

In This Section: |
The Mirror and Decrypt feature performs these actions on your Security Gateway, or Cluster:
Action |
Description |
|---|---|
Mirror only |
Your Security Gateway or Cluster clones all traffic (including HTTPS without decryption) that passes through it, and sends it out of the designated physical interface. |
Mirror and Decrypt |
Your Security Gateway or Cluster clones all HTTPS traffic that passes through it, decrypts it, and sends it in clear-text out of the designated physical interface. Note - If you wish to decrypt the HTTPS traffic, you must enable and configure the HTTPS Inspection on your Security Gateway, or Cluster. |
You can add a third-party Recorder or Packet-Broker in your environment and forward to it the traffic that passes through your Security Gateway, or Cluster. This Recorder or Packet-Broker must work in monitor (promiscuous) mode to accept the decrypted and mirrored traffic from your Security Gateway, or Cluster.
R80.30 Security Gateway, or Cluster works only with one Recorder, which is directly connected to a designated physical network interface (NIC) on the Check Point Gateway, or Cluster Members.
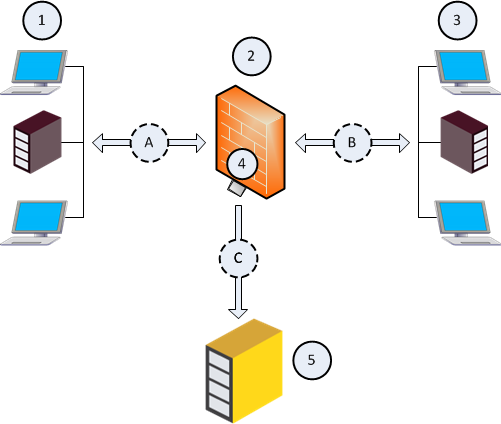
Example Topology and Traffic Flow:
Item |
Description |
|---|---|
1 |
First network that sends and receives traffic through the Security Gateway (2). |
2 |
Security Gateway, through which networks (1) and (3) send and receive their traffic. |
3 |
Second network that sends and receives traffic through the Security Gateway (2). |
4 |
Designated physical interface on the Security Gateway (2). |
5 |
Recorder, or Packet-Broker that works in a monitor (promiscuous) mode. |
A |
Traffic flow between the first network (1) and the Security Gateway (2). |
B |
Traffic flow between the second network (3) and the Security Gateway (2). |
C |
Flow of the decrypted and mirrored traffic from the Security Gateway (2) to the Recorder, or Packet-Broker (5). |
Workflow for configuring Mirror and Decrypt in Gateway mode:
Step |
Description |
|---|---|
1 |
Read and follow the Mirror and Decrypt Requirements. |
2 |
|
3 |
Configure the Mirror and Decrypt in the Security Gateway, or Cluster object in SmartConsole. |
Workflow for configuring Mirror and Decrypt in VSX mode:
Step |
Description |
|---|---|
1 |
Read and follow the Mirror and Decrypt Requirements. |
2 |
|
3 |
Configure the Mirror and Decrypt in the Virtual System object in SmartConsole: |
Source MAC address of the decrypted and mirrored packets
Traffic |
Source MAC address of the decrypted and mirrored packets the Security Gateway and Cluster Members send |
|---|---|
Mirror only of all traffic |
MAC address of the designated physical interface. |
Mirror and Decrypt of HTTPS traffic |
00:00:00:00:00:00: |