

In This Section: |
This section covers the search bar and filters in Views and Reports.
The search bar lets you:

The search applies to all widgets in the view / report.
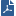
You can automatically enter query text into the search bar by right clicking a value in the widget and selecting Filter or Filter Out.
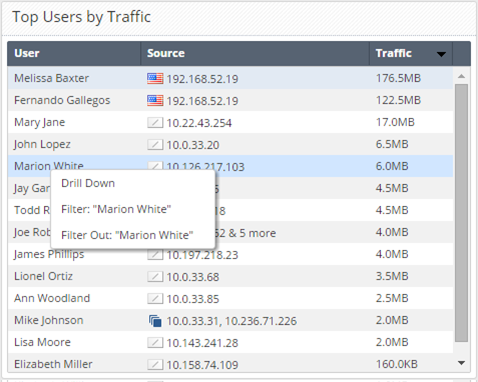
In the Log View, click the Favorites button to open the predefined queries.
For more on queries, see: Query Language Overview
The search bar is used to apply on-demand filters, but you can also save filters with the view / report definition.

There are different layers of filters:
Edit View Filter

Select one of these time frames:

You can also define a time range.
SmartEvent includes a powerful query language that lets you show only selected records from the log files, according to your criteria. You can create complex queries with Boolean operators, wildcards, fields, and ranges. This section is a detailed reference to the SmartEvent query language.
When you use the SmartEvent GUI to create a query, the applicable criteria show in the Query Definition field.
The basic query syntax is:
[<Field>:] <filter_criterion>
You can put together many criteria in one query with Boolean operators:
[<Field>:] <filter_criterion> AND|OR|NOT [<Field>:] <Filter_Criterion> ...
Query keywords and filter criteria are not case sensitive.
Most query keywords and filter criteria are not case sensitive, but there are some exceptions. For example, Risk:High is case sensitive (Risk:high will not match). If your query results do not show the expected results, change the case of your query criteria or try both upper and lower case.
Note: When you use queries with more than one criteria value, you must explicitly enter a Boolean operator.
Criteria values are written as one or more text strings. You can enter one text string, such as a word, IP address or URL, without delimiters. Phrases or text strings that contain more than one word must be surrounded by quotation marks.
One word string examples:
Phrase examples
"John Doe""Log Out""VPN-1 Embedded Connector"IPv4 addresses used in SmartEvent queries are counted as one word. You can enter IPv4 address using dotted decimal notation. You can also use the '*' wildcard character with IPv4 addresses.
Example:
You can use NOT <field> values with field keywords in SmartEvent queries to find events for which the filed has no value.
Syntax
NOT <field>
Example
NOT src:10.0.4.10
You can use the standard wildcard characters (* and ?) in queries to match variable characters or strings in log records. The wildcard character cannot be the first character in a query criterion. You can use more than wildcard character in query criteria.
Wildcard syntax
Examples:
If your criteria value contains more than one word, you can use the wildcard in each word. For example, 'Jo* N*' shows Joe North, John Natt, Joshua Named, and so on.
The * wildcard character can represent digits in IPv4 addresses. You can only use the wildcard character for one or more full octets in the address. It must be preceded by the dot character. For example, 192.168.* is legal, but 192.168.2* is not.
Examples:
You can use predefined field names, followed by a colon, as keywords in filter criteria. SmartEvent only shows log records that match the criteria in the specified field. If you do not use field names, SmartEvent shows records that contain the criteria in all fields.
This table shows the predefined field keywords. Some fields also support keyword aliases that you can type as alternatives to the primary keyword.
Keyword |
Keyword Aliases |
Description |
|---|---|---|
|
|
Severity of the event |
|
|
Potential risk from the event |
|
|
Name of the protection |
|
|
Type of protection |
|
|
Level of confidence that an event is malicious |
|
|
Action taken by a security rule |
|
|
Software Blade |
|
|
Traffic destination IP address, DNS name or Check Point network object name |
|
|
Name of originating Security Gateway |
|
|
Service that generated the log entry |
|
|
Traffic source IP address, DNS name or Check Point network object name |
|
|
User name |
The syntax for a field name query is: <field_name>:<values>
Examples:
source:192.168.2.1action:(Reject OR Block)You can use the OR Boolean operator in parentheses to include multiple criteria values.
You can use Boolean operators in queries. The available Boolean operators are:
Notes:
Examples:
blade:"application control" AND action:block - Shows log records from the Application Control and URL Filtering Software Blade where traffic was blocked.192.168.2.133 10.19.136.101 - Includes log entries that match the two IP addresses. The AND operator is presumed.192.168.2.133 OR 10.19.136.101 - Includes log entries the match one of the IP addresses.(blade:Firewall OR blade:IPS OR blade:VPN) AND NOT action:drop - Includes all log entries from the Firewall, IPS or VPN blades that are not dropped. The criteria in the parentheses are applied before the AND NOT criterion. Source:(192.168.2.1 OR 192.168.2.2) AND destination:17.168.8.2 - Includes log entries from the two source IP addresses if the destination IP address is 17.168.8.2. This example also shows how you can use Boolean operators with field criteria.