Introduction to Harmony Email & Collaboration
Overview
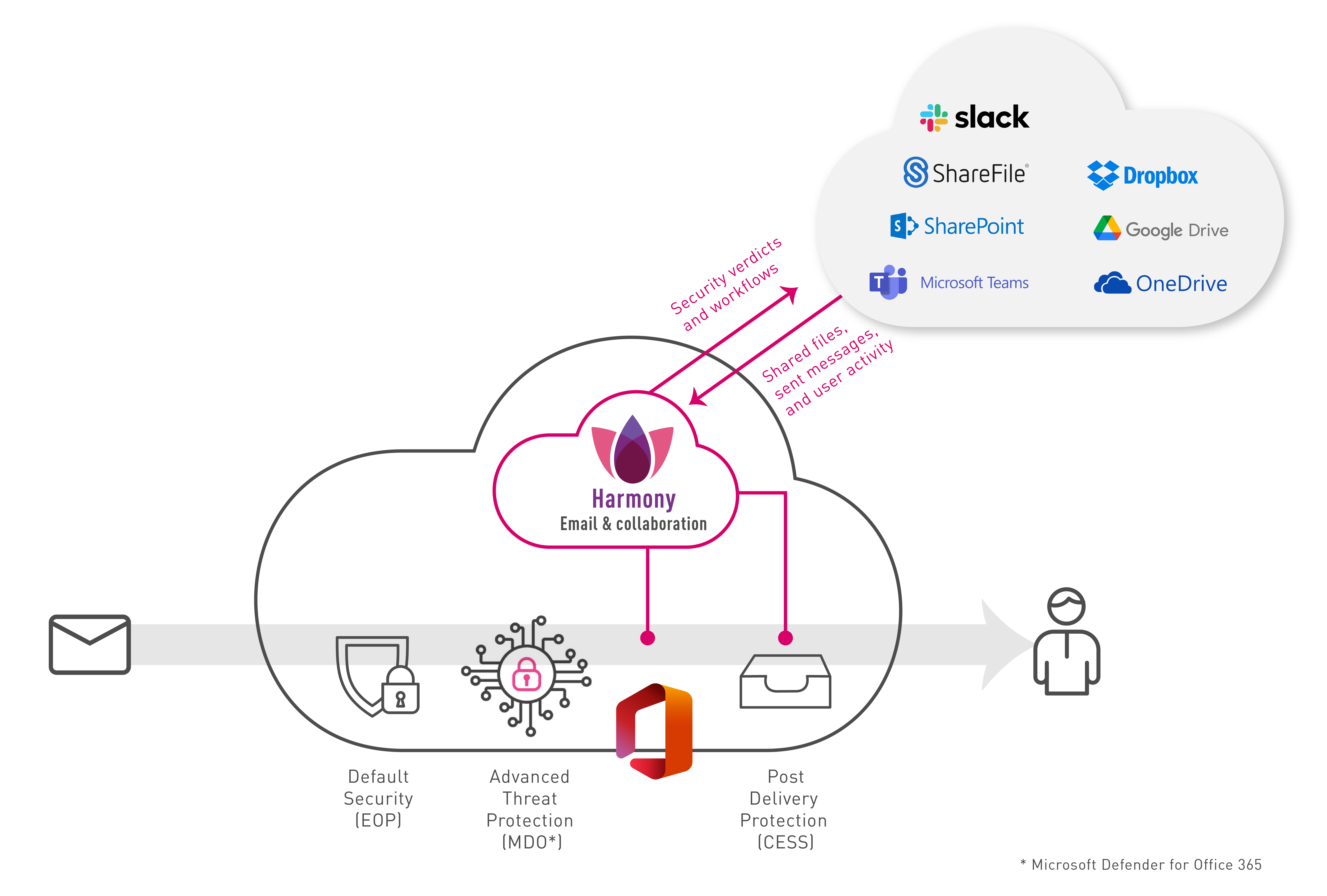
Check Point's Harmony Email & Collaboration is an API-based inline protection service that protects your SaaS applications from advanced threats, such as:
-
Zero-Day Threat
-
Phishing
-
Account Takeover
-
Data Leakage
-
SaaS Shadow IT Discovery
How It Works
Email Protection
When an email is sent, Harmony Email & Collaboration intercepts and sends the email to Check Point’s ThreatCloud for analysis before the email is delivered to the recipient. If the verdict is malicious, then the email is handled according to the configured workflow (for example, quarantine). Otherwise, the email is delivered to the recipient.
Harmony Email & Collaboration also inspects internal and outgoing traffic, both for data leakage and for phishing and malware. Emails can be removed and modified post-delivery if needed.
Supported Applications
-
Microsoft Exchange Online (Office 365 Mail)
-
Gmail
File Sharing Applications
When you upload a file to the application, Harmony Email & Collaboration inspects it for malware and against the organization's DLP policy. Files with detected threats are quarantined or vaulted.
Supported Applications
-
Microsoft OneDrive
-
Microsoft SharePoint
-
Google Drive
-
Citrix ShareFile
-
DropBox
-
Box
Messaging Applications
Harmony Email & Collaboration inspects every message for malware, DLP and phishing indicators. It also inspects every uploaded file for malware and DLP.
Supported Applications
-
Microsoft Teams
-
Slack
BEC/Compromised Accounts (Account Takeover)
Harmony Email & Collaboration inspects the behavior of users inside the Microsoft environment – their login patterns, correspondence patterns, and many more – to determine if an account has been compromised before any damage is done. The account is then automatically blocked by the system, or manually blocked by an administrator.
About this Guide
This guide describes how to protect cloud email and collaboration suites using Harmony Email & Collaboration.
Learn how to:
-
Activate the protection for supported SaaS applications.
-
Configure security policies and settings for each of the protected applications.
-
Review security events and act on them.
-
Generate reports and integrate with external SIEM platforms.