Password Protected Attachments Protection
When password-protected attachments are detected, Harmony Email & Collaboration attempts to extract the password using various techniques such as searching for the password in the email body. If the password is found, Harmony Email & Collaboration uses the password to decrypt the file and inspect it for malware.
If the password is not found, the administrator can select any one of these workflows:
Password Protected Attachments Workflow
|
|
Note - These workflows apply only for the incoming and internal emails. |
|
Workflow |
Description |
||
|---|---|---|---|
|
User receives the email with a warning |
The detected email is delivered to the user with a notification inserted in the body of the email. |
||
|
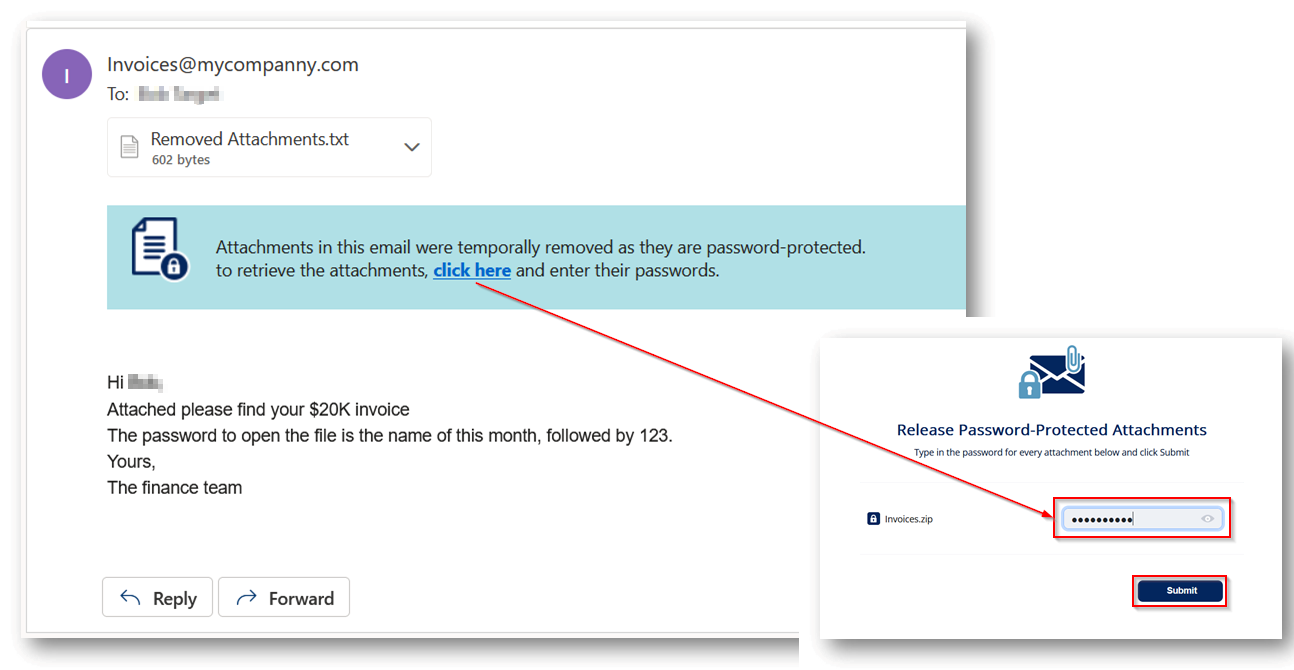
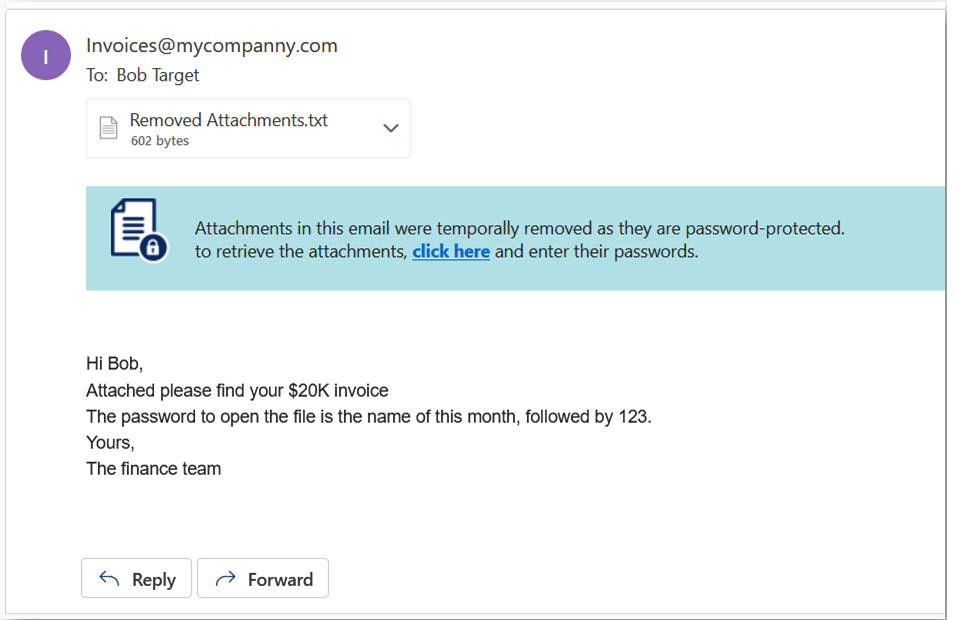
Require the end-user to enter a password |
The attachment is removed temporarily and a warning banner is added to the email along with a link to enter the password. After the password is entered, the Anti-Malware engine scans the attachment. If the Anti-Malware engine finds the attachment as clean, the original email with the original password-protected attachment gets delivered to the original recipients of the email. Notes:
|
||
|
Quarantine. User is alerted and allowed to restore the email |
The email is automatically quarantined and the user is notified about the quarantine. Using the link in the email, the user can release the attachment. The original email and attachment will be immediately delivered back to the inbox. |
||
|
Quarantine. User is not alerted (admin can restore) |
The email is automatically quarantined with no user notification. The administrator can restore the email. |
||
|
Trigger suspected malware workflow |
The email follows the workflow configured for Suspected Malware. |
||
|
Do nothing |
The attachment will be considered as clean.
|
To add allow-list for password-protected attachments from specific email addresses or domains, see Password-Protected Attachments Allow-List.
For more information on who receives the restored emails, see Who Receives the Emails Restored from Quarantine.
Supported File Types
Harmony Email & Collaboration can detect these file types as password-protected:
|
File Type |
File Extensions |
|---|---|
|
Archives |
AR, ARJ, BZ2, CAB, CHM, CRAMFS, CPIO, GZ, IMG, ISO, IZH, QCOW2, RAR, RPM, TAR,TAR.BZ2, TAR.GZ, TAR.XZ, TB2, TBZ, TBZ2, TGZ, TXZ, UDF, WIM, XZ, ZIP, and 7Z. |
|
Adobe PDF (all versions) |
|
|
Microsoft Excel 2007 and later |
XLSX, XLSB, XLSM, XLTX, XLTM, XLAM |
|
Microsoft Excel 2007 Binary |
XLSB |
|
Microsoft Excel 97 - 2003 |
XLS |
|
Microsoft PowerPoint 2007 and later |
PPTX, PPTM, POTX, POTM, PPAM, PPSX, PPSM |
|
Microsoft PowerPoint 97 - 2003 |
PPT, PPS, POT, PPA |
|
Microsoft Word 2007 and later |
DOCX, DOCM, DOTX, DOTM |
|
Microsoft Word 97 - 2003 |
DOC, DOT |
To add allow-list for password-protected attachments from specific email addresses or domains, see Password-Protected Attachments Allow-List.
Requesting Passwords from End Users - End-User Experience
Require end-user to enter a password workflow
For password protected attachments, if
To restore the password protected attachments
-
Click the link in the warning banner of the email.
-
Enter the password for the attachment and click Submit.
After you submit, the Anti-Malware engine scans the attachment for malicious content.
If the Anti-Malware engine finds the attachment as clean, the original email with password-protected attachment gets delivered to the original recipients of the email.
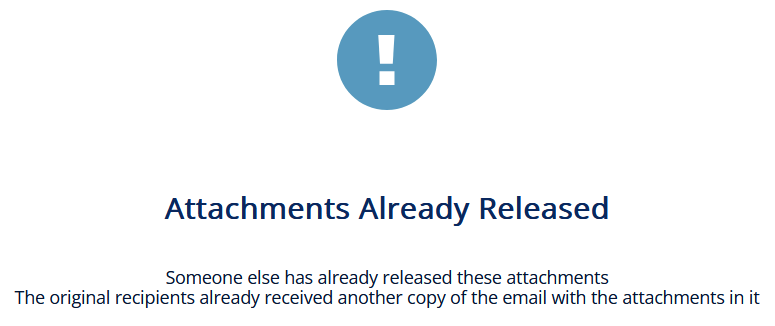
If the email was already released, this message appears:
Quarantine. User is alerted and allowed to restore the email workflow
For password protected attachments, if
To restore the email and its attachments
-
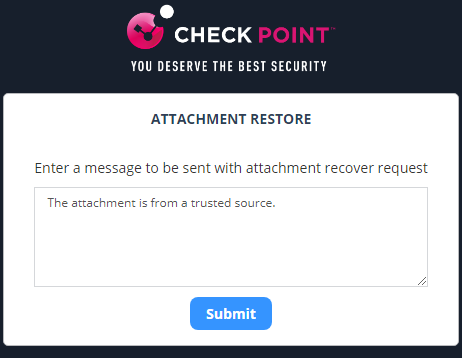
Click the link provided in the email.
-
If prompted, enter the reason for restoring the attachment, and click Submit.
After you submit, the admin receives the request.
After the admin approves, the user receives the original email.
Password Protected Attachments - Administrator Experience
For password protected attachments, if Quarantine. User is alerted and allowed to restore the email workflow is defined for the policy, and if the end-user requests to release the email, the administrator is notified about the request.
To review the request:
-
Open the security event of the email for which the user requested to release.
Under Security Stack, the password-protected attachments which are not scanned by Anti-Malware will be marked as Insecure attachments found.
-
To inspect the password-protected attachments before restoring the email:
-
Click Type in passwords to enter the password for the attachment.
-
Enter the password for the attachment and click Submit.
The Anti-Malware engine scans the attachment and gives a verdict. Depending on the verdict decide whether to restore the email or not.
-
To restore the email and its attachments, click Restore Email.
-
-
To release the original email without inspecting the password-protected attachments, click Restore Email.