
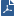

Workflow for several Virtual Systems:
Note - If the Recorder or Packet-Broker connects to the VSX Gateway, or VSX Cluster members through a Switch, configure a VLAN Trunk on the applicable Switch port. The VLAN Trunk port on the Switch must accept all VLAN IDs that you configure in the applicable Virtual Systems.
To enable the HTTPS Inspection in the object of applicable Virtual Systems:
Step |
Description |
|---|---|
1 |
In SmartConsole, from the left Navigation Panel, click Gateways & Servers. |
2 |
Open the Virtual System object. |
3 |
From the navigation tree, click HTTPS Inspection. |
4 |
View and export the certificate. |
5 |
Check Enable HTTPS Inspection. |
6 |
Click OK. |
To configure the HTTPS Inspection Rule Base:
Step |
Description |
|---|---|
1 |
In SmartConsole, from the left Navigation Panel, click Security Policies. |
2 |
In the Shared Policies section, click HTTPS Inspection. |
3 |
In the middle of the page, click Open HTTPS Inspection Policy in SmartDashboard. The Legacy SmartDashboard opens. |
4 |
Configure the HTTPS Inspection Rule Base. For details, see Configuring HTTPS Inspection. |
5 |
From the top toolbar, click Update (or press Ctrl+S) to save the changes in the database. |
6 |
Close the SmartDashboard. |
Define the designated physical interface as VLAN Trunk:
Step |
Description |
|---|---|
1 |
In SmartConsole, open the object of the VSX Gateway, or VSX Cluster. |
2 |
From the navigation tree, click Physical Interfaces. |
3 |
Check the box VLAN Trunk near the designated physical interface. |
4 |
Click OK. |
To add the designated physical interface in the object of each Virtual System:
Step |
Description |
|---|---|
1 |
In SmartConsole, open the Virtual System object. |
2 |
From the navigation tree, click Topology. |
3 |
From the top toolbar, click New > Regular. |
4 |
On the General tab:
|
To activate the Mirror and Decrypt in the object of each Virtual System:
Step |
Description |
|---|---|
1 |
In SmartConsole, open the Virtual System object. |
3 |
From the navigation tree of the gateway object, click the [+] near the Other and click Mirror and Decrypt. |
4 |
Check Mirror gateway traffic to interface. Mirror and Decrypt - User Disclaimer window opens.
|
5 |
In the Mirror gateway traffic to interface field, select the VLAN interface (which is configured on top of the designated physical interface). |
6 |
Click OK to save the changes and close the Virtual System properties window. |
To configure the Mirror and Decrypt rules:
Best Practice:
We recommend you to configure a new separate Access Control Layer to contain Mirror and Decrypt rules. Alternatively, you can configure the Mirror and Decrypt rules in the regular Rule Base.
Important:
When you configure the Mirror and Decrypt rules, these limitations apply:
The Name column of these rules cannot contain these strings: <M&D>, <M&d>, <m&D>, or <m&d>.
The procedure below describes how to configure the Mirror and Decrypt rules in a separate Access Control Layer:
Step |
Description |
|---|---|
1 |
In SmartConsole, from the left Navigation Panel, click Security Policies. |
2 |
Create a new Access Control Layer in the Access Control Policy. |
2B |
In SmartConsole top left corner, click Menu > Manage policies and layers. |
2C |
Select the existing policy and click Edit (the pencil icon). Alternatively, create a new policy. |
2D |
From the navigation tree of the Policy window, click General. |
2E |
In the Policy Types section, make sure you select only the Access Control. |
2F |
In Access Control section, click on the + (plus) icon. A pop up window opens. |
2G |
In the top right corner of this pop up window, click New Layer. Layer Editor window opens. |
2H |
From the navigation tree of the Layer Editor window, click General. |
2I |
In the Blades section, make sure you select only the Firewall. |
2J |
On other pages of the Layer Editor window, configure additional applicable settings and click OK. |
2K |
In Access Control section, you see the Network Layer and the new Access Control Layer. |
2L |
Click OK to save the changes and close the Policy window. |
3 |
In SmartConsole, at the top, click the tab of the applicable policy. |
4 |
In the Access Control section, click the new Access Control Layer. In the default rule, you must change the
|
5 |
Above the existing Cleanup rule, add the applicable rules for the traffic you wish to Mirror and Decrypt. You must configure the Mirror and Decrypt rules as follows:
Important:
|
6 |
Publish the session and install the Access Control Policy. |
7 |
If in a Mirror and Decrypt rule you set the Track to Log, then you can filter the logs for this rule by the Access Rule Name, which contains the configured string: <M&D>, <M&d>, <m&D>, or <m&d>. |