious files or sensitive files and messages
Required Permissions
Harmony Email & Collaboration requires these permissions to protect Microsoft Teams.
|
|
Note - All these permissions are required to access your data in the Harmony Email & Collaboration Administrator Portal. |
|
Permissions required from Microsoft |
Functions performed by Harmony Email & Collaboration |
|---|---|
|
Send channel messages |
Allows an app to send channel messages in Microsoft Teams on behalf of the signed-in user. |
|
Sign in and read user profile |
Allows users to sign in to the app and allows the app to read the profile of signed-in users. It also allows the app to read basic company information of signed-in users. |
|
Read domains |
Allows the app to read all domain properties without a signed-in user. |
|
Read and write tabs in Microsoft Teams |
Read and write tabs in any team in Microsoft Teams without a signed-in user. This does not give access to the content inside the tabs. |
|
Read tabs in Microsoft Teams |
Read the names and settings of tabs inside any team in Microsoft Teams without a signed-in user. This does not give access to the content inside the tabs. |
|
Read and write all group memberships |
Allows the app to list groups, read basic properties, read and update the membership of the groups this app has access to without a signed-in user. Group properties and owners cannot be updated, and groups cannot be deleted. |
|
Read all group messages |
Allows the app to read memberships and basic group properties for all groups without a signed-in user. |
|
Manage all users' Teams apps |
Allows the app to read, install, upgrade, and uninstall Teams apps for any user without a signed-in user. It does not give the ability to read or write application-specific settings. |
|
Read all users' installed Teams app |
Allows the app to read the Teams apps that are installed for any user without a signed-in user. It does not give the ability to read application-specific settings. |
|
Read all users' teamwork activity feed |
Allows the app to read all users' teamwork activity feed without a signed-in user. |
|
Read directory data |
Allows the app to read data in your organization's directory, such as users, groups, and apps, without a signed-in user. |
|
Read and write all groups |
Allows the app to create groups, read all group properties and memberships, update group properties and memberships, and delete groups. Also allows the app to read and write group calendar and conversations. All of these operations can be performed by the app without a signed-in user. |
|
Read all groups |
Allows the app to read group properties and memberships, and read the calendar and conversations for all groups, without a signed-in user. |
|
Flag channel messages for violating policy |
Allows the app to update Microsoft Teams channel messages by patching a set of Data Loss Prevention (DLP) policy violation properties to handle the output of DLP processing. |
|
Read all channel messages |
Allows the app to read all channel messages in Microsoft Teams. |
|
Read all chat messages |
Allows the app to read all 1-to-1 or group chat messages in Microsoft Teams. |
|
Flag chat messages for violating policy |
Allows the app to update Microsoft Teams 1-to-1 or group chat messages by patching a set of Data Loss Prevention (DLP) policy violation properties to handle the output of DLP processing. |
|
Read all users' full profiles |
Allows the app to read user profiles without a signed-in user. |
|
Read files in all site collections |
Allows the app to read all files in all site collections without a signed-in user. |
|
Read and write all chat messages |
Allows an app to read and write all chat messages in Microsoft Teams without a signed-in user. |
|
Read items in all site collections |
Allows the app to read documents and list items in all site collections without a signed-in user. |
|
Read all hidden memberships |
Allows the app to read the memberships of hidden groups and administrative units without a signed-in user. |
Activating Microsoft Teams
For details about the procedure to activate Microsoft Teams, see Activating Microsoft Teams.
Deactivating Microsoft Teams
To deactivate Microsoft Teams:
Microsoft Teams Security Settings
Customizing Tombstone Messages
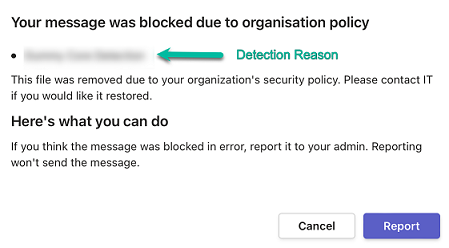
If a message/file is tombstoned, a tombstone message will appear instead of the tombstoned message/file. The original message/file becomes inaccessible to the sender and the recipients in the chat/channel.
Administrators can customize the tombstone message for both messages and files.
To customize the tombstone messages:
-
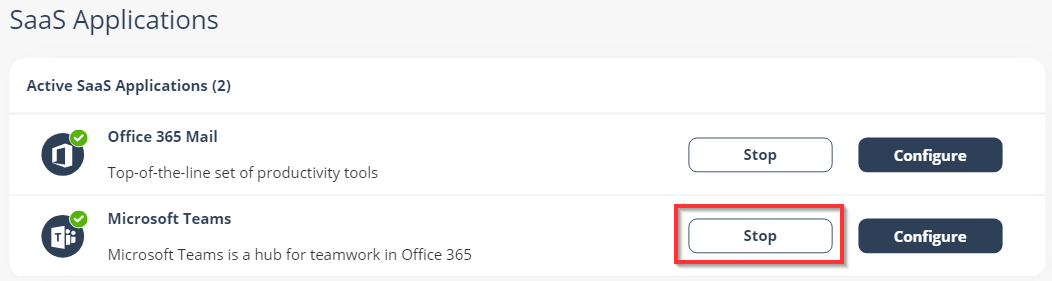
Navigate to Security Settings > SaaS Applications.
-
Click Configure for Microsoft Teams.
-
To customize the tombstone message for messages, update the Microsoft Teams Message field.
-
To customize the tombstone message for files, update the Microsoft Teams Files field.
-
To allow users to unblock tombstoned messages, enable the Allow unblock message checkbox.
-
Click Save.
Configuring Microsoft Teams Policy
Malware Policy
By default, the Microsoft Teams malware policy scans for malicious content in the files sent using Microsoft Teams.
Supported Actions
Microsoft Teams malware policy supports these actions:
-
Tombstone of files and text messages that contain malicious content.
-
If malicious content is found, the sender will get the tombstoned message.
For information about unblocking the tombstoned message, see Unblocking Messages.
-
If malicious content is found, the recipient(s) will get the tombstoned message.

-
-
Alert sender: Sends an email notification to the sender of a file or message that contains malicious content.
-
Alert admin(s): Sends an email notification to the admin(s) about the malicious files or messages.
Configuring Malware Policy
To configure Malware policy:
-
Click Policy on the left panel of the Harmony Email & Collaboration Administrator Portal.
-
Click Add a New Policy Rule.
-
From the Choose SaaS drop-down list, select Microsoft Teams.
-
From the Choose Security drop-down list, select Malware and click Next.
-
Select the desired protection mode (Detect and Remediate or Detect).
If required, you can change the Rule Name.
-
Under Blades, select the threat detection blades required for the policy.

Note - To select all the blades available for malware detection, enable All running threat detection blades checkbox.
-
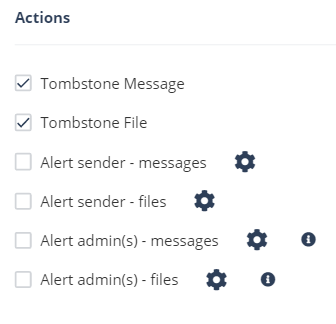
Configure Actions required from the policy.
-
To tombstone messages, enable the Tombstone Message checkbox.
Note - This option will be available only in Detect and Remediate protection mode and when URL Reputation threat detection blade is enabled.
-
To tombstone files, enable the Tombstone File checkbox.
Note - This option will be available only in Detect and Remediate protection mode and when the Anti-Malware threat detection blade is enabled.
-
To send email alerts to the sender about malware in messages and files, enable the Alert sender - messages and Alert sender - files checkbox.
-
To send email alerts to admins about malware in messages and files, enable the Alert admin(s) - messages and Alert admin(s) - files checkbox.

Notes:
-
Even when the alerts are enabled here in the policy, the administrator only receives email alerts for security events when Receive Alerts role is enabled in the Specific Service Role. For more details about managing roles and permissions in the Infinity Portal, refer to Global Settings > Users in Infinity Portal Administration Guide.
-
To customize the email alert templates, click on the gear icon to the right of the alert.
-
-
Click Save and Apply.
DLP Policy
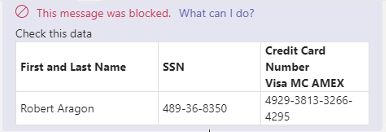
By default, the DLP policy scans the messages and files for potentially leaked information, such as credit card number and Social Security Number (SSN).
Supported Actions
Microsoft Teams DLP policy supports these actions:
-
Tombstone of files and text messages that contain sensitive information.
-
If sensitive information is found, the sender will get the tombstoned message.
For information about unblocking the tombstoned message, see Unblocking Messages.
-
If sensitive information is found, the recipient(s) will get the tombstoned message.

-
-
Alert sender: Sends an email notification to the sender of a file or message that contains sensitive information.
-
Alert admin(s): Sends an email notification to the admin(s) about the files or messages that contain sensitive information.
Configuring DLP Policy for Microsoft Teams
To configure DLP policy:
-
Click Policy on the left panel of the Harmony Email & Collaboration Administrator Portal.
-
Click Add a New Policy Rule.
-
From the Choose SaaS drop-down list, select Microsoft Teams.
-
From the Choose Security drop-down list, select DLP and click Next.
-
Select the desired protection mode (Detect and Remediate or Detect).
If required, you can change the Rule Name.
-
Under DLP Criteria, select the DLP categories required for the policy.
For more details about the DLP Data Types and categories, see Appendix E: DLP Built-in Data Types and Categories.
-
Select the sensitivity level required for the policy.
-
Very high (hit count > 0)
-
High (hit count > 2)
-
Medium (hit count > 5)
-
Low (hit count > 10)
-
Very Low (hit count > 20)
-
-
To exclude DLP policy for the messages and files shared only with the internal users, enable the Skip Internal items checkbox.
-
Configure Actions required from the policy.
-
To tombstone messages, enable the Tombstone Message checkbox.
Note - This option will be available only when Detect and Remediate protection mode is enabled.
-
To tombstone files, enable the Tombstone File checkbox.
Note - This option will be available only when Detect and Remediate protection mode is enabled.
-
To send email alerts to the sender about DLP in messages and files, enable the Alert sender - messages and Alert sender - files checkbox.
-
To send email alerts to admins about DLP in messages and files, enable the Alert admin(s) - messages and Alert admin(s) - files checkbox.
Notes:
-
Even when the alerts are enabled here in the policy, the administrator only receives email alerts for security events when Receive Alerts role is enabled in the Specific Service Role. For more details about managing roles and permissions in the Infinity Portal, refer to Global Settings > Users in Infinity Portal Administration Guide.
-
To customize the email alert templates, click on the gear icon to the right of the alert.
-
-
Click Save and Apply.
Secured Microsoft Teams Messages
Harmony Email & Collaboration connects with Microsoft Teams using Microsoft APIs.
As Microsoft APIs are primarily designed to tackle DLP challenges and not malware/phishing messages, they allow different security levels based on whether the sender is within the organization and whether it is a direct message or part of a team channel conversation. These limitations affect both DLP and malicious message scenarios.
|
Message direction |
Message visible in the portal |
Generate events and alerts |
Block malicious messages and files |
|
|---|---|---|---|---|
|
Direct Messages |
||||
|
Messages within the organization (Internal > Internal) |
Yes |
Yes |
Yes |
|
|
Messages sent from the organization to outside the organization (Internal > External) |
Yes |
Yes |
Yes |
|
|
Messages sent from outside the organization to the organization (External > Internal) |
Yes |
Yes |
No |
|
|
Messages sent in Microsoft Teams channels |
||||
|
Channels created by internal (protected) users |
Messages sent by internal users |
Yes |
Yes |
Yes |
|
Messages sent by external users |
Yes |
Yes |
Yes |
|
|
Channel created by external users |
Messages sent by internal users |
No |
No |
No |
|
Messages sent by external users |
No |
No |
No | |
Handling Partially Secured Messages
To protect the Microsoft Teams messages that cannot be inspected or tombstoned, administrators can do these:
-
Configure the Malware Policy and DLP Policy to receive alerts and respond quickly to the detected malicious messages from external parties.
-
Enhance the security settings for external meetings and chat with people outside the organization. See Microsoft documentation.
Secured Users
Like in any application, to protect a user's Microsoft Teams messages, the user must have one of the supported licenses. For more information, see Minimum License Requirements to Activate SaaS Applications.
Harmony Email & Collaboration does not protect messages sent by users and sent from external parties to users without a supported license. Also, these messages do not appear in the Harmony Email & Collaboration Administrator Portal.
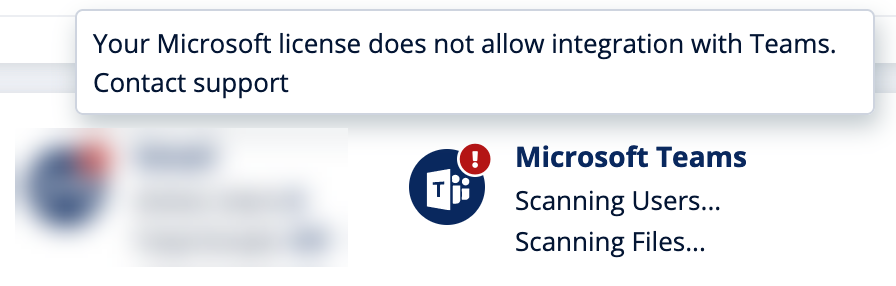
If Harmony Email & Collaboration detects users with unsupported Microsoft Teams licenses, it shows the status on the Overview page.
-
If there are no users with a supported license, Harmony Email & Collaboration shows an error indicator that Microsoft Teams is not secured.
-
If there are some users with unsupported licenses, Harmony Email & Collaboration shows a warning indicator that some of the users are not protected.

Unblocking Messages
When malicious or sensitive information is detected, Harmony Email & Collaboration tombstones the messages.
To unblock the message, the user should click What can I do?.
-
If it is configured to allow unblocking the messages in Customizing Tombstone Messages, the sender can select one of these.
-
To unblock the message:
-
Select Override and send.
-
Enter the justification for sending the message.
-
Click Confirm.
-
-
To unblock the message and also report it to the administrator, the sender can select Override and send and report it to my admin and click Confirm.
-
-
If it is not configured to allow unblocking the messages, the sender will see the following message:
Viewing Microsoft Teams Security Events
Harmony Email & Collaboration records the Microsoft Teams detections as security events. The event type depends on the type of policy that created the event. You can handle the security events in different ways, whether they are detected/prevented automatically or discovered by the administrators after not being prevented.
The Events screen shows a detailed view of all the security events.