Securing Voice Over IP
Introduction to Check Point Secure VoIP
IPS adds more than 80 IPS protections and VoIP settings to protect against malicious attacks. IPS protects by:
- Identifying attack signatures
- Identifying packets with protocol anomalies
- Ensuring RFC compliance
- Inspecting signaling protocols, verifying header formats and protocol call flow state
As part of IPS, VoIP Protections can be:
- Enforced for different gateways using IPS profiles
- Monitored using Detect Mode
IPS also lets you:
The Security Gateway interoperates with VoIP devices from many leading vendors and supports the SIP, H.323, MGCP and SCCP (Skinny) protocols.
VoIP Security Deployments
This section covers different deployments for enterprises, managed service providers, and telecom network providers.
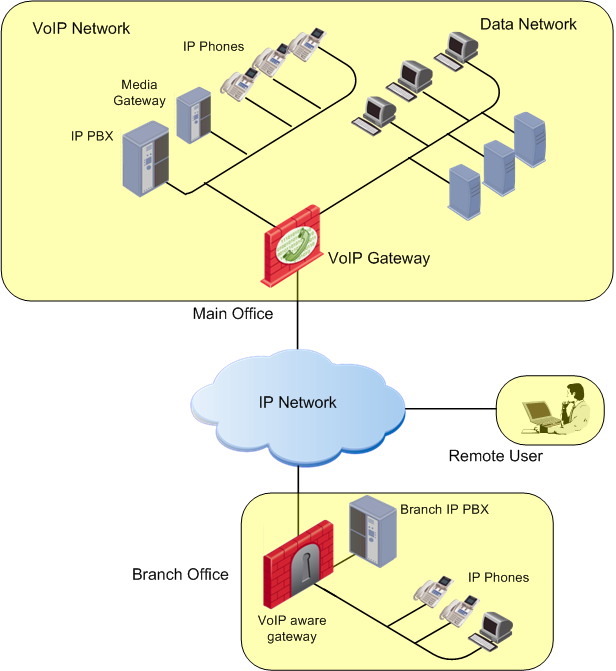
Enterprise Deployment 1: Perimeter VoIP Gateway
In this enterprise environment, remote users and branch offices make VoIP calls to and from the protected enterprise network. The Security Gateway is used to set up IPsec encrypted VPNs. For example, a VPN can be set up between the main office branch offices. Security capabilities for VoIP include:
- Protecting servers and PBXs in the enterprise LAN against Denial of Service attacks.
- Preventing unauthorized phone calls by means of Media admission control. These checks let only defined servers set up calls for the phones.
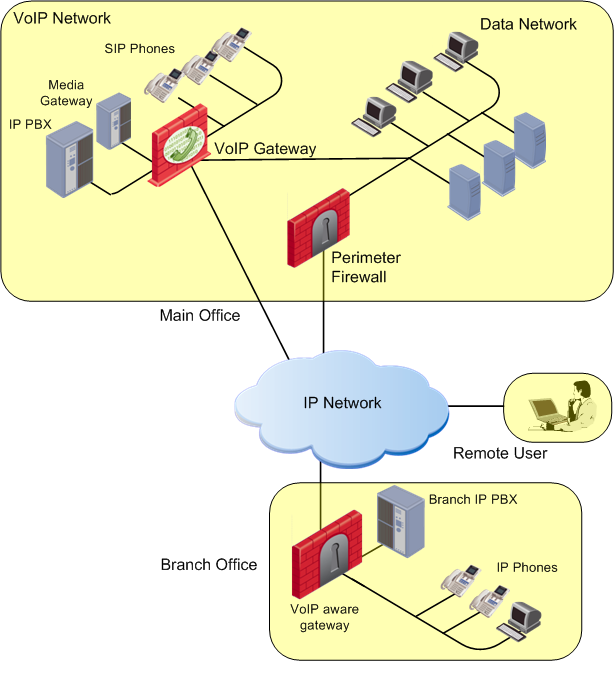
Enterprise Deployment 2: LAN Segmentation
In this enterprise deployment, the Security Gateway is used for internal LAN segmentation of VoIP and data traffic.
Dedicated gateways are deployed for VoIP security. Security is required to protect availability of VoIP equipment such as servers and PBXs in the enterprise LAN.
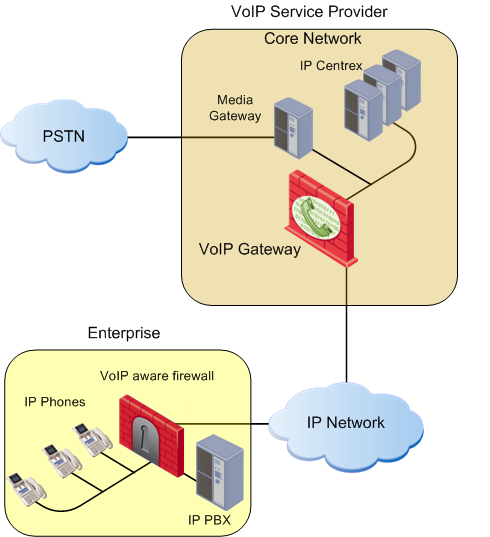
Service Provider Deployment
A service provider environment enables secure enterprise services. The Security Gateway also makes it possible to implement strong security measures that are necessary for a high quality of service.
VoIP Protocols
The Security Gateway secures VoIP traffic in H.323, SIP, MGCP, and SCCP environments.
VoIP calls use a series of complex protocols, each of which can transmit potentially malicious data through many ports.
The Security Gateway makes sure that:
- Caller and recipient addresses are where they claim to be
- Caller and recipient are allowed to make and receive VoIP calls
In addition, the Security Gateway examines the contents of the packets passing through all allowed ports to make sure the packets contain the correct information.
Full stateful inspection on H.323, SIP, MGCP, and SCCP protocols makes sure that:
- All VoIP packets are structurally valid
- The packets arrive in a valid sequence
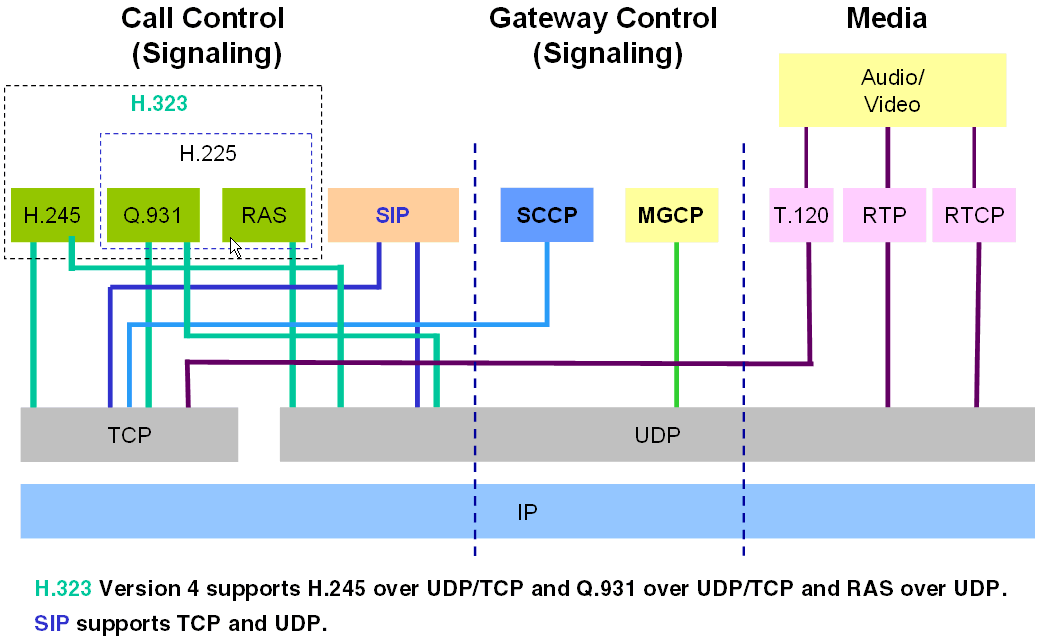
Signaling and Media Protocols
A phone call on an ordinary digital phone network and on a VoIP network is made up of media signals and control signals. The voice conversation is the media stream.
Dial tones and ringing tones, for example, are an indication that call control processes are occurring.
The different VoIP protocols use very different technologies, though they have the same aim. VoIP protocols handle these call control (or gateway) control and media functions:
- Call Control (signaling): Responsible for:
- setting up the call
- finding the peer
- negotiating coding protocols
- making the connection
- ending the call
- Gateway Control: Responsible for control signals between VoIP gateways, rather than between endpoint phones. These gateways negotiate VoIP traffic on behalf of the phones.
- Media: The voice or video payload. VoIP networks and ordinary phone networks use RTP/RTCP for the media. RTP carries the actual media and RTCP carries status and control information.
Control signals open fixed (known) ports and dynamic ports. The parties of a call then use control signals to negotiate dynamically assigned ports that each side opens to receive the RTP/RTCP media stream.
Supported Standards and Protocols
This section covers supported VoIP standards and protocols.
Supported SIP RFCs and Standards
The Security Gateway supports these SIP RFCs and standards:
- RFC 3261 SIP: Session Initiation Protocol
- RFC 3372 Session Initiation Protocol for Telephones (SIP-T)
- RFC 3311 UPDATE message
- RFC 2976 INFO message
- RFC 3515 REFER message
- RFC 3265 SIP Events
- RFC 3262 Reliability of Provisional Responses
- RFC 3428 MESSAGE message
- RFC 4566 SDP Session Description Protocol
- RFC 3264 An Offer-Answer Model with Session Description Protocol
- RFC 3265 Specific Event Notification
- RFC 3840 Indicating User Agent Capabilities in SIP
- RFC 3263 Locating SIP Servers
- RFC 3581 An Extension to the SIP for Symmetric Response Routing
- RFC 3892 SIP Referred-By Mechanism
- RFC 5194 Framework for Real-Time Text over IP Using SIP
- RFC 3326 The Reason Header Field for SIP
Supported MGCP RFCs and Standards
The Security Gateway supports these MGCP RFCs and standards:
- RFC-2705.
- RFC-3435 (version 1.0)
- ITU TGCP specification J.171.
Supported H.323 Protocols and Standards
Media in H.323 uses the RTP/RTCP and/or T.120 protocols.
Signaling is handled by these H.323 protocols:
- RAS manages registration, admission, and status. RAS uses a fixed port: UDP 1719.
- Q.931 manages call setup and termination. Q.931 uses a fixed port: TCP 1720.
- H.245 negotiates channel usage and capabilities. H.245 uses a dynamically assigned port.
As an H.323 call is processed by a Gatekeeper, these protocols are used in sequence and then the media passes. To end a call, the signaling protocols are used in reverse order.
When an endpoint connects to a Gateway, it does not use RAS. Otherwise, the protocol sequence for a Gateway is the same as for a Gatekeeper.
R77 also supports H.245 tunneling and Fast Connect, a H.323 capability that ensures that audio is available when the phone is answered. This feature is active by default, and is always available.
These H.323 ITU standards are supported:
- H.323 Versions 2, 3, and 4
- H.225 Versions 2, 3, and 4
- H.245 Versions 3, 5, and 7
SmartDashboard Toolbar
You can use the SmartDashboard toolbar to do these actions:
Icon
|
Description
|

|
Open the SmartDashboard menu. When instructed to select menu options, click this button to show the menu.
For example, if you are instructed to select > , click this button to open the Manage menu and then select the option.
|

|
Save current policy and all system objects.
|

|
Open a policy package, which is a collection of Policies saved together with the same name.
|

|
Refresh policy from the Security Management Server.
|

|
Open the Database Revision Control window.
|

|
Change global properties.
|

|
Verify Rule Base consistency.
|
|
Install the policy on Security Gateways or VSX Gateways.
|

|
Open SmartConsole.
|
|



