H.323-Based VoIP
Introduction to H.323
H.323 is an ITU (International Telecommunication Union) standard that specifies the components, protocols, and procedures that provide multimedia communication services over packet networks (including IP based networks).
The Security Gateway supports these H.323 architectural elements:
- IP phones
Devices that:
- Handle signaling (H.323 commands)
- Connect to an H.323 gatekeeper
IP Phones are defined in SmartDashboard, usually as a network of IP Phones. Usually it is not necessary to define Network objects for individual IP Phones.
- Standard telephones that connect to an H.323 gateway
These are not IP devices. It is not necessary to define them in SmartDashboard
- A Gatekeeper that manages a collection of H.323 devices, such as phones
Gatekeepers convert phone numbers to IP addresses. A Gatekeeper usually provides gateway services as well.
- A Gateway that provides interoperability between different networks
The gateway translates between the telephony protocol and IP.
Supported H.323 Deployments and NAT Support
Supported H.323 deployments are listed the Table. NAT (Hide or Static) can be configured for the phones in the internal network, and (where applicable) for the Gatekeeper.
- NAT is not supported on IP addresses behind an external Check Point gateway interface
- Manual NAT rules are only supported in environments where the gatekeeper is in the DMZ
|
No NAT
|
NAT for Internal Phones —
Hide/Static NAT
|
NAT for Gatekeeper —
Static NAT
|
Endpoint to Endpoint
|
Yes
|
Static NAT only
|
Not applicable
|
Gatekeeper/Gateway in External
|
Yes
|
Yes
|
Not applicable
|
Gatekeeper/Gateway to Gatekeeper/Gateway
|
Yes
|
Yes
|
Yes
|
Gatekeeper/Gateway in DMZ
|
Yes
|
Yes
|
Yes
|
|
|
|
Endpoint-to-Endpoint Communication
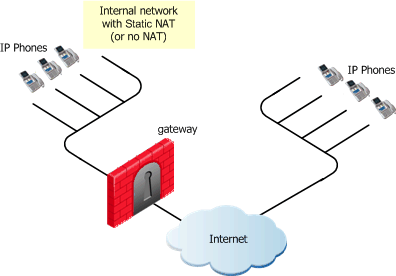
|
The IP Phones communicate directly, without a Gatekeeper or an H.323 Gateway. Static NAT can be configured for the phones on the internal side of the gateway.
|
Gatekeeper or H.323 Gateway in External Network
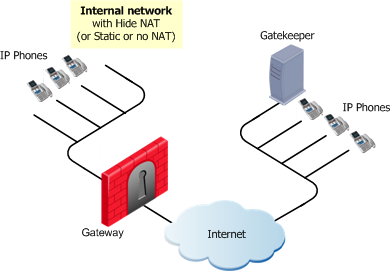
|
The IP Phones use the services of a Gatekeeper or H.323 Gateway on the external side of the gateway. This topology enables using the services of a Gatekeeper or an H.323 Gateway that is maintained by another organization. It is possible to configure Hide NAT (or Static NAT or no NAT) for the phones on the internal side of the gateway.
|
H.323 Gatekeeper/Gateway to Gatekeeper/Gateway
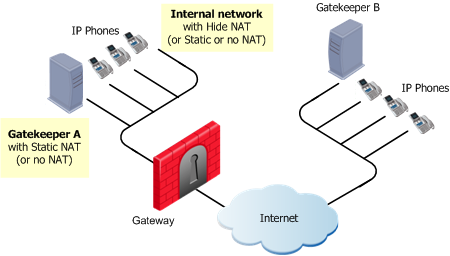
|
Each Gatekeeper or H.323 Gateway controls a separate endpoint domain. Static NAT can be configured for the internal Gatekeeper. For the internal phones, Hide NAT (or Static NAT) can be configured.
|
Gatekeeper or H.323 Gateway in the DMZ
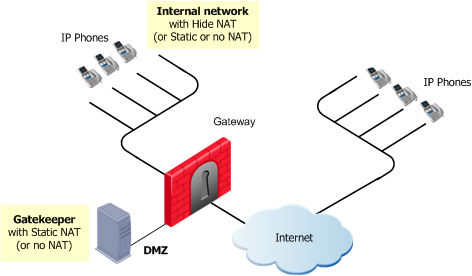
|
The same Gatekeeper or H.323 Gateway controls both endpoint domains. This topology makes it possible to provide Gatekeeper or H.323 Gateway services to other organizations. Static NAT (or no NAT) can be configured for the Gatekeeper or H.323 Gateway. Hide NAT (or Static or no NAT) can be configured for the phones on the internal side of the gateway.
|
H.323 Security Rule Base Configuration
This section explains how to configure rules that allow H.323 calls through the gateway.
H.323 Specific Services
These predefined H.323 services are available:
Service
|
Purpose
|
TCP:H323
|
Allows a Q.931 to be opened (and if needed, dynamically opens an H.245 port), and dynamically opens ports for RTP/RTCP or T.120.
|
UDP:H323_ras
|
Allows RAS port to be opened, and then dynamically opens a Q.931 port (an H.245 port if needed). Also dynamically opens and RTP/RTCP and T.120 ports.
|
UDP:H323_ras_only
|
Allows only RAS. Cannot be used to make calls. If this service is used, no Application Intelligence checks (payload inspection or modification as NAT translation) are made. Do not use if you want to perform NAT on RAS messages. Do not use in the same rule as the H323_ras service.
|
TCP:H323_any
|
Relevant only for versions prior to R75.40VS:
Similar to the H323 service, but also allows the in the rule to be ANY rather than a Network object. Only use H323_any if you do not know the VoIP topology, and are not enforcing media admission control (formerly known as Handover) using a VoIP domain. Do not use in the same rule as the H.323 service.
|

|
Note - In general, use the H.323 and H.323_ras services in H.323 Security Rule Base rules.
|
General Guidelines for H.323 Security Rule Configuration
- It is recommended to configure anti-spoofing on the Check Point gateway interfaces.
- To allow H.323 traffic, create rules let H.323 control signals through the gateway.
It is not necessary to define a rule that specifies which ports to open and which endpoints can talk. The gateway derives this information from the signaling. For a given H.323 signaling rule (with RAS and/or H.323 services), the gateway automatically opens ports for the H.245 connections and RTP/RTCP media stream connections.
Dynamic ports will only be opened if the port is not used by a different service. For example: if the Connect message identifies port 80 as the H.245 port, the port will not be opened. This prevents well-known ports from being used illegally.
- To allow H.323 traffic in the Security Rule Base, use regular Network objects. It is not necessary to define special Network objects.
- When using Hide NAT for H.323, include the hiding IP address in the destination of the H.323 rule. This allows the initiation of a TCP handshake from the external network to the hiding IP.
- When configuring a security rule, if you want calls that are in progress not to be dropped during Install Policy, make sure to select in the Service Properties dialog box.
Note – even if the new policy does not allow calls like those in progress, they will not be dropped during Install Policy.
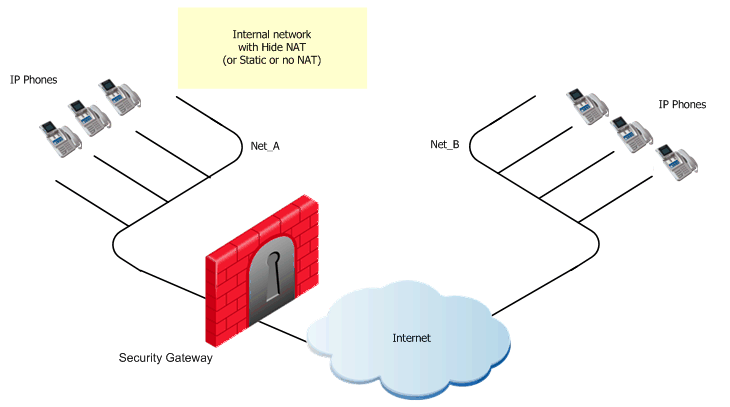
H.323 Rule for an Endpoint-to-Endpoint Topology
An endpoint-to-endpoint topology is shown in the figure, with Net_A and Net_B on opposite sides of the gateway. This procedure explains:
VoIP rule for this scenario:
Source
|
Destination
|
Service
|
Action
|
Net_A
Net_B
|
Net_B
Net_A
|
H323
|
Accept
|
To define an H.323 rule for endpoint-to-endpoint topology:
- Configure the VoIP rule.
- Define Hide NAT (or Static NAT) for the phones in the internal network.
Do this by editing the network object for the internal network (Net_A):
- In the tab, select
- Select the (Hide or Static)
If you define Hide NAT, add a Node object (with the Hide NAT IP address) to the of the rule(s) defined in step 1.
- Install the security policy.
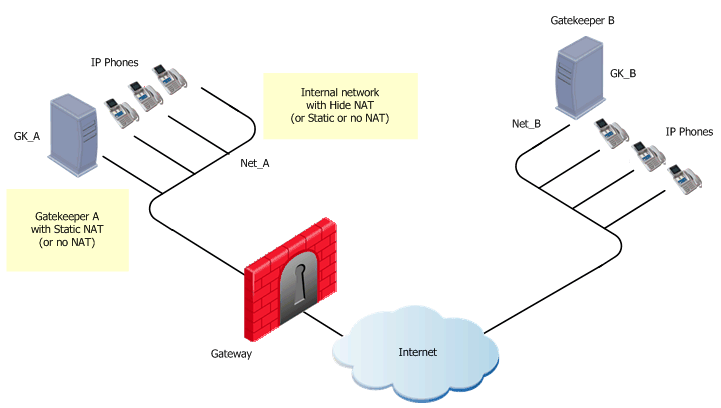
H.323 Rules for a Gatekeeper-to-Gatekeeper Topology
A Gatekeeper-to-Gatekeeper topology is shown in the figure, with Net_A and Net_B on opposite sides of the gateway. This procedure shows you how to:
- Allow bidirectional calls between the phones in the internal network (Net_A) and phones in an external network (Net_B)
- Define NAT for the internal phones and the internal Gatekeeper (GK_A)
VoIP rule for this scenario:
Source
|
Destination
|
Service
|
Action
|
Comment
|
GK_A
GK_B
|
GK_B
GK_A
|
H323
H323_ras
|
Accept
|
Bidirectional calls.
|
To define an H.323 rule for gatekeeper-to-gatekeeper topology:
- Define the network objects (Nodes or Networks) for
- Phones that use the Gatekeeper for registration
- Allowed to make calls and their calls tracked by the gateway.
In the figure, these are Net_A and Net_B.
- Define the Network object for the Gatekeeper objects (GK_A and GK_B)
- Define the VoIP rule.
- Define Hide NAT (or Static NAT) for phones in the internal network.
Do this by editing the network object for the internal network (Net_A):
- On the tab, select
- Select the (Hide or Static).
- To define Static NAT for the Gatekeeper or Gateway in the internal network: do step 4 again.
- Make the time-out of the
H323_ras service equal to or greater than the Gatekeeper registration time-out. Configure the time-outs in the window of the Service object.
- Install the security policy.
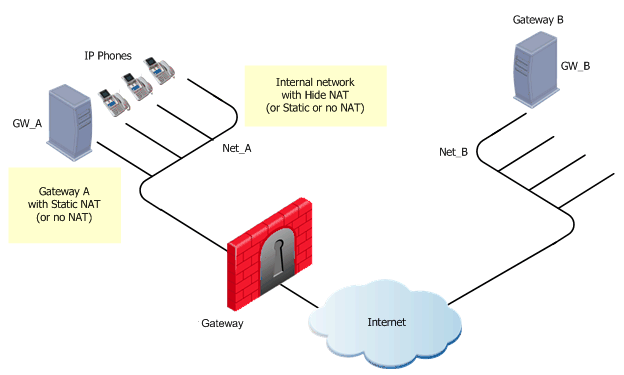
H.323 Rules for a Gateway-to-Gateway Topology
The illustration shows a Gateway-to-Gateway topology, with Net_A and Net_B on opposite sides of the gateway.This procedure shows you how to:
- Allow bidirectional calls between phones in the internal network (Net_A), and phones in an external network (Net_B)
- Define NAT for the internal phones and the internal gateway (GW_A).
VoIP rule for this scenario:
Source
|
Destination
|
Service
|
Action
|
Comment
|
GW_A
GW_B
|
GW_B
GW_A
|
H323
|
Accept
|
Bidirectional calls.
|
To define an H.323 rule for gateway-to-gateway topology:
- Define the network objects (Nodes or Networks) for phones that are allowed to make calls and their calls tracked by the gateway.
For this example, these are Net_A and Net_B.
- Define the network object for the gateway objects (GW_A and GW_B)
- Define this VoIP rule.
- Define Hide NAT (or Static NAT) for the phones in the internal network.
Do this by editing the network object for the internal network (Net_A):
- On the tab, select
- Select the (Hide or Static).
- To define Static NAT for the Gatekeeper/Gateway in the internal network, do step 4 again for the Gatekeeper/Gateway object (GK_A).
- Install the security policy.
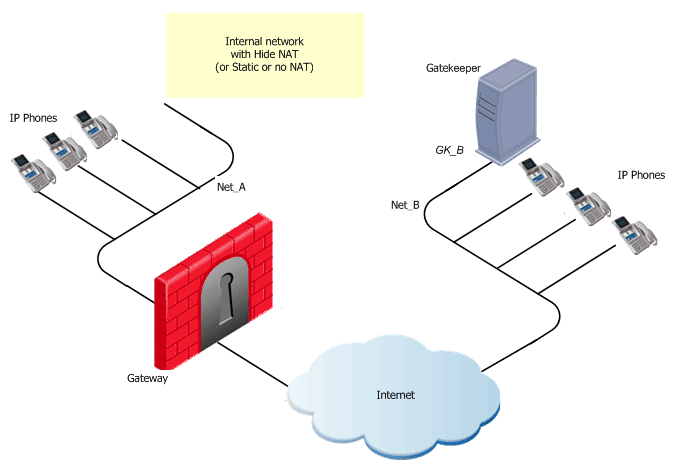
H.323 Rules for a Gatekeeper in the External Network
This figure shows a H.323 topology with a Gatekeeper in the Internet, with Net_A and Net_B on opposite sides of the gateway.This procedure explains how to:
- Allow bidirectional calls between the phones in the internal network (Net_A) and phones in an external network (Net_B)
- Define NAT for the internal phones
VoIP rule for this scenario:
Source
|
Destination
|
Service
|
Action
|
Comment
|
Net_A
Net_B
GK_B
|
GK_B
Net_A
|
H323_ras
H323
|
Accept
|
Bidirectional calls.
|
To define an H.323 rule for a gatekeeper in the external network:
- Define the network objects (Nodes or Networks) for the phones that:
- Use the Gatekeeper for registration
- Are allowed to make calls and their calls tracked by the gateway
In the figure, these are Net_A and Net_B.
- Define the network object for the Gatekeeper (GK_B)
- Configure the VoIP rule.
- Define Hide NAT (or Static NAT) for the phones in the internal network.
Do this by editing the network object for the internal network (Net_A):
- On the tab, select
- Select the (Hide or Static)
If you define Hide NAT, add a Node object (with the Hide NAT IP address) to the of the rule(s) configured in step 3.
- Make the time-out of the
H323_ras service greater or equal to the Gatekeeper registration time-out. Configure the time-outs in the window of the Service object. - Install the security policy.
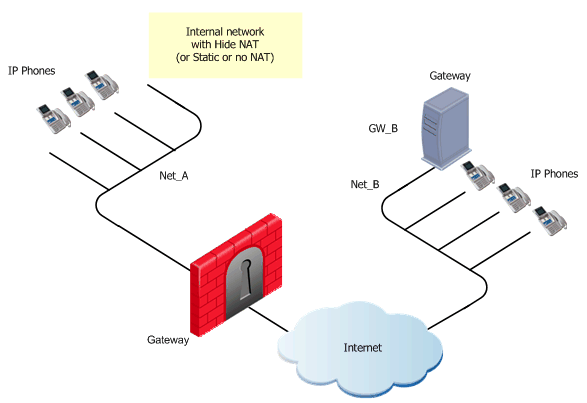
H.323 Rules for a Gateway in the External Network
The figure shows an H.323 topology with a Gateway in the Internet, with Net_A and Net_B on opposite sides of the gateway. This procedure shows you how to:
- Allow bidirectional calls between phones in the internal network (Net_A) and phones in an external network (Net_B)
- Define NAT for the internal phones
VoIP rule for this scenario:
Source
|
Destination
|
Service
|
Action
|
Comment
|
Net_A
Net_B
GW_B
|
GW_B
Net_A
|
H323
|
Accept
|
Bidirectional calls.
|
To define an H.323 rule for a gateway in the external network:
- Define network objects (Nodes or Networks) for phones that are allowed to make calls, and their calls tracked by the gateway.
For the example, these are Net_A and Net_B.
- Define the network object for the Gateway (GW_B)
- Define the VoIP rule.
- Define Hide NAT (or Static NAT) for the phones in the internal network.
Do this by editing the object for the internal network (Net_A):
- On the tab, select,
- Select the (Hide or Static).
If using Hide NAT, add a Node object (with the Hide NAT IP address) to the of the rule(s) defined in step 3.
- Install the security policy.
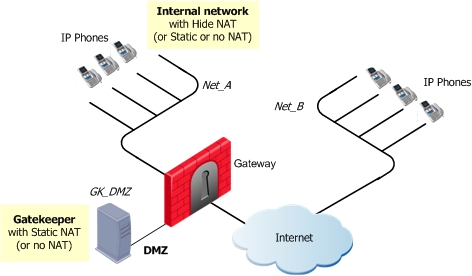
H.323 Rules for a Gatekeeper in DMZ Topology
The figure shows a H.323-based VoIP topology where a Gatekeeper is installed in the DMZ. This procedure explains how to:
- Allow bidirectional calls between the phones in the internal network (Net_A) and phones in an external network (Net_B)
- Define NAT for the internal phones and the Gatekeeper in the DMZ (GK_DMZ)
VoIP rule for this scenario:
Source
|
Destination
|
Service
|
Action
|
Comment
|
GK_DMZ
Net_A
Net_B
|
Net_A
Net_B
GK_DMZ
|
H323
H323_ras
|
Accept
|
Bidirectional calls.
|
Static NAT rules for the Gatekeeper in the DMZ:
|
|
|
|
|
|
|
Original
|
Translated
|
Comment
|
Source
|
Destination
|
Service
|
Source
|
Destination
|
Service
|
GK_DMZ
|
Net_B
|
*Any
|
GK_DMZ:
Static
|
=
|
=
|
Outgoing calls
|
Net_B
|
GK_DMZ_NATed
|
*Any
|
=
|
GK_DMZ:
Static
|
=
|
Incoming calls
|
To define an H.323 rule for a gatekeeper in the DMZ:
- Define the network objects (Nodes or Networks) for the phones:
- That use the Gatekeeper for registration
- Are allowed to make calls and their calls tracked by the gateway
In the figure, these are Net_A and Net_B.
- Define the network object for the Gatekeeper (GK_DMZ).
- Define the VoIP rule.
- Define Hide NAT (or Static NAT) for the phones in the internal network.
Do this by editing the network object for Net_A:
- In the tab, select
- Select the (Hide or Static).
If using Hide NAT:
(i) Select the option.
(ii) Enter the IP address of the Hiding address of the phones in the internal network.
(iii) Add a Node object with the Hide NAT IP address to the of the rule(s) defined in step 3.
- Define Static NAT for the Gatekeeper in the DMZ:
- Create a Node object for the Static address of the Gatekeeper (for example: GK_DMZ_NATed).
- Define the manual static NAT rules:
- Configure proxy-ARPs.
You must associate the translated IP address with the MAC address of the gateway interface that is on the same network as the translated addresses. Use the arp command in UNIX or the local.arp file in Windows.
The command fw ctl arp displays the ARP proxy table on gateways that run on Windows. On UNIX, use the arp -a command.
- Make the time-out for the
H.323_ras service greater than or equal to the Gatekeeper registration time-out. Configure the time-outs in the window of the Service object. - Install the security policy.
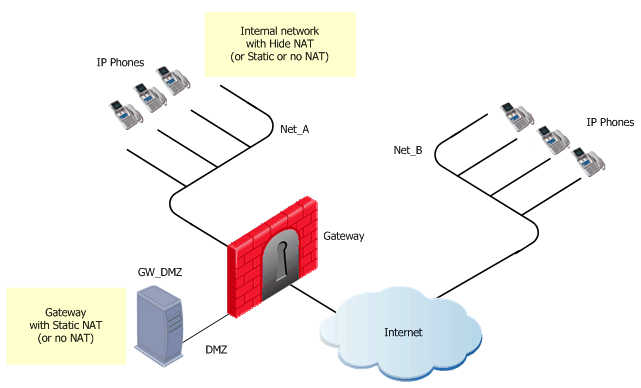
H.323 Rules for a Gateway in DMZ Topology
The figure shows a H.323-based VoIP topology where a Gateway is installed in the DMZ. This procedure shows you how to:
- Allow bidirectional calls between the phones in the internal network (Net_A) and phones in an external network (Net_B)
- Define NAT for the internal phones and the Gateway in the DMZ (GW_DMZ)
VoIP rule for this scenario:
Source
|
Destination
|
Service
|
Action
|
Comment
|
GW_DMZ
Net_A
Net_B
|
Net_A
Net_B
GW_DMZ
|
H323
|
Accept
|
Bidirectional calls.
|
Static Nat rule for the Security Gateway in the DMZ:
|
|
|
|
|
|
|
Original
|
Translated
|
Comment
|
Source
|
Destination
|
Service
|
Source
|
Destination
|
Service
|
GW_DMZ
|
Net_B
|
*Any
|
GW_DMZ:
Static
|
=
|
=
|
Outgoing calls
|
Net_B
|
GW_DMZ_NATed
|
*Any
|
=
|
GW_DMZ:
Static
|
=
|
Incoming calls
|
To define an H.323 rule for a gateway in the DMZ:
- Define network objects (Nodes or Networks) for phones that are allowed to make calls and their calls tracked by the gateway.
In the figure, these are Net_A and Net_B.
- Define the network object for the Gateway (GW_DMZ).
- Define the VoIP rule:
- Define Hide NAT (or Static NAT) for the phones in the internal network.
Edit the network object for Net_A:
- On the tab, select
- Select the (Hide or Static).
If using Hide NAT:
(i) Select the .
(ii) Enter the IP address of the Hiding address of the phones in the internal network.
(iii) Add a Node object with the Hide NAT IP address to the of the rule(s) defined in step 3.
- Define Static NAT for the Gateway in the DMZ, add manual NAT rules:
- Create a Node object for the Static address of the Gateway (for example: GW_DMZ_NATed).
- Define these manual NAT rules:
- As for all manual NAT rules, configure proxy-arps.
You must associate the translated IP address with the MAC address of the Check Point Gateway interface that is on the same network as the translated addresses. Use the arp command in UNIX or the local.arp file in Windows.
The command fw ctl arp displays the ARP proxy table on gateways that run on Windows. On UNIX, use the arp -a command.
- Install the security policy.
|
|



