Threat Detection Policy for Outgoing Emails
Administrators can enable threat detection to prevent malware, phishing, and spam emails from being sent by their organization’s users to external parties.
|
|
Note - This feature is supported only for Office 365 Mail. |
Configuring a Threat Detection Policy Rule
To enable threat detection for outgoing emails:
-
Navigate to Policy on the left panel of the Infinity Portal.
-
Click on an Office 365 Mail Threat Detection policy rule.
If you do not have a Office 365 Mail Threat Detection policy rule, create a new policy. See Threat Detection Policy for Incoming Emails.
-
Select the desired policy protection mode (Detect, Detect and Remediate or Prevent (Inline)).
If required, you can change the Rule Name.
-
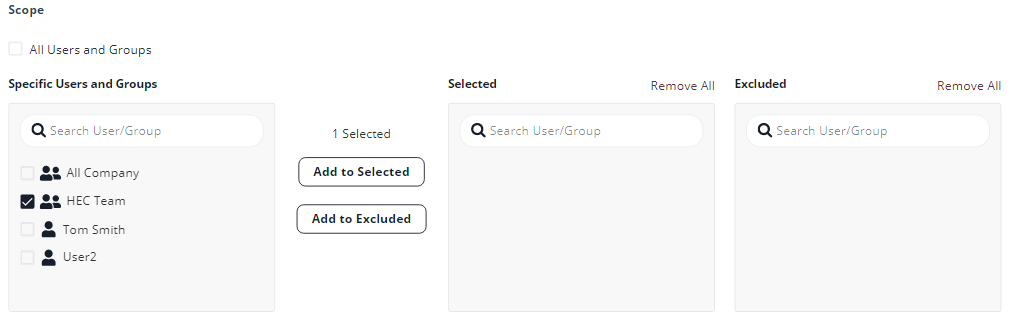
Under Scope, select the users and groups to which the policy is applicable and click Add to Selected.
-
To apply the policy to all users and groups in your organization, select All Users and Groups checkbox.
-
To apply the policy only to specific users or groups, select the users/groups and click Add to Selected.
-
To exclude some of the users or groups from the policy, select the users/groups and click Add to Excluded.
For more information about excluded users, see Excluding Members of Microsoft 365 Groups from a Prevent (Inline) Policy.
-
-
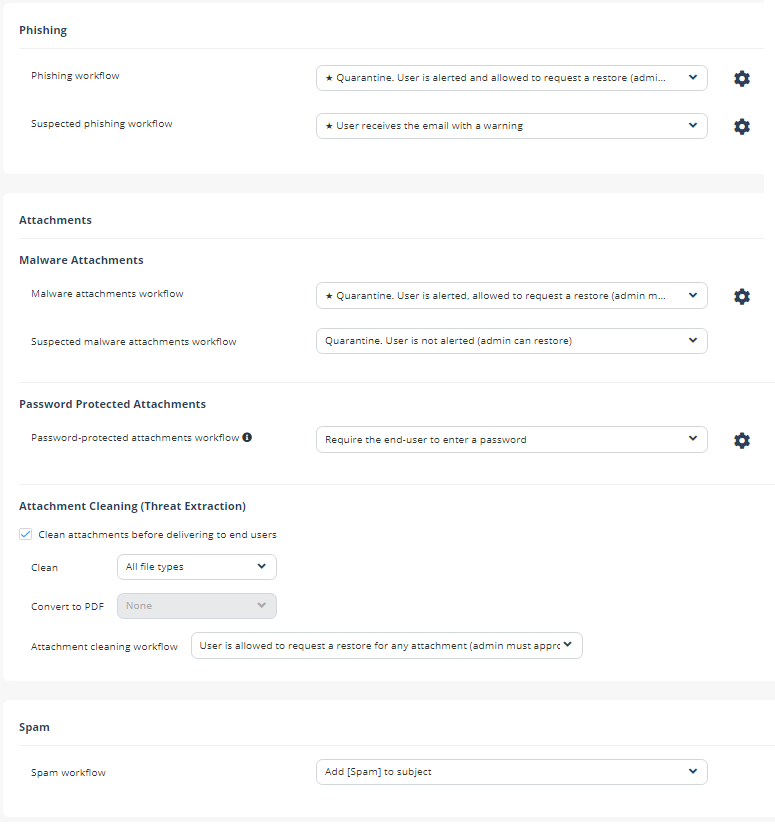
Select the workflows required for the policy.

Note - If you select Detect and Remediate or Detect mode, you may not see some of these additional configuration options that allows you to customize the end user email notifications.
For more information on workflows, see Phishing Protection, Malware Protection, and Password Protected Attachments Protection.
-
Scroll down and expand Advanced Configuration.
-
Under Advanced Settings, enable Protect (Inline) Outgoing Traffic checkbox.
-
Click Save and Apply.
Supported Workflow Actions
As the protected emails are sent from inside the organization to external parties, the threat detection for outgoing emails do not support all the workflows as specified for the incoming emails.
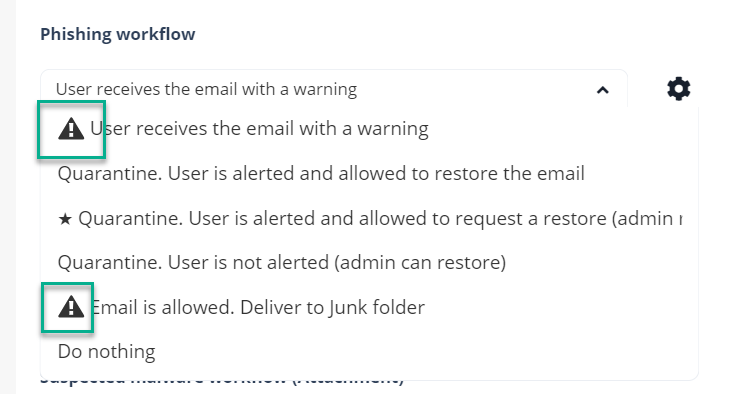
It does not support these workflows:
-
Delivering the email to the recipient's Junk folder (Email is allowed. Deliver to Junk folder)
-
Delivering the email with a warning banner (User receives the email with a warning)
-
Delivering the email with a prefix added to the subject (Add [Spam] to subject)
All the workflow actions that are not supported for outgoing emails are marked with a warning symbol.
|
|
Notes:
|
Prerequisites to Avoid Failing SPF Checks
For Office 365 Mail, if you enable Protect (Inline) Outgoing Traffic in the DLP or Threat Detection policy, Harmony Email & Collaboration gets added to the email delivery chain before reaching external recipients (Internal email sender > Microsoft 365 > Harmony Email & Collaboration > Microsoft 365 > External recipient).
The recipient's email security solution sees the Harmony Email & Collaboration IP address as part of the delivery chain. If the recipient's email security solution fails to recognize the original IP address, it may consider the Harmony Email & Collaboration IP address as the IP address from which the email was sent.
If you do not configure the SPF record in your DNS to allow Harmony Email & Collaboration IP addresses to send emails on behalf of your domain, your emails might fail SPF checks and may be quarantined.
Check Point recommends you add the Harmony Email & Collaboration IP addresses to your SPF record before you enable Protect (Inline) Outgoing Traffic for outgoing emails.
To prevent outgoing emails from failing SPF checks and being quarantined, you must add include:spfa.cpmails.com to your SPF record.
|
|
Note - The above statement includes several IP addresses and networks, some outside your Infinity Portal's data region. This is done for uniformity and consistency in all Check Point SPF records regardless of your data region. Harmony Email & Collaboration sends the emails only from one of the IP addresses in your region. |